Mondoo 11.8 is out!
🥳 Mondoo 11.8 is out! This release includes fine-grained cloud asset scanning, enhanced software inventory, Snowflake scanning, and more!
Get this release: Installation Docs | Package Downloads | Docker Container
🎉 NEW FEATURES
Fine-grained cloud asset scanning
Bring greater visibility to your cloud security posture with new fine-grained asset scanning for Azure, Google Cloud, and Mondoo-hosted AWS integrations. Mondoo now discovers and scans common cloud resources such as load balancers, virtual networks, or storage buckets as individual assets.
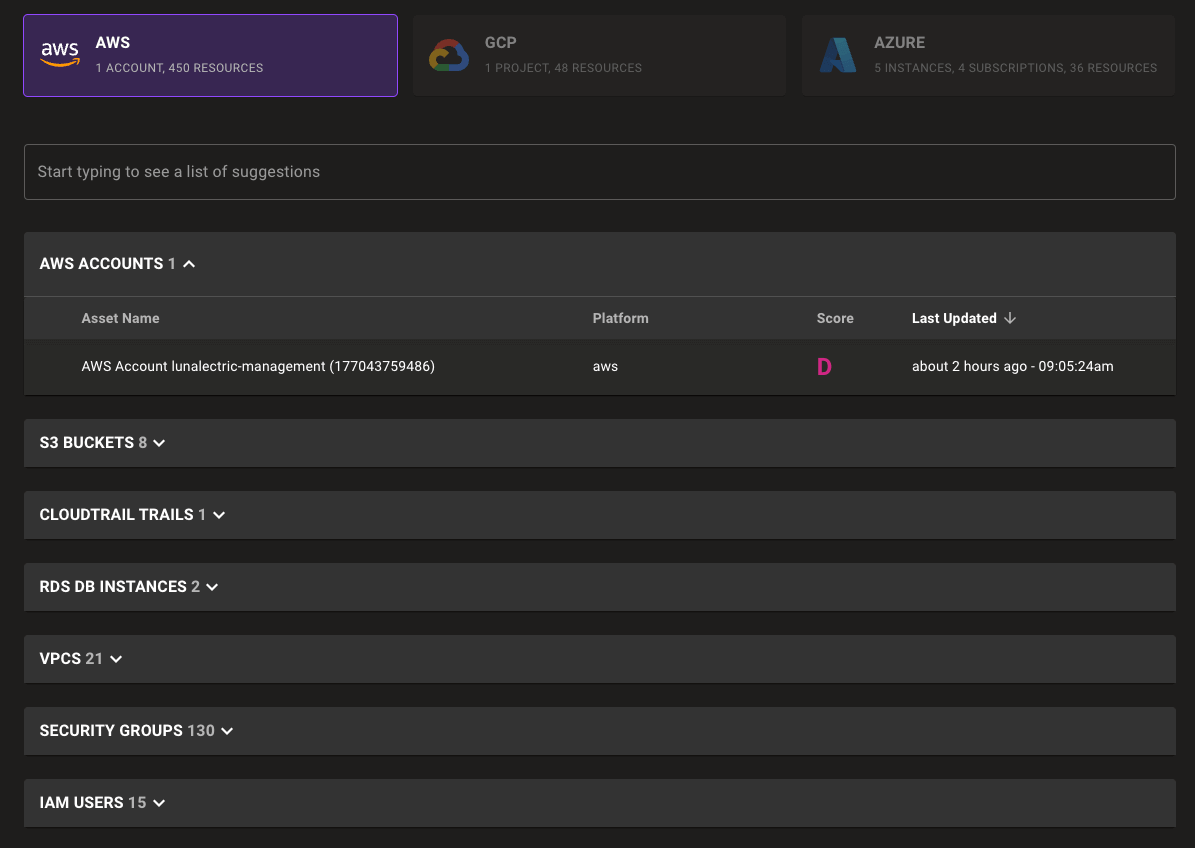
Expanded asset inventory
With fine-grained asset scanning you can quickly find and understand cloud assets across multiple providers or accounts—all within Mondoo. Search for resources by name or type using our newly expanded search capabilities.
