Mondoo 7.11 is out!
🥳 Mondoo 7.11 is out! This release includes new GCP resources, GitHub Code Scanning of policies, and simplified Windows deployment!
Get this release: Installation Docs | Package Downloads | Docker Container
🎉 NEW FEATURES
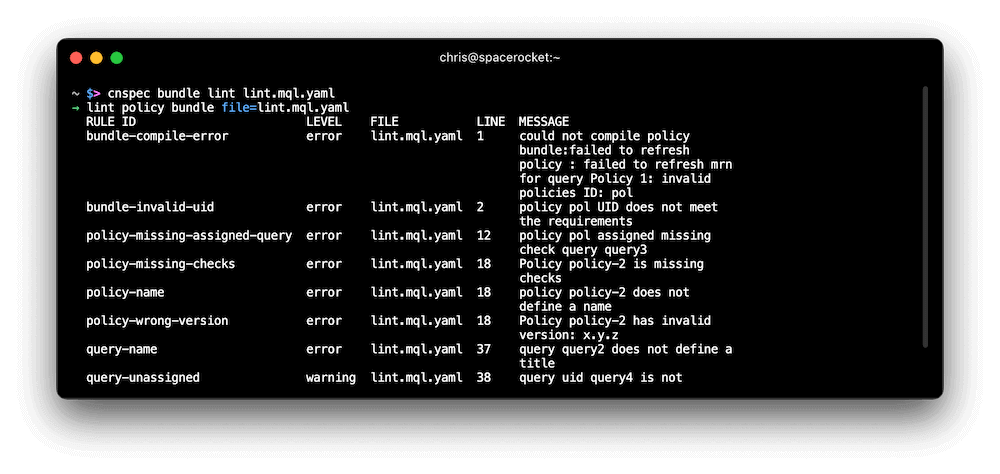
MQL policy linting
Problem: Custom MQL policies can become large quickly, making it difficult to make sure they are properly formatted.
Solution: cnspec now includes a new cnspec bundle lint command that helps you find incorrectly formatted policies. This new command checks for the following conditions:
- MQL compile error
- UID is not valid
- Missing policy UID
- Missing policy name
- No unique policy UID
- Policy is missing checks
- Assigned query missing
- Policy version is missing
- Policy version is invalid
- Missing query UID
- Missing query title
- No unique query UID
- Unassigned query
But wait, there's more! This new linting works with GitHub Code Scanning through our Mondoo GitHub Action. Applying the updated action scans your repository for Mondoo policies, annotates pull requests with any problems it finds, and even opens GitHub Code Scanning issues for problems.
The action is compact and doesn't require a service account or any other additional setup:
---
name: Lint Policies
on:
pull_request:
push:
branches:
- main
jobs:
build:
runs-on: ubuntu-latest
steps:
- name: Checkout repository
uses: actions/checkout@v3
- name: Lint cnspec policies and output SARIF
uses: mondoohq/actions/cnspec-lint@main
with:
path: .
