Mondoo 11.25 is out!
🥳 Mondoo 11.25 is out! This release includes expanded platform and AWS region support, updated Ubuntu 22.04 CIS policies, and more!
Get this release: Installation Docs | Package Downloads | Docker Container
🧹 IMPROVEMENTS
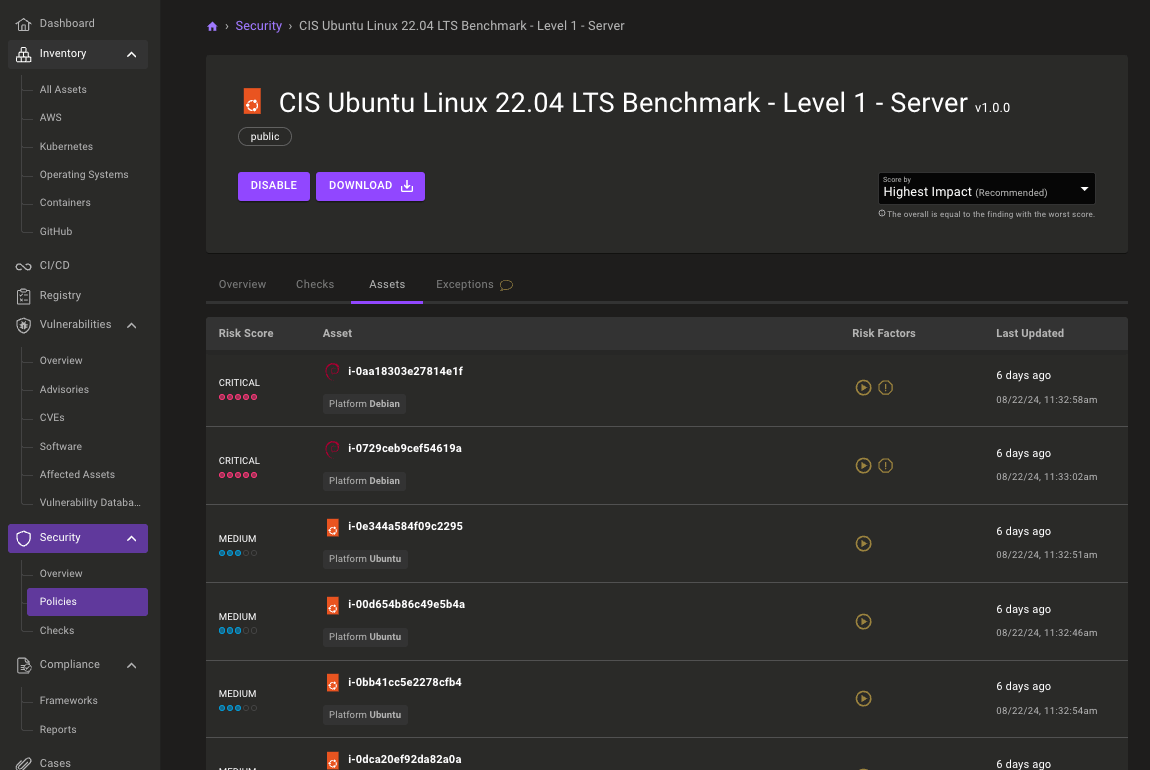
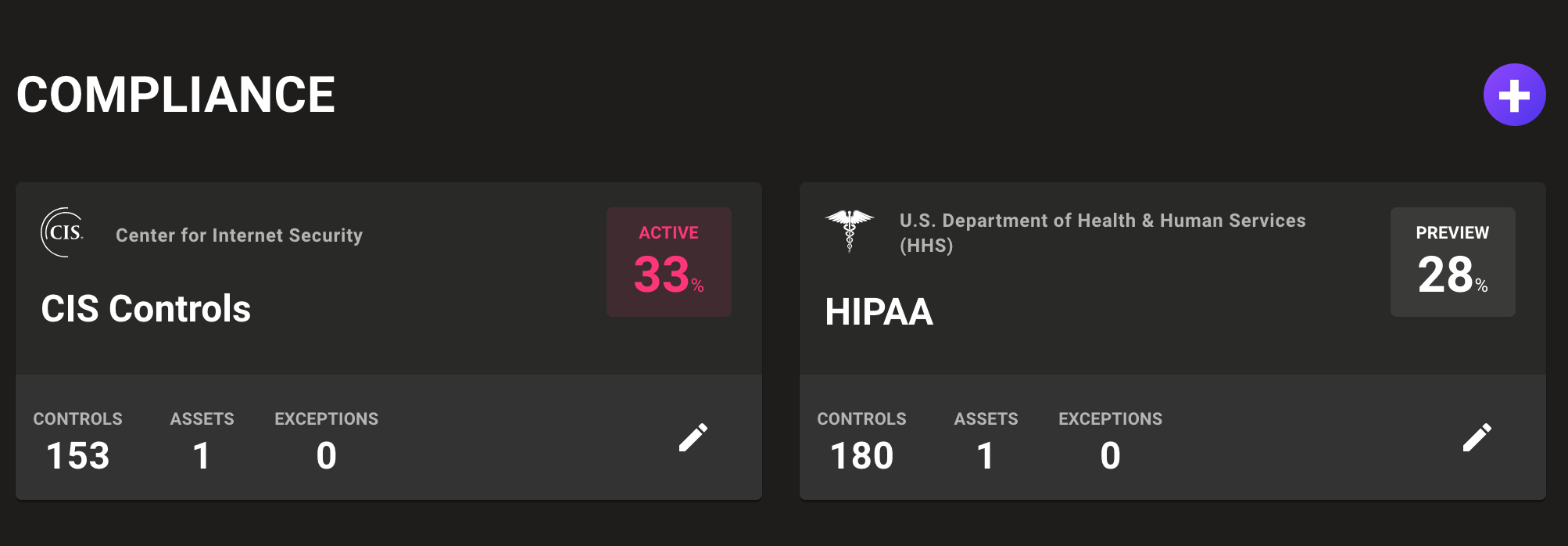
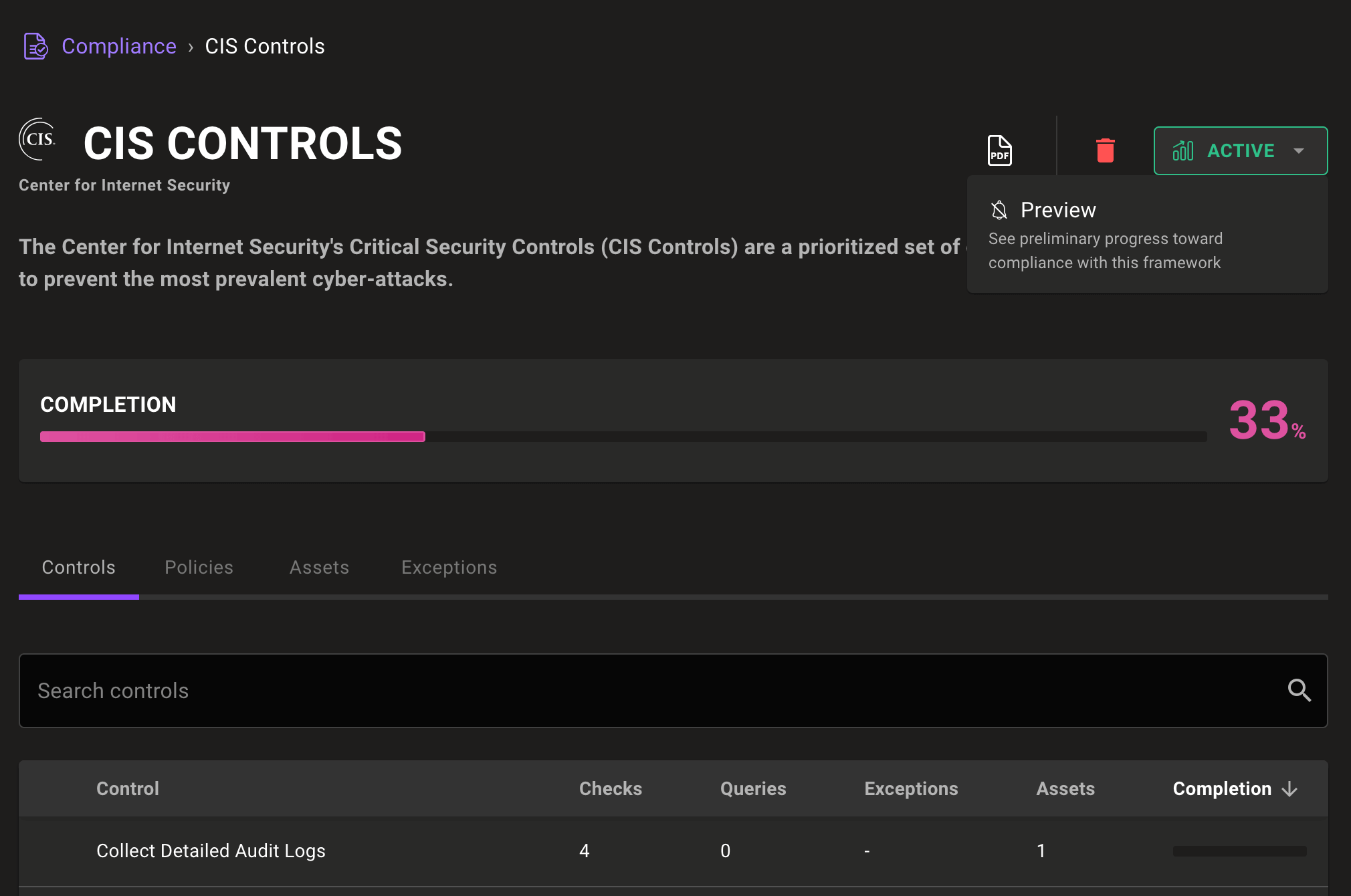
Updated CIS Ubuntu 22.04 benchmark policy
Secure critical Ubuntu 22.04 systems with the latest CIS Ubuntu benchmark version 2.0 