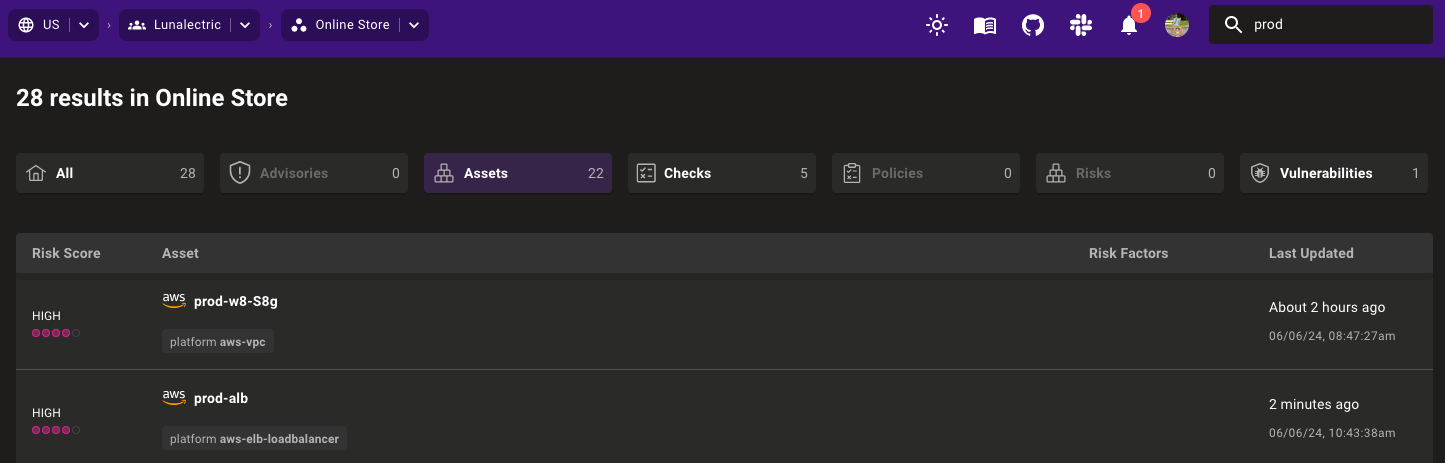
Once you've found the right asset, quickly determine the location and owner with detailed asset overview data for each asset type.
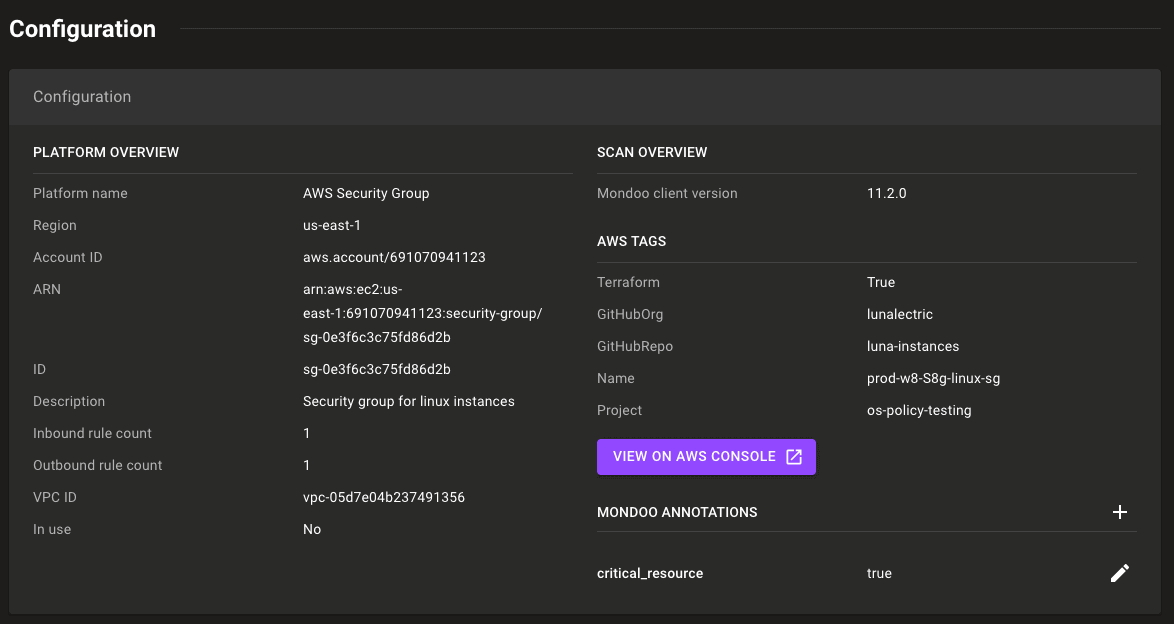
Improved security visibility
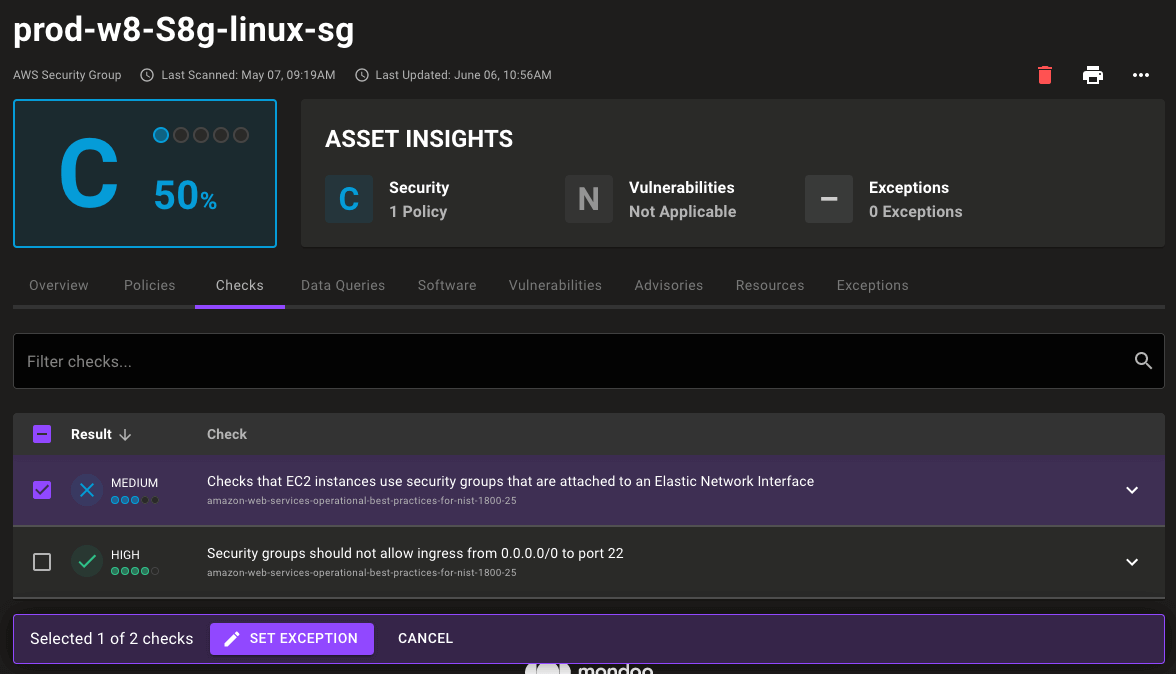
You can now understand where critical security vulnerabilities exist within your infrastructure. With checks applied directly to cloud assets, you can more easily see which assets pass and which assets fail checks without diving into complex, account-wide check output.
