Mondoo 10.6 is out!
🥳 Mondoo 10.6 is out! This release includes a new EDR policy, policy filtering, additional MQL capabilities, and more!
Get this release: Installation Docs | Package Downloads | Docker Container
🎉 NEW FEATURES
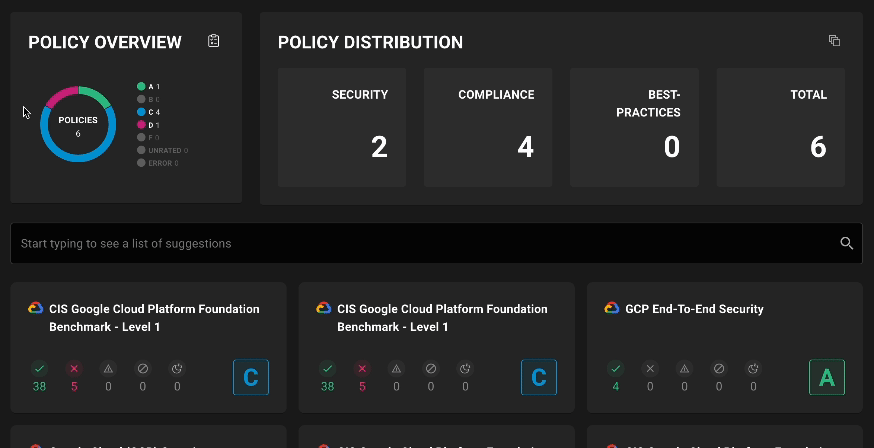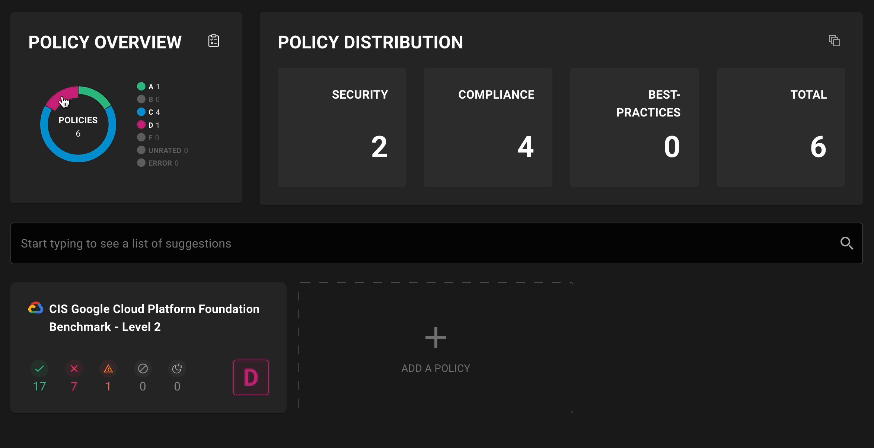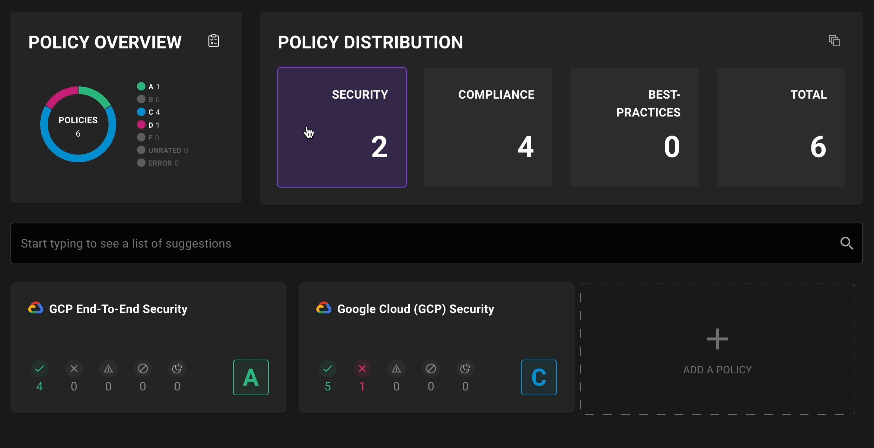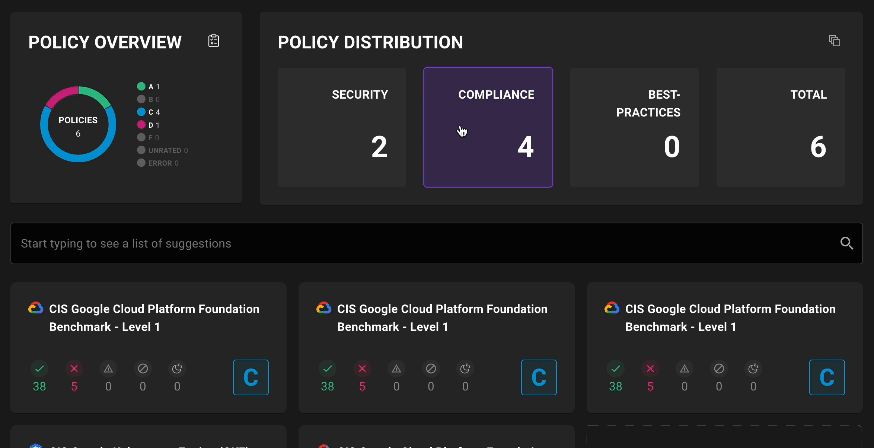
Filter policies on assets
Asset policy pages now include filtering by policy types and scores so you can see exactly what policies are applied and where failures are occurring.
