Mondoo 7.12 is out!
🥳 Mondoo 7.12 is out! This release includes new GCP/Azure resources, New/Updated CIS Policies, AWS ECS scanning, and more!
Get this release: Installation Docs | Package Downloads | Docker Container
🎉 NEW FEATURES
New GCP and Azure resources
Problem: You want to explore and secure your GCP and Azure cloud accounts using cnquery and cnspec.
Solution: cnquery and cnspec now include new resources for securing GCP and Azure cloud services:
- NEW
azure.cloudDefenderresource - NEW
azure.sql.server.vulnerabilityassessmentresource - NEW
azure.authorization.roleDefinitionresource - NEW
azure.mysql.flexibleServerresource - NEW
azure.storage.account.queueService.propertiesresource - NEW
azure.storage.account.blobService.propertiesresource - NEW
azure.storage.account.tableService.propertiesresource - NEW
azure.storage.account.dataProtectionresource - NEW
azure.network.watcher.flowlogresource - NEW
azure.monitor.diagnosticSettingsresource - NEW
azure.monitor.activitylogresource - NEW
gcp.project.apiKeysresource - NEW
gcp.project.essentialContactsresource - NEW
gcp.project.loggingresource - NEW
gcp.project.sqlresource gcp.compute.firewallnow includesallowedanddenieddatagcp.compute.networknow includesmodedatagcp.project.clustersmoved togcp.project.gke.clusters
See the full documentation for all GCP resources in our GCP Resource Pack docs and Azure Resource Pack docs.
New and updated CIS policies
Problem: Your infrastructure is complex, with an ever growing number of operating systems you need to secure.
Solution: Mondoo now includes the latest macOS and Linux CIS policies with new policies for the latest OS releases.
New CIS policies:
- CIS Red Hat Enterprise Linux 9 Benchmark 9 1.0
- CIS AlmaLinux OS 9 Benchmark 1.0
- CIS Rocky Linux 9 Benchmark 1.0
- CIS Oracle Linux 9 Benchmark 1.0
- CIS Apple macOS 13.0 Ventura Benchmark 1.0.0
Updated CIS policies:
- CIS CentOS Linux 8 Benchmark updated from 1.0.1 to 2.0.0
- CIS Oracle Linux 8 Benchmark updated from 1.0.1 to 2.0.0
- CIS SUSE Linux Enterprise 11 Benchmark updated from 2.0.0 to 2.1.1
- CIS Apple macOS 10.15 Catalina Benchmark updated from 2.1.0 to 3.0.0
- CIS Apple macOS 11.0 Big Sur Benchmark updated from 2.1.0 to 3.0.0
- CIS Apple macOS 12.0 Monterey updated from 1.1.0 to 2.0.0
AWS ECS container scanning
You can now scan all AWS ECS containers when scanning your AWS account with a new --discover flag option, ecs. Use this flag with cnquery and cnspec to explore and secure ECS containers in your infrastructure.
Multiple login methods in the Mondoo Console
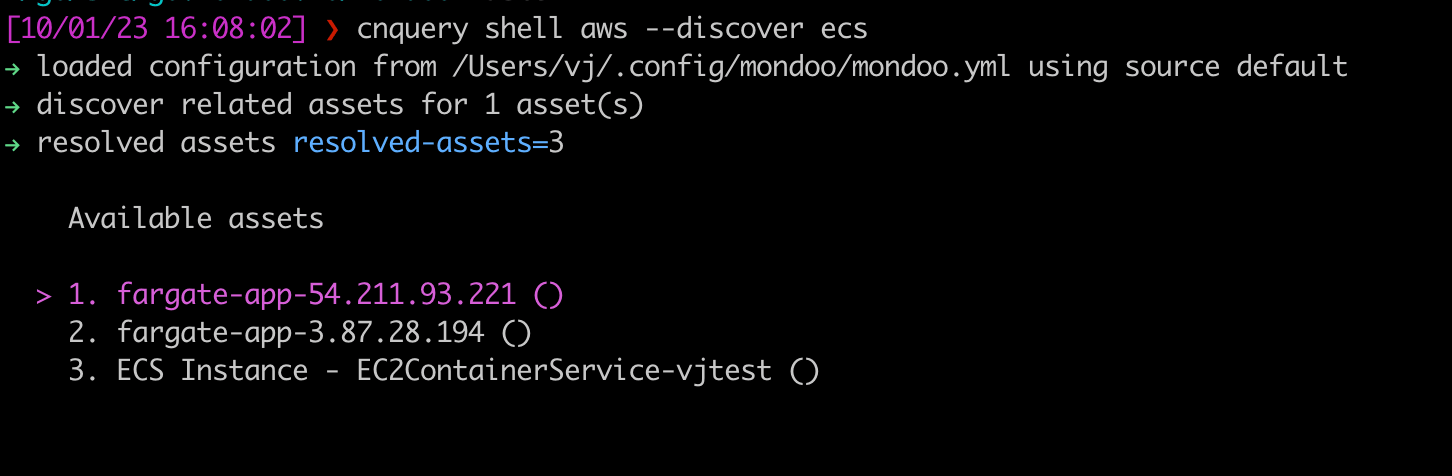
Problem: You signed up with your email account, and now you want to sign in with your Google, Microsoft, or GitHub login.
