Mondoo 10.9 is out!
🥳 Mondoo 10.9 is out! This release includes CVE remediation automation, detection of remote exploits in your infra, and more!
Get this release: Installation Docs | Package Downloads | Docker Container
🎉 NEW FEATURES
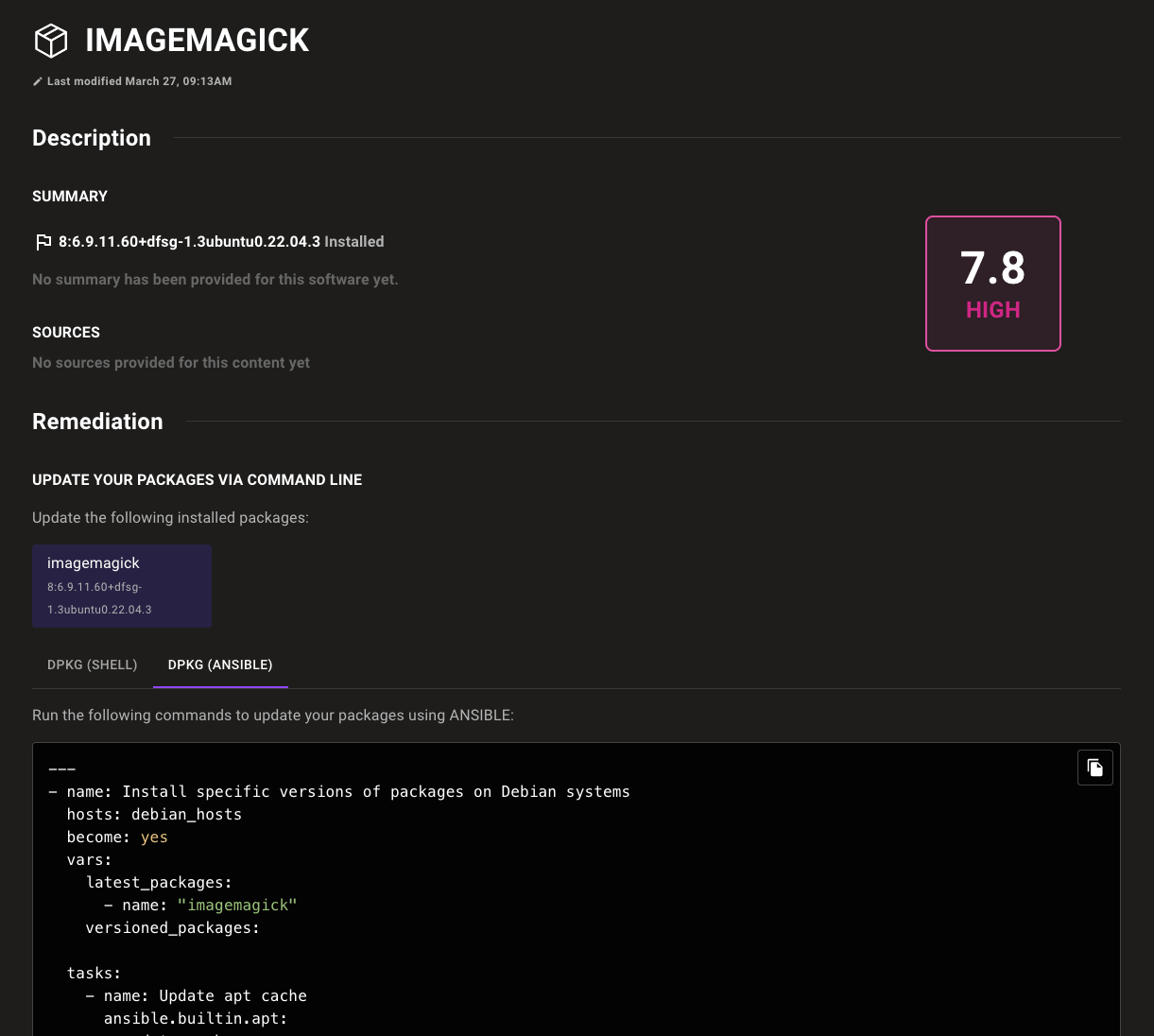
Automate your CVE remediation
Let Mondoo do the heavy lifting when it comes to remediating critical software vulnerabilities in your infrastructure with new Ansible and Bash remediation scripts to accelerate the patching of systems.
