Mondoo 7.10 is out!
🥳 Mondoo 7.10 is out! This release includes support for K8s Ingress certificates and a resource for GCP GKE clusters!
Get this release: Installation Docs | Package Downloads | Docker Container
🎉 NEW FEATURES
New GCP GKE resource
Problem: You've secured your Kubernetes workloads and kubelet configs with Mondoo and NSA Kubernetes security policies, but you need to secure your GKE cluster configuration as well.
Solution: A new gcp.project.clusters resource lets you explore your GKE clusters and write policies to secure your cluster control plane.
cnquery> gcp.project.clusters { * }
gcp.project.clusters: [
0: {
resourceLabels: {}
name: "luna-gke-cluster-2"
projectId: "luna-edge"
locations: [
0: "us-central1-b"
1: "us-central1-c"
2: "us-central1-f"
]
created: 2022-12-15 20:43:41 +0000 +0000
status: "RUNNING"
zone: "us-central1"
description: ""
nodePools: [
0: gcp.project.cluster.nodepool name="generic-pool"
]
loggingService: "logging.googleapis.com/kubernetes"
expirationTime: null
enableKubernetesAlpha: false
initialClusterVersion: "1.24.5-gke.600"
network: "luna-gke-cluster-2"
clusterIpv4Cidr: "10.20.0.0/16"
autopilotEnabled: false
endpoint: "63.192.209.236"
currentMasterVersion: "1.24.5-gke.600"
id: "123abcbcada644fcb3b83c30ea0efcfc3cd6d8f42a814bccbcb3503181e12b5a"
subnetwork: "luna-gke-cluster-2-subnet"
monitoringService: "monitoring.googleapis.com/kubernetes"
}
]
Examine Kubernetes Ingress certificates
Problem: You've secured your Kubernetes Ingresses with the new k8s.ingress resource, but you need to examine and secure the certificates associated with those Ingresses as well.
Solution: A new k8s.ingress.certificates resource allows you to explore and secure certificates associated with Kubernetes Ingress objects.
$ ./cnquery run k8s --discover ingresses -c
'k8s.ingress.certificates{ expiresIn }'
→ discover related assets for 1 asset(s)
→ use cluster name from kube config cluster-name=minikube
→ resolved assets resolved-assets=1
k8s.ingress.certificates: [
0: {
expiresIn: 12 days 2 hours 12 minutes 14 seconds
}
]
🧹 IMPROVEMENTS
Continued migration to cnspec
Our migration from the legacy Mondoo CLI to cnspec continues this week with CI and Kubernetes. CI integration examples in the console now show simpler cnspec steps, and the Mondoo Kubernetes Operator uses the new cnspec container images for all cluster scans. Stay tuned as we continue to migrate to our improved open source cnspec CLI over the coming weeks.
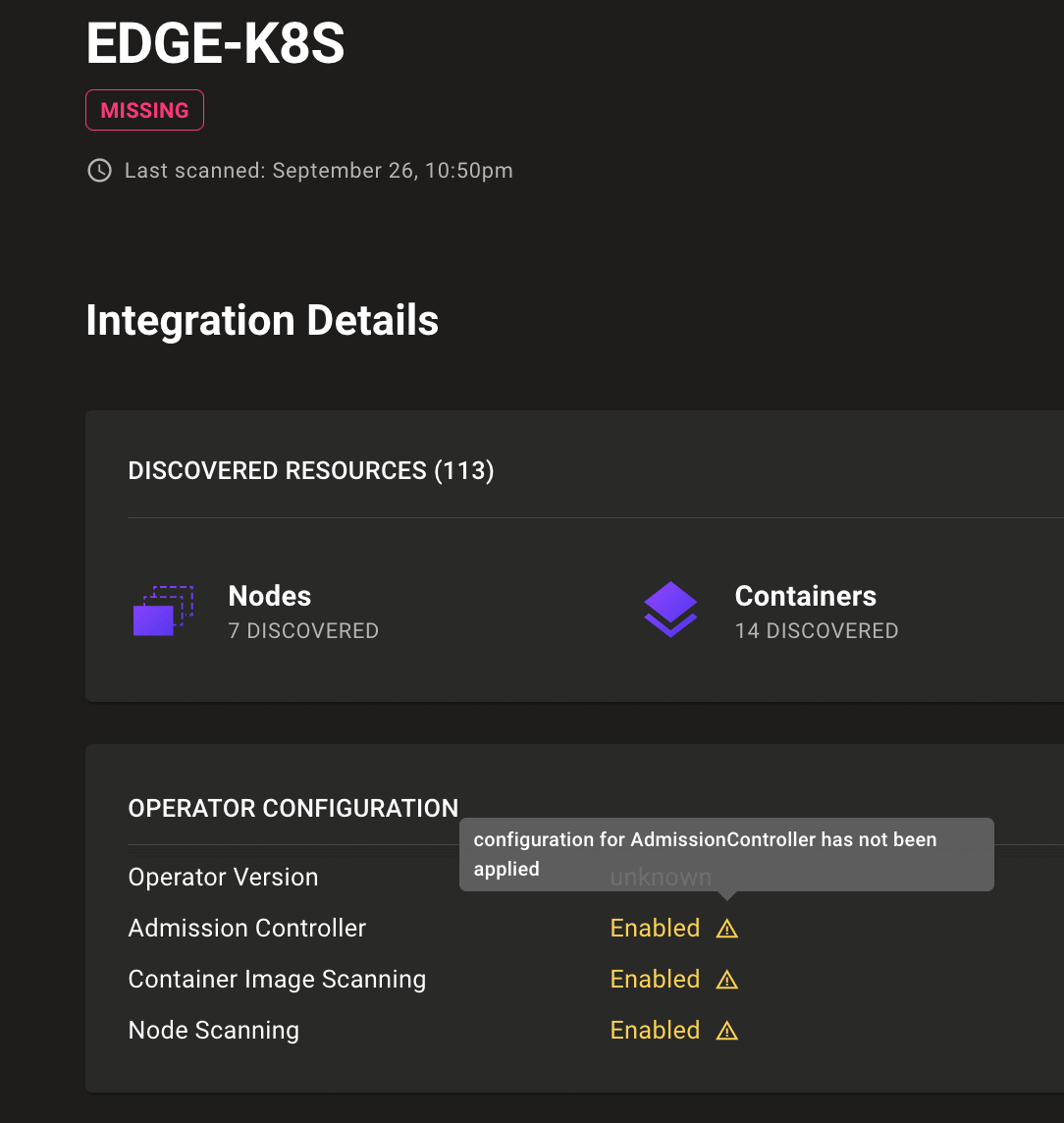
See errors from the Kubernetes operator
Kubernetes integration pages show any errors reported by the Mondoo Kubernetes Operator so you can more easily troubleshoot operator failures.
Improved help descriptions
cnspec and cnquery now include improved help and resource descriptions: We've improved many command descriptions to help new users, added descriptions for many resources, and removed some invalid resources that were showing up in auto-complete in the cnquery/cnspec shells.
🐛 BUG FIXES AND UPDATES
- Fix MachineType error in
gcp.compute.instancesresource. - Fix integer comparisons in MQL failing when resources returned a 32-bit integer instead of the assumed 64-bit integer.
- Allow users to navigate the console tabs with the keyboard.
- Allow users to upload policies that use alternative YAML MIME types to the Policy Hub.
- Fix errors in
Ensure default user umask is 027 or more restrictiveandEnsure default user umask is configuredcontrols within Mondoo and CIS Linux policies.