output-file: "results.sarif"
- name: Upload SARIF results file
uses: github/codeql-action/upload-sarif@v2
with:
sarif_file: results.sarif
This action scans each opened PR and merge, giving you annotations directly in the GitHub UI:
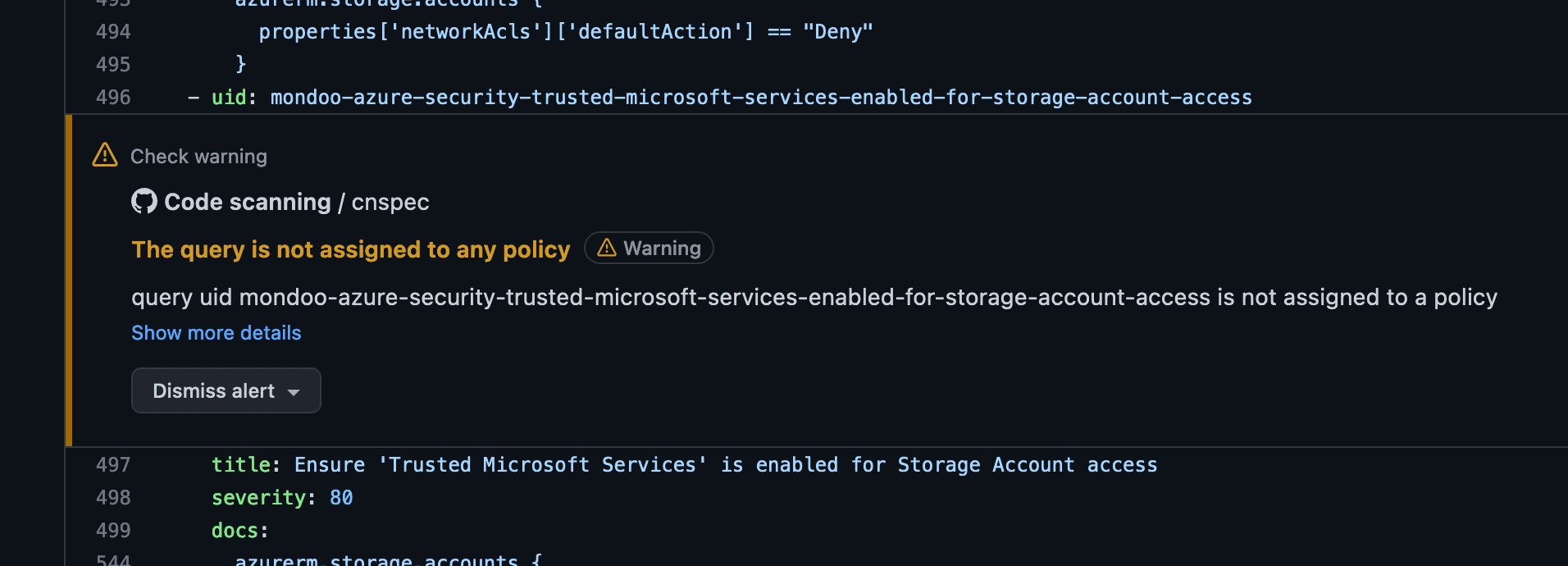
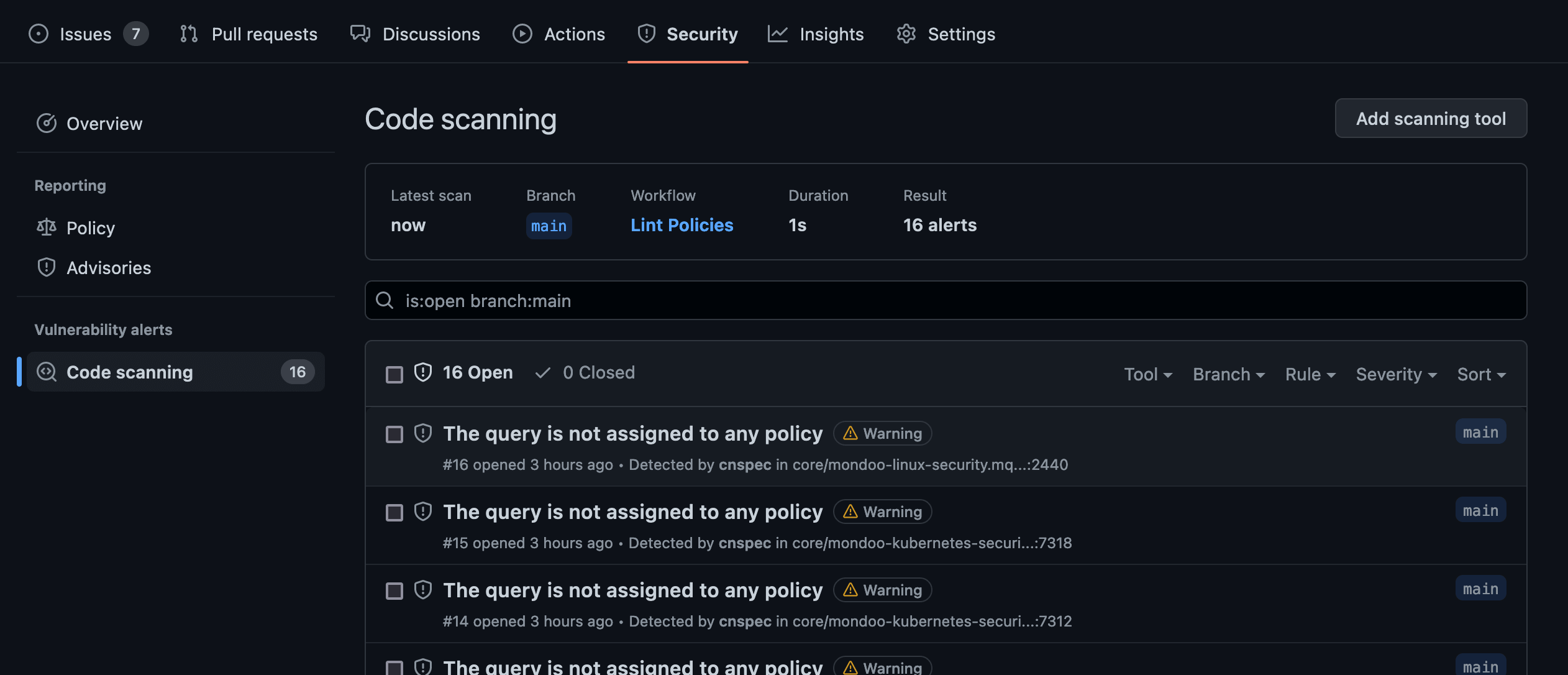
The GitHub Action integrates with GitHub Code Scanning to open GitHub Code Scanning issues for each problem in your policy:
New GCP resources
Problem: You want to explore and secure your GCP Pub/Sub and KMS services using cnquery and cnspec.
Solution: cnquery and cnspec now include new resources for securing GCP Pub/Sub and KMS services.
We added new resources to query GCP KMS Key Rings and their cryptographic keys:
cnquery> gcp.project.kms.keyrings { * }
gcp.project.kms.keyrings: [
0: {
resourcePath: "projects/example-project/locations/global/keyRings/testring"
created: 2022-12-19 15:17:46.974842182 +0000 UTC
projectId: "example-project"
cryptokeys: [
0: gcp.project.kmsService.keyring.cryptokey name="testring-key" purpose="ENCRYPT_DECRYPT"
]
name: "testring"
location: "global"
}
]
Inspect details for Crypto Keys:
cnquery> gcp.project.kms.keyrings { name cryptokeys { * } }
gcp.project.kms.keyrings: [
0: {
name: "testring"
cryptokeys: [
0: {
purpose: "ENCRYPT_DECRYPT"
resourcePath: "projects/example-project/locations/global/keyRings/testring/cryptoKeys/testring-key"
versions: [
0: gcp.project.kmsService.keyring.cryptokey.version name="1" state="ENABLED"
]
name: "testring-key"
primary: gcp.project.kmsService.keyring.cryptokey.version name="1" state="ENABLED"
}
]
}
]
We also added support for GCP Pubsub Subscriptions, Topics and Snapshots:
cnquery> gcp.project.pubsub { * }
gcp.project.pubsub: {
topics: [
0: gcp.project.pubsubService.topic name="gke-cluster-event-queue"
]
snapshots: []
projectId: "example-project"
subscriptions: [
0: gcp.project.pubsubService.subscription name="gke-cluster-event-queue-subscription"
]
}
See full documentation for all GCP resources in our GCP Resource Pack docs.
Mondoo installation PowerShell module
Problem: You need to deploy trusted binaries from Mondoo to Windows hosts using Active Directory Group Policy or MDM solutions.