policy. This updated policy includes 488 changes including dozens of all-new checks to keep your systems secure against the latest threats.
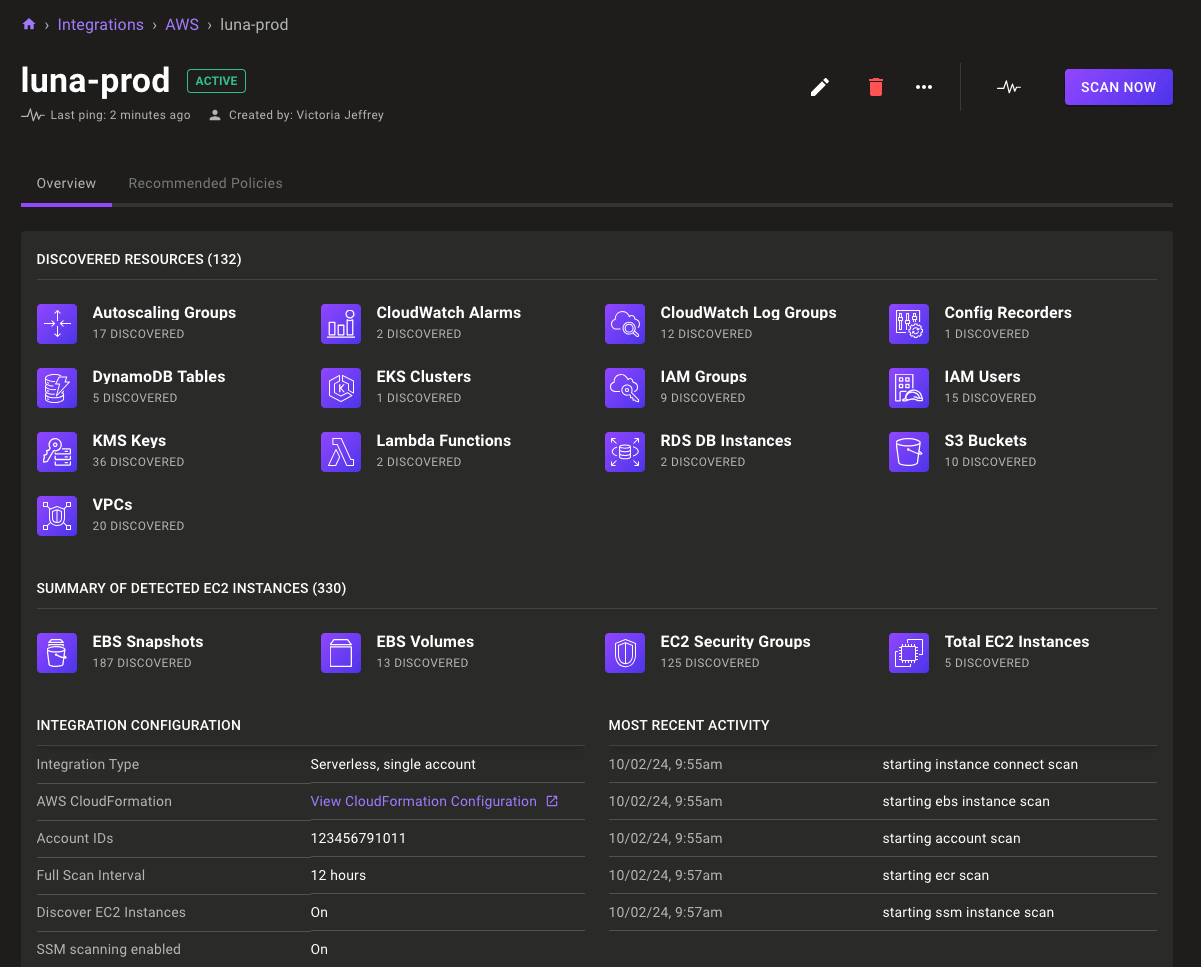
Expanded AWS serverless integration region support
