Mondoo 9.12 is out!
🥳 Mondoo 9.12 is out! This release includes improved asset UX, expanded AWS/M365 resources, and more!
Get this release: Installation Docs | Package Downloads | Docker Container
🎉 NEW FEATURES
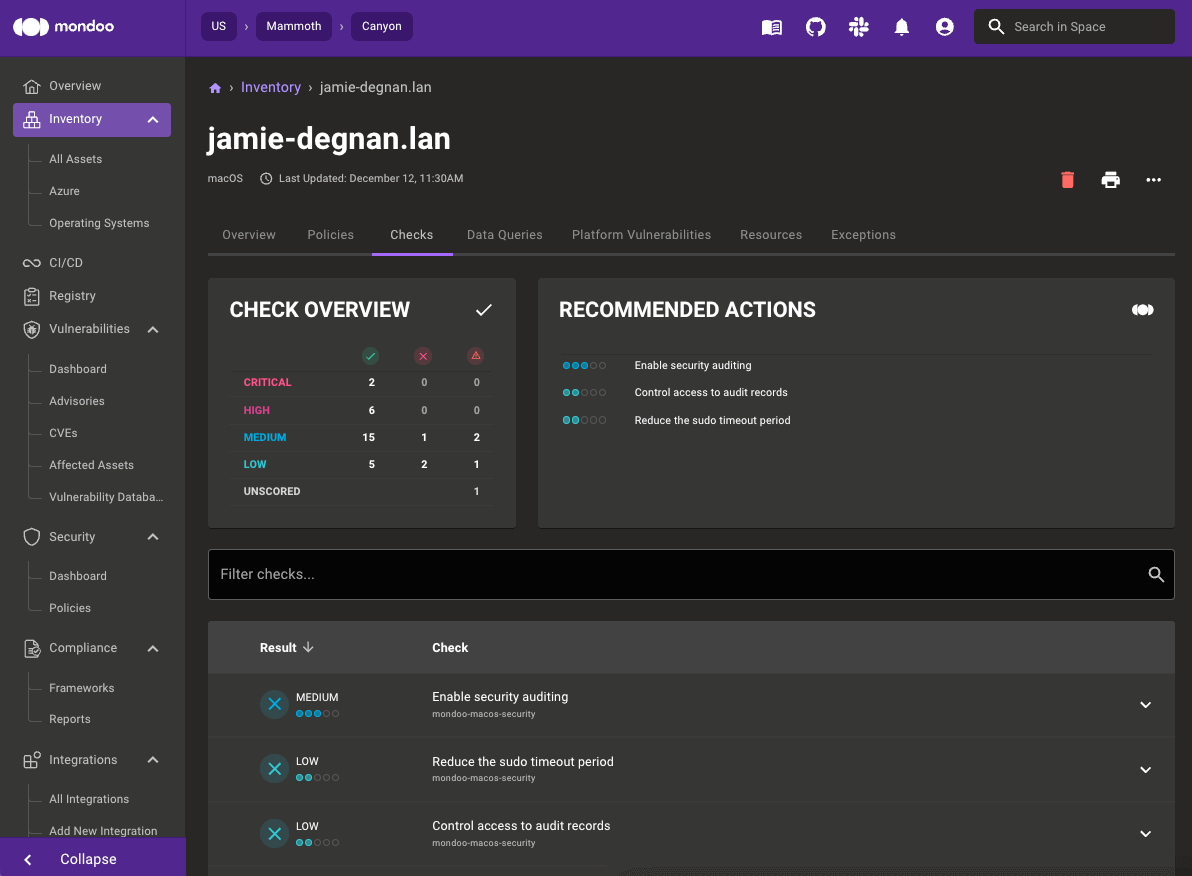
Check overview summary information
We added an overview to the Checks tab for each of your assets. Now you can quickly grasp the state of checks and see the most important recommended actions.