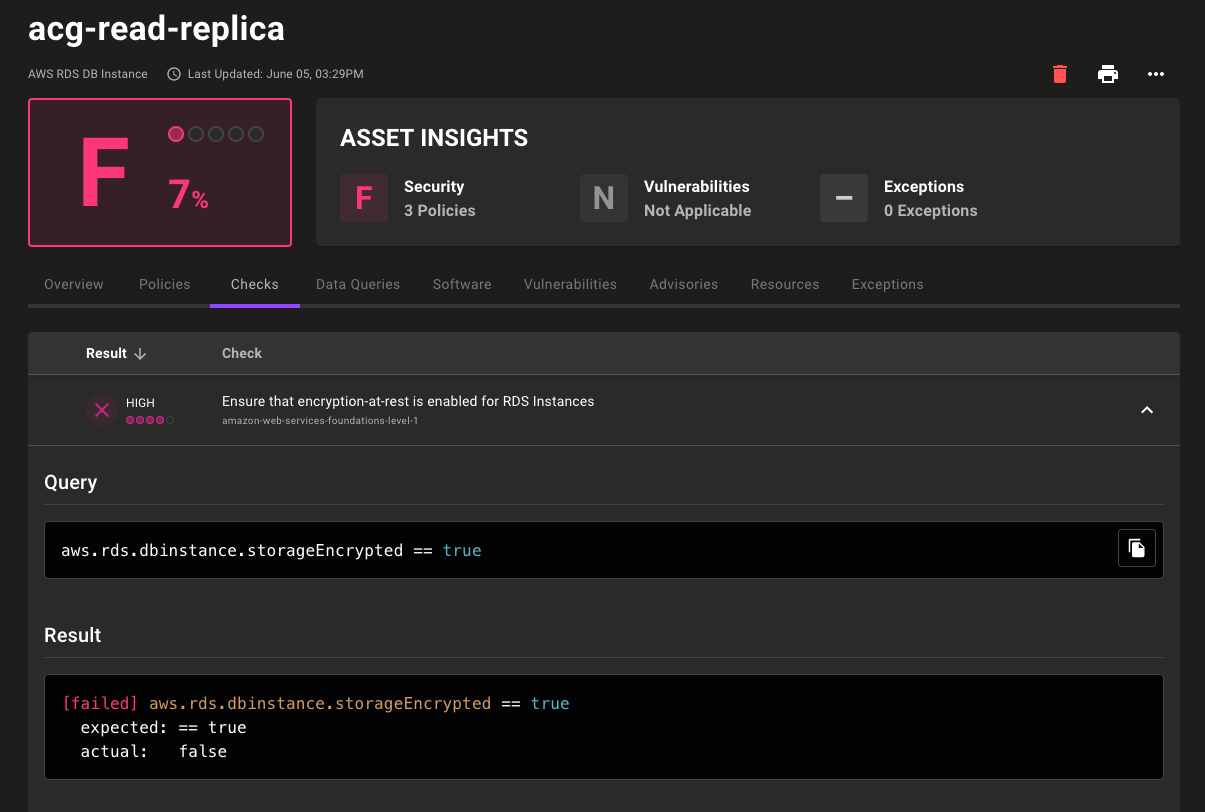
Granular exceptions
The world is full of edge cases! Now you have the granularity to account for those exceptions where necessary. With fine-grained asset scanning you can create exceptions that run on the specific cloud resources instead of on the account. This means you can disable or snooze a check without losing security visibility across your entire cloud account.
Common questions
Q: Why is one of my cloud resources not scanning as an individual asset?
A: In this initial release, Mondoo doesn't scan every type of cloud resource independently. We've begun with common resources that include security checks in CIS Level 1 policies. We will expand our scanning coverage as time goes on and as new checks are developed. If there's a resource you'd love to see scanned as an asset in Mondoo let us know at hello@mondoo.com.
Q: Will the increase in asset counts impact billing?
A: Because we believe that cost shouldn't prevent you from solving critical security findings, there is no additional charge for these assets.
Space-wide software vulnerability page
Mondoo now provides an exhaustive list of all the vulnerable software in your infrastructure. Even better, you can precisely identify risks by digging into specific versions of packages and see everywhere they're installed. This new feature also works seamlessly with Mondoo Firewatch, automatically helping you prioritize remediation using contributing risk factors such as known exploits, running processes, and open network ports.
To get started, under Vulnerabilities in the main navigation, select Software. From there, you can access the full suite of features and immediately begin improving your infrastructure's security posture.
