Mondoo 11.36 is out!
🥳 Mondoo 11.36 is out! This release includes ad hoc risk prioritization with workspaces!
Get this release: Installation Docs | Package Downloads | Docker Container
🎉 NEW FEATURES
Zero in on exactly the assets you need with workspaces
Do you find yourself repeatedly searching for the same groups of assets? Do you wish you could see a subgroup of assets in your space to compare them or measure progress on a certain project? Or maybe some assets just get in the way of what you want to focus on right now? What you need are workspaces!
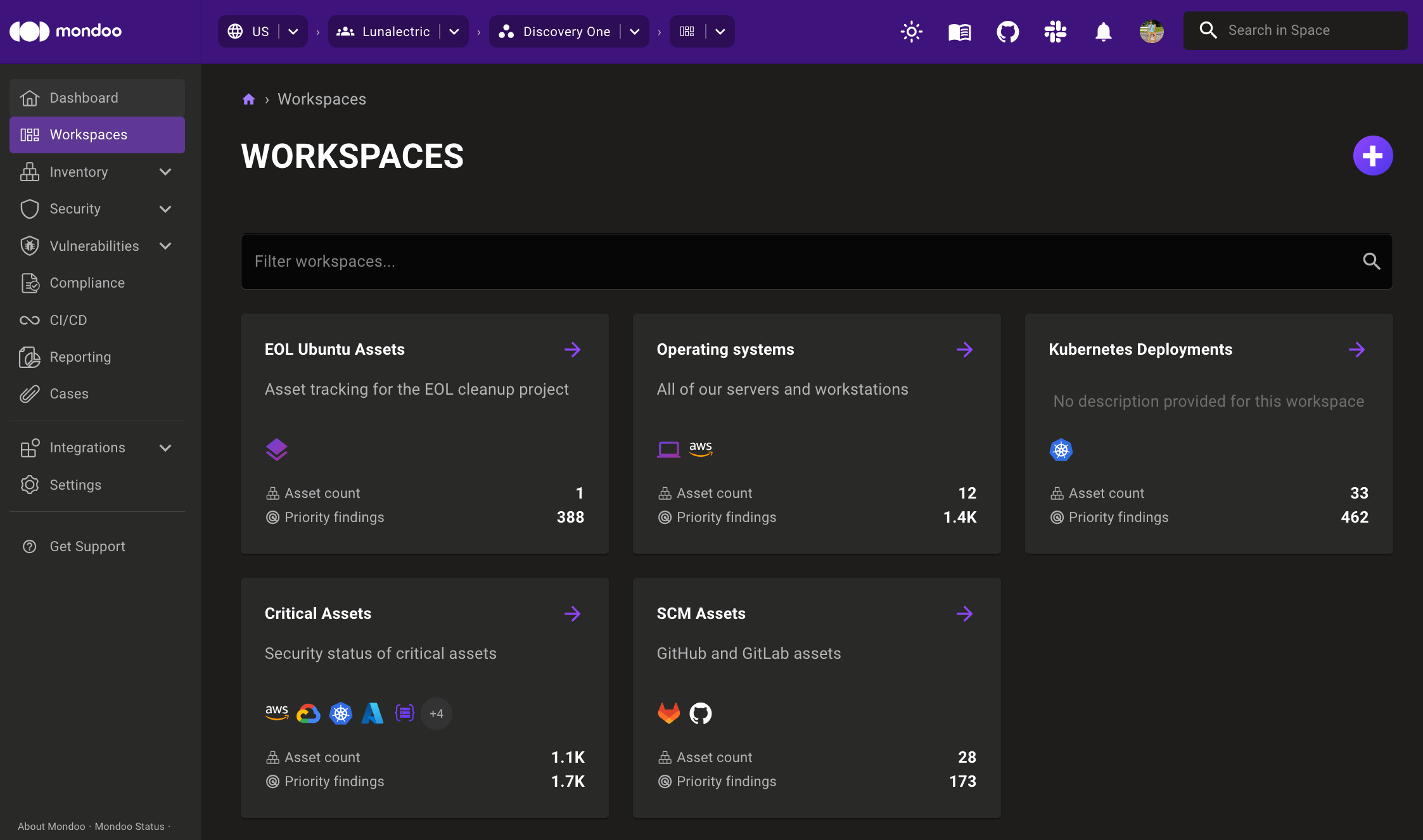
Workspaces are dynamic groups of assets in a space that you want to view and assess together. Unlike spaces, assets in a workspace are included based on queries. Best of all, an asset can be in as many workspaces as you want. Create a workspace that shows only assets with critical findings, another workspace that has all your Windows 2016 systems that still need to be upgraded, and another that includes all the systems owned by the front end team... whatever meets your specific business needs.
