Mondoo 8.7 is out!
· 3 min read
🥳 Mondoo 8.7 is out! This release includes public report viewing, improved policy filtering, and more!
Get this release: Installation Docs | Package Downloads | Docker Container
🎉 NEW FEATURES
Public report viewing in cnspec
Open source users: Want to scan your infrastructure with cnspec and instantly see a visual report on the results? Now you can! Upload scan results to mondoo.com. For 72 hours, you can view the graphical report is available to view and share with anyone.
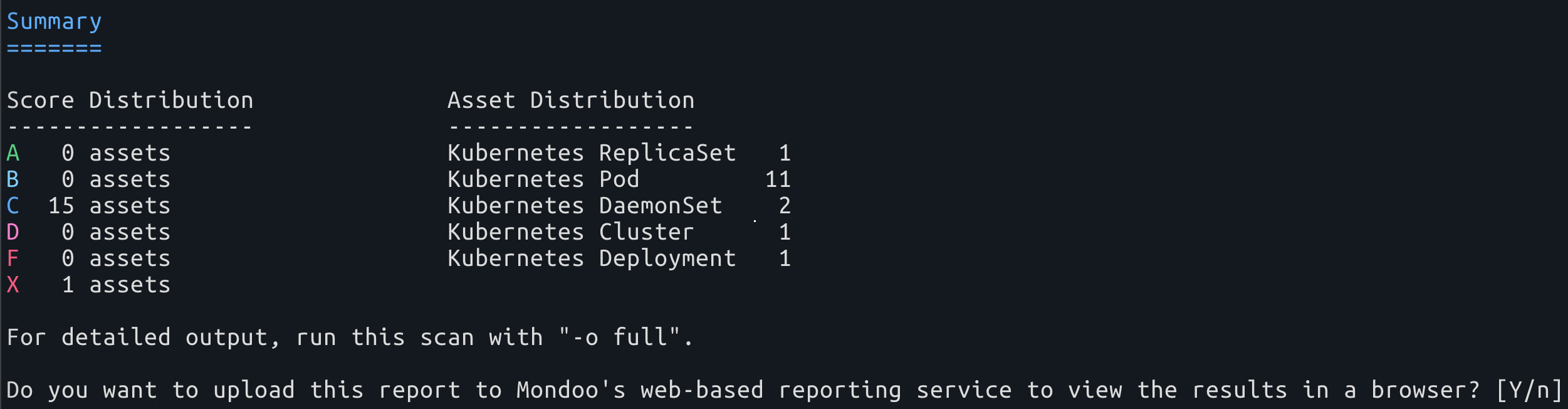
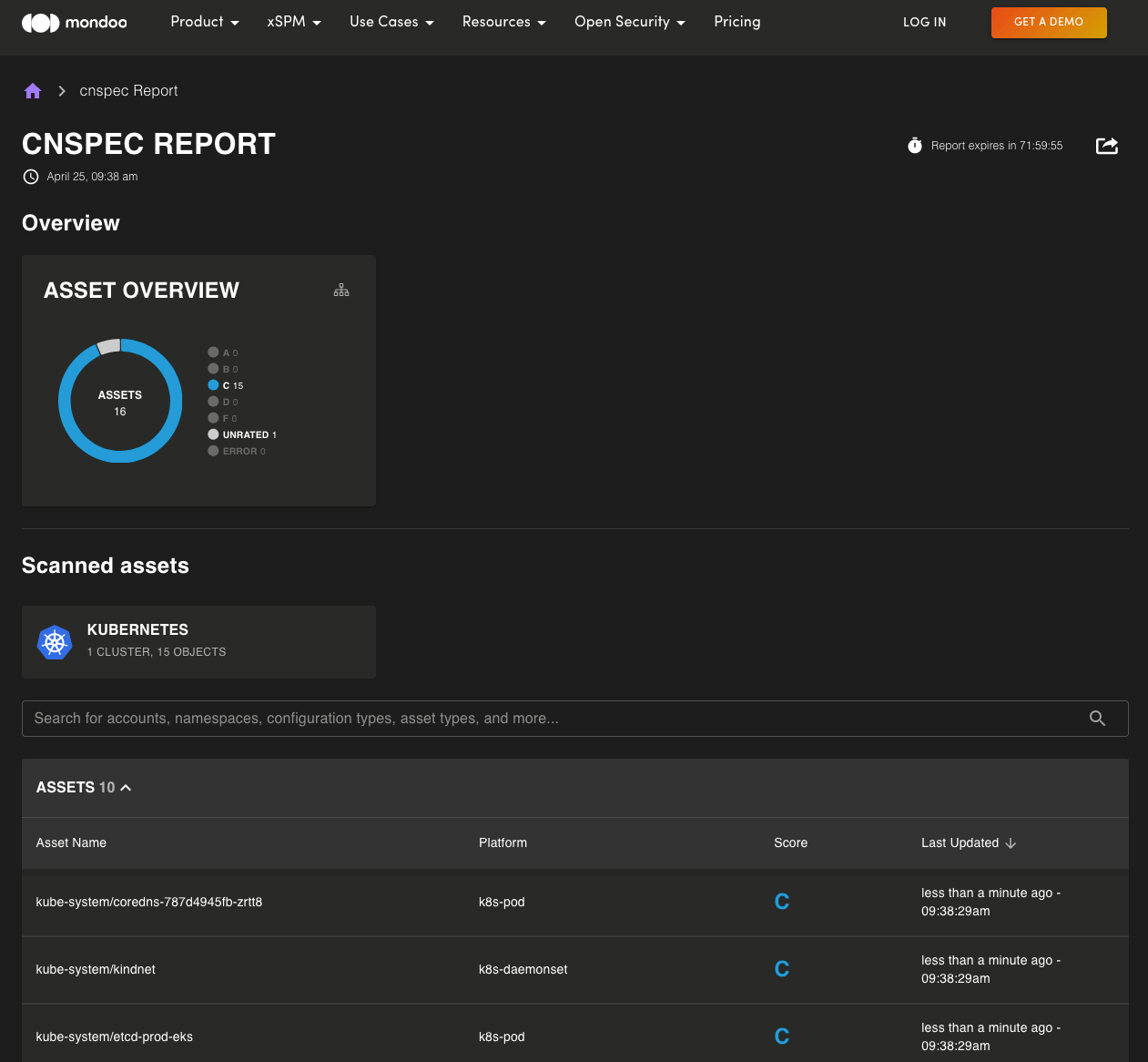
Want reports for longer than 72 hours? Register your cnspec installation with Mondoo Platform for reports that never expire, asset relationships, security planning, regression alerting, and more.
🧹 IMPROVEMENTS
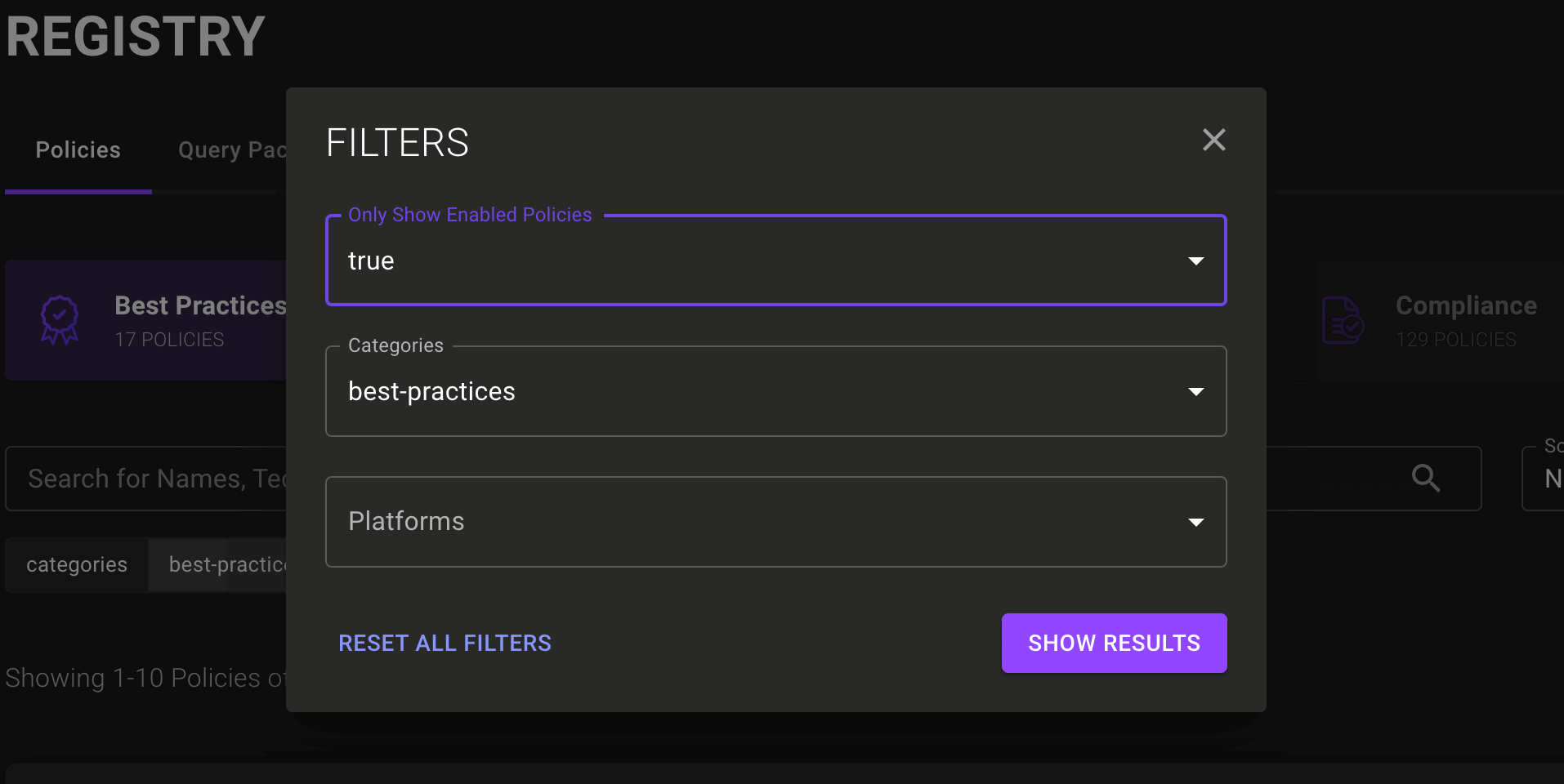
Filter on enabled policies
Filtering in the registry now lets you show only policies that are enabled in the space.
🐛 BUG FIXES AND UPDATES
- Fix