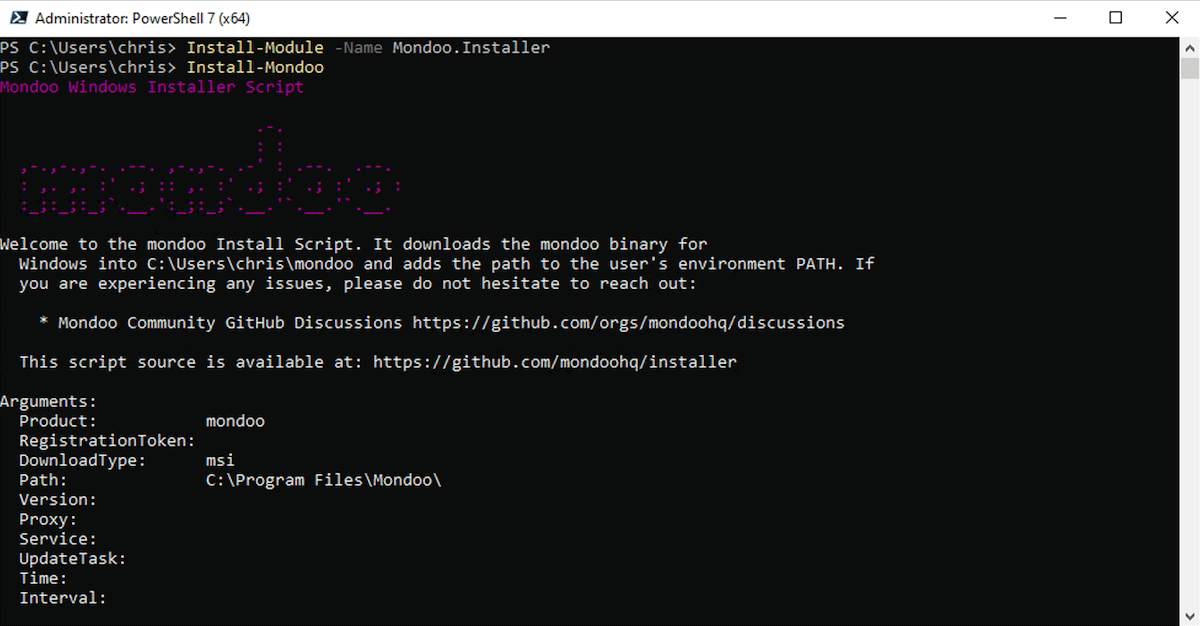
Solution: You can now install Mondoo using a new Mondoo.Installer signed PowerShell module that is published on the PowerShell Gallery at https://www.powershellgallery.com/packages/Mondoo.Installer/1.0. You can use this new signed module to deploy Mondoo CLIs to managed Windows hosts by running Install-Mondoo.
Install-Module -Name Mondoo.Installer
Install-Mondoo
Because our scripts and binaries are fully signed, the rollout of cnquery and cnspec was never easier. The module automatically validates if the latest version is already installed, or it updates to the newest version if required:
After the installation script is complete, cnquery and cnspec are available for use:

🧹 IMPROVEMENTS
Detect expiring certs in Kubernetes Ingresses
A new Ingress certificates less than 15 days from expiration query in the Kubernetes Best Practices by Mondoo policy detects certificates nearing their expiration data in your Kubernetes cluster. This query looks at all certificates defined in a Kubernetes Ingress resource that are stored as a Secret and fails when the expiration data is less than 15 days.
Better asset scanning with the Mondoo AWS Lambda integration
The Mondoo AWS integration has been improved to better scan large and complex AWS environments:
- Scan regions with more than 1,000 running instances.
- Use AWS Instance Connect to scan instances if SSH scans fail.
Add cnquery/cnspec to the integrations page
You can now set up cnquery and cnspec to communicate with Mondoo Platform directly on the Integrations page of the console.
🐛 BUG FIXES AND UPDATES
- Fix some help descriptions not being displayed.
- Don't cut off the beginning of some help descriptions.
- Using two or more search filters in the console requires all filters to match instead of just one.
- Allow organization owners to delete invites.
- Improve the default output of the
kernelresource. - Fix
terraform.modulenot discovering all modules. - Fix invalid command examples in some console integration pages.
- Update Workstation integrations page text to better match terms used by cloud vendors.