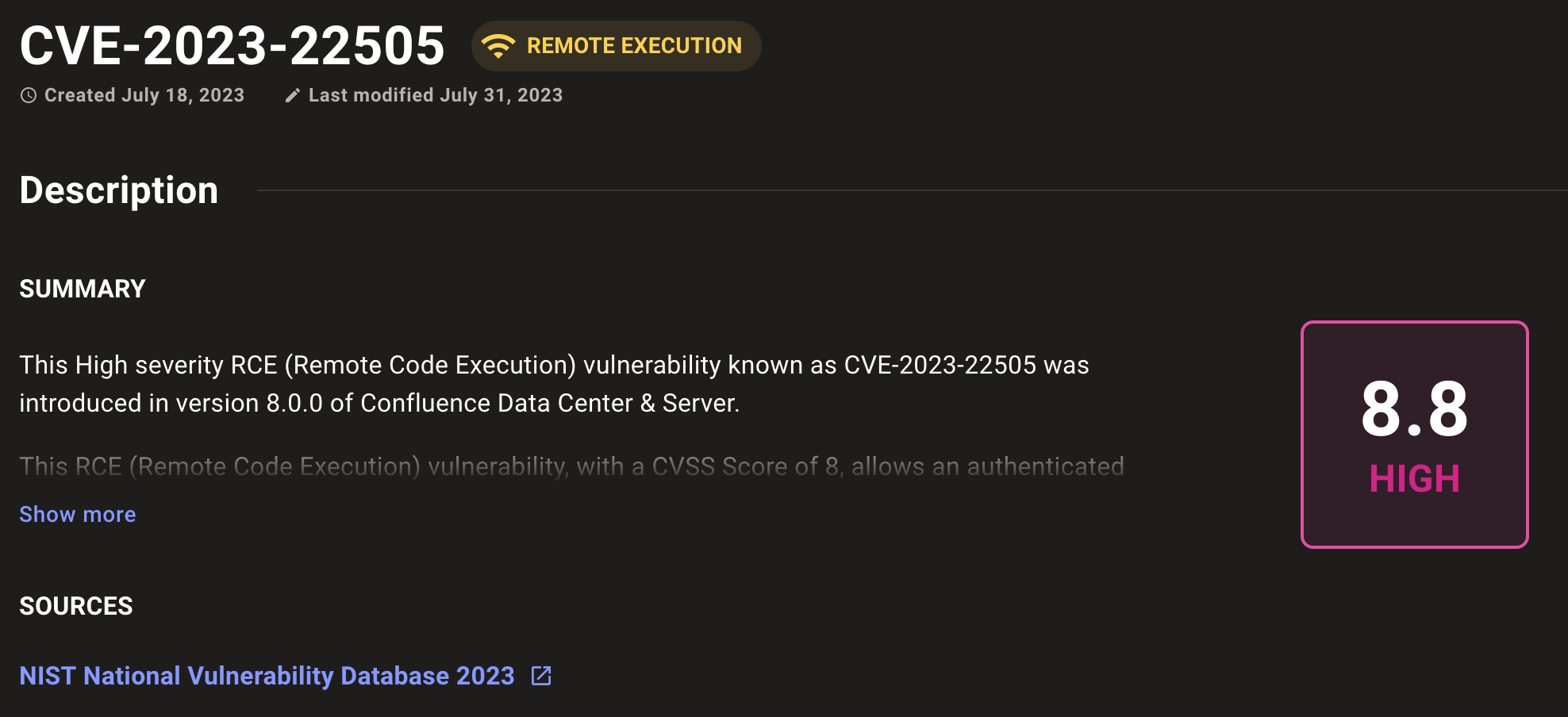
Expose remote exploits in your infrastructure
With the new "Remote execution" risk for CVEs and advisories, you can now prioritize and patch the highest risks to your business before attackers find them. Mondoo lets you sort by CVEs and vendor advisories that are known to be susceptible to remote code execution over the network.
🧹 IMPROVEMENTS
Resource improvements
asset
- New field
annotations.
aws.iam.policies
- Fix parsing data in
attachedRolesfield.
aws.rds.dbcluster
- New field
hostedZoneId. - New field
latestRestorableTime. - New field
masterUsername.
aws.rds.dbinstance
- New field
latestRestorableTime. - New field
masterUsername.
Ansible scan interval / splay settings
Control the scan interval and splay settings for Mondoo clients set up with the Mondoo Ansible role using new splay and timer variables.
Learn more in our all new Ansible docs!
Signed providers on Windows
Is it an advanced security product or a virus? It turns out that sometimes your endpoint protection software can't tell the difference. To help, we're signing all Mondoo providers to prevent tools flagging providers as potentially malicious software.
Friendly messages for space viewers in Kubernetes integrations
Want to take a peek at the configuration of Kubernetes integrations, but you only have the viewer permissions on the space? No worries. Kubernetes integration pages now show friendly messages when service account information is unavailable due to a lack of permissions. Stay curious.
🐛 BUG FIXES AND UPDATES
- Collect running kernel in SBOMs.
- Don't fail if a Linux process is running under a user that has been deleted.
- Fix AWS instances failing to scan via SSM in the Lambda integration.
- Improve network security group checks in the CIS Azure Foundation benchmark policy to ignore case and better target the security rules.
- Update CIS benchmarks for AlmaLinux, Rocky Linux, and Oracle Linux to skip GDM checks on headless systems.
- Display the Terraform logo for the Terraform Asset Inventory Pack.
- Display the Windows logo instead of the Microsoft 365 logo for all Windows desktop CIS policies.
- Improve Azure Pipeline setup examples in the console.
- Show labels on the asset overview when an asset is unscored.
- Update instructions and documentation links in Azure integration to match the latest Microsoft Entra ID pages.
- Improve AWS integration error messages in the console.
- Prevent multiple AWS scan requests from running at once in the AWS integration.
- Fix incorrect links in Red Hat advisories.
- Fix newer vendor advisories showing as unscored when the attached CVEs have no score.
- Improvements to Okta and Azure SCIM 2.0 support.
- Fix scanning of Docker images that are not on the system.
- Fix fetching of Microsoft 365 groups when there are a large number of groups in Entra ID.
- Fix scanning of private images in Kubernetes clusters.
- Improve performance in the
tls.certificateresource.