Mondoo 8.3 is out!
🥳 Mondoo 8.3 is out! This release includes a new vulnerabilities experience, updated CIS/Mondoo policies, and more!
Get this release: Installation Docs | Package Downloads | Docker Container
🎉 NEW FEATURES
New vulnerabilities views
We've reworked our Vulnerabilities page to make it quicker to find vulnerabilities in your environment, identify the worst offending assets, and investigate newly released CVEs. A new Vulnerabilities menu now includes individual options for Advisories, CVEs, Affected Assets, and Mondoo Vulnerability Database (VMD).
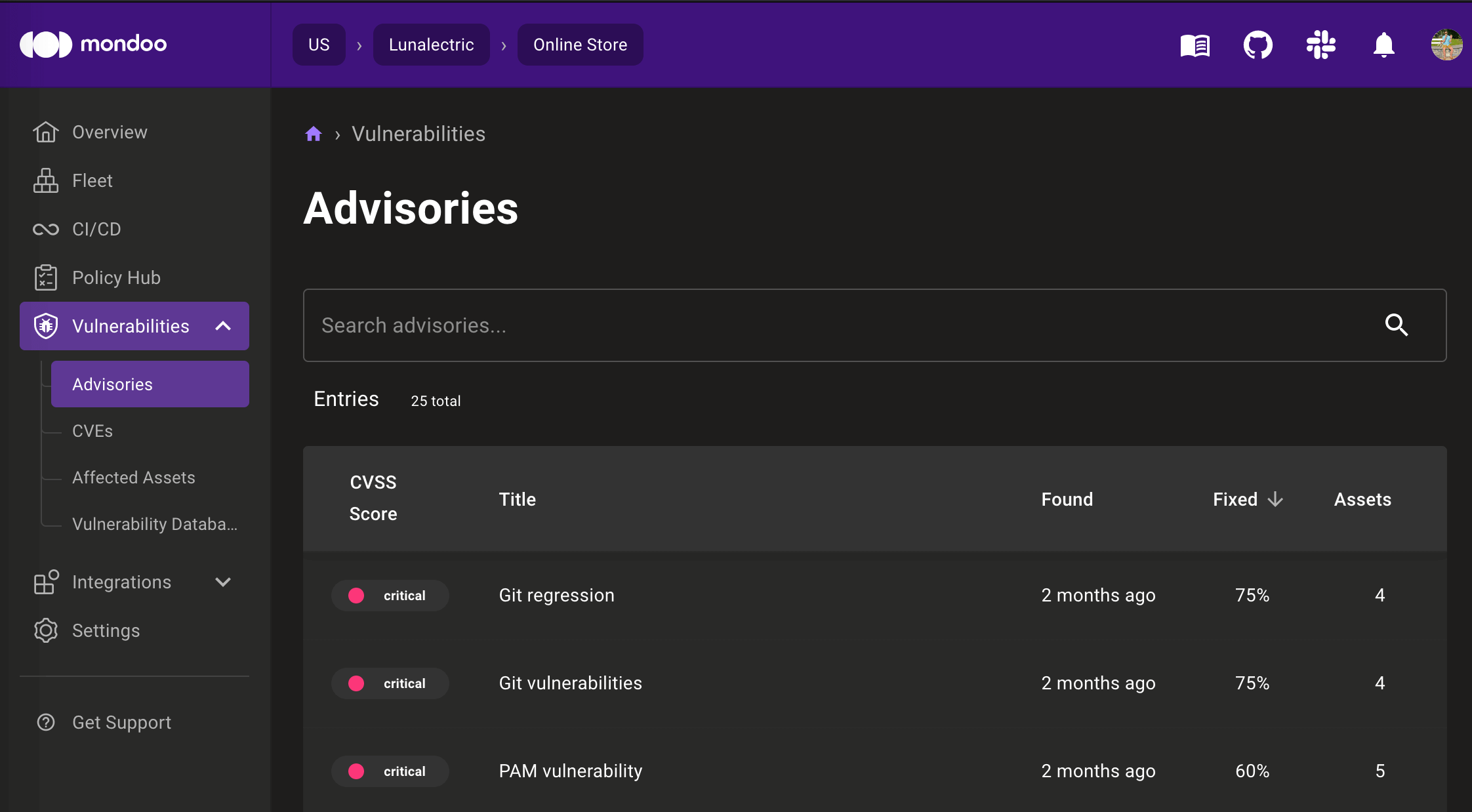
The Advisories and CVEs pages allow you to dive into specific vendor security advisories and CVEs that impact your environment. You can see when these issues were first discovered, progress towards patching them, and get more details on the advisory/CVEs, including impacted assets.
