Mondoo 8.10 is out!
🥳 Mondoo 8.10 is out! This release includes new SaaS scanning integrations, Oracle Cloud Infrastructure (OCI) support, expanded OS CVE detection, and more!
Get this release: Installation Docs | Package Downloads | Docker Container
🎉 NEW FEATURES
Scan Oracle Cloud Infrastructure (OCI)
cnquery and cnspec now include support for scanning Oracle Cloud Infrastructure (OCI) using your local OCI CLI configuration file. Explore your infrastructure configuration using cnquery or enforce security and compliance with custom cnspec security policies.
Connect to OCI using the cnquery shell:
$ cnquery shell oci
Query the tenant information:
cnquery> oci.tenancy
oci.tenancy: oci.tenancy name="example"
Fetch all users:
cnquery> oci.identity.users
oci.identity.users: [
0: oci.identity.user name="alice@example.com"
1: oci.identity.user name="bob@example.com"
2: oci.identity.user name="john@example.com"
]
Fetch all groups:
cnquery> oci.identity.groups
oci.identity.groups: [
0: oci.identity.group name="All Domain Users"
1: oci.identity.group name="Administrators"
]
Dive deeper with information from new OCI resources:
# list identity policies
oci.identity.policies
# list compute instances
oci.compute.instances
# list compute images
oci.compute.images
# list virtual cloud networks
oci.network.vcns
# list virtual cloud networks security lists
oci.network.securityLists
# list all buckets
oci.objectStorage.buckets
Stay tuned for additional OCI support, including Mondoo/CIS policies, and continuous scanning with Mondoo Platform.
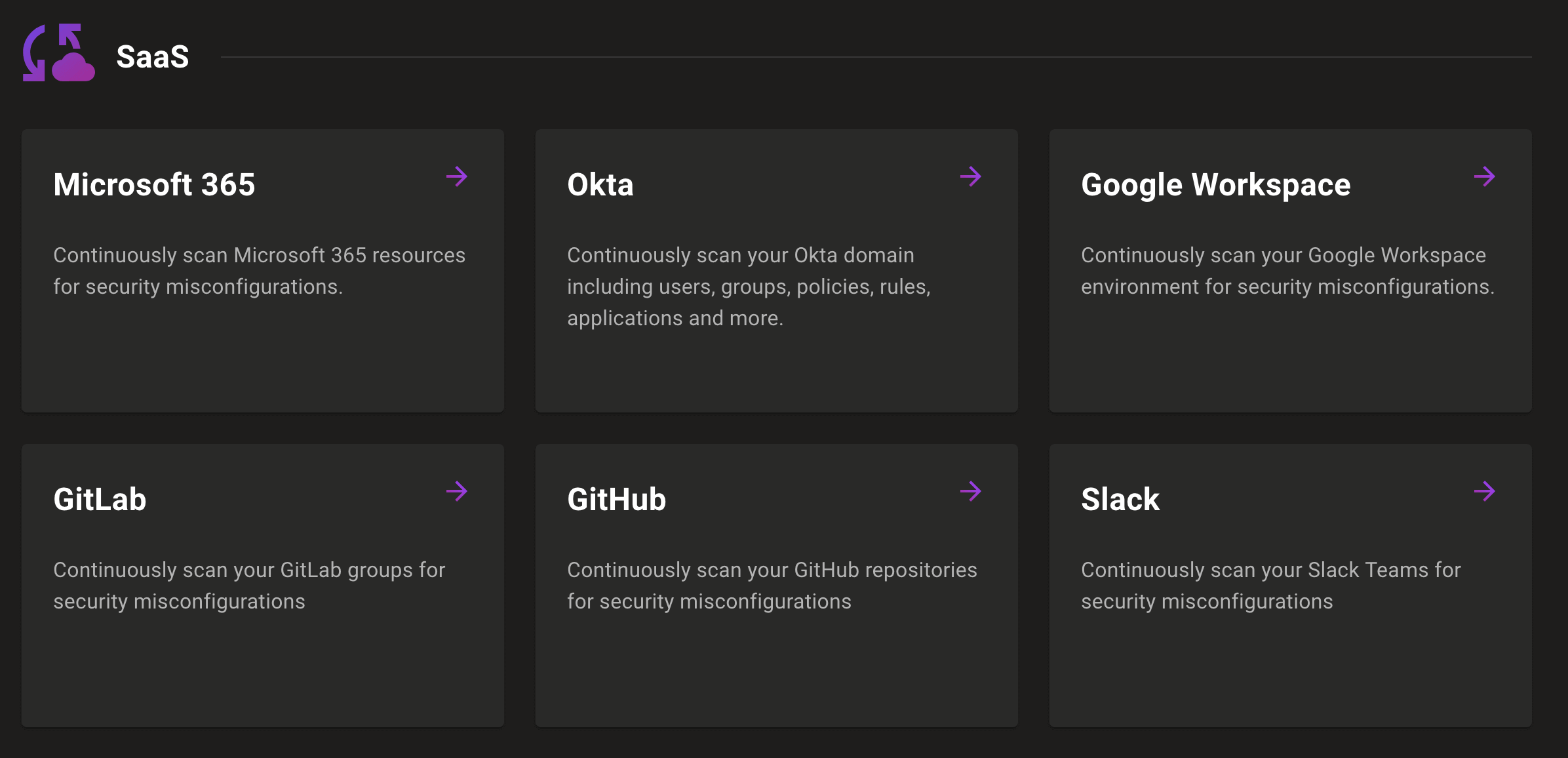
Slack / GitHub / GitLab integrations
Need continuous visibility into the security of the SaaS services you rely to do business? Now you can continuously scan GitHub repositories, GitLab groups, and Slack teams directly from the Mondoo Console without installing anything into your infrastructure.
Find these new integrations under SaaS in the Mondoo Console:
Query Terraform plan configurations
Expand the security posture of your IaC code with a new terraform.plan.configuration resource for querying Terraform plan configurations.
terraform.plan.configuration: {
resources: [
0: {
address: "null_resource.this"
mode: "managed"
name: "this"