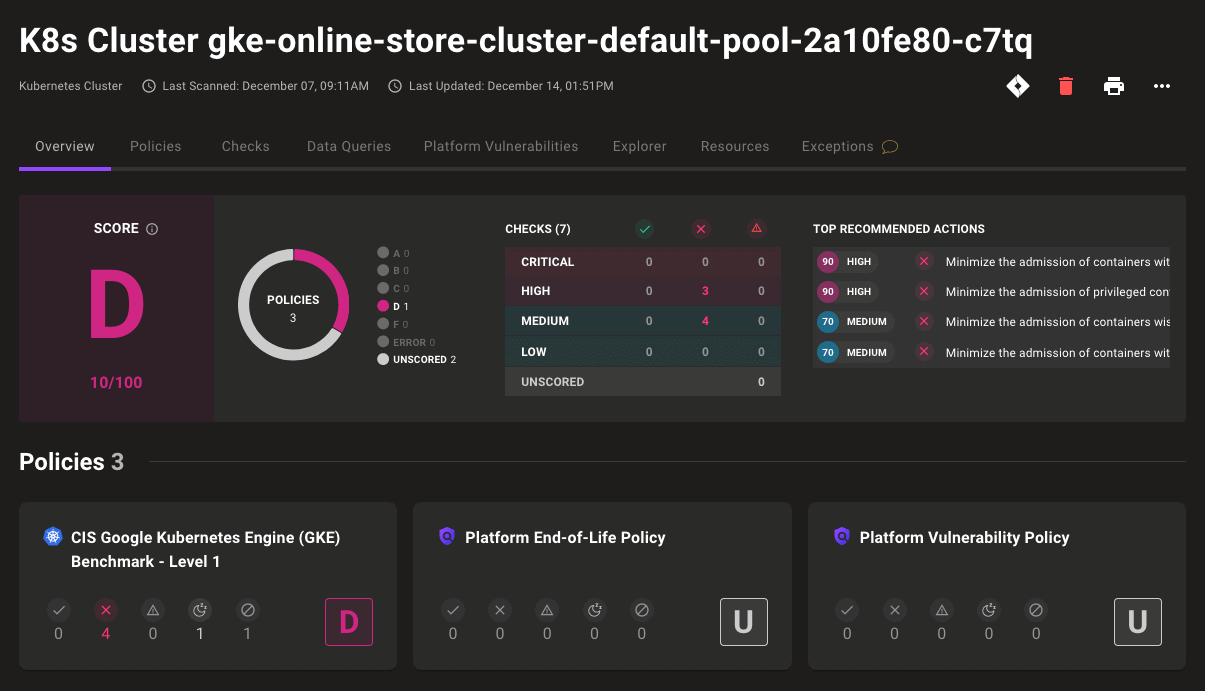
View exceptions on policy cards
New information on the Overview tab for each asset exposes exceptions at a glance. For each policy applied to the asset, you can now see whether (and how many) exceptions are applied.
🧹 IMPROVEMENTS
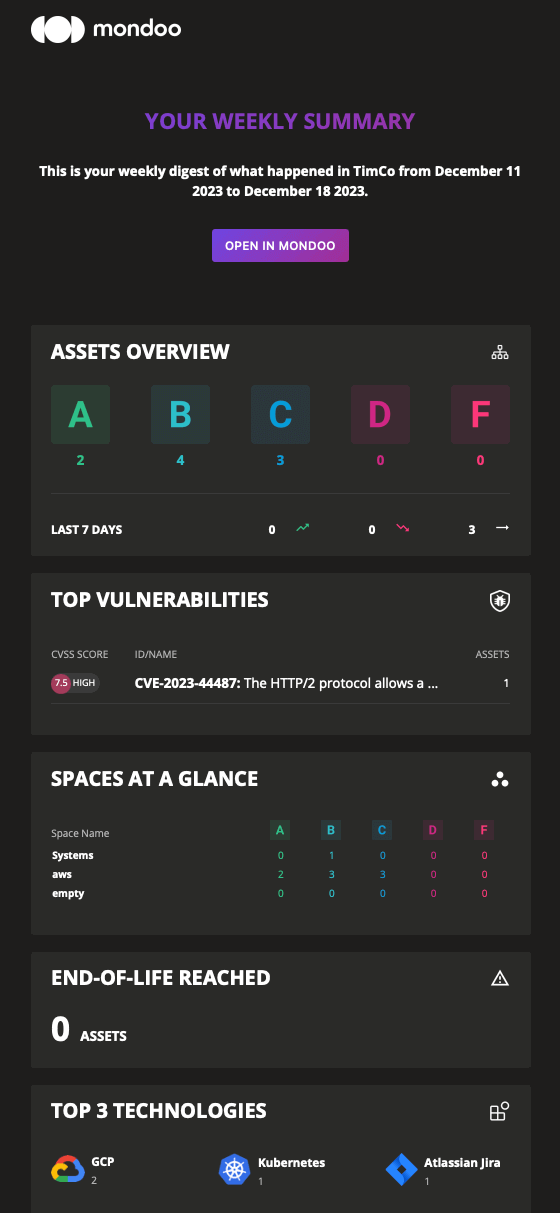
Updated weekly email notifications
We rebuilt the Mondoo weekly organization overview emails from the ground up to deliver the most important information about your spaces... and with a fresh new design to top it all off. The email still shows an overview of scores in your spaces, but now also includes top vulnerabilities, end-of-life assets, and a count of improving vs. worsening asset scores.