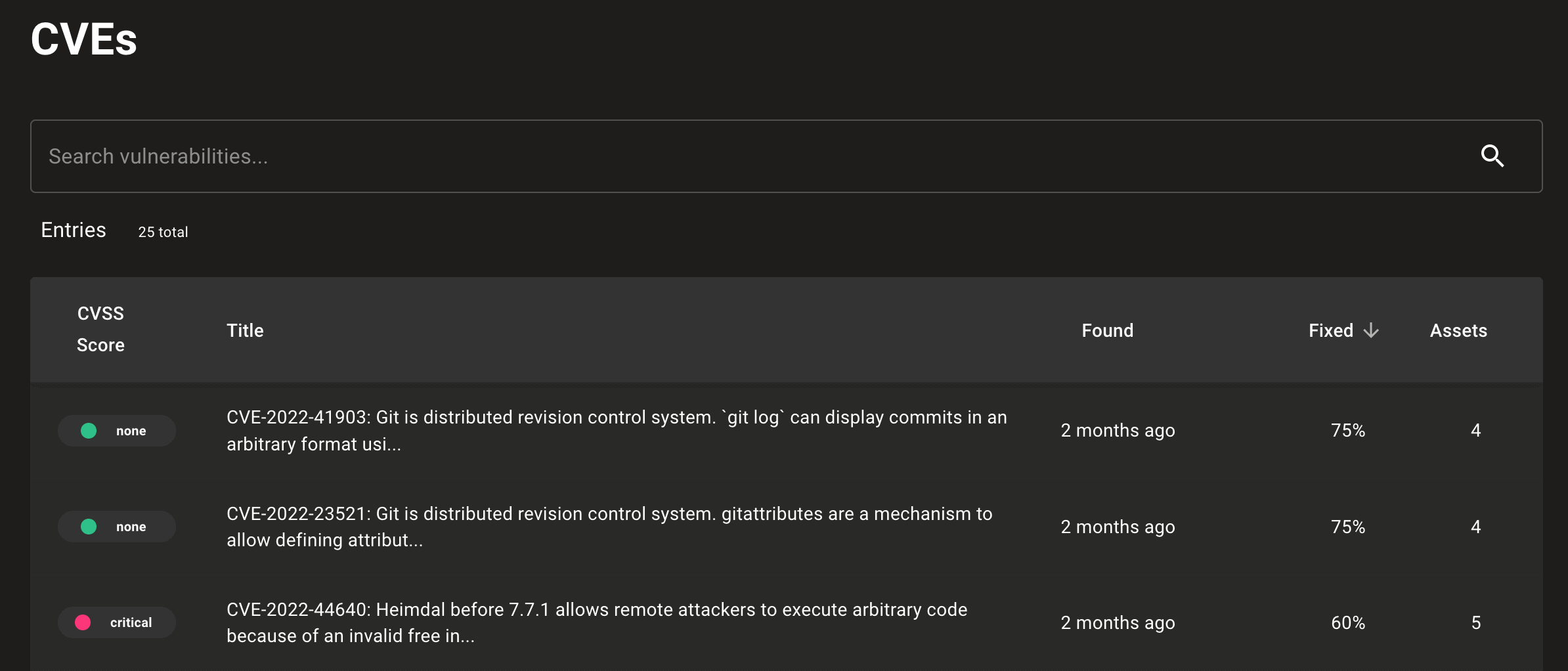
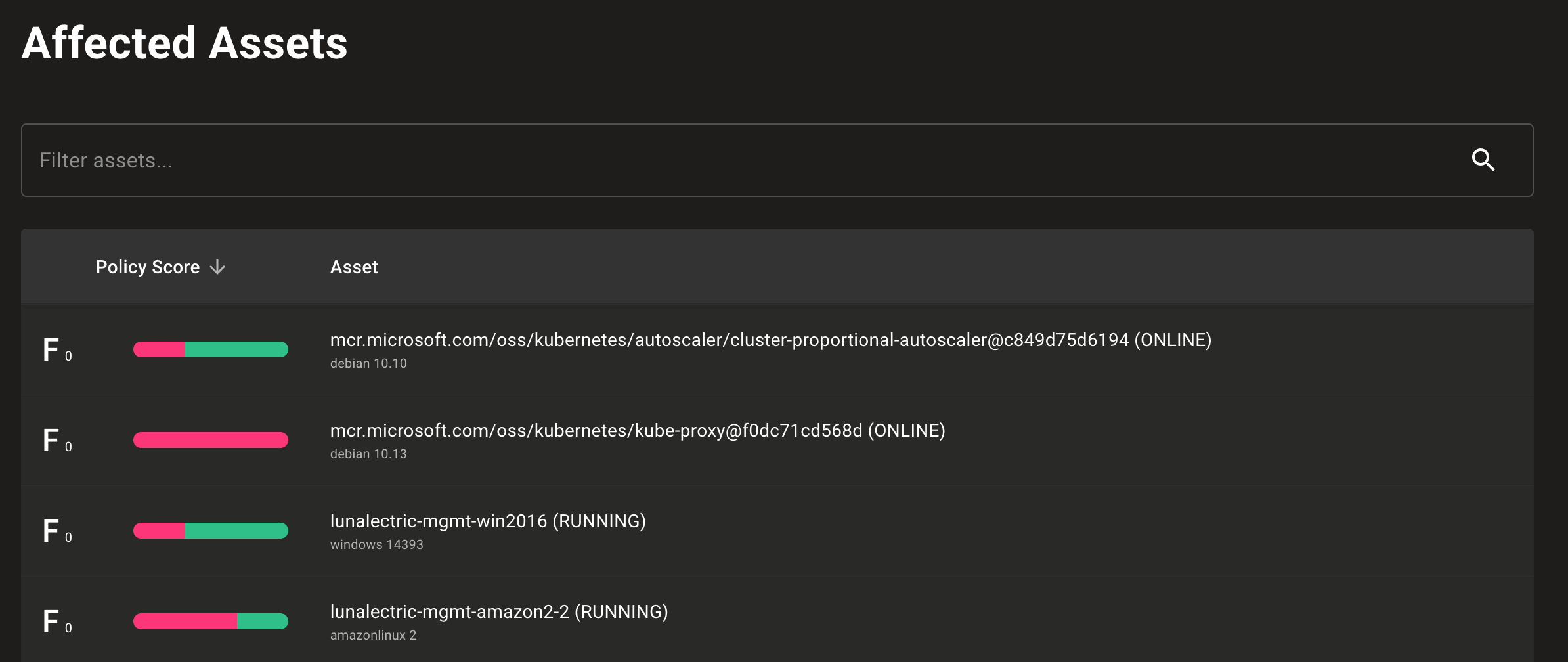
The new Affected Assets page lets you quickly dive into assets with unpatched CVEs or vendor advisories in your space.
