Mondoo 11.33 is out!
🥳 Mondoo 11.33 is out! This release includes Cloudflare asset inventory, expanded Entra ID inspection, and more!
Get this release: Installation Docs | Package Downloads | Docker Container
🎉 NEW FEATURES
Explore Cloudflare services
Dive deep into your Cloudflare infrastructure with a new Cloudflare provider for cnquery/cnspec. Use this provider to gather information on key Cloudflare services:
- Accounts
- Zones
- DNS records
- R2
- Zero Trust apps
- Streams
- Videos
- Workers
- Pages
This example queries DNS zones:
cnquery run cloudflare -c "cloudflare.zones[1] { name dns { * } }"
cloudflare.zones[1]: {
name: "lunalectric.com"
dns: {
records: [
0: cloudflare.dns.record type="A" content="164.90.210.141" name="api.lunalectric.com"
1: cloudflare.dns.record type="A" content="142.93.110.9" name="console.lunalectric.com"
3: cloudflare.dns.record type="CNAME" content="console.lunalectric.com-pages.pages.dev" name="prod.lunalectric.com"
7: cloudflare.dns.record type="MX" content="mail.protonmail.com" name="lunalectric.com"
9: cloudflare.dns.record type="TXT" content="v=DMARC1; p=none; rua=mailto:e60948910ee34fe61be5a6bf2c3fb@dmarc-reports.cloudflare.net,mailto:dmark@lunalectric.com" name="_dmarc.lunalectric.com"
11: cloudflare.dns.record type="AAAA" content="100::" name="meet.lunalectric.com"
]
}
}
🧹 IMPROVEMENTS