How might you use workspaces to solve problems?
Like many companies, Lunalectric has thousands of assets, but recently their CISO has been increasingly focused on their supply chain. To ensure GitHub and GitLab source code and CI/CD configuration meet best practices, let's create a workspace just for these SCM assets.
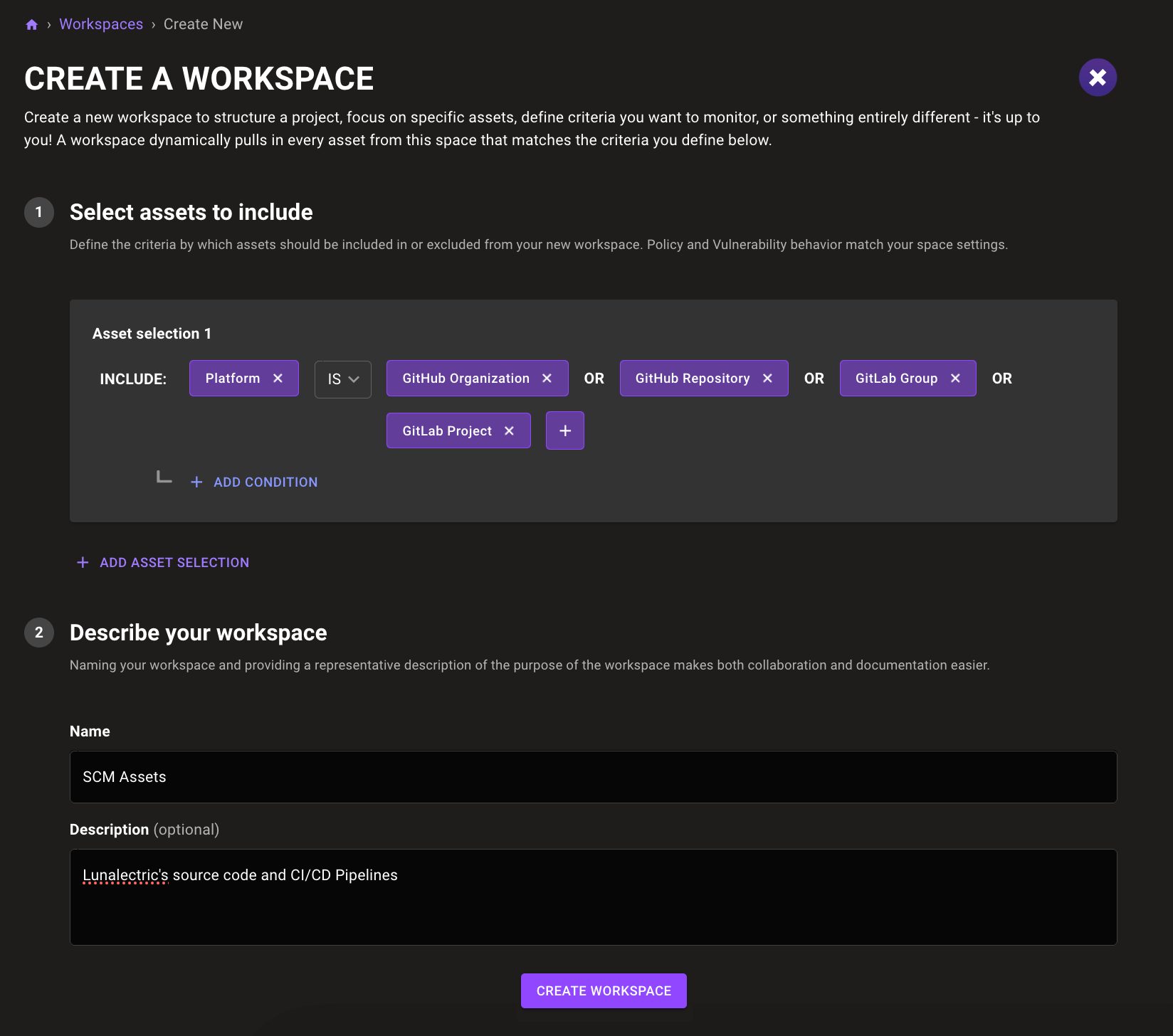
We create a single asset selection that includes the GitHub and GitLab platforms. Asset selections can match on asset name, kind, platform, platform version, and risk rating with more options coming soon. We can even add as many additional conditions to the selection as we want to create complex queries like Windows systems with a critical risk rating that aren't Windows 2022 and have the word "luna" in the asset name.