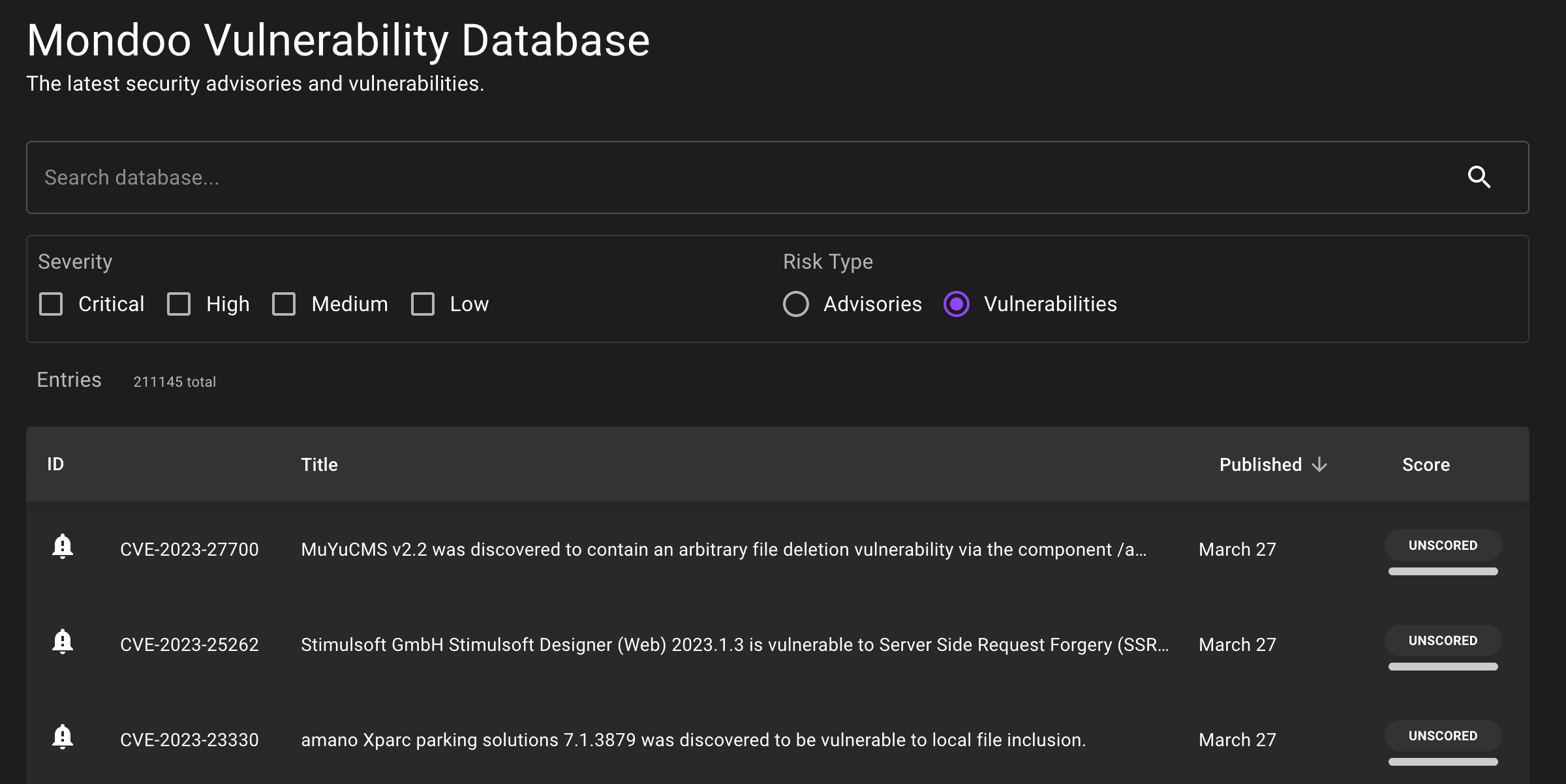
The completely reworked Mondoo Vulnerability Database (MVD) gives you a single UI to research new vendor CVEs and advisories even if they don't apply to your assets. Curious about that new CVE you read about online? Look it up to learn more, including details on the CVSSv3 score and any impacted assets in your environment.
Slack Team Security by Mondoo policy
Mondoo now includes a new Slack Team Security policy with seven checks to secure your Slack Team (Workspace):
- Ensure that between 2 and 4 users have admin permissions
- Ensure that admins use the most secure 2FA method
- Ensure all users use 2FA
- Use clear naming for external channels
- Ensure there is at least one internal channel per workspace
- Ensure there is at least one internal channel in the workspace and there are no external members
- Ensure domain allowlisting is enforced on internal channels
Microsoft 365 assets grouped in console
Problem Microsoft 365 assets weren't grouped together on the Fleet page, so finding them all could take a moment.
Solution We grouped Microsoft 365 assets together on the Fleet page so you can quickly find them.
Set a proxy server for all Mondoo Platform communication
Problem There was no way to isolate cnspec-to-Mondoo-Platform and cnquery-to-Mondoo-Platform communication from non-Mondoo traffic.
Solution A new --api-proxy config flag allows you to specify the proxy server for Mondoo Platform API calls when you register an asset with the cnspec login command. You can also manually add the api_proxy configuration option in your mondoo.yml config.
