Mondoo 6.19 is out!
🥳 Mondoo 6.19 is out! This release includes new Kubernetes content and UI improvements!
Get this release: Installation Docs | Package Downloads | Docker Container
🎉 IMPORTANT CHANGES
New Mondoo Policies Replace Existing Policies
We've introduced newly renamed Mondoo out-of-the-box policies. These policies include more consistent policy and UID names to communicate security vs. best practices as well as the new scoring system mentioned below. We've marked the existing policies as deprecated to avoid impacting users at this time. You can switch to these new policies by disabling the deprecated policy and enabling these new policies in the Policy Hub. At a date we will automatically migrate users from the existing policies to these new policies. Stay tuned for more details!
New Policy Scoring Evaluation
We've updated our out-of-the-box Mondoo policies to use a more appropriate scoring system. With this change the overall score a policy receives is now always reflecting the most critical failure. Previously, we would compute an average for all failed controls, which sometimes hid critical controls. With this change high impact controls in policies are not hidden by a large number of low impact passing controls anymore. For many users this will increase the number of low scoring policies in their spaces by exposing controls that are failing.
GitHub Discussions open for business
Problem: You have a question about writing policies or scanning hosts with Mondoo, but nothing comes up in search engines, and waiting on Slack responses can take forever.
Solution: We decided to move our main community presence to GitHub Discussions. Slack is fantastic for real-time discussions, but it's problematic for getting quick answers to common questions. With GitHub Discussions, every question asked in the past is available in search. Over time this builds up an extensive FAQ resource. You can find these discussions at https://github.com/orgs/mondoohq/discussions. We already started to move interesting topics there, so you'll find plenty of MQL guidance. We'll still be around on Slack and Discord for interactive chat, but prefer to discuss common topics on GitHub now.
🎉 NEW FEATURES
New Kubernetes Security Policies
Problem: Your Kubernetes workloads are secure, but you want to ensure that the cluster and cluster nodes are also secured.
Solution: We've introduced a number of new controls for the Kubernetes API Server and Kubelets to keep your cluster secure:
| Policy | Applies To |
|---|---|
| Ensure the kube-apiserver is not listening on an insecure HTTP port | API Server |
| Ensure the kube-apiserver does not allow anonymous authentication | API Server |
| Deployments should not run Tiller (Helm v2) | Deployments |
| Pods should not run Tiller (Helm v2) | Pods |
| Deployments should not run Kubernetes dashboard | Deployments |
| Pods should not run Kubernetes dashboard | Pods |
| Disable anonymous authentication for kubelet | Kubelets |
| Configure kubelet to capture all event creation | Kubelets |
| Configure kubelet to ensure IPTables rules are set on host | Kubelets |
| Configure kubelet to protect kernel defaults | Kubelets |
| Do not allow unauthenticated read-only port on kubelet | Kubelets |
| Ensure the kubelet is not configured with the AlwaysAllow authorization mode. | Kubelets |
| Configure kubelet to use only strong cryptography | Kubelets |
| Run kubelet with a user-provided certificate/key | Kubelets |
| Run kubelet with automatic certificate rotation | Kubelets |
| Ownership and permissions of kubelet configuration should be restricted | Kubelets |
| Specify a kubelet certificate authorities file and ensure proper ownership and permissions | Kubelets |
NSA/CISA Kubernetes Hardening Guidelines Preview Policy
Problem: You want to secure your Kubernetes infrastructure against the latest NSA/CISA guidance.