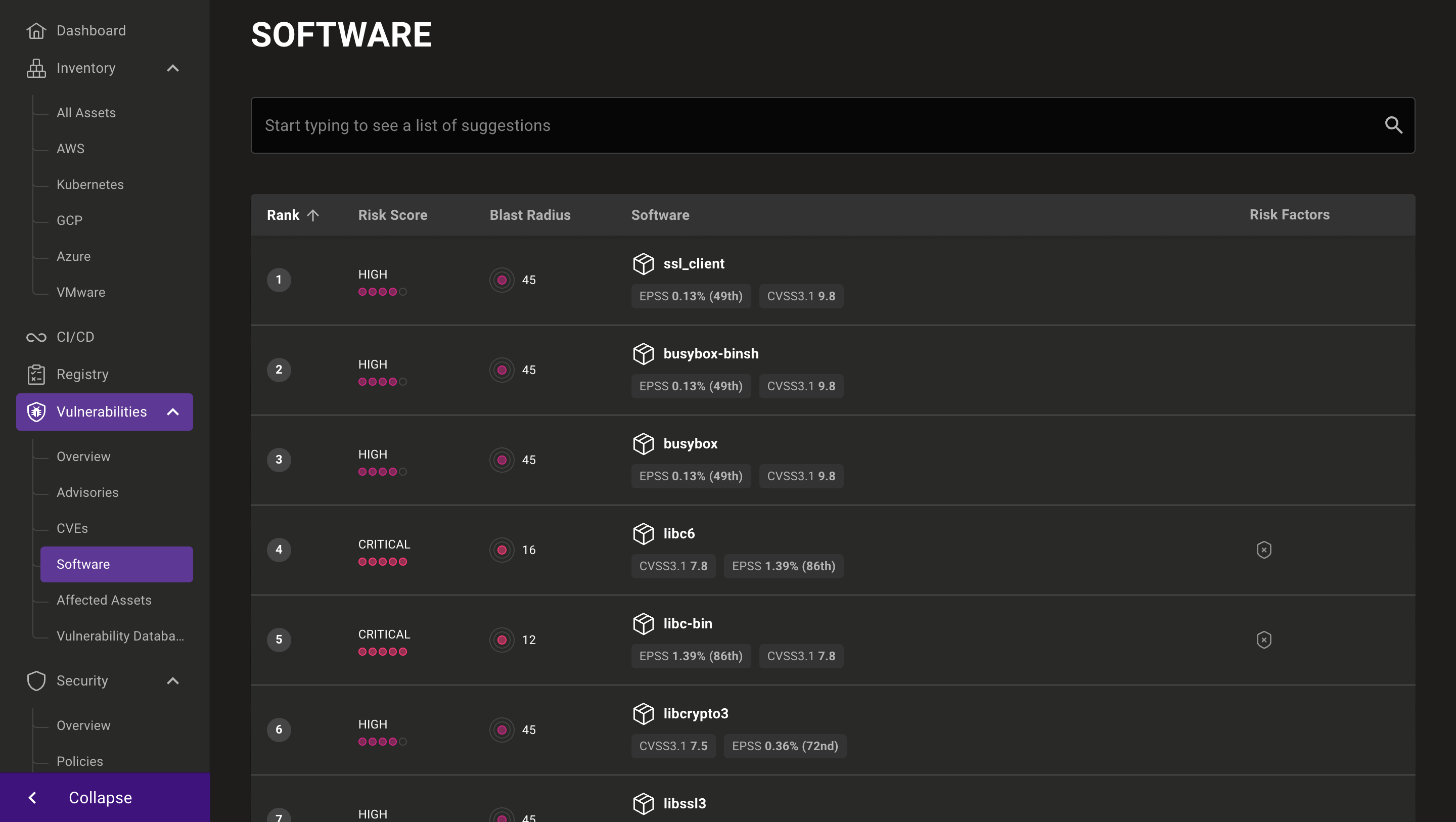
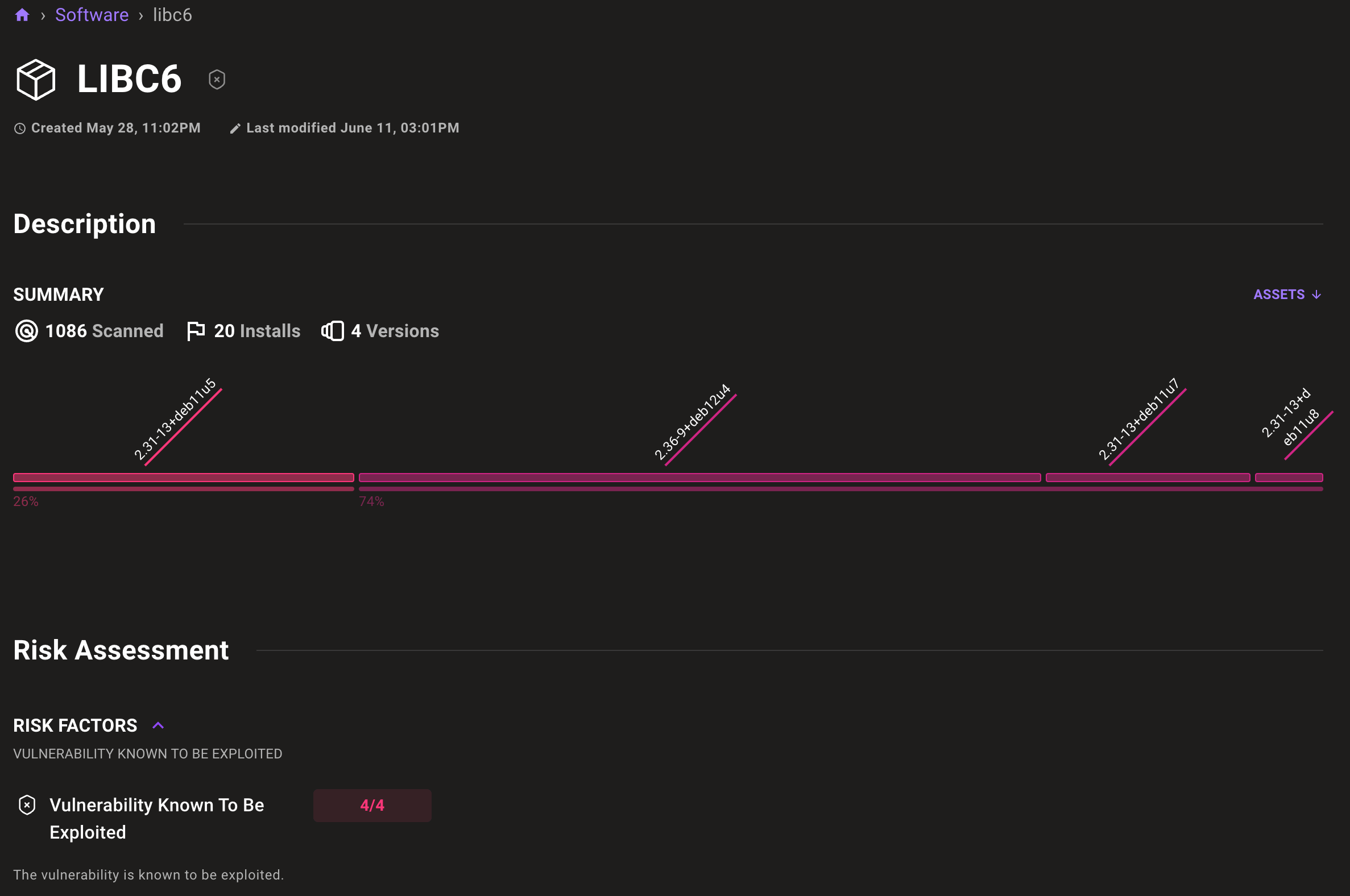
Individual software pages provide a breakdown of deployed package versions, software CVEs, risk factors, and which assets in your environment are running the particular software.
