Mondoo 9.7 is out!
🥳 Mondoo 9.7 is out! This release includes a new compliance UI, expanded resources, and even more CVE data!
Get this release: Installation Docs | Package Downloads | Docker Container
🎉 NEW FEATURES
New compliance exceptions UI
We've reworked the compliance exceptions system to make it easier to understand when exceptions have been set and what that means for your compliance data collection.
Each control includes a new Set Exception button so you can quickly create exceptions directly from framework control pages.
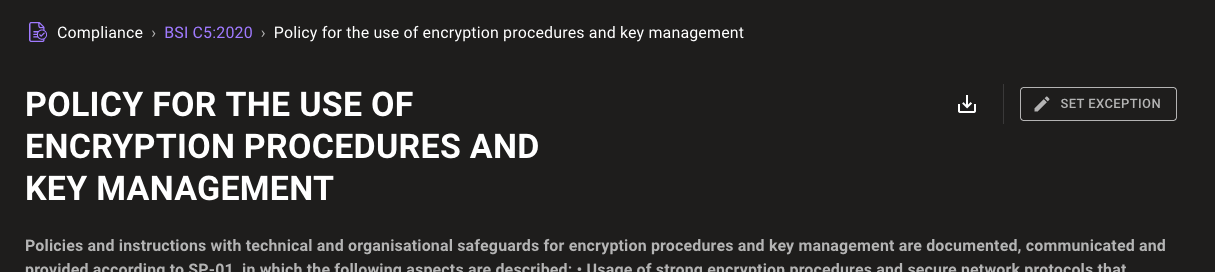
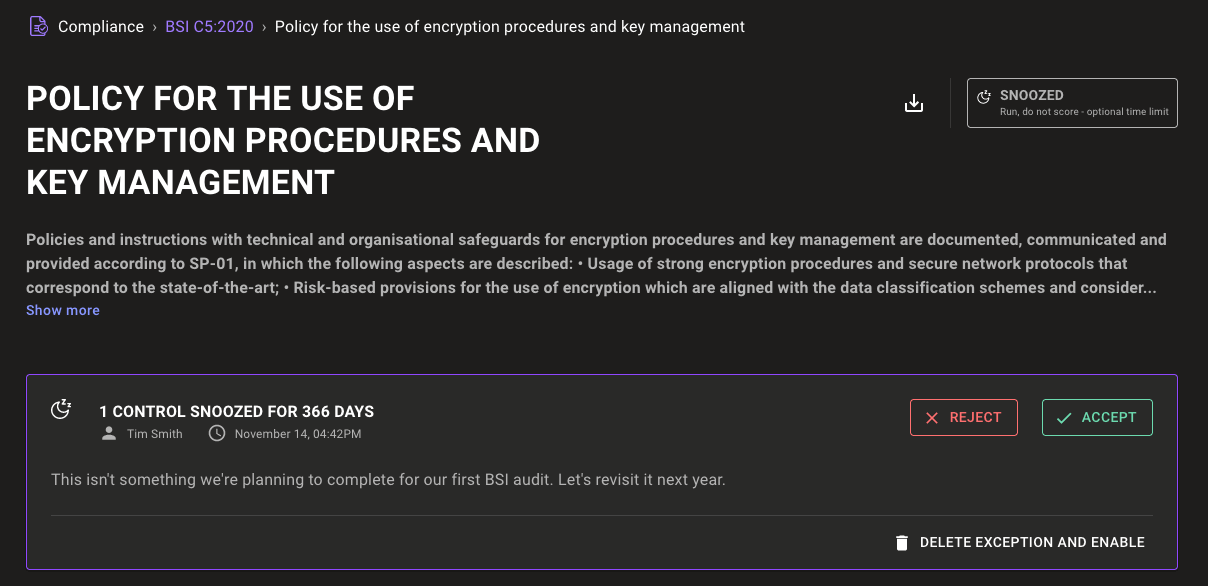
For controls with an exception set, the UI now communicates which type of exception has been set: snooze or disable. It gives a quick description of how the exception affects compliance data collection. The details of the exception are also shown directly on the control page, allowing you to accept, reject, or delete the exception without needing to dig through the exceptions tab.
