Mondoo 8.26 is out!
🥳 Mondoo 8.26 is out! This release includes OCI asset configuration data, improved Compliance Hub results, and more!
Get this release: Installation Docs | Package Downloads | Docker Container
🎉 NEW FEATURES
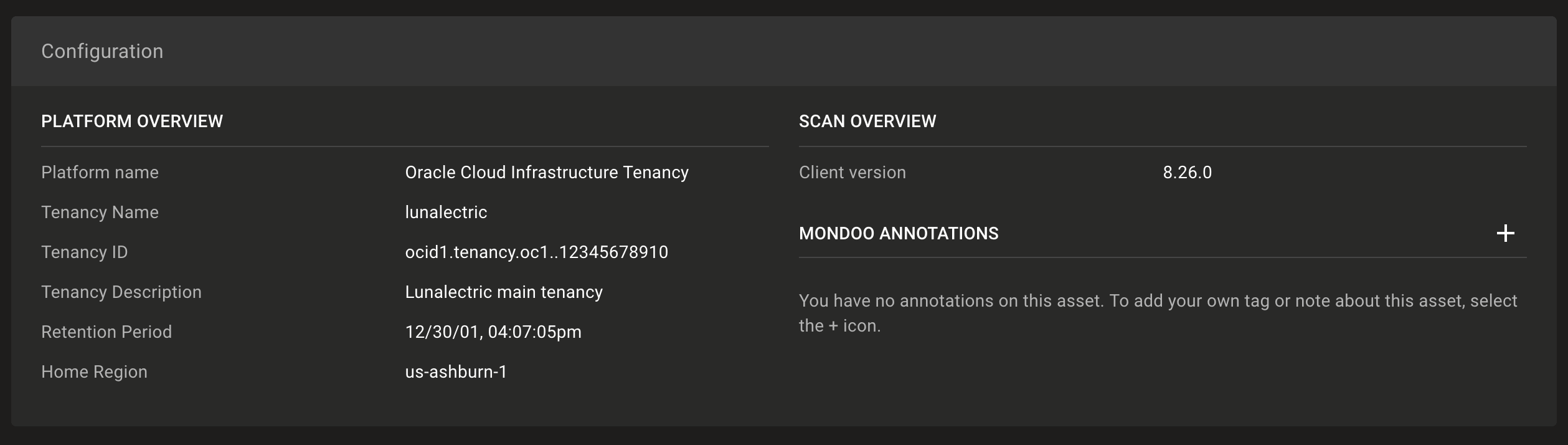
OCI asset configuration overview data
Mondoo now shows configuration data for Oracle Cloud Infrastructure (OCI) Tenancies.
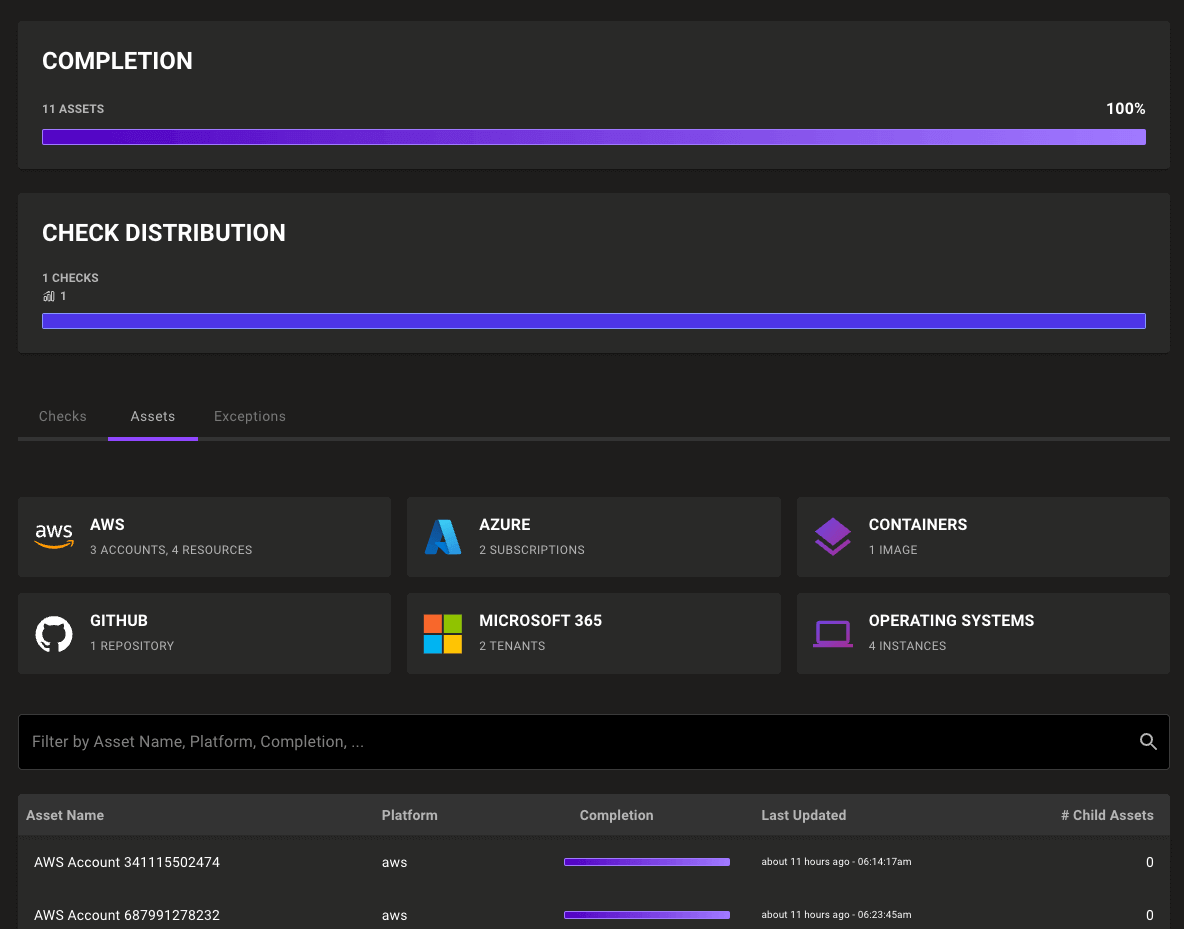
Filter compliance results by asset type
Compliance Hub now has buttons that let you quickly filter compliance assets by platform type. Because these group buttons in the fleet view were so helpful to users, we added them to compliance as well.