Data type conversion MQL helpers
New MQL helpers allow you to quickly convert data to the right format for your custom checks and data queries.
> int(1.23)
1
> bool(1)
true
> float(12)
12
> string(1.89)
"1.89"
> regex("w.r.d") == "world 🌎"
/w.r.d/
Endpoint detection and response (EDR) policy
Ensure critical employee endpoints have endpoint detection and response (EDR) software installed and running with our new Endpoint Detection and Response (EDR) policy. This policy checks to see if SentinelOne or CrowdStrike are installed on macOS, Linux, and Windows systems.
Open source Mondoo documentation
Do typos in documentation keep you up at night like they do for me? We open sourced our documentation so you can fix that problem and get some sleep.
Check out our new public repo at github.com/mondoohq/docs for instructions on how to contribute fixes and improvements.
🧹 IMPROVEMENTS
Resource improvements
aws.cloudtrail.trails
- Add support for advanced selectors in the
eventSelectorsfield.
aws.config
- Add new
deliveryChannelsfield.
aws.config.deliverychannel
- Add a new resource with fields representing an individual AWS Config delivery channel configured within an account.
aws.iam.role
- Add new
assumeRolePolicyDocumentfield.
package
- Add new
originVersionfield on Debian Linux-based assets. - Include version data in the
originfield for source packages on Debian Linux-based assets.
Filter AWS scans by region
Filter cnspec command line scans by AWS region with new filter options:
cnspec scan aws --filters all:region=us-east-2
cnspec scan aws --filters region=us-east-2
cnspec scan aws --filters ec2:region=us-east-2
Thanks for this great contribution @montera82!
Updated policy check impact scores
Prioritize the most important checks first with newly adjusted check priorities for CIS Linux distribution policies. These improved scores ensure that only the most important checks are listed as failures, so you can more easily prioritize critical work.
Improved AWS policies
Both the CIS AWS Foundations benchmark policy and the various AWS Best Practices policies have seen major refactoring. These changes include improved queries and result output as well as new descriptions and remediation data. Stay tuned for more updates as we refactor all queries in these policies to use the latest MQL resources and helpers.
🐛 BUG FIXES AND UPDATES
- Improve reliability of fetching CVE data for assets.
- Only show unresolved CVEs in the asset CVE list.
- Fix package CVE false positives for some Debian packages.
- Fix CVEs not showing after the first asset scan.
- Fix failures scanning a GitHub organization if the supplied token cannot access all repositories.
- Only show the options to add new integrations when the user has the appropriate permissions for the space.
- Change documentation links in the console to go directly to Mondoo Platform documentation.
- Improve how space owners are listed in the Organization dashboard's CVE list.
- Fix policy recommendations during the Kubernetes integration setup.
- Show EPSS scores with a single decimal point in all locations.
- Don't fail scanning if the location of an S3 bucket cannot be determined.
- Return more than 100 Microsoft 365 users in queries.
- Improve output of the "Ensure macOS is up to date" check in the macOS Security policy.
- Distinguish between domain controllers and member servers in Windows Security policy checks.
- Improve empty states for software, CVE, and advisory asset page tabs.
- Improve rendering of columns in the asset page's Advisories tab.
- Enforce a max session time of 1 day in the console for added security.
- Don't include the legacy Platform Vulnerability Policy in asset policy counts.
- Improve wrapping of long asset names on narrow screens.
- Don't include "unknown" integrations in the organization dashboard integrations list.
- Add missing impact scores to the CIS AIX benchmark policies.