Solution: Mondoo now includes a preview policy implementing the NSA/CISA guidance. This guidance looks at Kubernetes security in the control plane, cluster nodes, and workloads. Stay tuned for updates to this policy in the coming weeks. Be sure to check out the NSA's press release announcing this new guidance document, which includes a link to the complete PDF: https://www.nsa.gov/Press-Room/News-Highlights/Article/Article/2716980/nsa-cisa-release-kubernetes-hardening-guidance/
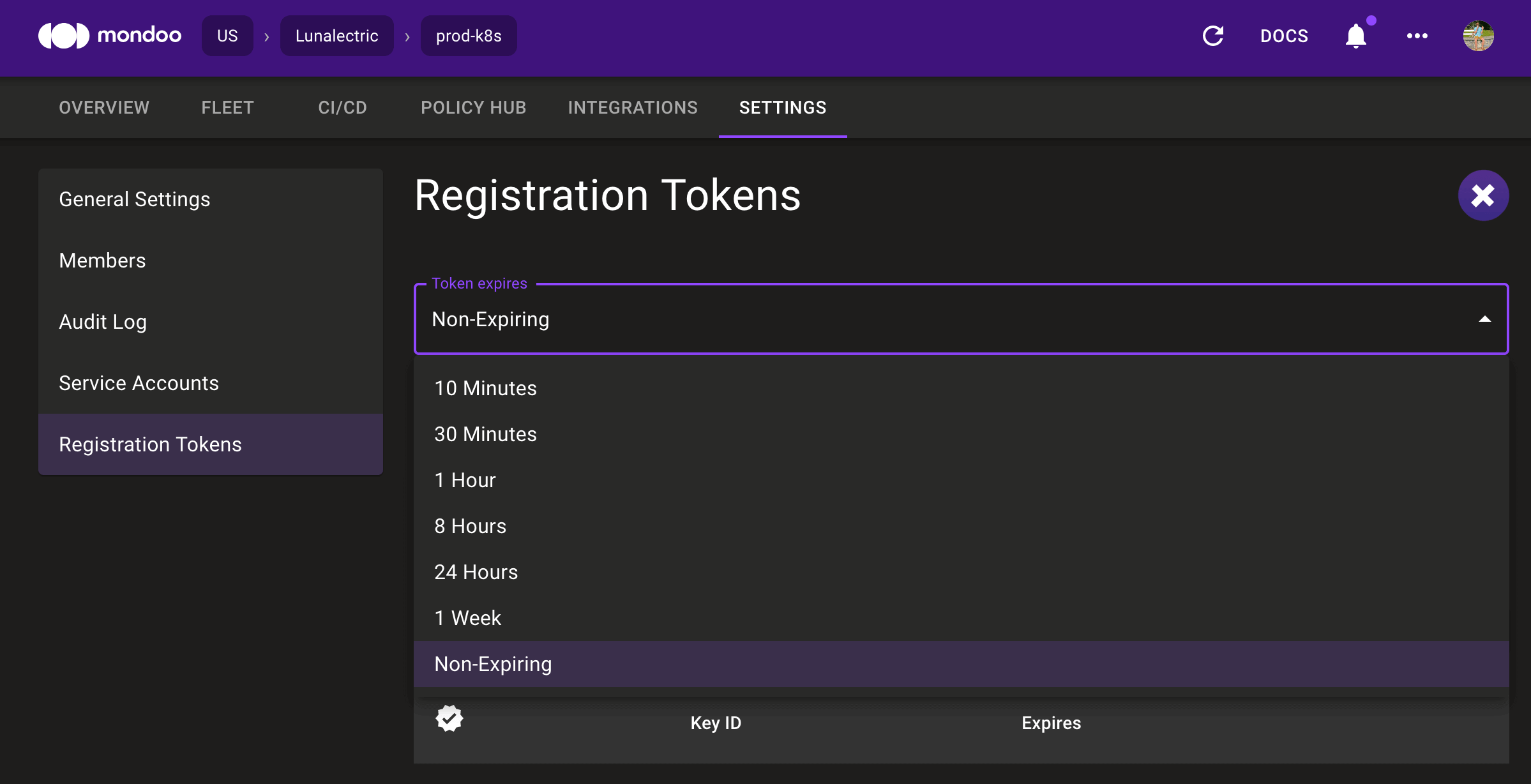
Long-Lived Registration Tokens
Problem: You want to automate the registration of new nodes into Mondoo Platform, but it's difficult when new registration tokens need to be generated constantly.
Solution: You can now generate long-lived aka non-expiring registration tokens in the UI. These are ideal for automated processes like auto-scaling groups where tokens are stored in secrets management systems and cannot expire.