Resource updates
aws.ecr.image
- New
lastRecordedPullTimefield - New
pushedAtfield - New
sizeInBytesfield
microsoft.user
- New
creationTypefield - New
identitiesfield using the newmicrosoft.user.identityresource - New
auditlogfield using the newmicrosoft.user.auditlogresource
🐛 BUG FIXES AND UPDATES
- Improve default output of the
github.repository.adminCollaboratorsresource. - Improve default output of the
github.organization.packagesresource. - Fix macOS process resource executable values to align with the output from Linux systems.
- Add the EOL date for Fedora 41 and update dates for 40 and 39 to match the latest published information from the Fedora Project.
- Improve cleanup of inactive assets in large organizations.
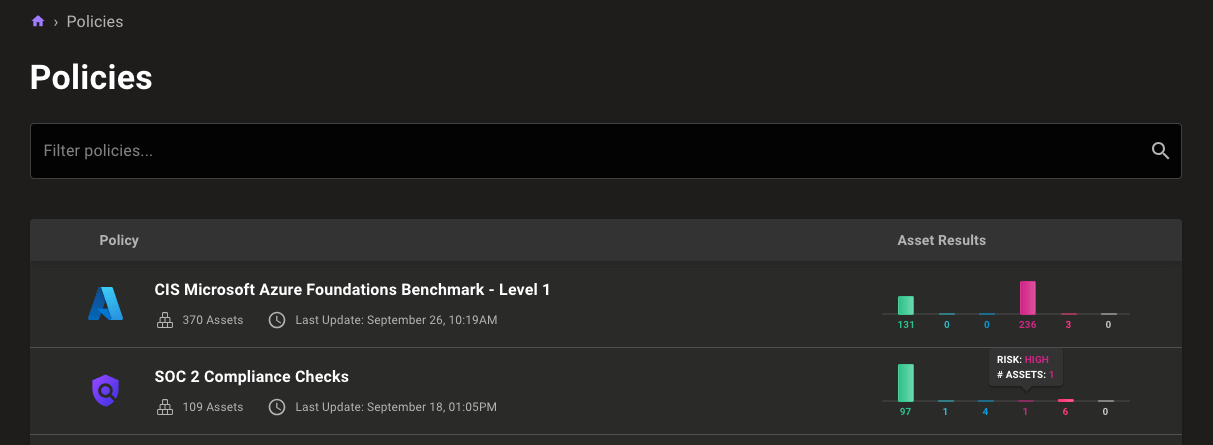
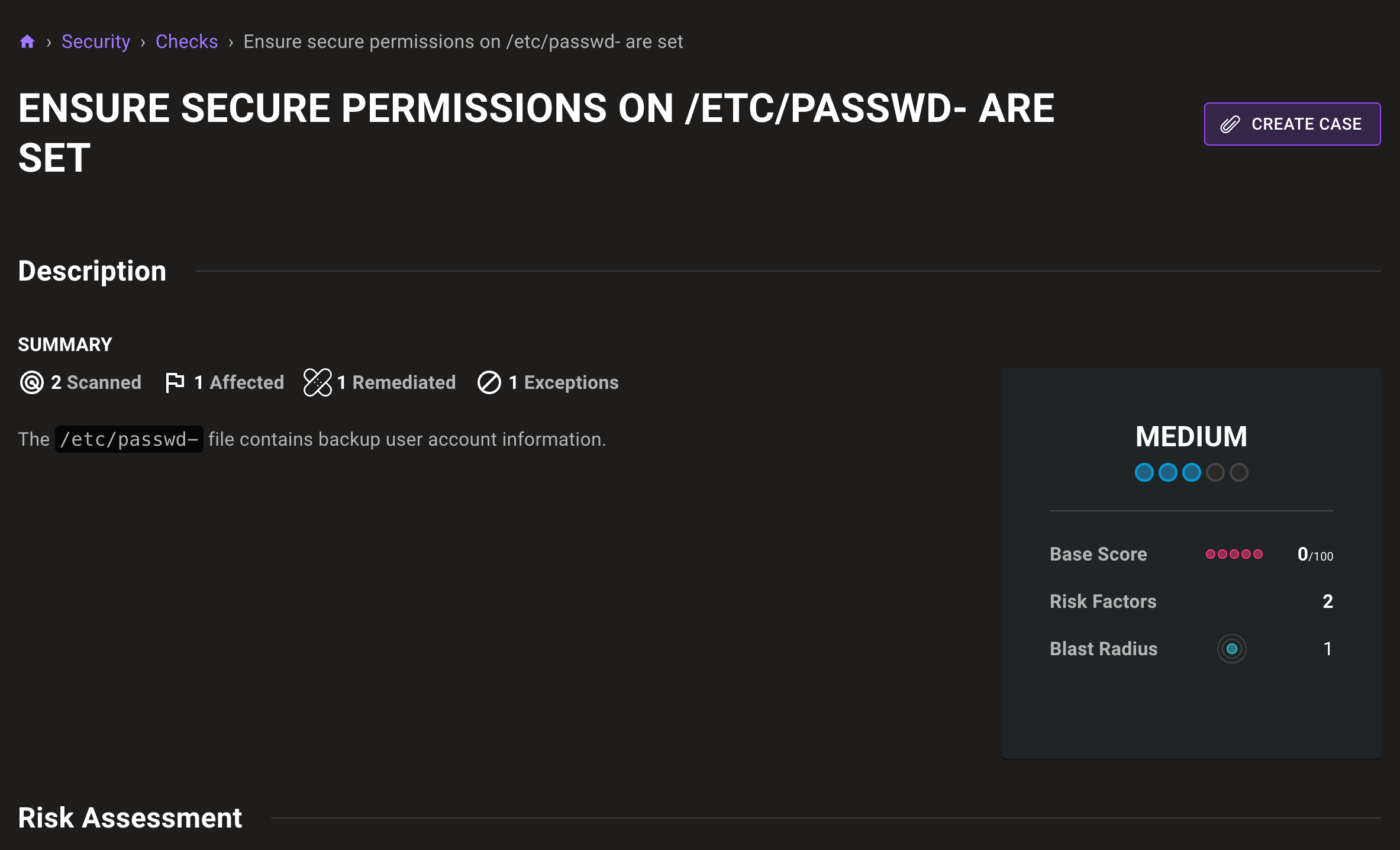
- Fix missing compliance check mappings for some frameworks.
- Add the missing query
Ensure permissions on /etc/group.old are configuredto the CIS SUSE Linux Enterprise 11 Benchmark policy. - Improve the reliability of aggregate score generation on dashboards.
- Add two checks to the CIS VMware ESXi 6.7 and 7.0 Benchmark policies:
Ensure port-level configuration overrides are disabledEnsure Virtual Distributed Switch NetFlow traffic is sent to an authorized collector
- Add an asset group for Kubernetes Namespace assets.