Mondoo 9.0 is out!
🥳 Mondoo 9.0 is out!
This is a major new release with exciting improvements to cnquery and cnspec's extensibility.
This release includes a whole new cnquery and cnspec client, enhanced GitLab scanning, piles of new resource updates, and more!
Get this release: Installation Docs | Package Downloads | Docker Container
🎉 NEW FEATURES
All-new cnspec and cnquery clients!
Up to this point, both cnquery and cnspec had all connectors and providers built into one binary file each. This was great when we only had a few connectors and things were small. Recently, however, the binaries have exploded in size with every new technology that we added. Since both projects are designed to also run on small devices and embedded controllers, we wanted to change this approach for some time now.
This release includes entirely new binaries for cnquery and cnspec. Both are 90% smaller, re-usable, and extensible now!
-
Provider plugins
When you connect to any technology (like AWS, Azure, K8s, etc) we now install a dedicated provider for that technology. This happens automatically for all core technologies we support:
> cnquery run aws -c asset.name
→ installing provider 'aws' version=9.0.8
→ successfully installed aws provider path=/home/zero/.config/mondoo/providers/aws version=9.0.8
→ loaded configuration from /home/zero/.config/mondoo/mondoo.yml using source default
asset.name: "AWS Account lunalectric-management (177048008586)"These provider plugins are shared between cnquery and cnspec. If you install any provider for cnquery, it is available to cnspec and vice versa.
-
Automatic updates
Providers are automatically updated to the latest version of the current major release:
~ $> cnspec shell aws
→ found a new version for 'aws' provider installed=9.0.5 latest=9.0.8
→ successfully installed aws provider path=/home/zero/.config/mondoo/providers/aws version=9.0.8
...We avoid breaking changes during all major versions and will notify users of deprecations with a full major version of grace period, during which you can use deprecated features.
For containers and restricted environments, you can turn off updates via
--auto-update=falseorauto_update: falsein the config file. This will prevent existing providers from getting updated and prevent new providers from being installed.For example: If you install cnquery or cnspec on a container, you can pre-install all providers you aim to use with it. At the end of the build process you then deactivate the auto-update in the config file.
-
Custom providers
You can view all providers via the
providerssubcommand:> cnquery providers
→ builtin (found 2 providers)
core 9.0.1
mock 9.0.0 with connectors: mock
→ /home/zero/.config/mondoo/providers (found 4 providers)
aws 9.0.8 with connectors: aws
azure 9.0.4 with connectors: azure
gitlab 9.0.4 with connectors: gitlab
os 9.0.8 with connectors: local, ssh, winrm, vagrant, container, docker, filesystem
→ /opt/mondoo/providers has no providersThis command not only prints the current providers and versions, but it also shows the locations in which providers are installed.
In the coming days we will share written and video guides on how to create your very own provider. In the meantime, feel free to check out cnquery's "providers" folder with lots of examples! All providers are distributed as binaries with a proto interface, so you can write them in Go or any other language with GRPC support.
You can now create custom providers and install them everywhere you want to run them! This also includes restricted code that may use your company's internal APIs and which you don't want to publish. Mondoo will support the schema-upload shortly so you can see results in our UI without exposing any code.
Hassle-free asset discovery in GitLab scans
We've removed the pain of manually discovering assets throughout your GitLab environment with new hassle-free asset discovery. The GitLab Mondoo Platform integration and the cnspec CLI now include options to automatically discover all GitLab projects, groups, and even Terraform files within your GitLab projects. Set it once and continuously scan your entire environment to secure your software supply chain and the Terraform files that define your infrastructure.
