Mondoo 7.2 is out!
🥳 Mondoo 7.2 is out! This release launches our new OSS projects cnquery and cnspec + much more!
Get this release: Installation Docs | Package Downloads | Docker Container
🎉 NEW FEATURES
Powered by new open source projects
We are excited to announce the open-source release for: cnquery and cnspec. These are the core components of the Mondoo CLI and will replace it going forward.
cnquery is an asset inventory and search engine, which features an interactive shell, MQL runner, and query pack execution. Query packs are a new way to create a bundle of queries which are automatically executed and all data collected. This is useful for the creation of asset inventories and collection of data during incidents. They are a lightweight alternative to policies (without scoring).
cnspec is the security test project, which focuses on misconfigurations and vulnerabilities. It is built on top of cnquery and adds policies and scored controls. It is also a drop-in replacement to the Mondoo CLI today and uses the same commands to scan assets, run queries, open a shell, or work with policies.
Together with this open-source release, we are opening the ability to create custom resources and providers. In the coming weeks we will start to release more guides for developers who are interested in contributing.
Furthermore, we are solidifying MQL as and open standard for GraphQL-based infrastructure querying and assertions. Most of the engine can be found in cnquery and is highly extensible as well as embeddable.
We highly encourage you to try out cnquery and cnspec! Please let us know if you encounter any challenges switching from the Mondoo CLI to cnspec. We will continue to support the Mondoo CLI throughout the v7 release.
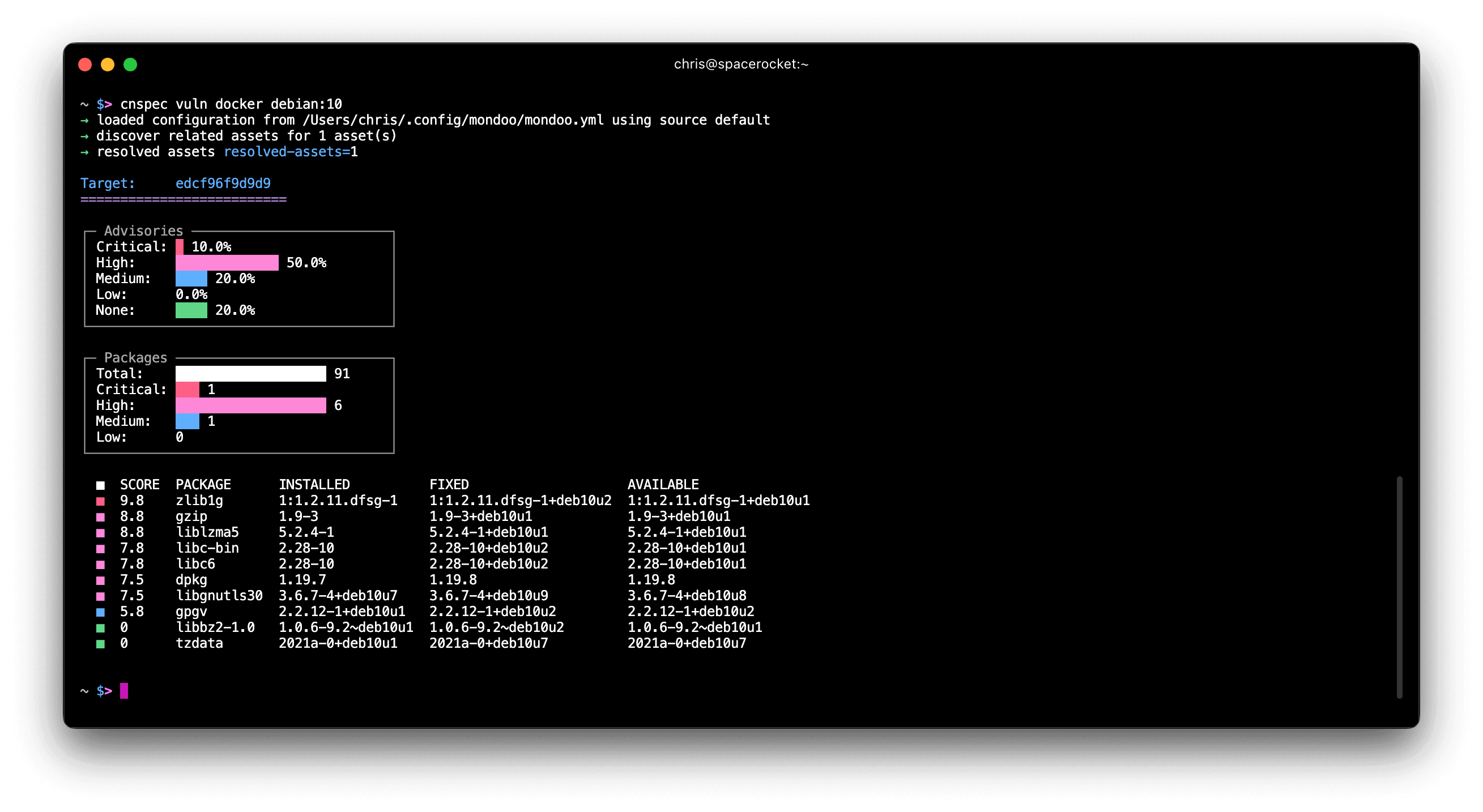
CLI CVE scanning
Problem: Sometimes you only care about CVEs on a server, container, or container image, but you have to scan the system for security misconfigurations as well.