--asset-nameflag not setting a custom asset name for all asset types. - Fix failure gathering data in the
azure.subscription.network.ipAddressresource. - Add missing default resource values to
gcp.project.bigqueryServiceandgcp.project.bigqueryService.dataset.accessEntry. - Add a more user-friendly error message when an unauthenticated client attempts to query CVE or EOL platform data.
- Add a more user-friendly status error message when cnquery/cnspec receive invalid credentials.
- Provide an error message in the
ms365provider when the certificate is malformed. - Set the
ms365provider's--client-idand--tenant-idcommand line flags as required. - Be clear in help that the
ms365provider allows for both PKCS #12/PFX and PEM format certificates. - Fix false negatives in the Google Cloud (GCP) Security policy's
Ensure that Cloud Storage buckets have uniform bucket-level access enabledcheck. - Update the Linux Security policy's
Ensure SSH root login is disabled or set to prohibit-passwordcheck to detect additional methods of preventing password-based logins from the root user. - Display values in nested arrays such as
aws.ec2.securityGroups[1].ipPermissions[0]in the Asset Resource Explorer. - Display field-only queries such as
github.repository.license.spdxIdin the Asset Resource Explorer. - Fix display of queries with multiple nested resources such as
gcp.project.bigquery.datasets {*}in the Asset Resource Explorer. - Don't count fixed CVEs in the Organization dashboard.
- Group
k8s-ingressassets underK8s Ingressin the fleet view instead ofOthers. - Fix the display of policies with variants in the registry.
- Fix a page load error when selecting CVE lists in the organization overview.
- Fix a failure displaying CVE data on an asset.
- Fix editing of properties in variant policies.
- Allow deleting private policies in the registry.
- Resize data display in the Asset Resource Explorer to make it easier to get back to resource navigation.
- Fix vendor advisories to list all included CVEs.
- Allow re-scheduling integration scans and exports after a failure.