provider_config_key: "null"
provisioners: [
0: {
expressions: {
command: {
constant_value: "echo hello_world >> hello_world.txt"
}
}
type: "local-exec"
}
]
schema_version: 0.000000
type: "null_resource"
}
]
providerConfig: [
0: {
full_name: "registry.terraform.io/hashicorp/null"
name: "null"
version_constraint: "3.2.1"
}
]
}
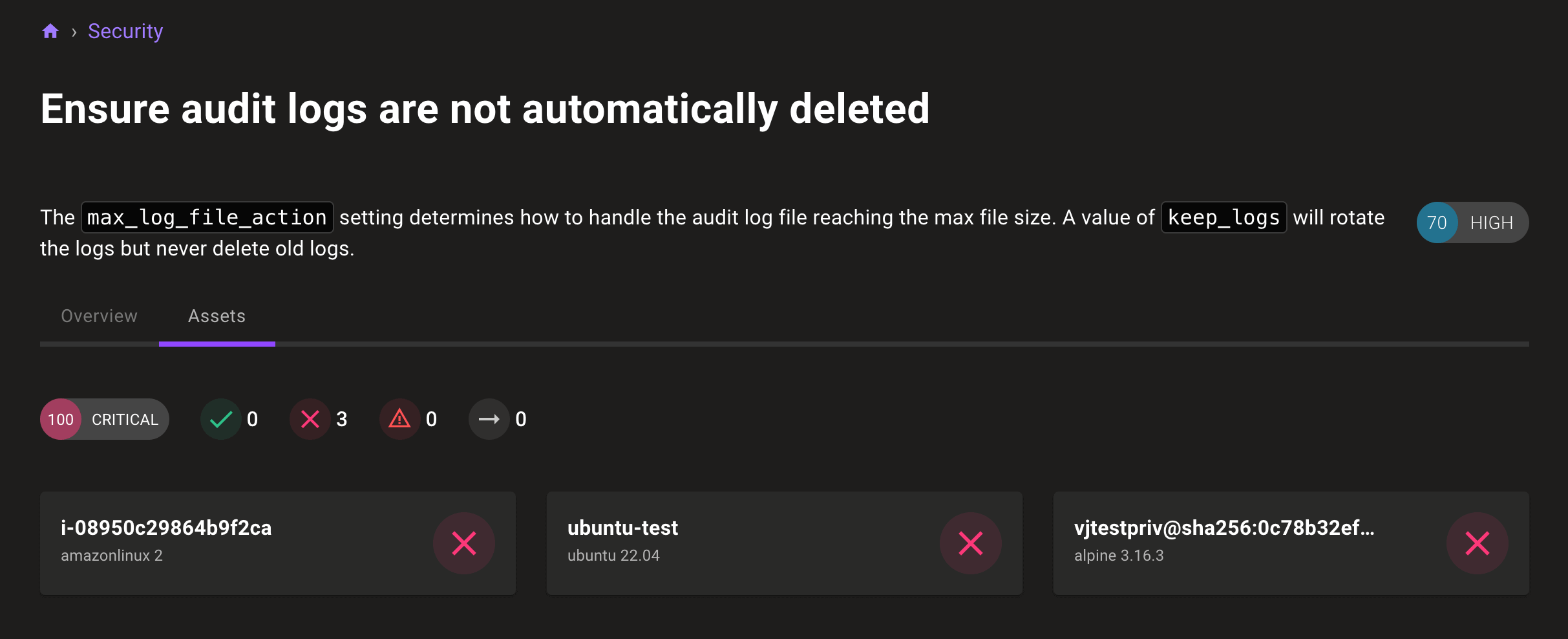
New query pages showing impacted assets
New query pages make it easier to see which assets are affected by failing security checks. Security policy checks now have their own pages, with a tab of affected assets:
Expanded CVE and EOL platform detection
Mondoo now detects the latest platform EOL and CVE data, so you can ensure your systems are in support and fully updated.
- Alpine 3.18 EOL/CVE detection
- Fedora 38 EOL/CVE detection
- VMware vSphere/ESXi 8 EOL/CVE detection
- Debian 12 CVE detection
- Ubuntu 22.10/23.04 CVE detection
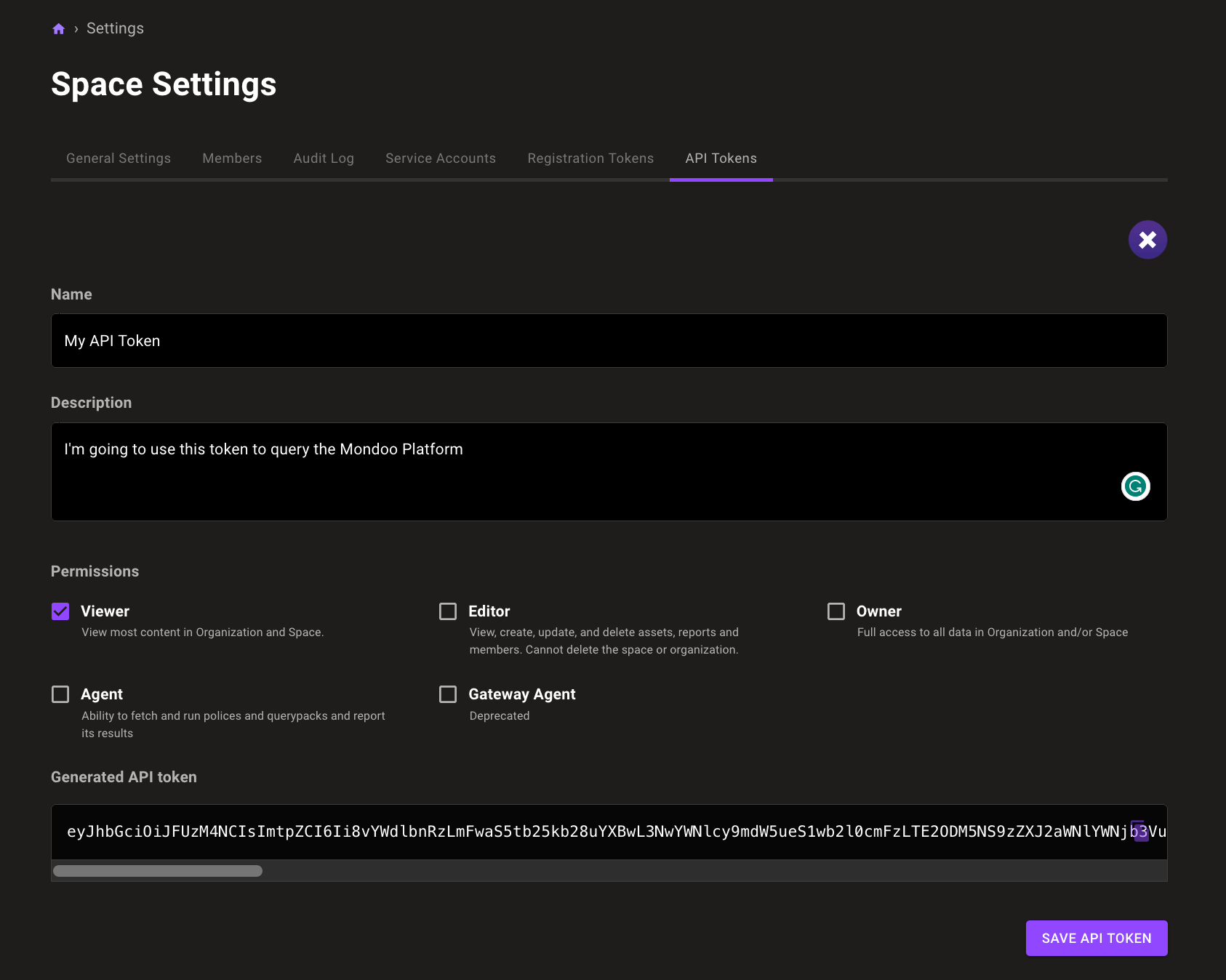
Create API token for spaces
Generate API tokens to query Mondoo in the Space settings.
🧹 IMPROVEMENTS
Support UID / GUID for files on running Docker containers