New fields and defaults in resources
aws.acm.certificate
- Default fields now display
domainName,issuer,createdAt, andnotAfter - New
keyAlgorithmfield - New
serialfield - New
sourcefield - New
issuerfield - New
issuedAtfield - New
importedAtfield
aws.dynamodb.table
- New
statusfield - New
sizeBytesfield
aws.ec2.keypair
- Default fields now display
name,type, andregion - New
createdAtfield
aws.rds.dbcluster
- New
storageEncryptedfield - New
storageAllocatedfield - New
storageIopsfield - New
storageTypefield - New
statusfield - New
createdTimefield - New
backupRetentionPeriodfield - New
autoMinorVersionUpgradefield - New
clusterDbInstanceClassfield - New
enginefield - New
engineVersionfield - New
publiclyAccessiblefield - New
multiAZfield - New
deletionProtectionfield
aws.rds.snapshot
- New
enginefield - New
statusfield - New
allocatedStoragefield
aws.vpc.endpoint
- New
privateDnsEnabledfield - New
statefield - New
createdAtfield
aws.vpc.flowlog
- New
createdAtfield - New
destinationfield - New
maxAggregationIntervalfield - New
trafficTypefield
aws.vpc.routetable
- New
tagsfield
aws.vpc.subnet
- New
assignIpv6AddressOnCreationfield - New
statefield
github.user
- Default fields now display
login,name,email, and company
microsoft.group
- New
visibilityfield
ms365.exchangeonline
- New
externalInOutlookfield
ms365.exchangeonline.externalsender
- New resource with
identity,allowList, andenabledfields
ms365.teams.teamsmeetingpolicyconfig
- New resource with
allowAnonymousUsersToJoinMeeting,allowAnonymousUsersToStartMeeting,autoAdmittedUsers,allowPSTNUsersToBypassLobby,meetingChatEnabledType,designatedPresenterRoleMode,allowExternalParticipantGiveRequestControl, andallowSecurityEndUserReportingfields
ms365.teams.tenantfederationconfig
- New resource with
identity,blockedDomains,allowFederatedUsers,allowPublicUsers,allowTeamsConsumer,allowTeamsConsumerInbound,treatDiscoveredPartnersAsUnverified,sharedSipAddressSpace, andrestrictTeamsConsumerToExternalUserProfilesfields
microsoft.organization
- New
onPremisesSyncEnabledfield
slack.conversation
- A new resource that simplifies accessing channel, direct message, and group message data. This replaces the
conversationsfield in theslackresource.
German/Italian support in Windows Security policy
We've reworked our Windows Security policy to fully support both Windows Server and Workstation editions with the language set to either German or Italian.
New checks in HTTP Security policy
Our HTTP security policy now includes additional checks to ensure that Content Security Policy (CSP) and Strict-Transport-Security (HSTS) headers are set. New groups in this policy ensure that checks are grouped by protocol and only enabled when appropriate.
Complete Microsoft 365 scanning, anywhere
Sit back for a moment while I put on my engineer's hat. Sometimes, APIs are hard. Perhaps the best example is Microsoft 365. Some data can be retrieved using their Golang SDK, but much of the API can only be accessed through PowerShell.
Until now, Mondoo queried the necessary data using both methods and returned MQL as if it were easy—that is—if you were on Windows with PowerShell. On Linux, macOS, or using a Mondoo integration, queries that relied on PowerShell-gathered data failed.
But no more! cnquery and cnspec now query Microsoft 365 data using PowerShell installed on macOS / Linux systems so that Mondoo Platform integrations now successfully run these queries.
🐛 BUG FIXES AND UPDATES
- Don't allow creating an exception for a control/asset/check more than once.
- Resolve multiple edge cases in multi-select when setting up exceptions.
- Improve the rendering of code blocks in the console.
- Improve performance loading pages in the console.
- Add validation of IP addresses in the Domain/IP integration.
- Don't remove previously rejected exceptions when removing the current exception.
- Fix detecting platform IDs for Kubernetes operator manifests.
- Reduce network traffic when scanning assets with cnspec.
- Fix failures setting sudo to active in an inventory file.
- Add API retries to the Slack resources to better handle throttling while querying large amounts of data.
- Improve the suggestion text when checks, assets, or data queries tabs are empty in Compliance Hub.
- Fix failures running
cnspec vuln. - Add back the feature flag for Kubernetes node scanning that was accidentally removed in the 9.0 release.