Solution: You can now add multiple authentication methods to your Mondoo Platform account, so you can log in with any combination of email, Microsoft, Google, or GitHub accounts.
To change your login method:
- In the top-right corner of the Mondoo Console, select your user icon.
- Select User Settings.
- In the left navigation, select Security. Under Connected Accounts, you can connect and disconnect accounts to update your login methods.
New scan summaries for multiple asset scans
Problem: cnspec scan output gives you quick insight into the security posture of assets. However, when scanning complex systems like Kubernetes clusters with hundreds or thousands of assets, there is often too much data to consume.
Solution: We've developed an all-new summary view for asset scans that allows you to more easily understand the security posture of complex systems like Kubernetes in cnspec.
An example scan of a small Kubernetes cluster:
Scanned 29 assets
Debian GNU/Linux 9 (stretch)
F index.docker.io/library/nginx@f7988fb6c02e
F index.docker.io/library/postgres@3f4441460029
Distroless
B registry.k8s.io/etcd@6f72b8515449
B registry.k8s.io/kube-apiserver@4188262a351f
B registry.k8s.io/kube-controller-manager@d3a06262256f
B registry.k8s.io/kube-proxy@6bf25f038543
B registry.k8s.io/kube-scheduler@f478aa916568
Kubernetes Cluster
F K8s Cluster minikube
Kubernetes DaemonSet
D kube-system/kube-proxy
Kubernetes Deployment
C kube-system/coredns
D luna/luna-frontend
D luna/postgres
Kubernetes Pod
C kube-system/coredns-565d847f94-b4pcx
C kube-system/etcd-minikube
D kube-system/kube-apiserver-minikube
D kube-system/kube-controller-manager-minikube
D kube-system/kube-proxy-bqthk
D kube-system/kube-scheduler-minikube
D kube-system/storage-provisioner
D luna/luna-frontend-7fb96c846b-jjnhz
D luna/luna-frontend-7fb96c846b-tmg95
D luna/luna-frontend-7fb96c846b-xrl6c
D luna/postgres-5bb9d69b96-d9zzg
Kubernetes ReplicaSet
C kube-system/coredns-565d847f94
D luna/luna-frontend-7fb96c846b
D luna/postgres-5bb9d69b96
D luna/postgres-655d75f54b
scratch
U gcr.io/k8s-minikube/storage-provisioner@18eb69d1418e
U registry.k8s.io/coredns/coredns@8e352a029d30
Summary
=======
Score Distribution Asset Distribution
------------------ ------------------
A 0 assets Kubernetes ReplicaSet 4
B 5 assets Kubernetes Pod 11
C 4 assets Kubernetes DaemonSet 1
D 15 assets Distroless 5
F 3 assets Kubernetes Cluster 1
U 2 assets scratch 2
Debian GNU/Linux 9 (stretch) 2
Kubernetes Deployment 3
For detailed output, run this scan with "-o full".
See more scan results and asset relationships on the Mondoo Console: https://console.mondoo.com/space/fleet?spaceId=lunalectric-prod-eks
Iterating over keys and values
MQL already supports accessing keys and values via key and value in maps:
> sshd.config.params.where( key == /p/ )
sshd.config.params.where: {
ChallengeResponseAuthentication: "no"
Ciphers: "aes256-ctr,aes192-ctr,aes128-ctr"
}
We've extended this support to include parsed JSON and YAML structures:
> parse.json("my.json").params.where( value == 1 )
parse.json.params.where: {
apples: 1.000000
oranges: 1.000000
}
You can use these structures to quickly filter maps via key and value or to make assertions. For example you can ensure that certain keys exist:
> parse.json("my.json").params.where( key == /or/ )
parse.json.params.where: {
"hawthorn berries": 16.000000