Once our workspace is created, we can find it by selecting Workspaces in the left navigation menu or choosing it from the new workspaces top navigation drop-down menu.
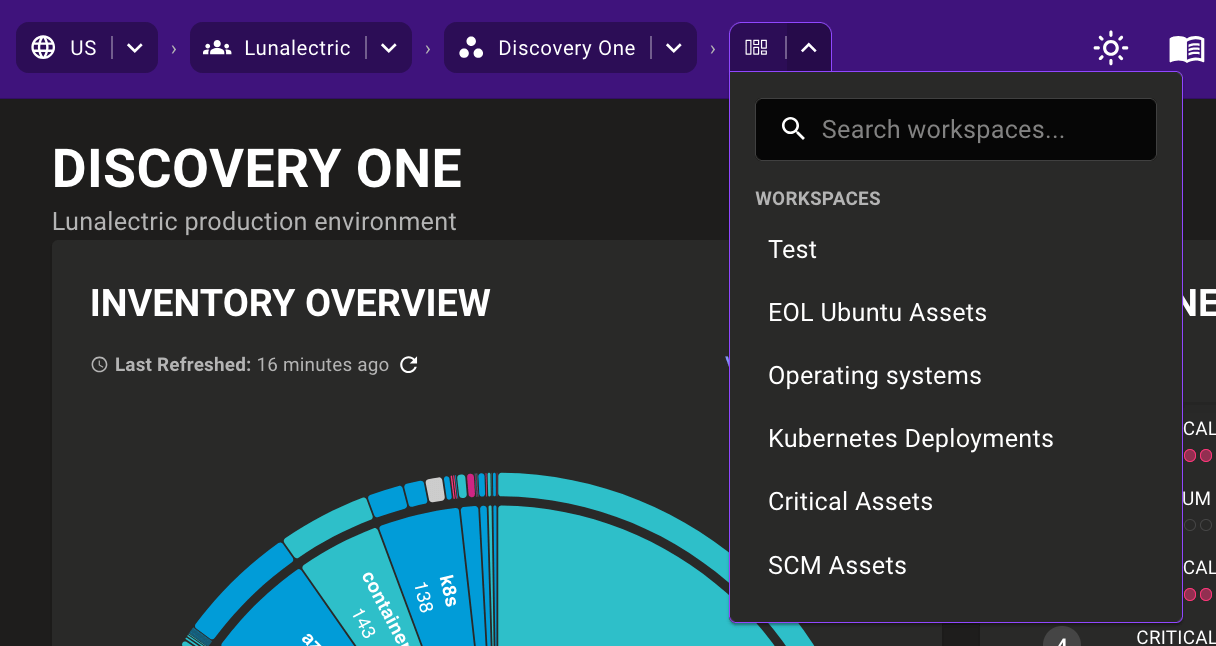
Once in our new SCM Assets workspace, the layout feels similar to the existing Lunalectric spaces, only more focused on understanding risks and exploring assets. Our workspaces dashboard shows just our GitLab and GitHub assets, including the top misconfigurations we should start tackling. We can dive into policies, checks, CVES, or advisories to see more details... all the while remaining tightly focused on the task at hand.