Run local query packs from cnspec
Want to quickly test a custom query pack you've written? Now it's easier than ever because you can run a local query pack directly from cnspec:
cnspec scan -f example-pack.mql.yaml
→ no provider specified, defaulting to local. Use --help to see all providers.
→ loaded configuration from /Users/tsmith/.config/mondoo/mondoo.yml using source default
→ using service account credentials
→ discover related assets for 1 asset(s)
Asset: Luna-Laptop.local
----------------------
Data queries:
packages.where.list: [
0: package name="ssh" version=""
]
services.where.list: [
0: service name="com.openssh.ssh-agent" running=true enabled=true type="launchd"
]
sshd.config.params: {
AcceptEnv: "LANG LC_*"
AuthorizedKeysFile: ".ssh/authorized_keys"
Subsystem: "sftp /usr/libexec/sftp-server"
UsePAM: "yes"
}
Scanned 1 asset
macOS
U Luna-Laptop.local
🧹 IMPROVEMENTS
Atlassian asset grouping
Atlassian admin, Jira, Confluence, and SCM assets scanned with cnspec are now grouped as Atlassian assets in the console. This helps you quickly find all your Atlassian assets.
Ubuntu 23.10 EOL/CVE detection
Ubuntu 23.10 is out, and Mondoo is ready with EOL reporting and CVE detection now available for this latest Ubuntu release. See our blog post What's New in Security for Ubuntu 23.10 to learn more about this release's great new security features.
Raspbian 11 and 12 CVE detection
cnspec scans on Raspbian 11.x and 12.x releases now include important CVE data on both the CLI and in the console, so you can keep your Raspberry Pi hobby and IoT projects secure.
Better application of CIS Distribution Independent Linux Benchmark policy
The CIS Distribution Independent Linux Benchmark policy is a fantastic alternative Linux security policy to use when your operating system distribution or specific version is not supported by one of the main CIS Linux benchmarks. Thanks to new filters, you can now apply this policy in any space and rest assured it will only apply to systems for which more specific CIS benchmark policies aren't available. This means that now you can always have security and compliance data available, even when you're running distros that are a bit off the beaten path, such as non-LTS Ubuntu releases, Arch Linux, or Raspbian.
New AWS resource fields
AWS resources include new default values to improve data pack queries and navigation in the cnquery/cnspec shell. The resources also have many new fields to expose valuable asset inventory data:
- enabled
- httpVersion
- isIPV6Enabled
- priceClass
- createdAt
- deletionProtectionEnabled
- globalTableVersion
- id
- createdAt
- lastResourceAnalyzed
- lastResourceAnalyzedAt
- region
- createdAt
- encryptionKeyArn
- locked
- region
🐛 BUG FIXES AND UPDATES
- Ensure asset groups display correctly as new assets are added or deleted.
- Show the correct status badges on the Managed Clients page.
- Fix incorrect EBS volume scan regions.
- Fix a failure to display asset scores for EBS volume scans.
- Add the ability to list processes on Windows systems in the
ports.listeningresource. - Fix EKS node checks not correctly executing in the CIS Amazon Elastic Kubernetes Service (EKS) Benchmark policies.
- Improve reliability of checks within the CIS Amazon Elastic Kubernetes Service (EKS) Benchmark policies.
- Fix failures in CIS macOS Benchmark policies' "Ensure Pop-up Windows Are Blocked" and "Ensure Show Status Bar Is Enabled" checks.
- Fix VMware vSphere CVE detection with cnspec 8.x clients.
- Return a 100 (A) score when no CVEs are detected on a system.
- Fix CIS rsyslog checks to fail instead of erroring when the rsyslog config is not found.
- Improve chrony configuration detection in the Operational Best Practices for Time Synchronization policy.
- Better detect when journald is running in the
Ensure journald is not configured to receive logs from a remote clientcheck. - Improve titles of queries in multiple query packs.
- Fix failures in some JSON data exports due to malformed JSON data.
- Fix failures detecting the platform on some remote scans.
- Improve shell help content for many resources.