Solution: We've added a new cnspec vuln command that allows you to scan for CVEs on servers, containers, and container images without performing a full security scan. The command also offers more detailed CVE output so you can see what's best to patch first.
FreeBSD scanning support
Problem: You run a diverse infrastructure including FreeBSD hosts which need to be properly secured.
Solution: cnquery and cnspec now include initial support for remotely scanning FreeBSD hosts. With this update, you can now list packages and services, examine file contents, and execute commands. Stay tuned for more FreeBSD updates, and if you have thoughts or would like to contribute resource support for FreeBSD, join the Mondoo GitHub Discussions.
🧹 IMPROVEMENTS
Add ephemeralContainers to k8s.pod
The k8s.pods and k8s.pod and resources now includes information on ephemeralContainers attached to the pods. ephemeralContainers are a relatively new feature in Kubernetes. They let you attach containers to Pods for debugging. You can't remove them, and if you forget about them, they can introduce significant security risks to your environment.
Example workload with ephemeralContainers defined:
apiVersion: v1
kind: Pod
metadata:
annotations:
creationTimestamp: "2022-11-03T16:40:54Z"
labels:
admission-result: pass
name: passing-pod-yaml
namespace: debug-ns
resourceVersion: "75952"
uid: 823d82d5-890e-4d6a-9da6-404648144585
spec:
automountServiceAccountToken: false
containers:
...
dnsPolicy: ClusterFirst
enableServiceLinks: true
ephemeralContainers:
- args:
- sleep
- "9999"
image: busybox:1.28
imagePullPolicy: IfNotPresent
name: ephemeral_junk
resources: {}
securityContext:
privileged: true
terminationMessagePath: /dev/termination-log
terminationMessagePolicy: File
preemptionPolicy: PreemptLowerPriority
priority: 0
restartPolicy: Always
...
Improve CLI warnings when no provider is specified
In cnquery, if the user specified an invalid provider, the CLI unexpectedly used the local provider instead:
cnquery shell rockylinux
→ no provider specified, using defaults.
Use --help for a list of available providers. provider=local
→ discover related assets for 1 asset(s)
→ resolved assets resolved-assets=1
___ _ __ __ _ _ _ ___ _ __ _ _
/ __| '_ \ / _` | | | |/ _ \ '__| | | |
| (__| | | | (_| | |_| | __/ | | |_| |
\___|_| |_|\__, |\__,_|\___|_| \__, |
mondoo™ |_| |___/ interactive shell
Now if a user accidentally forgets the provider usage information is provided:
$ cnquery shell rockylinux
x provider rockylinux does not exist
Allows for the interactive exploration of MQL queries
Usage:
cnquery shell [flags]
cnquery shell [command]
Available Commands:
arista Connect to an Arista endpoint
aws Connect to an AWS account or instance
azure Connect to a Microsoft Azure account or instance
container Connect to a container, an image, or a registry
...