cnspec now supports inspecting the UID/GUID of files within running containers:
before
cnquery> file("/tmp").user.name
Query encountered errors:
cannot cast resource to resource type: <nil>
file.user.name: no data available
now
cnquery> file("/tmp").user.name
file.user.name: "root"
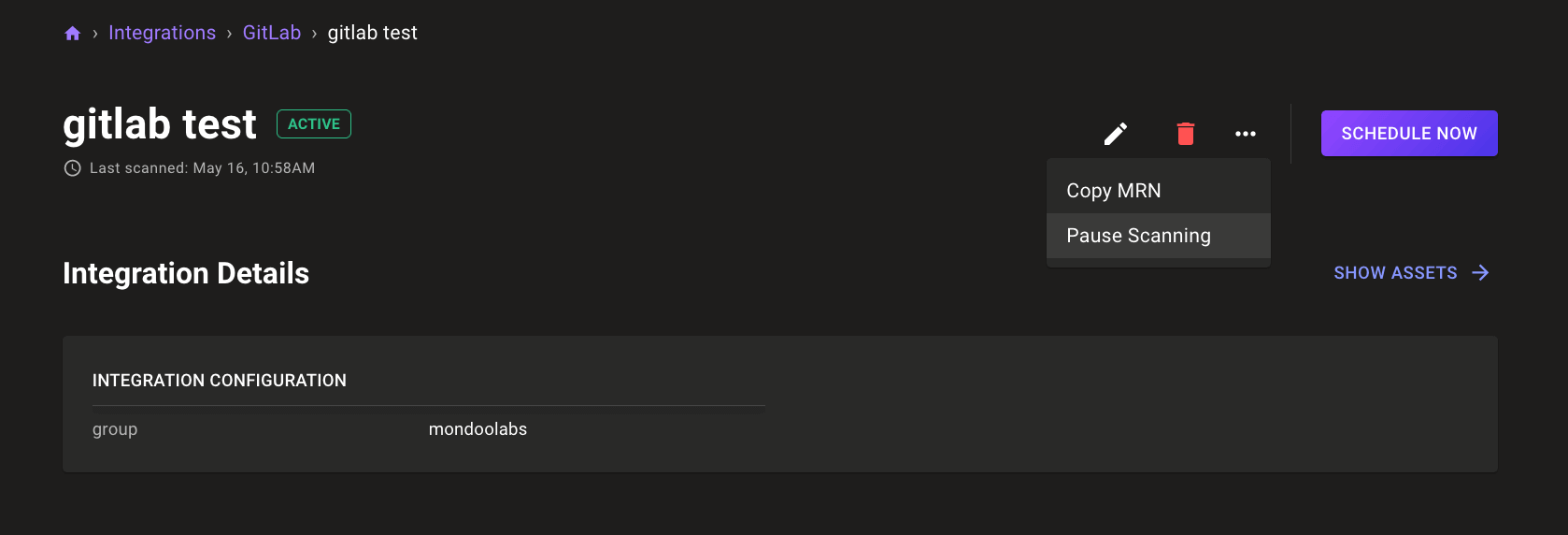
Pause integrations
Want to stop scanning in an integration temporarily without deleting it? Now you can pause integrations from the integrations settings pages.
Improved CIS Microsoft Azure Foundations Benchmark policy
The CIS Microsoft Azure Foundations Benchmark policy now includes impact scores for each control and improved queries to return actionable results for all discovered findings.
Simplified variants policies
In Mondoo version 8.0, we introduced the concept of policy variants so you can write a single security check that applies to assets in different parts of their lifecycle such as Terraform plans and the cloud assets they creates. With Mondoo 8.10, we've improved variants to remove repetitive coding from your policies. Variant queries now inherit fields from the parent query if they are no longer specified. This means you can set common fields like title, description, and properties once and have them propagate automatically to all variant queries.
