Mondoo 9.11 is out!
🥳 Mondoo 9.11 is out! This release includes continuous domain/IP scanning, new and expanded AWS resources, and more!
Get this release: Installation Docs | Package Downloads | Docker Container
🎉 NEW FEATURES
Continuous domain and IP scanning
New continuous domain and IP scanning ensures the security and compliance of your external web properties.

Scan these endpoints using out-of-the-box SSL/TLS, DNS, and HTTP security policies to ensure your properties meet security best practices. Protect against common endpoint security mistakes such as:
- Certificates nearing their expiration date
- Insecure TLS releases or ciphers
- Missing
X-Content-Type-Optionsin HTTP headers
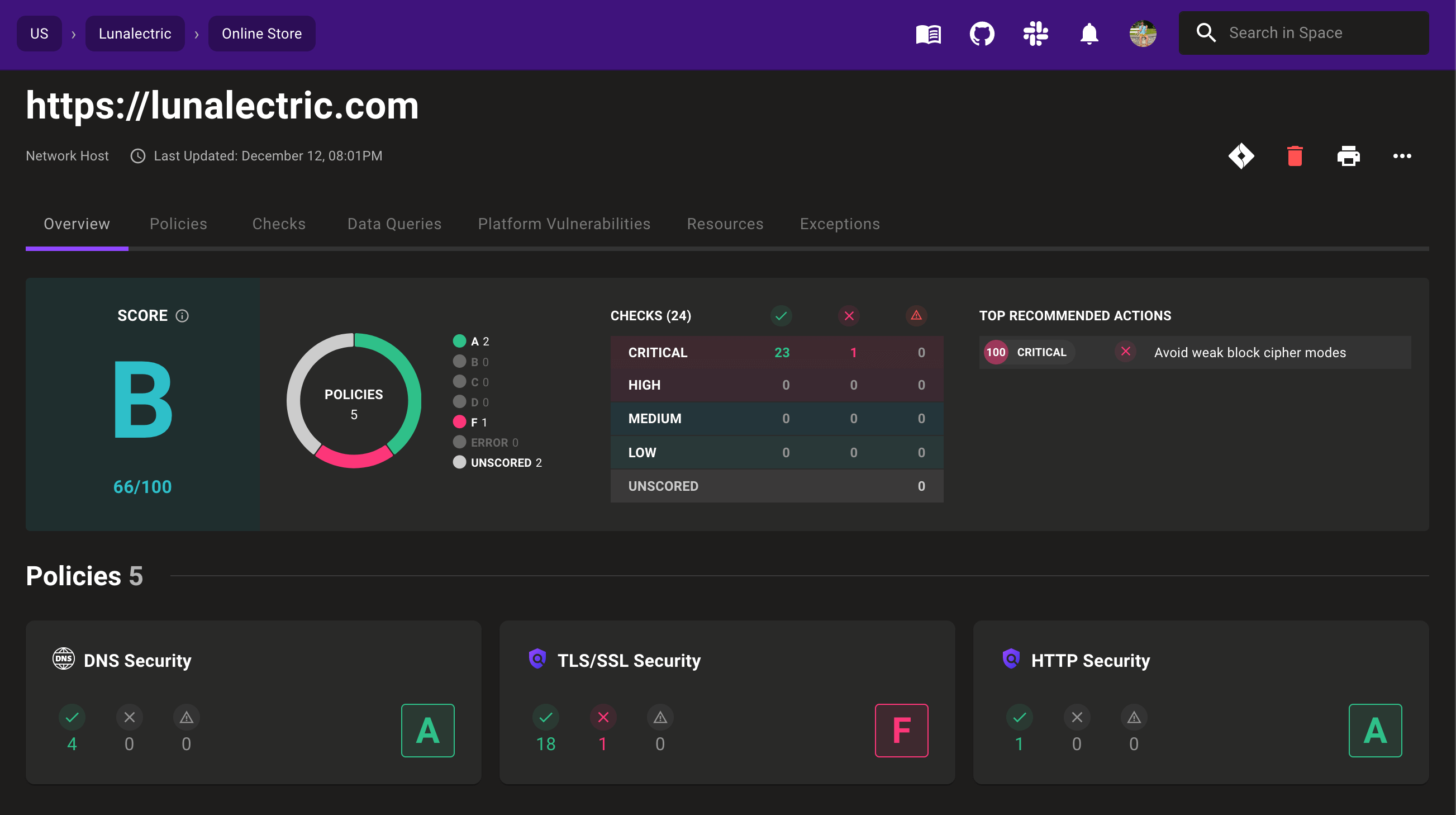
Domain and IP scans don't stop with just security. These scan results are automatically mapped to compliance controls such as SOC 2 type 2's CC6.7.2: Uses Encryption Technologies or Secure Communication Channels to Protect Data. This provides continuous compliance for your web properties.
New AWS Web Application Firewall (WAF) resource
Secure Amazon's Web Application Firewall (WAF) service with new Mondoo WAF resources. These resources allow you to query WAF ACLs, Rules, RuleGroups, and IP Sets.
See the AWS Resource Pack documentation for a complete list of new WAF resources.