Load base64 configuration directly from env vars
cnspec now loads a Base64-encoded configuration from the MONDOO_CONFIG_BASE64 env var. This means you no longer need to load the Base64-encoded config in your CI jobs, write it out to a config file on disk and then run cnspec to scan your CI job.
Previously CI jobs had to write the config to disk:
echo $VARIABLE_WITH_BASE64_CONFIG > mondoo.json
cnspec scan k8s my_file.yml --config mondoo.json
Now with MONDOO_CONFIG_BASE64 set you can just run the CLI:
cnspec scan k8s my_file.yml
Add MQL ports resource for macOS and Windows
The MQL ports resource now supports Windows and macOS hosts in addition to Linux hosts. Using this resource you can track ports to listening addresses and executables:
cnquery> ports.listening
ports.listening: [
port port=56863 protocol="ipv4" address="*" process.executable="/usr/libexec/rapportd"
port port=56863 protocol="ipv6" address="*" process.executable="/usr/libexec/rapportd"
port port=7000 protocol="ipv4" address="*" process.executable="/System/Library/CoreServices/ControlCenter.app/Contents/macOS/ControlCenter"
port port=7000 protocol="ipv6" address="*" process.executable="/System/Library/CoreServices/ControlCenter.app/Contents/macOS/ControlCenter"
port port=5000 protocol="ipv4" address="*" process.executable="/System/Library/CoreServices/ControlCenter.app/Contents/macOS/ControlCenter"
port port=5000 protocol="ipv6" address="*" process.executable="/System/Library/CoreServices/ControlCenter.app/Contents/macOS/ControlCenter"
port port=44960 protocol="ipv4" address="127.0.0.1" process.executable="/Users/chris/Library/Application"
port port=44950 protocol="ipv4" address="127.0.0.1" process.executable="/Users/chris/Library/Application"
port port=18412 protocol="ipv4" address="127.0.0.1" process.executable="/Users/chris/Library/Application"
port port=7335 protocol="ipv4" address="127.0.0.1" process.executable="/Users/chris/Library/Application"
port port=17223 protocol="ipv4" address="127.0.0.1" process.executable="/Users/chris/Library/Application"
port port=17223 protocol="ipv6" address="[::1]" process.executable="/Users/chris/Library/Application"
]
Auto discover ESXi hosts for vSphere
When scanning VMware vSphere assets, Mondoo now automatically discovers all ESXi hosts.
New controls for macOS security policy
We've added new controls to the macOS Security policy to make sure that automatic updates are securely configured:
- Ensure automatic checking of software updates enabled
- Ensure automatic download of software updates enabled
- Ensure critical updates are installed automatically
New NSA Kubernetes Hardening Guide Version 1.2 controls
We've added several new controls to the NSA Kubernetes Hardening Guide Version 1.2 policy to help you secure your Kubernetes cluster and workloads:
- Protect Pod service account tokens
- Minimize and verify access to cluster-admin binding via rolebindings
- Minimize and verify access to cluster-admin binding
- CVE-2021-25742 - checking nginx-ingress ConfigMaps for dangerous settings
🐛 BUG FIXES AND UPDATES
- Detect Rocky Linux 9 as platform family
redhatsopackageandserviceresources function properly. - Better raise permission issues when running the
portsresource. - Avoid panics in cnquery when there are no query bundles.
- Escape JSON data to prevent errors parsing some values.
- If an asset is terminated mid-scan, report it as unscored instead of an error.
- Fix asset filter not properly applying Terraform HCL Security Static Analysis for AWS policy.
- Update EOL dates for Debian releases to the latest versions on their wiki.
- Improve spacing of EBS volume scans to reduce API throttling.
- Greatly improve the speed of service account and space deletion.
- Fix typos in NSA Kubernetes Hardening Guide Version 1.2 policy.
- Resolve errors when checking for default ingress/egress network rules in NSA Kubernetes Hardening Guide Version 1.2 policy.
- Resolve errors when checking for the PKI directory on Minikube in NSA Kubernetes Hardening Guide Version 1.2 policy.
- Avoid incorrect CVE counts for assets in the console.
- Update the Amazon Linux 2 EOL date to reflect the updated date of June 30, 2024.
- Detect the upcoming Fedora 37 release in the EOL policy.
- Improve error messages in the Mondoo Kubernetes Operator when private images cannot be scanned.