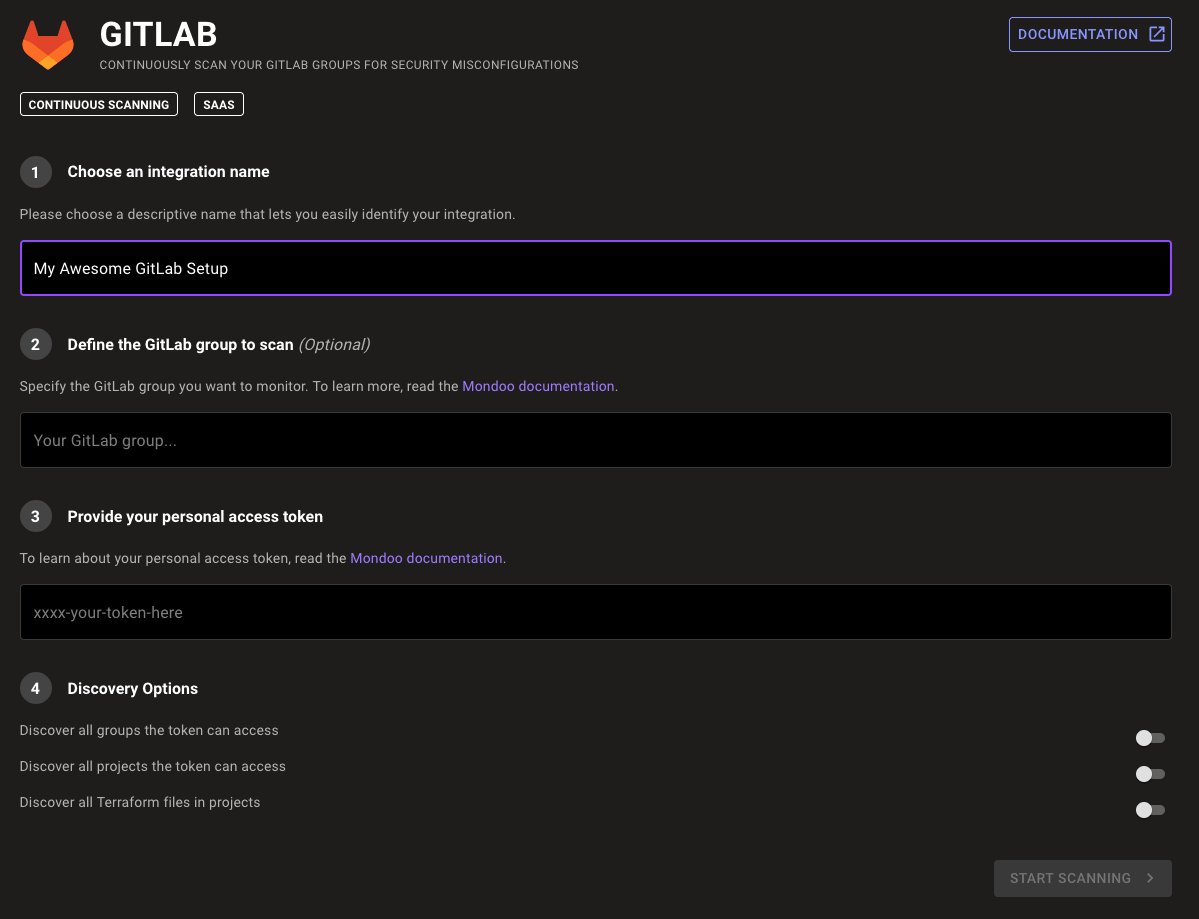
New cnspec GitLab discovery options:
cnspec scan gitlab --token TOKEN <- returns all groups the user has access to
cnspec scan gitlab --token TOKEN --discover groups <- returns the defined group and all subgroups of that group
cnspec scan gitlab --token TOKEN --discover projects <- returns all the projects discovered in all the groups the user has access to
cnspec scan gitlab --token TOKEN --discover terraform <- returns all the Terraform files in all the projects discovered in all the groups the user has access to
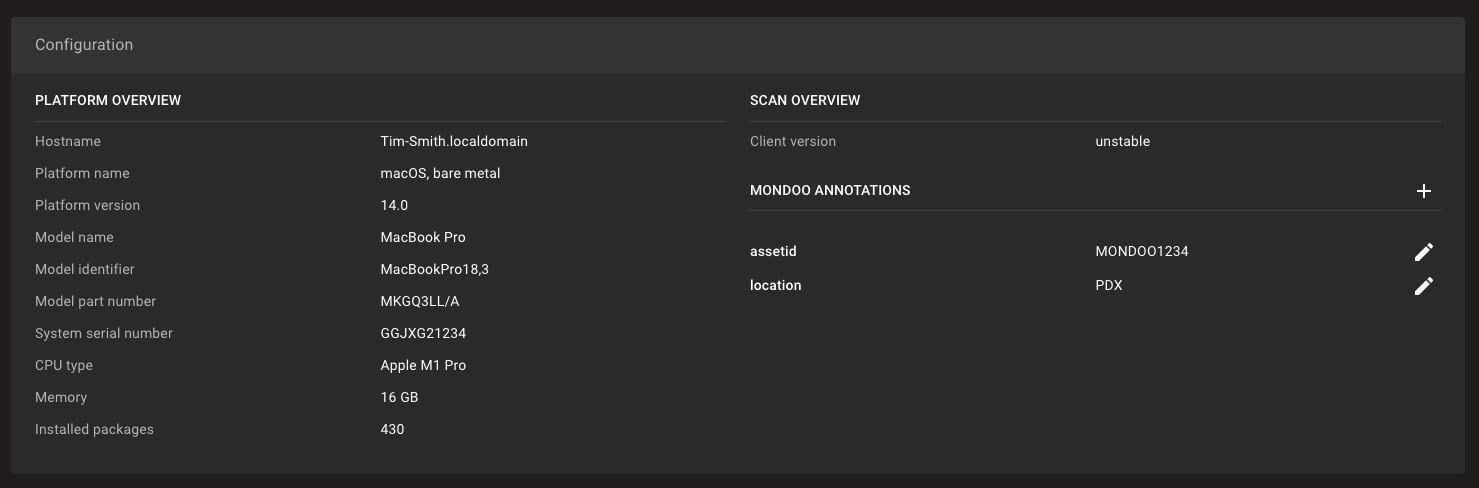
Set asset annotations during client login
Asset annotations let you add additional information on assets that can't necessarily be detected using Mondoo resources. Traditionally, these annotations have been set in the console on each asset page, but now you can automate setting annotations during the client registration process. This allows you to pass in data like employee workstation asset tags from an MDM solution.
Setting annotations during the client login:
cnspec login --token <token> --annotation assetid=MONDOO1234 --annotation location=PDX
🧹 IMPROVEMENTS
New resources and resource fields
What fun is a Mondoo release without new resources and fields to secure your infrastructure? For version 9.0, we went big with 46 new fields and resources. Stay tuned for updated policies and new asset inventory capabilities using some of these new additions.
aws.ec2.instance
- New
httpEndpointfield: Status of the IMDS endpoint enabled on the instance - New
stateTransitionTimefield: Time when the last state transition occurred
aws.elb
- New
createdTimefield: Date the load balancer was created - New
vpcIDfield: The ID of the VPC where the load balancer is located
aws.rds.dbInstances
- Improve default values for use in
cnquery shell - New
storageAllocatedfield: The amount of storage, in GiB, provisioned on the instance - New
storageIopsfield: The storage IOPS provisioned on the instance - New
storageTypefield: The type of storage provisioned on the instance - New
availabilityZonefield: Availability zone where the instance exists - New
engineVersionfield: The version of the database engine for this DB instance - New
createdTimefield: The creation date of the RDS instance
aws.s3.bucket
- New
createdTimefield: Date the bucket was created
aws.vpc
- Fix
routeTablesto return the correct values for the VPC - New
cidrBlockfield: IPv4 CIDR block of the VPC - New
instanceTenancyfield: How instance hardware tenancy settings are enforced on instances launched in this VPC - New