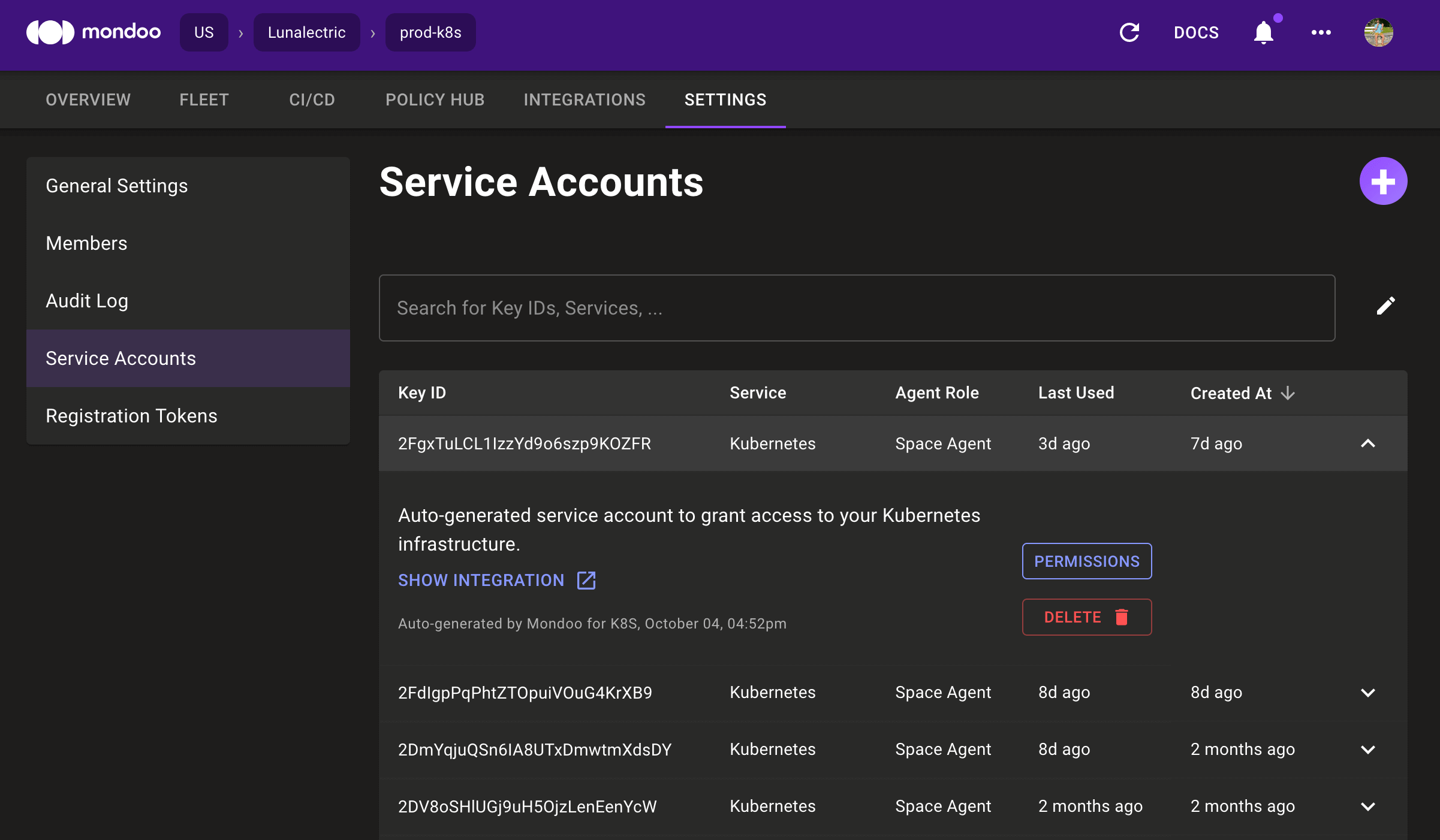
New Service Account UI
Problem: Each integration you set up in Mondoo adds a service account, and managing these accounts can be difficult if you want to remove unused accounts or view usage.
Solution: We've updated the service account page to make it easier to manage service accounts. The new UI exposes important information like the creation date, the last used date, and what created the account. You can also expand each item in the list to link to the integration using the service account, change permissions, or delete the account.
🧹 IMPROVEMENTS
EBS Volume Scanning in the Instance's Region
Problem: You want to scan AWS instances without installing the Mondoo Client using the EBS volume scanning, but you run in multiple regions, making the cost prohibitive.