🧹 IMPROVEMENTS
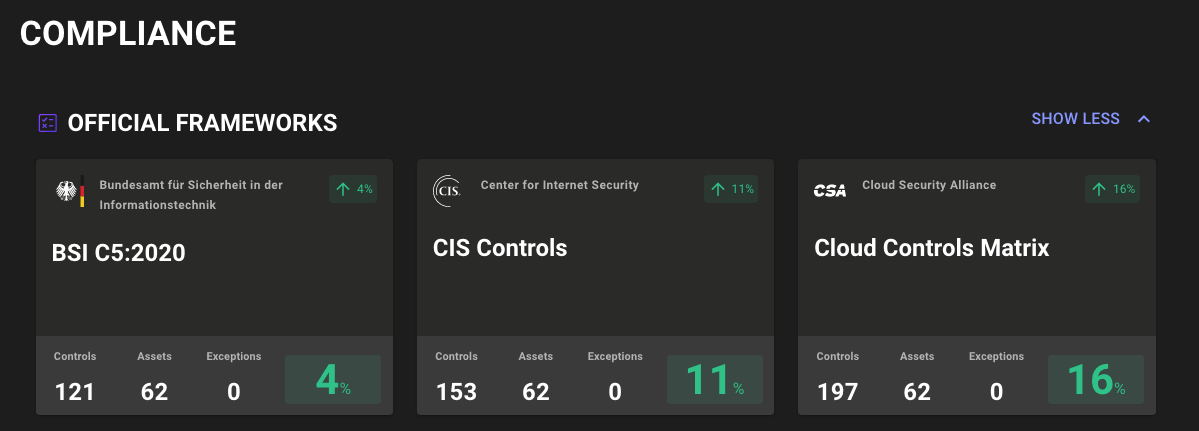
Improved Compliance Hub framework completion calculations
When we set out to build Compliance Hub, we wanted to enable teams to quickly asses their compliance posture and track progress as they worked to secure systems and services. After launching Compliance Hub, we received insightful feedback from our users. Based on that feedback, this week we've improved how we report progress towards compliance completion.
Previously we calculated a space's compliance completion by the percentage of all assets that were 100% compliant. In some circumstances, the completion status could remain 0% until the team deployed one last magical fix that made all assets compliant.
Compliance Hub now calculates a space's completion as the average of all control completion percentages. Teams can now see incremental progress with each security improvement they deploy. We think this better reflects the true state of compliance and gives users the small wins they deserve as they work to secure their environments.
Improved CIS policy results
We've reworked many of our bundled CIS benchmark policies to make them more resilient and improve the rendering of scan results:
- Rework queries in CIS AWS Foundations to improve rendering of results.
- Improve reliability of auditd, SELinux, and AppArmor checks in Linux policies.
- Improve the reliability of the
Ensure audit_backlog_limit is sufficientcheck. - Prevent failures in the
Ensure permissions on /etc/gshadow are configuredcheck when the file does not exist. - Prevent failures in the
Ensure cron is restricted to authorized userscheck when/etc/cron.allowdoes not exist. - Expand the
Ensure HTTP server is not installedcheck for Nginx and lighttpd in addition to Apache2. - Add two additional controls to the CIS AWS Foundations benchmark policy.
- Improve reliability and result output of queries in the CIS GCP and GKE policies.
- Improve the query output of failing Kubernetes namespaces in the
Ensure that all Namespaces have Network Policies definedcheck. - Add missing audit blocks to checks in Kubernetes policies.
🐛 BUG FIXES AND UPDATES
- Improve rendering of GCP tiles in the fleet view when organizations, projects, and cloud assets have scanned.
- Fix sorting of assets by count in Security > Policies table when there are checks with 0 assets.
- Don't show empty Manufacturer or Product configuration data on cloud assets.
- Add the July 31, 2023 EOL date for FreeBSD 13.1.
- Remove the unused user settings option "Send me space alerts."
- Improve performance of reporting first time asset scans.
- Improve error messages when scanning GCP VM instances/snapshots outside of a GCP environment.
- Rename Oracle Cloud Infrastructure assets to Oracle Cloud Infrastructure Tenancy to better reflect that these are the OCI tenancies.
- Show policy descriptions in the registry.
- Show audit content in asset check pages.