The Mondoo AWS serverless integration has always supported scanning your AWS resources in any region. Now you have additional options for where the scanner itself runs. Mondoo now supports installing the integration into the following new regions:
- ca-central-1
- eu-north-1
- eu-west-2
- eu-west-3
- ap-south-1
Expanded platform support
Ensure systems are supported and secured with expanded vulnerability and end of life detection:
- Windows 11 24H2
- Google COS 117
- macOS Monterey (12)
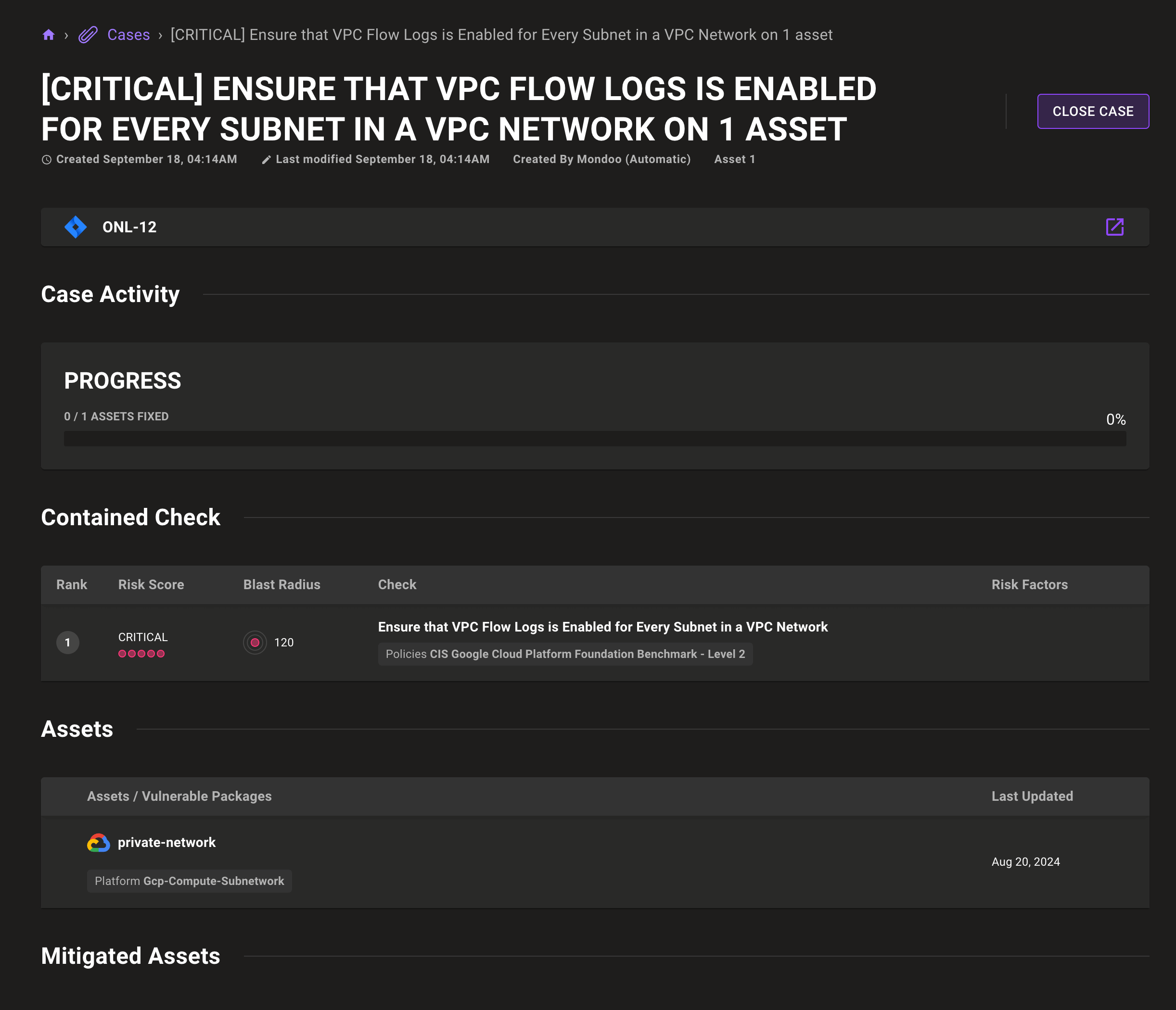