Solution: We now scan the EBS volume of instances in the regions where the instances run. This avoids potentially costly data transfer costs.
More Severity Data in Policies
Problem: At first scan Mondoo finds an enormous pile of security issues in your environment for you to tackle, but which ones are the most important?
Solution: We've continued to improve our Mondoo's ability to help you prioritize your work with severities in policies. Our Windows policies now all include severity data and Linux policies have been adjusted to make sure you're tackling the most pressing issues first.
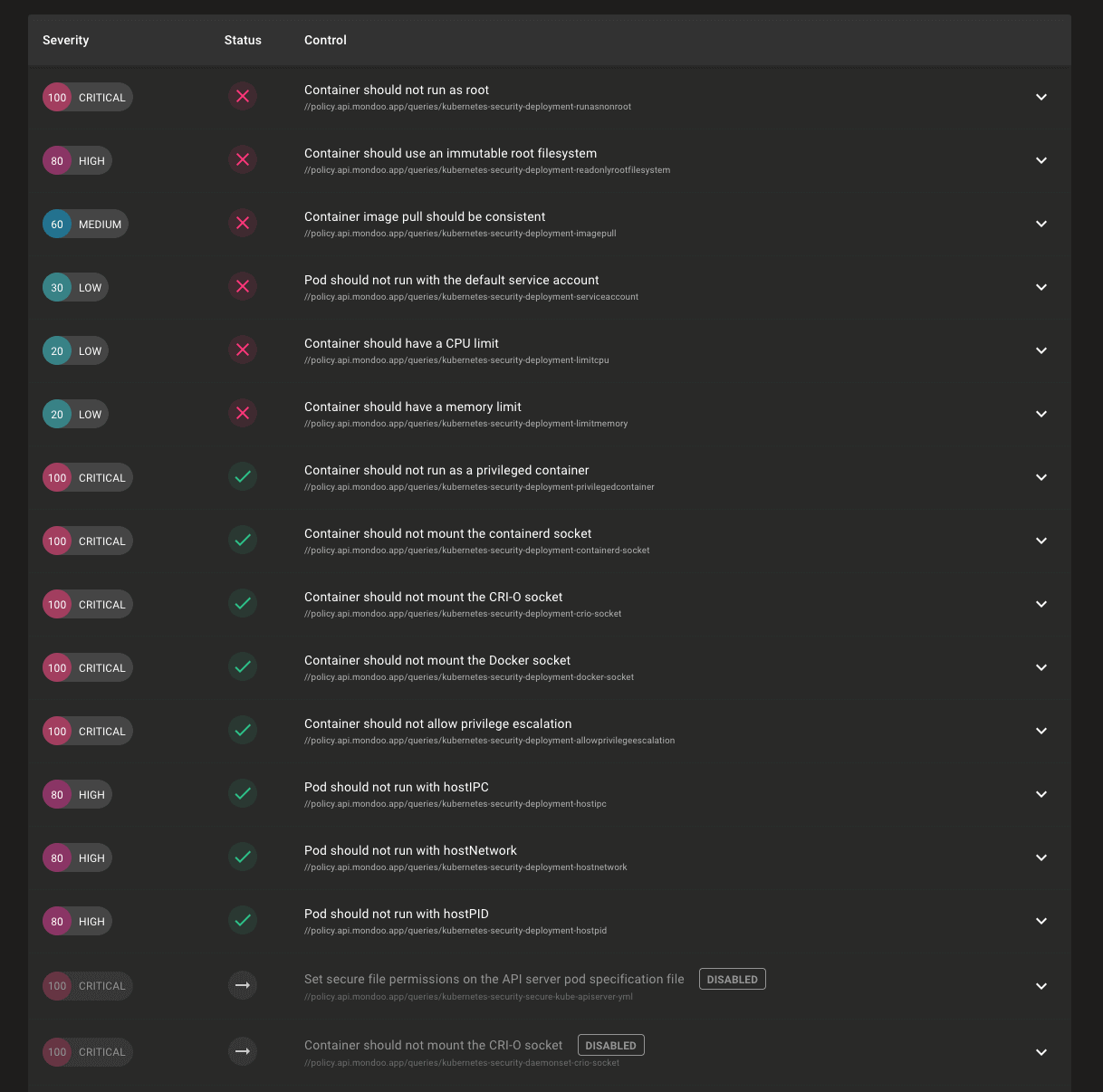
Better Prioritized Control Views
Problem: Policies on your assets can have hundreds of controls and you need to evaluate the security of an asset at a glance.