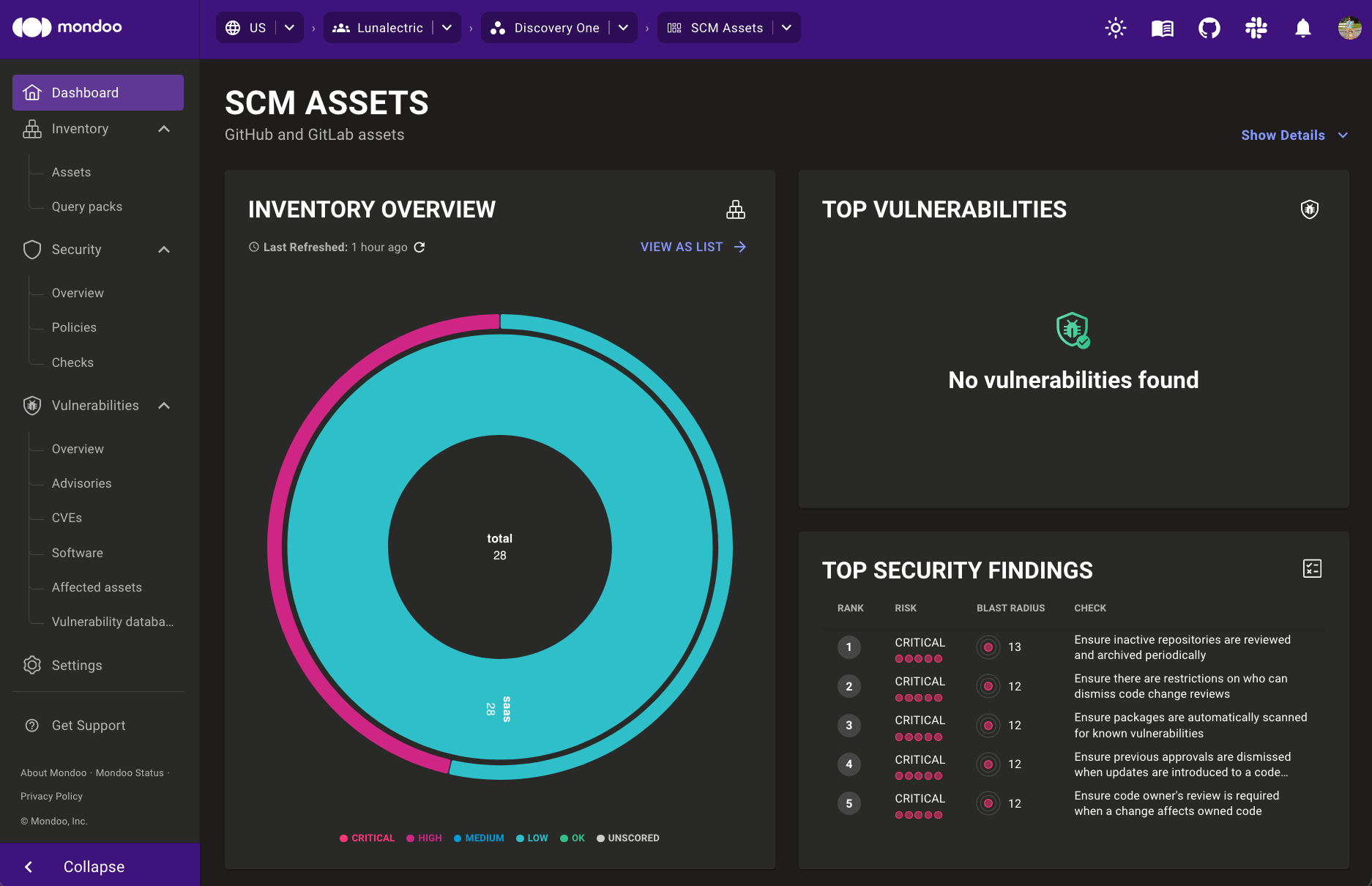
Even without diving deeper, the workspace dashboard's inventory overview is telling quite a story. GitLab assets are all passing checks, but GitHub assets, on the other hand, are all high risk.
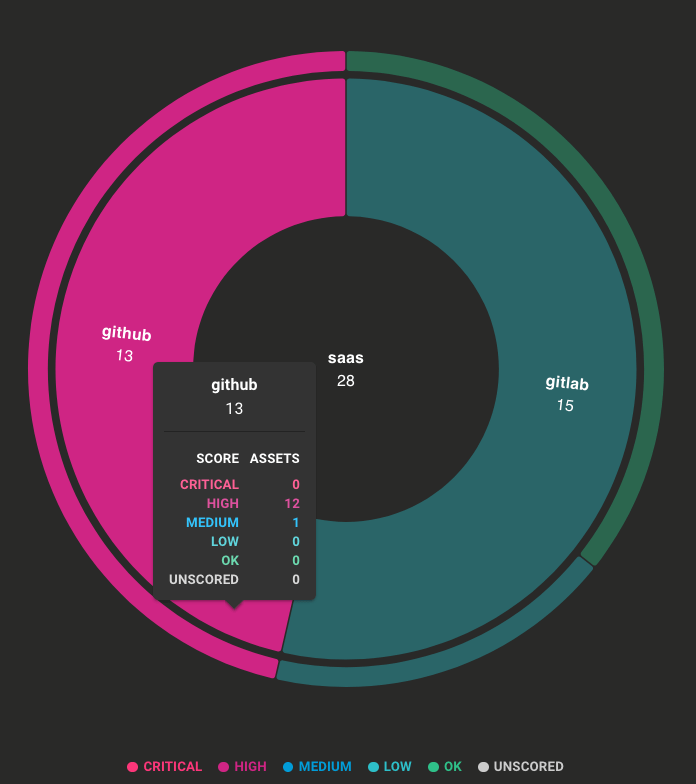
Armed with this quick insight, we have the information we need to let our CISO know about the current SCM risk and develop a remediation plan to secure these critical assets.