See the Mondoo variants documentation for more information on using policy variants to simplify your policy as code experience.
Expanded data in BigQuery exports
Mondoo exports to Google BigQuery now provide more robust data to BigQuery for analysis:
- Add policy mappings to see which check relates to which policy
- Add support for variants so that diff can work at the variants level
- Add export time to BigQuery tables
- Allow users to tag scans with snapshot names to make it easier for them to reference them in diff queries
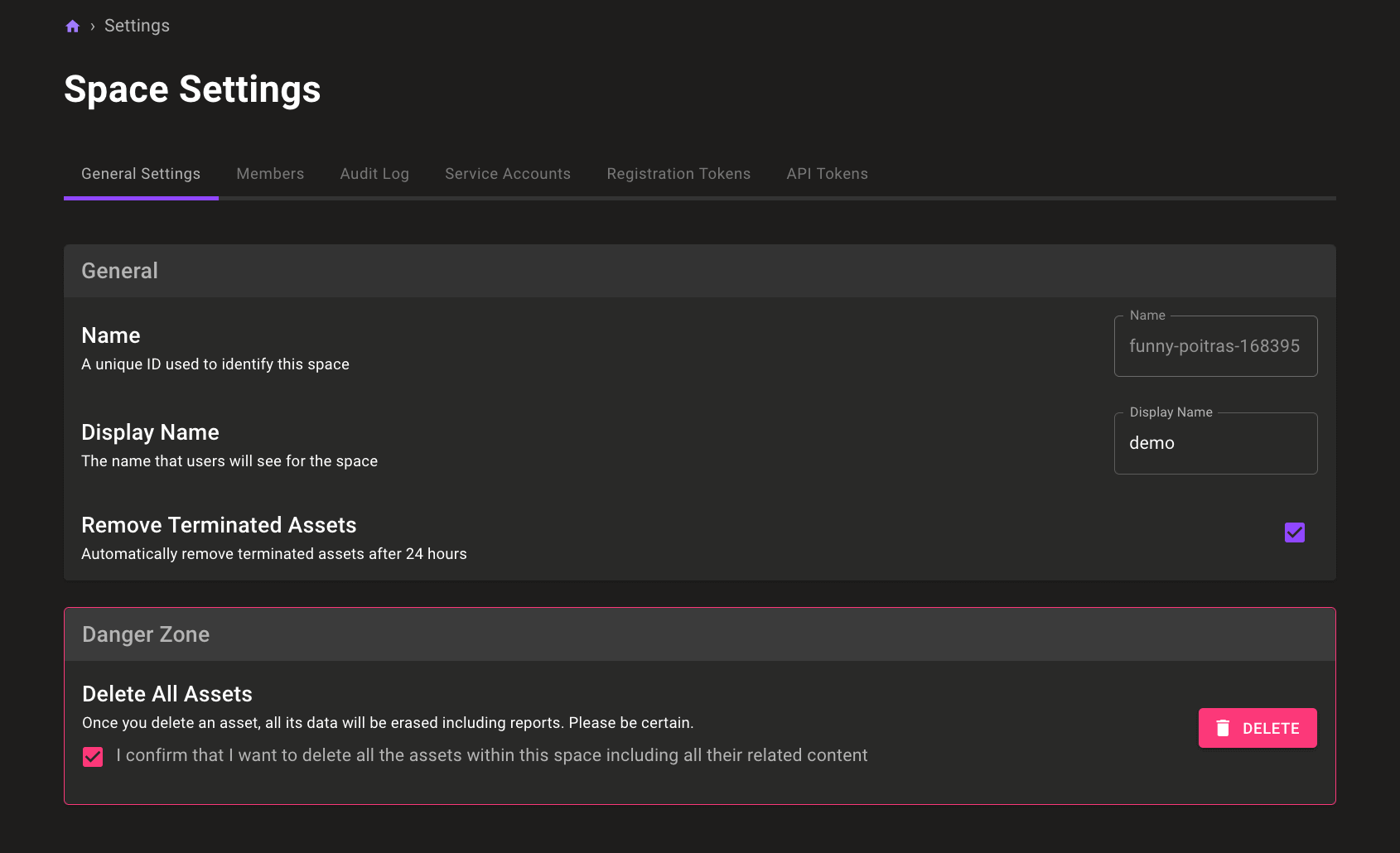
Improved asset cleanup in spaces
Done testing your Mondoo policy and integration settings, but need to remove all the temporary assets created during testing? Now you can delete all the assets in a space with a single selection while retaining custom policies and integration configurations.
🐛 BUG FIXES AND UPDATES
- Fix a failure when scanning with a policy that is missing the defined variants. Thanks for reporting this, @kmf!
- Allow piping Kubernetes manifests to cnspec for scanning. Thanks for reporting this, @michaelkrieg!
- Fix CI scans showing up as standard assets on the fleet page.
- Reduce API usage in the
aws.dynamodbresource by making the tags field optional. - Rename
Protectedfield toisProtectedin thegithub.branch. - Fix some impacted assets now showing on the CVEs page.
- Fix a failure loading data in the asset resource explorer under certain circumstances.
- Fix the fleet view summary for Google Workspace assets to show "Workspaces" not "Others".
- Fix some query results not properly displaying in the console scan results.
- Fix fetching of CVE data on VMware Photon 4.0.
- Fix scanning of GitHub repos that belong to a user not an organization.
- Fix a failure running the query
asset{ * }. - Fix missing queries in the printer formatted reports.
- Fix the URL to query packs in the registry to not mention policies.
- Fix the collapse button in the navigation bar disappearing if all items are expanded.
- Improve navigating policies with variants in the registry.
