Mondoo 7.3 is out!
🥳 Mondoo 7.3 is out! This release includes UI and policy improvements!
Get this release: Installation Docs | Package Downloads | Docker Container
🎉 NEW FEATURES
New Azure authentication options
Problem: You want to secure your Azure infrastructure, but you don't want to authenticate using less secure methods like token authentication.
Solution: Mondoo now includes additional options for authenticating against your Azure infrastructure, including those that enable security features such as MFA. You can now authenticate to your Azure infrastructure using certificates or a client ID and secret.
Certificate authentication:
cnquery shell azure --client-id <id> --certificate-path /Users/stella/certificate.pfx --tenant-id <tenant-id> --certificate-secret supersecret
Client ID/secret authentication:
cnquery shell azure --client-id <id> --tenant-id <tenant-id> --client-secret my_secret
If you don't specify an authentication method, Mondoo uses the method you've set up for the az CLI. So if you prefer shorter CLI commands, feel free to leave out the authentication flags entirely.
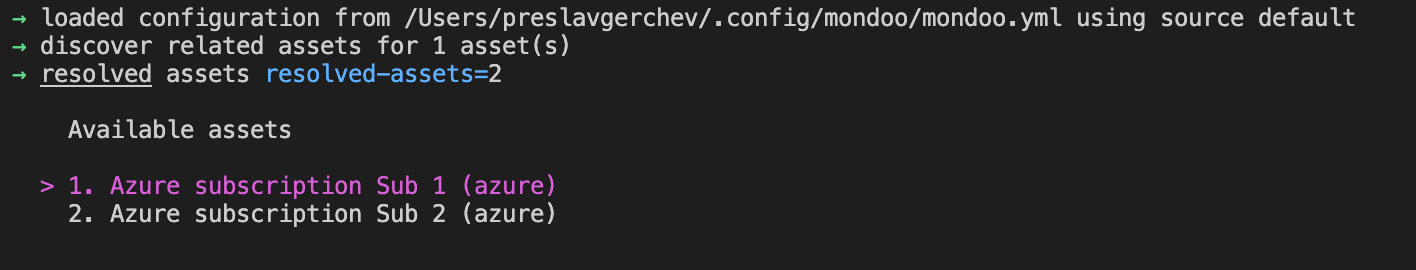
We also know you often have multiple subscriptions, so we've made it easy to select subscriptions. If the subscription flag is not set, you'll get a CLI menu of possible subscriptions to use:
Policies for OpenSSL
Problem: You want to apply a specific policy to find instances or containers running OpenSSL versions vulnerable to the recently announced CVE-2022-3786 and CVE-2022-3602 CVEs.
Solution: We've introduced a new policy, OpenSSL Vulnerability Policy by Mondoo, to specifically report on CVEs in OpenSSL so you can more easily target these systems for remediation.
🧹 IMPROVEMENTS
Status tabs on top of asset pages
Asset pages now include tabs for navigating between policies, controls, configuration, and vulnerabilities at the top of the page. Not only are these a bit easier to find here, the content of these tabs now shows on the whole screen so you can better explore the data.
Resource improvements
We continue to improve the cnquery resource to give you the best insight into servers, clouds, Kubernetes clusters, and more. This week we shipped the following fixes and improvements:
- Resolve errors running
github.repository { webhooks }if no webhooks were found. - Resolve errors running
aws.rds.dbClusters {*}. - Add
statedata to theaws.ec2.snapshotresource.
Policy improvements
This week we made several improvements to Linux and Kubernetes policies with new and updated controls:
- Added missing queries to controls in the AlmaLinux CIS benchmark.
- Added new
Limit the access of Pods to cloud metadata servicescontrol to theNSA Kubernetes Hardening Guide Version 1.2policy. - Added new
Minimize and verify access to secretscontrol to theNSA Kubernetes Hardening Guide Version 1.2policy. - Updated
Kubernetes Cluster and Workload Securitypolicy to avoid failures scanning Kubernetes master nodes.
🐛 BUG FIXES AND UPDATES
- Resolve failures loading base64 configs from env vars in cnspec.
- Resolve a panic when running cnspec in GitHub Actions.
- The install script now points users to GitHub Discussions not Slack.
- Improve cleanup of Kubernetes admissions controller scans older than 30 days to improve performance in spaces.
- EOL warning banners now show up on asset pages after an asset becomes EOL with the OS vendor.
- Show errors when policies cannot be uploaded to Policy Hub.
- Resolve errors with pagination on the asset not behaving as expected.
- Resolve incorrect links in Microsoft Teams notifications.