endpointssubresource with additional fields:id: Unique ID of the endpointtype: Type of the endpointvpc: VPC the endpoint exists inregion: Region the VPC exists inserviceName: The name of the endpoint servicepolicyDocument: The policy document associated with the endpoint, if applicablesubnets: The subnets for the (interface) endpoint
- New
subnetssubresource with additional fields:arn: ARN of the subnetid: Unique ID of the subnetcidrs: A list of CIDR descriptionsmapPublicIpOnLaunch: Whether instances launched in this subnet receive a public IPv4 address
azure.subscription.monitorService.activityLog
- New
subscriptionIdfield: The subscription identifier
azure.subscription.monitorService.diagnosticsetting
- New
storageAccountIdfield: ID of the diagnostic setting storage account
azure.subscription.monitorService.logprofile
- New
storageAccountIdfield: ID of the log profile storage account
github.organization
- New
membersCanForkPrivateReposfield: Whether members can fork private repositories to their own GitHub account
github.repository
- New
hasDiscussionsfield: Whether the repository has discussions - New
isTemplatefield: Whether the repository is an organization repository template
gitlab.project
- New
allowMergeOnSkippedPipelinefield: Allow merging merge requests when a pipeline is skipped - New
archivedfield: Is the project archived? - New
autoDevopsEnabledfield: Is the Auto DevOps feature enabled? - New
containerRegistryEnabledfield: Is the container registry feature enabled? - New
createdAtfield: Create date of the project - New
defaultBranchfield: Default git branch - New
emailsDisabledfield: Disable project email notifications - New
fullNamefield: The full name of the project, including the namespace - New
issuesEnabledfield: Is the issues feature enabled? - New
mergeRequestsEnabledfield: Is the merge request feature enabled? - New
mirrorfield: Is the project a mirror? - New
onlyAllowMergeIfAllDiscussionsAreResolvedfield: Only allow merging merge requests if all discussions are resolved - New
onlyAllowMergeIfPipelineSucceedsfield: Only allow merging merge requests if the pipelines succeed - New
packagesEnabledfield: Is the packages feature enabled? - New
requirementsEnabledfield: Is the requirements feature enabled? - New
serviceDeskEnabledfield: Is the Service Desk feature enabled? - New
snippetsEnabledfield: Is the snippets feature enabled? - New
webURLfield: URL of the project - New
wikiEnabledfield: Is the wiki feature enabled?