Solution: We've improved how controls in policies are displayed to make it easier to quickly understand the security posture of your assets. Skipped policies are now displayed at the bottom of the results, allowing you to see the controls that have passed or failed more easily. This is particularly useful when viewing the results of the Mondoo Kubernetes Security policy, which has many workload controls skipped depending on the asset type. We're also now sorting by severity within each status so you can quickly see the highest severity failed controls.
You can now also manually sort on any column in the results, so you can always view the data just how you like.
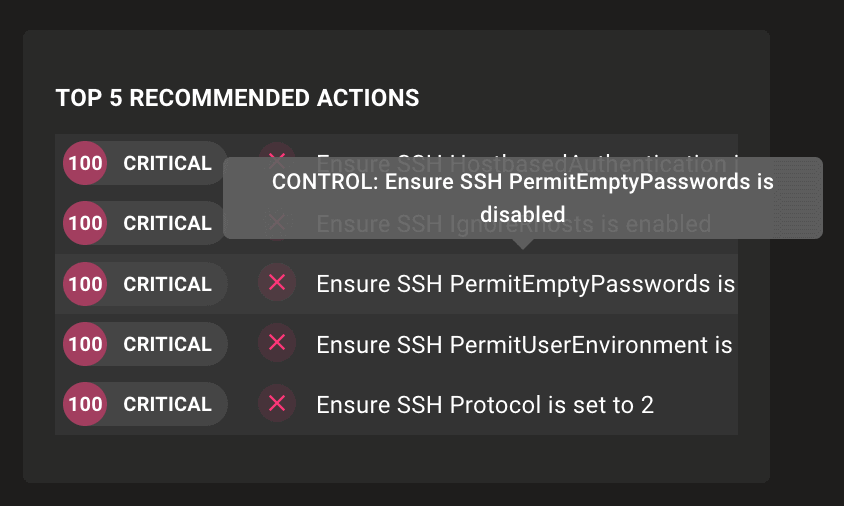
Hover over in Top 5 Recommended Actions tile
Problem: The Top 5 Recommended Actions tile shows high-impact failures that should be resolved first, but it's often hard to determine which controls have failed due to the small size of the tile and the long control names.
Solution: If part of a control name is clipped due to the size of the Top 5 Recommended Actions tile, you can now hover over the titles for a tooltip with the complete name.
All Kubernetes Namespaces Scanned by Default
Problem: You want to scan your Kubernetes cluster, but it includes workloads from many different namespaces, which aren't scanned by default.
Solution: By default Mondoo will now scan all Kubernetes namespaces. This means a complete cluster scan can be achieved with just mondo scan k8s now. The --all-namespaces CLI flag has been deprecated and will be removed from a future release. If you'd like to limit your scans to just a single namespace, you can still do this by specifying the namespace on the CLI with --namespace FOO.
🐛 BUG FIXES AND UPDATES
- Fix failures to properly filter on tags when scanning AWS instances.
- Fix failures parsing the contents of
/proc/syswhen a file was empty. - Fix incorrect asset counts in the fleet view after an asset was deleted.
- Kubernetes manifest names in the shell now show as the file name and not the file's directory.
- Improve help text to make it more clear what commands do.
- Remove the undocumented
mondoo scan github usersub-command. Stay tuned for the return of this command with more clear use cases for scanning all user repositories. - Use sysctl to scan Linux kernel parameters where we can to prevent failures scanning
/proc/sysin some scenarios. - Properly read the exit codes of commands that are executed on Docker containers.
- Improve error output when connecting to AWS accounts.
- Do not panic when querying a single k8s resource without providing id/name.
- Do not fail when using
k8s.networkPoliciesif a cluster has the Calico CNI. - Registration tokens properly refresh in the integrations setup UI pages.
- Prevent failures to scan EC2 instances when a single keypair is missing.
- Fix failures using Microsoft 365 certificate authentication.
- Fix failures in search filtering for Kubernetes admission controller assets.