To learn how you can use workspaces to better organize assets and expose risks, read Plan Your Mondoo Organization and Workspaces in the Mondoo documentation.
Quick access to reports
Quickly access compliance reports by selecting Reporting in the left navigation menu. Looking for more reports? Stay tuned for more updates in upcoming releases. If you're looking for something in particular, let us know at product@mondoo.com!
🧹 IMPROVEMENTS
Optionally follow HTTP -> HTTPS redirects
You now have additional control over how Mondoo scans HTTP hosts in the host provider. By default cnquery and cnspec no longer follow redirects from HTTP to HTTPS endpoints, so you can now inspect your HTTP configurations when you choose. If you prefer to follow redirects, use the new --follow-redirects flag.
Without the redirect you can inspect the original page and headers:
$ cnquery shell host http://mondoo.com
cnquery> http.get
http.get: http.get url=url id = http://mondoo.com statusCode=301
cnquery> http.get.body
http.get.body: ""
With redirects specified, you can follow all redirects to the final page users would see:
$ cnquery shell host --follow-redirects http://mondoo.com
cnquery> http.get
http.get: http.get url=url id = http://mondoo.com statusCode=200
cnquery> http.get.body
http.get.body: "<!DOCTYPE html><!-- Last Published: Fri Jan 10 2025 00:09:49 GMT+0000 (Coordinated Universal Time) --><html..."
Resource updates
azure.subscriptions.defenderForContainers
- Expose
Extensionsvalues
azure.subscription.policy.assignment
- New
parametersfield
fstab
- Update
optionsfield to an array of options instead of a single string
k8s.node
- New
kubeletPortfield - New
nodeInfofield - New
createdfield
microsoft.applications
- Fetch all applications in large installations
Improved CIS benchmarks
Sometimes the best changes are behind the scenes. This week we shipped all-new internal tooling to generate CIS benchmark policies in Mondoo Platform. These changes not only let us to bring you the latest and greatest policies more quickly in the future—they also enabled us to make a huge number of small improvements to existing policies:
- New checks that were previously marked as requiring manual user validation
- More clear and concise descriptions for each policy
- Expanded check descriptions, including rationale behind the security concerns
- New audit and remediation steps in many Linux distribution policies
- Simplified MQL queries to improve readability
- Additional platform version tags to improve searching for policies
- Improved policy search results when searching for platform versions
🐛 BUG FIXES AND UPDATES
- Display CVEs for Fedora 41 assets.
- Fix a failure querying Microsoft 365 applications.
- Correct the remediation steps in the BSI 'Ensure SSH Idle Timeout Interval is configured' check.
- Add EOL dates for FreeBSD 14.2 and Alpine Linux 3.21.
- Correct the EOL date for FreeBSD 14.1.
- Update the Amazon Linux 2 EOL date, which has been extended to June 30, 2026.
- Support EBS volume scanning of instances with LVM partitions.
- Improve remediation step formatting in Mondoo VMware policies.
- Open check remediation links in a new window or tab.
- Fix an
unknown-score-typeerror when comparing semver data in checks. - Fix display of GitHub provider help.
- Don't reinstall some providers on each scan.
- Fix errors using the Cloudflare provider.
- Show the link to discovered assets on each integration page.
- Add detection of the upcoming M4 MacBook Air/Pro models to asset overview information.
- Add form validation to the Microsoft Defender for Cloud integration to ensure UIDs are correctly formatted.
- Display platform icon for Nmap assets in affected asset tables.
- Update Windows checks for the
RestrictSendingNTLMTrafficregistry entry to accept both Audit All and Deny All configurations. - Add a missing permission to the automated CLI Azure setup.
- Show the platform in all cnspec scan results. Thanks for suggesting this, @DrackThor!