🧹 IMPROVEMENTS
Updated CIS Microsoft Azure Foundations Benchmark 2.0 policy
The CIS Microsoft Azure Foundations Benchmark policy has been updated from 1.5 to 2.0. This new release includes reworked audit and remediation steps that match Azure's latest UI and CLI experiences.
Expanded Microsoft Azure Security policy
The Microsoft Azure Security by Mondoo policy has been expanded with new checks for database systems and network assets in your Azure subscription:
- Ensure SSL connection is enabled for PostgreSQL Database Server
- Ensure SSL connection is enabled for MariaDB Database Server with the latest version
- Ensure Public Network access for MariaDB is disabled
- Ensure SSL connection enabled for MySQL Database Server with the latest version
- Ensure Public Network access for SQL Server is disabled or only possible through firewall rules
- Ensure default Public Network access for Key Vault is disabled
- Ensure that all activities on SQL Server are audited
- Ensure that transparent data encryption is enabled on SQL Server
- Ensure that diagnostic settings exist for the subscription
- Ensure that Diagnostic Setting collects essential security categories
- Ensure that direct UDP access to Azure Virtual Machines from the Internet is restricted
Expanded Windows Security policy
The Windows Security by Mondoo policy now includes a new check to ensure that Local Security Authority (LSA) protection is enabled on Windows assets.
Fewer API calls in the AWS Lambda integration
We've optimized our Lambda-based AWS integration to reduce the number of API calls made by the integration to reduce Lambda costs. Don't worry; you'll still get the same great AWS resource scans, but now with added efficiency.
etcd database encryption state in gcp.project.gke.cluster resource
The gcp.project.gke.cluster resource now includes information on encryption of the etcd database.
cnquery> gcp.project.gke.clusters[0]{databaseEncryption}
gcp.project.gke.clusters[0]: {
databaseEncryption: {
keyName: "projects/***/locations/us-central1/keyRings/***/cryptoKeys/***"
state: "ENCRYPTED"
}
2FA type in slack.users resource
The slack.users resource now includes the type of two-factor authentication (2FA) used by users. This lets you query which users are configured for insecure SMS vs. more secure app-based 2FA.
cnquery> slack.users.where( has2FA == true ){ has2FA twoFactorType }
slack.users.where.list: [
0: {
twoFactorType: "app"
has2FA: true
}
]
Updated and certified CIS Google Kubernetes Engine (GKE) Benchmark policy
The CIS Google Kubernetes Engine (GKE) Benchmark policy has been enhanced with the following new checks and is now fully certified by CIS:
- 5.1.1 Ensure Image Vulnerability Scanning using GCR Container Analysis or a third party provider
- 5.6.4 Ensure clusters are created with Private Endpoint Enabled and Public Access Disabled
Smaller Mondoo package size
We've further optimized the Mondoo package to reduce the installation size by another 10MB.
🐛 BUG FIXES AND UPDATES
- Replace
mondoo shellwithcnspec shellin some policy audit instructions. - Improve remediation steps in Mondoo Azure, Google, and AWS policies.
- Fix
cnspec bundle fmtremovingscoring_systemfrom policies when converting between 7.x and 8.x formats. - Fix
cnspec bundle fmtnot properly parsing typed docs. - When scanning Kubernetes manifests containing resources without a namespace, don't create an unnamed namespace asset as the parent.
- Fix failures querying Azure Cloud Defender security contacts when none exist.
- Fix failure running
github.organization {*}query. - Fix CVSS aggregated score calculation in the
platform.advisoriesresource. - Fix some CIS Kubernetes policies not displaying in the Policy Hub.
- Improve ad-hoc scan instructions in AWS/Azure/GCP policies.
- Update CIS Azure AKS v.1.2 Pod Security Policy checks to only execute on Kubernetes < 1.25.
- Update Linux Security by Mondoo policy's
Ensure events that modify the system's Mandatory Access Controls are collectedcheck to expect a trailing slash in directories. Thanks @micheelengronne! - Remove the
runningandunknownstates shown in asset names in the console, which did not consistently or correctly show asset scan status. - Add missing impact scores to Windows Security by Mondoo policy.
- Fix the Kubernetes Operator not immediately scanning newly deployed workloads in a cluster.
- Update wording on the Azure and M365 integration pages to make it more clear that the .pem file needs to include both the certificate and the private key.