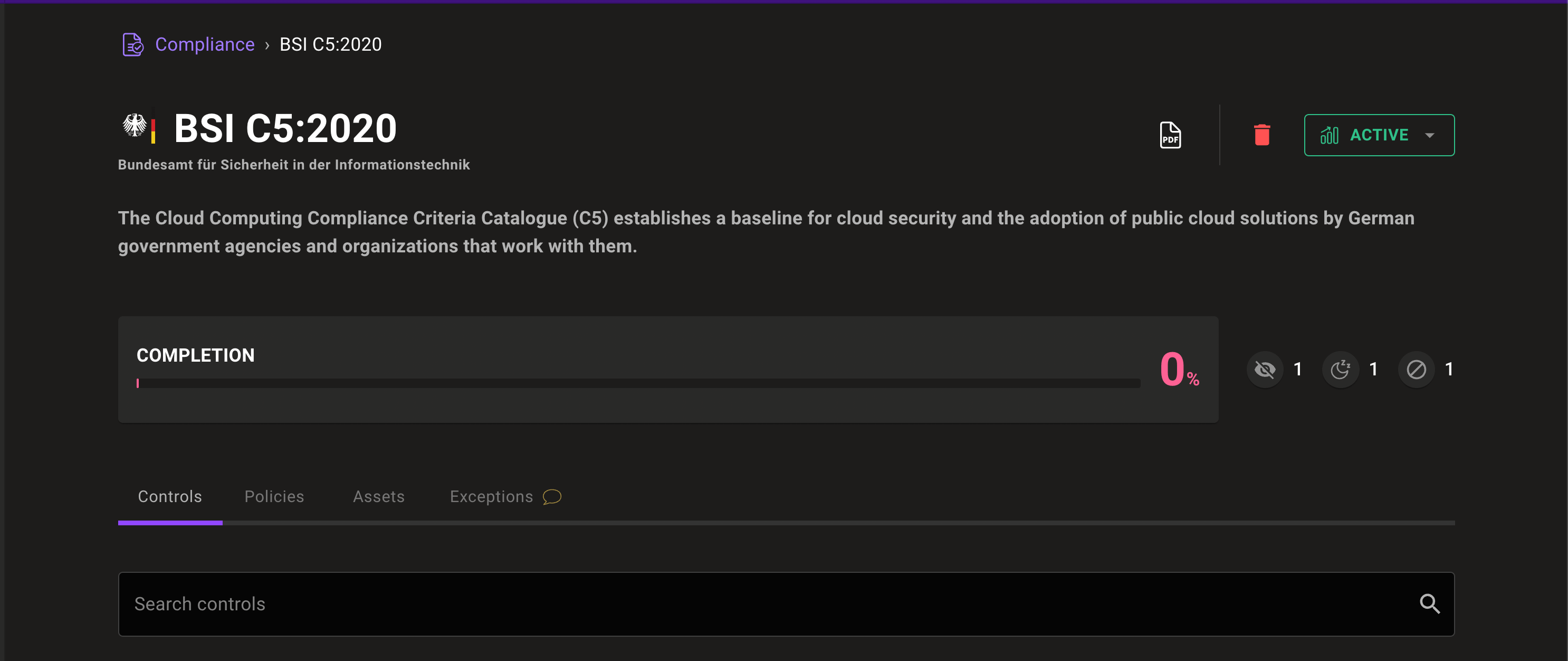
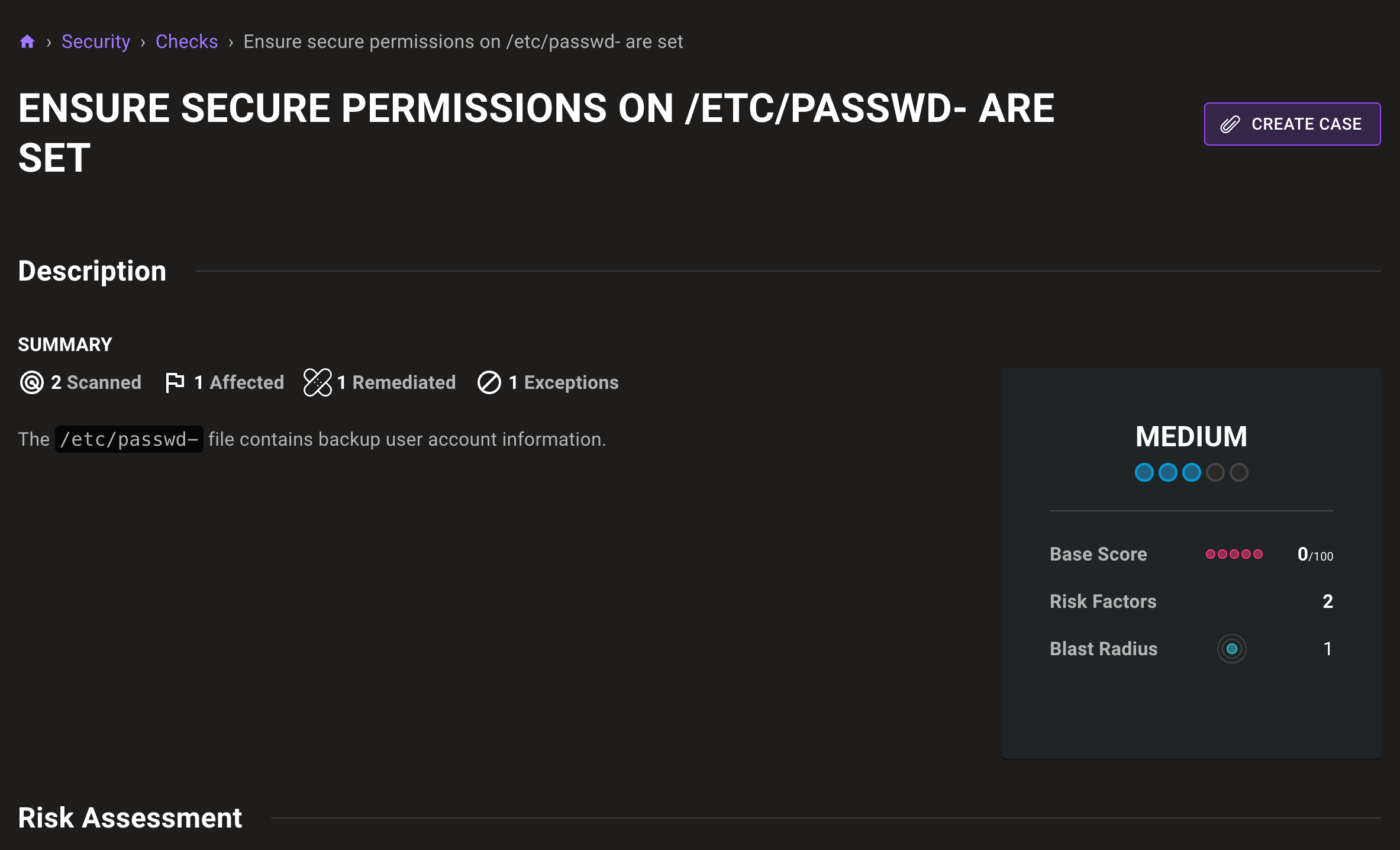
View exception count on check pages
Exception counts on individual check pages let you quickly see how many exceptions are set for an individual check.