Load policies from AWS S3 buckets
Want to run custom policies across multiple systems without storing those policies in the Mondoo Platform's Registry? Now you can load policies in cnspec directly from AWS S3 buckets.
Specify an entire bucket and cnspec picks the correct policy:
cnspec scan -f s3://mysupernotexistingbucket1234567
Or specify the exact policy file in your bucket:
cnspec scan -f s3://mysupernotexistingbucket1234567/packs.mql.yaml
🧹 IMPROVEMENTS
New fields and defaults in AWS resources
aws.ec2.instance
- Improve default values
- New
enaSupportedfield - New
hypervisorfield - New
instanceLifecyclefield - New
rootDeviceTypefield - New
rootDeviceNamefield - New
architecturefield
aws.ec2.volume
- Improve default values
- New
multiAttachEnabledfield - New
throughputfield - New
sizefield - New
iopsfield
aws.ec2.snapshot
- Improve default values
- New
volumeSizefield - New
descriptionfield - New
encryptedfield
aws.cloudwatch.logGroups
- New
retentionInDaysfield
aws.ec2.securityGroups
- Improve default values
aws.ec2.networkacl
- New
isDefaultfield - New
tagsfield
New GitHub pull request query capabilities
New fields in the GitHub resource give you fine-grained control over queries for GitHub pull requests.
First, connect to your GitHub repository with the cnquery shell:
cnquery shell github repo mondoohq/cnspec
Once you're connected to the GitHub repo in cnquery, you can query pull requests in a few different ways.
Query individual pull requests by number:
cnquery> github.mergeRequest(number: 1){ number state title }
github.mergeRequest: {
number: 1
title: "🧹 update command line help"
state: "closed"
}
Query all closed pull requests:
cnquery> github.repository.closedMergeRequests
github.repository.allMergeRequests: [
0: github.mergeRequest id=1640488170 state="closed"
1: github.mergeRequest id=1638254852 state="closed"
2: github.mergeRequest id=1638253038 state="closed"
...
]
Query all closed and open pull requests:
cnquery> github.repository.allMergeRequests
github.repository.allMergeRequests: [
0: github.mergeRequest id=1640488170 state="closed"
1: github.mergeRequest id=1640302075 state="open"
2: github.mergeRequest id=1638694955 state="open"
...
]
Improve bucket JSONL export
Do you export your Mondoo data through one of our storage integrations? We've made it easier for you to process these exports in systems like Splunk or ELK: We added ExportedAt and asset_mrn fields:
{
"mrn": "//assets.api.mondoo.app/spaces/vibrant-edison-123456/assets/2Z8pfFOyDBcZhGHi123456789",
"asset_mrn": "//assets.api.mondoo.app/spaces/vibrant-edison-123456/assets/2Z8pfFOyDBcZhGHi123456789",
"name": "https://mondoo.com",
"platform_name": "host",
"error": "",
"score_updated_at": "2023-12-06T14:03:51Z",
"updated_at": "2023-12-06T14:03:51Z",
"labels": {
"mondoo.com/integration-mrn": "//integration.api.mondoo.app/spaces/vibrant-edison-123456/integrations/2YzVgXUPvA09dZ1tBD123456789"
},
"annotations": null,
"exported_at": "2023-12-06T15:12:57.619506985Z"
}
Alpine 3.19 support
On December 7th the Alpine Linux team released Alpine Linux 3.19 with an updated Kernel and new versions of common language packages. Mondoo includes support for this latest release with EOL and CVE detection. Learn more about what's new in this updated version at alpinelinux.org.
Ignore .terraform directory during scans
Want to scan Terraform files in a project directory, but the pesky .terraform directory is getting in your way? Now you can ignore files in the .terraform directory with the new --ignore-dot-terraform flag.
🐛 BUG FIXES AND UPDATES
- Improve the display of categories in integrations during setup and on the integrations page.
- Improve the UI on the space registration token page when no tokens have been created.
- In audit log entries, include the asset on which the action occurs.
- Improved registry search results for policies and query packs.
- Detect Kali Linux systems running on AWS.
- Display more than 100 spaces on the organization page.
- Fix incorrect EOL asset counts on the organization dashboard.
- Don't double-log failures to find SSH keys from the SSH agent in cnspec/cnquery.
- Performance improvements loading spaces and assets in the console.
- Fix tooltips for space and organization tokens to show the right messages.
- Show the GCP icon for Google Container Optimized policies.
- Use the latest Microsoft 365 logo on all integration pages.
- Add the Okta logo to the integration page.
- Fix + icon in the Okta integration to go directly to the Okta integration setup page.
- Report Kali Linux as a rolling release without an EOL date.
- Fix
cannot convert primitive with NO type informationerror ingithub.mergeRequestresource. - Update host resources to show as
Network Hostsin the console instead ofNetwork API. - Properly display
ReadOnlyPortvalue ink8s.kubelet.configurationresource when it is0. - Fix
caCertFileink8s.kubeletresource to be in "authentication" and not "authorization". - Fix URL links from cnspec failing to load if you had previously loaded a different space.