gitlab.group
- New
emailsDisabledfield: Disable group email notifications - New
preventForkingOutsideGroupfield: Don't allow forking projects outside this group - New
mentionsDisabledfield: Disable group mentions within issues and merge requests - New
webURLfield: URL of the group
k8s.namespace
- New
kindfield: Kubernetes object type
rsyslog.conf
- New
pathfield: Path for the main rsyslog file and search
terraform.settings
- New
backendfield: Backend configuration information
Improved query packs
- The Azure Asset Inventory Pack now includes a list of all public IP addresses in Azure subscriptions.
- The Mondoo Asset Count query pack now includes asset counts for all GCP and GitLab assets, including all-new GCP assets discovered when scanning with the
--discover allflag.
MQL improvements
Mondoo 9.0 further improves MQL so you can more easily query assets in your environment and write custom security policies.
Simple accessors for unstructured data
Accessing structures in JSON, Terraform, and Kubernetes has often been painful:
dict["one"]["more"]["field"]
To make it easier to access these nested fields, we've introduced a new optional syntax. This is well-known from other scripting languages (like JS and TS):
dict.one.more.field
This mode continues to support our GraphQL foundation:
dict {
one { more.field }
two
...
}
It has helped simplify many use-cases for Terraform and Kubernetes:
# OLD:
tfblock {
_["attributes"]["account_id"]["value"]
}
# NEW:
tfblock {
attributes.account_id.value
}
Empty type
With the new empty type, there's no need for complex logic to check for different kinds of empty values. Each of these common situations evaluate as empty:
[] == empty
null == empty
'' == empty
{} == empty
A single query can now check for an empty value in any type of data:
users.list == empty
Expanded platform EOL data
- Add Fedora 39: November 12, 2024
- Add Google COS 109: September 1, 2025
🐛 BUG FIXES AND UPDATES
- Significantly improve querying time of ports on Linux systems. If you query ports without accessing its related process, it will now return in a fraction of the time. We are working to further speed this up for use-cases with related processes.
- Remove errors for
files.findwhen no results were returned. Do not return an empty file object. - Improve output of GCP resources in the cnquery shell.
- Resolve errors running the CIS
Ensure default user shell timeout is 900 seconds or lesscheck. - Resolve errors running the CIS
Ensure lockout for failed password attempts is configuredcheck. - Resolve errors running the CIS
Ensure password hashing algorithm is SHA-512 or yescryptcheck. - Resolve errors running the CIS
Ensure password reuse is limitedcheck. - Fix false positive in the CIS
Ensure lockout for failed password attempts is configuredcheck. - Don't show buttons to accept a compliance exception if the user only has viewer privileges in the space.
- Don't show
nullat the end of compliance framework and control descriptions. - Show the asset completion percentage on compliance control pages.
- Fix invalid CloudFormation links on the AWS integration page.
- Avoid repeatedly generating registration tokens in the organization/space page.
- Fix incorrect integrations listed on the Google Workspace integration page.
- Add missing label examples in the search page.
- Change all
unknownandunratedcheck statuses tounscored. - Improve the rendering of Compliance Hub control distribution graphs with large numbers of controls.
- In the registry, fix platform icons not displaying correctly for policies that use variants.
- Allow updating the GCP service account configuration file in GCP integrations.
- Fix scanning of untagged Amazon ECR images.
- Fix some check links in Compliance Hub not loading.
- Fix EC2 instance detection when IMDSv1 is disabled.