Snowflake scanning
Use the new snowflake provider in cnquery/cnspec to query and secure critical data in your Snowflake account.
cnquery shell snowflake
Required arguments:
--account- The Snowflake account name--region- The Snowflake region--user- The Snowflake username--role- The Snowflake role
Password authentication arguments:
--password- The Snowflake password--ask-pass- Prompt for the Snowflake password
shell snowflake --account zi12345 --region us-central1.gcp --user CHRIS --role ACCOUNTADMIN --ask-pass
Certificate authentication arguments:
--private-key- The path to the private key file
shell snowflake --account zi12345 --region us-central1.gcp --user CHRIS --role ACCOUNTADMIN --private-key ~/.ssh/id_rsa
You need to generate a RSA key pair and assign the public key to your user via Snowsight.
Example queries
Retrieve all users:
cnquery> snowflake.account.users
snowflake.account.users: [
0: snowflake.user name="CHRIS"
1: snowflake.user name="DATAUSER"
2: snowflake.user name="SNOWFLAKE"
]
Retrieve all users that have no MFA:
cnquery> snowflake.account.users.where(extAuthnDuo == false)
snowflake.account.users.where: [
0: snowflake.user name="CHRIS"
1: snowflake.user name="DATAUSER"
2: snowflake.user name="SNOWFLAKE"
]
Retrieve all users that have password authentication:
cnquery> snowflake.account.users.where(hasPassword)
snowflake.account.users.where: [
0: snowflake.user name="CHRIS"
1: snowflake.user name="DATAUSER"
2: snowflake.user name="SNOWFLAKE"
]
Retrieve all users that have certificate authentication:
cnquery> snowflake.account.users.where(hasRsaPublicKey)
snowflake.account.users.where: [
0: snowflake.user name="CHRIS"
]
Retrieve users that have not logged in for 30 days:
cnquery> snowflake.account.users.where(time.now - lastSuccessLogin > time.day * 30) { lastSuccessLogin }
snowflake.account.users.where: [
0: {
lastSuccessLogin: 366 days
}
]
Check that SCIM is enabled:
cnquery> snowflake.account.securityIntegrations.where(type == /SCIM/).any(enabled == true)
[failed] [].any()
actual: []
Check that the retention time is greater 90 days:
cnquery> snowflake.account.parameters.one(key == "DATA_RETENTION_TIME_IN_DAYS" && value >= 90)
Retrieve all databases:
cnquery> snowflake.account.databases