🐛 BUG FIXES AND UPDATES
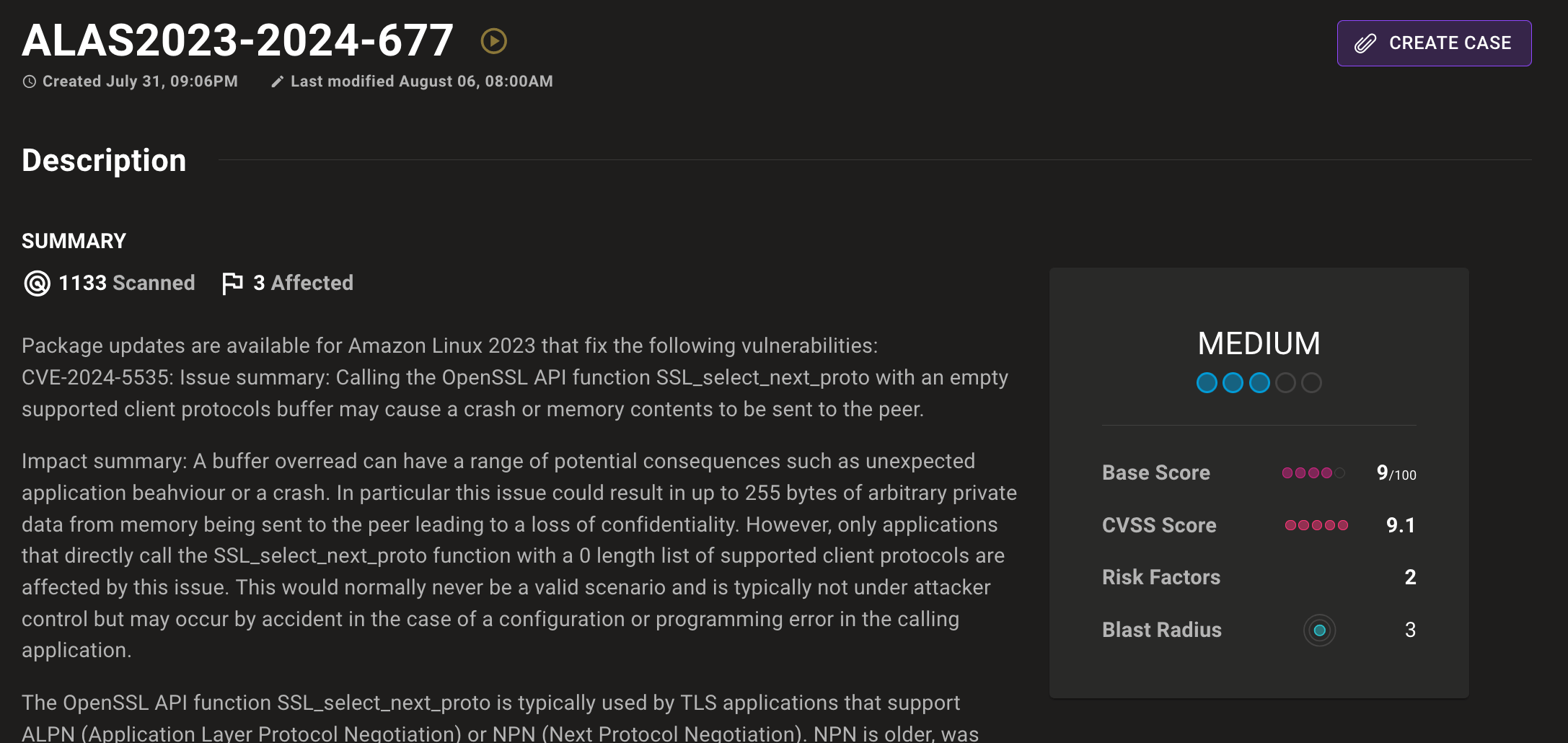
- Improve score accuracy for CVEs and checks.
- Open links from the AWS integration page in new tabs.
- Improve form validation and formatting in the AWS integration setup form.
- Fix incorrectly clipped log messages in the AWS integration page.
- Make single account installs the default option during AWS serverless integration setup.
- Improve auditd checks in CIS Linux benchmark policies to better support container image and filesystem snapshot scans.
- Redirect to the spaces list page after deleting a space.
- Support sending very large scan results to Mondoo Platform.
- Fix returning an incorrect platform family for Dockerfiles.
- Improve scan reliability in the AWS serverless integration.
- Expand and improve help in cnquery and cnspec.
- Update CIS Google Cloud Foundations policy to version 3.0 to match the check content.