oranges: 1.000000
}
🧹 IMPROVEMENTS
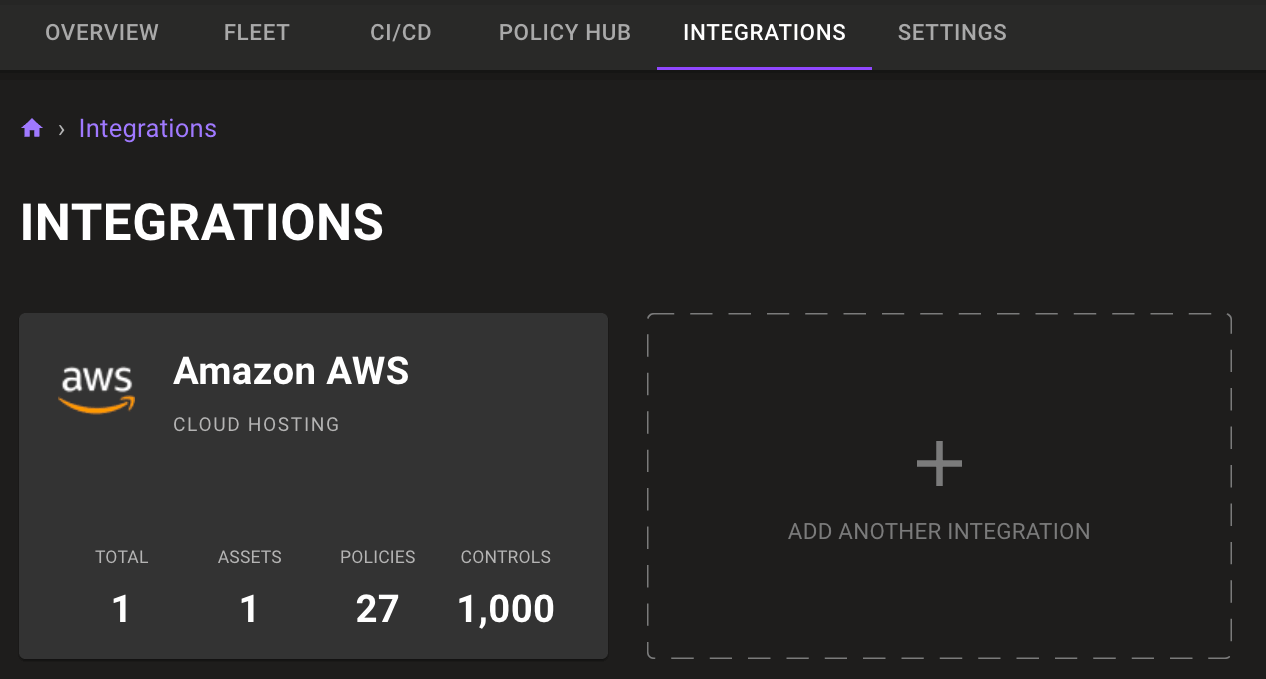
Asset counts on integration tiles
Integration tiles in the integration tab now show a summary of discovered assets, applied policies, and total applied controls. Now you can more easily see where assets are discovered.
Detect missing asset filters in cnspec bundle lint
cnspec bundle lint now includes a new check to ensure the policy's spec section includes an asset filter. This new check raises an error for policies that have no asset filter defined:
policies:
- uid: mondoo-azure-security
name: Microsoft Azure Security by Mondoo
version: 1.0.0
specs:
- scoring_queries:
mondoo-azure-security-ensure-os-disk-are-encrypted: null
mondoo-azure-security-ssh-access-restricted-from-internet: null
The policy should be updated with an asset filter like this:
policies:
- uid: mondoo-azure-security
name: Microsoft Azure Security by Mondoo
version: 1.0.0
specs:
- asset_filter:
query: |
platform.name == "azure"
platform.kind == "api"
scoring_queries:
mondoo-azure-security-ensure-os-disk-are-encrypted: null
mondoo-azure-security-ssh-access-restricted-from-internet: null
Expanded vault support for storing secrets
cnquery and cnspec now have expanded vault support for short-term secret storage when using inventory files. You can now store secrets with an in-memory vault or using GCP KMS encryption and GCP Cloud Storage through the Berglas project.
Example inventory file storing secrets with gcp-berglas:
apiVersion: v1
kind: Inventory
metadata:
name: inventory
spec:
assets:
- name: cool-stuff
connections:
- backend: 0
credentials:
- secret_id: storage/my-secrets/secret
type: 1
secret_encoding: 3
options:
discover:
targets:
- all
vault:
name: gcp-berglas
type: gcp-berglas
options:
project_id: id
Fine-grained control over Azure subscription scanning
You can now control particular Azure subscriptions to include or exclude during scans with new --subscriptions and --subscriptions-exclude flags. You can use these new flags to control which subscriptions you want to inspect. For example, to run the cnquery shell on all subscriptions except for two, you can exclude those subscriptions explicitly: cnquery shell azure --subscriptions-exclude=984df67f-fc2e-4ebf-80a2-1234567891011,1e829eb0-e6a3-4c7b-8212-1234567891011
🐛 BUG FIXES AND UPDATES
- Show better results for failures in the
Google Cloud (GCP) Security by Mondoopolicy. - Only check SSH server configuration when the SSH server is installed in the
Linux Server Security by Mondoo. Thanks. @stdevel! - Avoid failures when the Kubernetes Ingress has no certificates.
- Fix queries in
Linux Workstation Security by Mondoo,BSI SYS.1.2 Windows Server, andAmazon Web Services (AWS) Operational Best Practices,CIS Distribution Independent Linux Benchmark, andCIS VMware ESXi 6.7 Benchmarkpolicies that were not executing. - Don't show a policy lint error if the policy spec has either scoring queries or data queries attached.
- Improve reliability when scanning instances using SSM in cnquery, cnspec, and the Mondoo AWS Integration.
- Better describe when a directory of Terraform or Kubernetes files is scanned.
- Improve reliability in MQL queries that execute commands concurrently.
- Don't silently fail to run the
socketstatsresource when it's not supported. - Improve the reliability of scanning ECR images.