snowflake.account.databases: [
0: snowflake.database name="CNQUERY"
1: snowflake.database name="SNOWFLAKE"
2: snowflake.database name="SNOWFLAKE_SAMPLE_DATA"
]
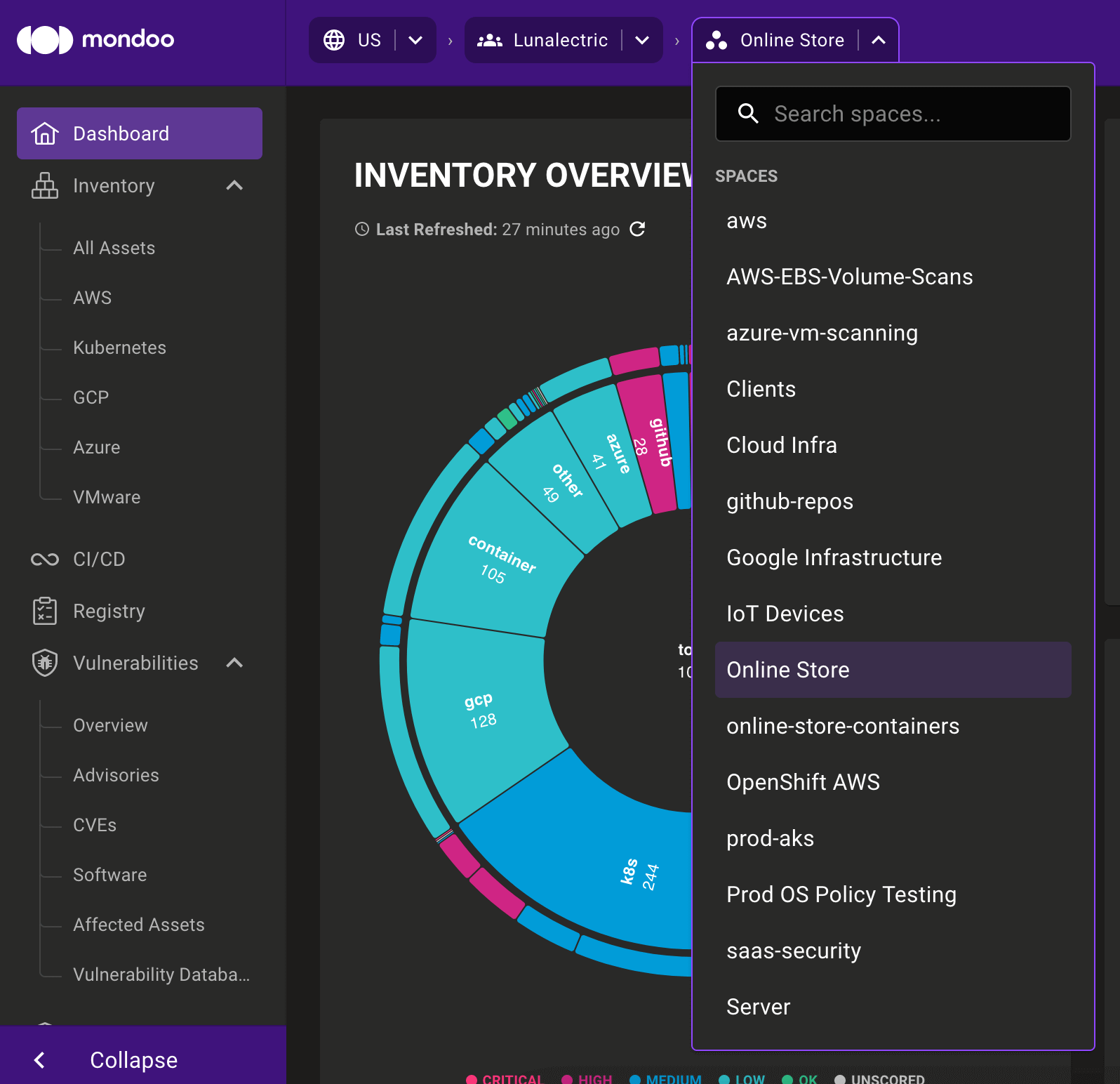
Quick space and organization navigation
Quickly navigate between different organizations or spaces with our new navigation bar. With this improved navigation tool, you can:
- Search for organizations or spaces within the drop-down menus
- Choose a space without accessing an organization's Spaces page
🧹 IMPROVEMENTS
New risk factors for critical Windows systems
Expose vulnerabilities and misconfigurations on the most important Windows systems in your environment with new risk factors for assets running Microsoft SQL Server or IIS.
Resource updates
aws.applicationautoscaling.target
- New
createdAtfield
aws.ec2.image
- New
deprecatedAtfield
🐛 BUG FIXES AND UPDATES
- Fix a type error querying data from the
aws.ecs.taskresource. - When a policy on an asset is in preview, display it in gray on the asset page.
- Show the correct Microsoft icon on the Mondoo Console login page.
- Fix the display of priority chart totals in light mode.
- Improve rendering of priority chart tooltips with large names.
- Fix the tooltip for the priority chart sometimes displaying in the top left of the screen.
- Expand Linux policies to support PowerPC and ARM based systems.
- Improve icons on the workstation setup page.
- Allow updating the Mondoo-hosted AWS integration without re-entering credentials.
- Improve policy score calculations when some policies are in preview.
- Display the correct VPC icon in the AWS integration overview.
- Improve the AWS integration page's Type column to distinguish between organization and single account integrations.
- Improve the performance of Azure VM scanning.
- Add a log entry to the Azure integration when a stopped VM skips during scans.
- Add missing
resolved_onCVE data in S3 exports. - Improve detection of the latest VMware CVEs.
- Avoid rendering the entire page when switching between spaces.
- Improve rendering of text on the "Welcome to Mondoo" that displays when new spaces are created.
- Improve the reliability of the Kubernetes Workload and Cluster Security policy's "Container image pull should be consistent" check.
