Mondoo 10.3 is out!
🥳 Mondoo 10.3 is out! This release includes Microsoft application vulnerability detection, expanded EOL/CVE detection, and more!
Get this release: Installation Docs | Package Downloads | Docker Container
🎉 NEW FEATURES
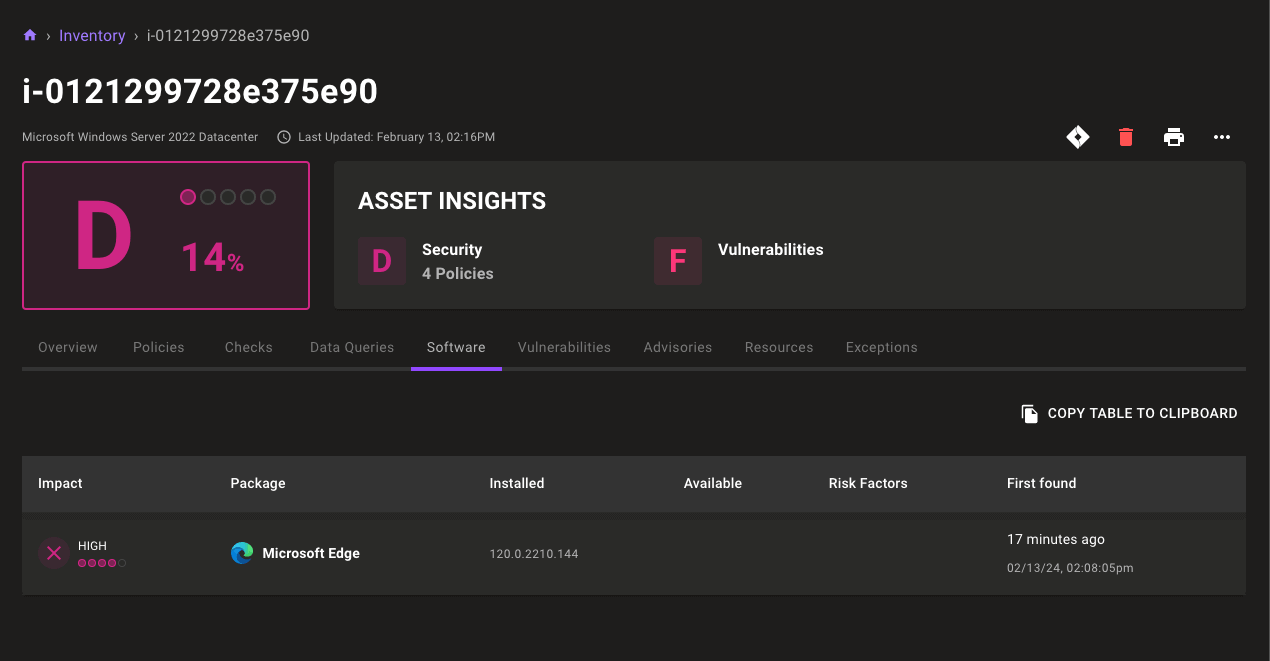
Microsoft application CVE detection
Expose additional critical vulnerabilities on your workstations and servers with new application vulnerability detection for Microsoft Edge, .NET Framework, and Visual Studio Code. Mondoo automatically flags vulnerable releases on the asset's Software tab. Links to relevant CVEs and Microsoft KB advisories help you understand the risk of outdated software releases in your environment.
🧹 IMPROVEMENTS
Paginate affected assets
Have thousands of systems impacted by a security check? No problem with new asset pagination on the security check pages.
Performance improvements
We refactored how Mondoo initiates scans, compiles CVE data, and executes the shell to make sure you get the best security results without waiting.
Reverse IP Lookup PTR record check in the Email Security policy
Gmail now requires a reverse IP Lookup PTR record for your domain to accept emails. The Mondoo Email Security policy now includes a new "Ensure Reverse IP Lookup PTR record is set (DNS Forward confirmed)" check so you can validate your domain is ready for these new stringent Gmail requirements.
Vulnerability data on Pop!_OS
Mondoo now supports CVE detection for Pop!_OS, the Ubuntu-derived distribution for System76 laptops.
Ubuntu 24.04 EOL and CVE support
Mondoo now detects the EOL date for the upcoming Ubuntu 24.04 release as well as package CVE data. The Ubuntu release doesn't come out until April, but this way you'll be secure from day one.
🐛 BUG FIXES AND UPDATES
- Simplify the description of EPSS data in CVE/Advisory console pages.
- Fix fields not displaying correctly in the
vulnmgmt.cvesresource. - Fix querying CloudWatch metrics alarms where the SNS topic does not exist in the
aws.cloudtrail.trailsresource. - Add a friendly error message when the
aws.cloudtrailresource is called without an ARN. - Don't report the core provider as needing to be updated.
- Fix failures parsing time values in some AWS resources.
- Fix dict value parsing in the
gcp.bucketsresource. - Remove duplicate Jira resource autocompletion in the shell.
- Improve light mode in the registry and asset filters.
- Add an empty state to the asset insights when no policies or vulnerability data are available.
- Show an empty state for data queries when the scan result is an empty string, nil value, or 0.
- Prevent empty titles in Microsoft KBs.
- Fix scanning of AWS instances using SSM when the instance lacks tar.
- Improve remediation instructions in the Google Cloud (GCP) Security policy.
- Fix missing severities in some Scientific Linux security advisories.
- Support RHEL-based distributions in the CIS Distribution Independent Linux
Ensure updates, patches, and additional security software are installedcheck. - Improve query output and reliability in the CIS Amazon Web Services (AWS) Foundations Benchmark and AWS Best Practices policies.
- Update Amazon 2023 and Fedora 38/39 EOL dates to reflect updated dates.
- Fix CVE detection for some packages on Ubuntu 23.10.
- Improve example cnspec/cnquery commands in the console.
- Fix fetching policies from the public registry.
- Fix failures in the CIS "Ensure journald service is enabled" check.
- Improve the check reliability and output in the CIS AWS Foundations policy.
