Mondoo 6.17 is out!
🥳 Mondoo 6.17 is out! This release includes a new asset explorer UI and Kubernetes MQL resources!
Get this release: Installation Docs | Package Downloads | Docker Container
🎉 NEW FEATURES
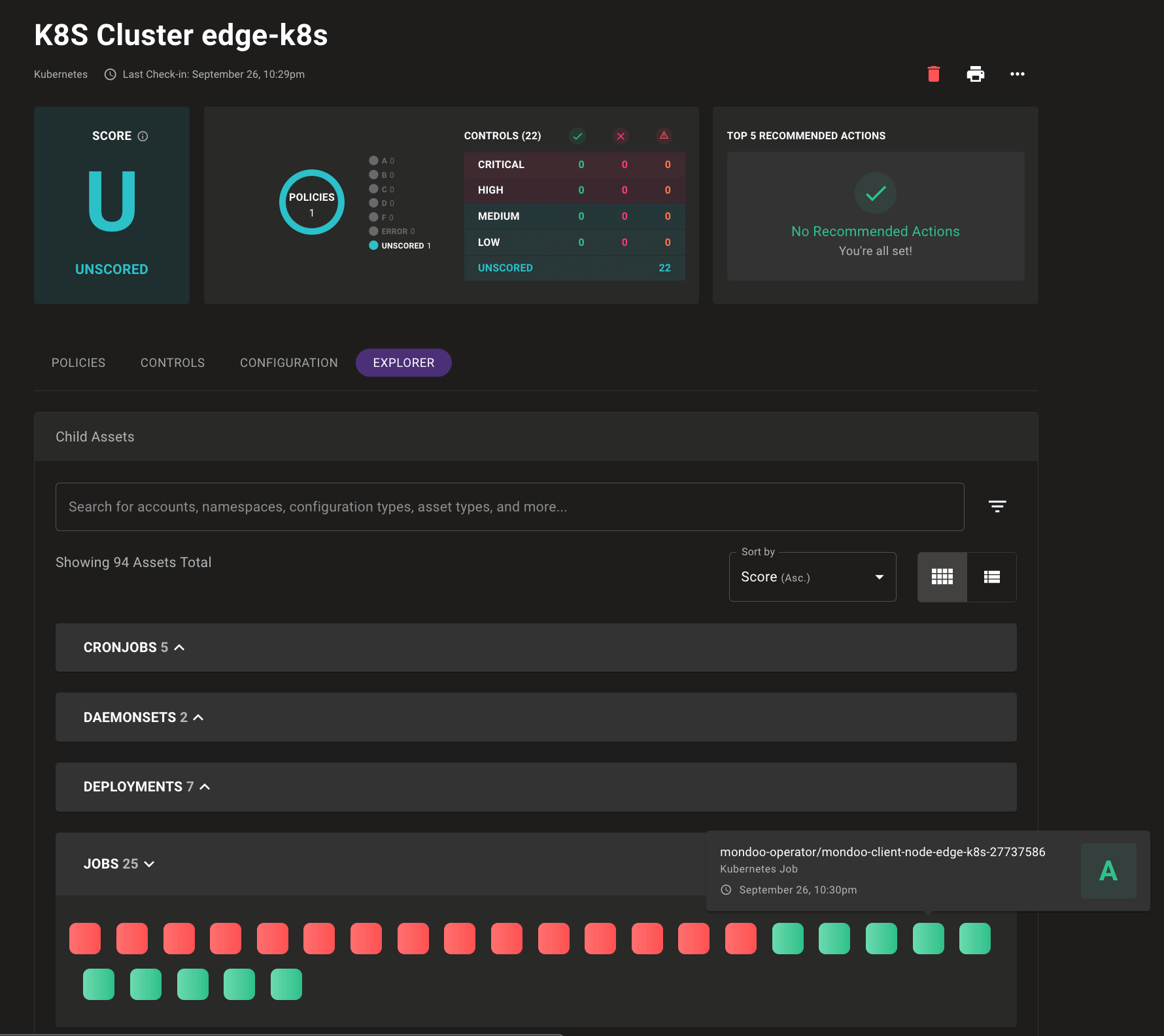
Explore Asset Relationships
Problem: Your environment is complex, and so is the job of securing it. You want to understand not just the security of a single asset, but how each asset relates to your overall infrastructure security.
Solution: Mondoo now exposes the complex relationships that make up your infrastructure security in a new Explorer tab for each asset. The Explorer view lets you quickly evaluate the security of related assets so you can better understand the security of complex infrastructure like cloud accounts or Kubernetes clusters. Each related asset is shown as a color-coded tile, which you can hover over for additional scan information. Here we see the results of Kubernetes job scans, including a Mondoo Operator job, which scored an A:
Bundesamt für Sicherheit in der Informationstechnik (BSI) Windows Policy
Problem: You want to secure your Windows systems according to the Federal Office for Information Security (BSI) and pass a BSI audit.
Solution: Mondoo now includes a new BSI SYS.1.2 Windows Server 2016/2019/2022 policy. BSI is a German standard for IT security, similar to SOC 2 in the US. This new policy complements our existing BSI SYS.1.3 Linux and Unix Servers policy for Debian- and Red Hat-based Linux systems. These policies are especially helpful for users in the DACH region and Germany in particular.
Automatic Cleanup of Kubernetes Resources
Problem: Resources come and resources go, but they sure add up quickly. Kubernetes clusters often contain large numbers of ephemeral resources, and over time Mondoo's scanning of resources results in spaces full of long-dead assets.
Solution:
Mondoo now automatically cleans up Kubernetes assets older than 24 hours, keeping your spaces tidy and full of relevant scans.
New k8s.admissionreview and k8s.admissionrequest Resources
Problem: You want to write policies against incoming Kubernetes deployments to understand the security of the deployment request itself.
Solution: Mondoo now includes new k8s.admissionreview and k8s.admissionrequest resources that allow you to write policies against incoming deployments. Stay tuned as we expand this functionality over time to allow additional control over the workloads that make it into your cluster.
New k8s.kubelet Resource
Problem: You need to secure your Kubernetes cluster nodes to secure your infrastructure, but the Kubelet configuration system is complex. How do you handle the different names for the same configs and different defaults depending on the config location? Should you check the CLI flags, the YAML config, or the JSON config?
Solution: We've abstracted the complexity of parsing the Kubelet config options into a new k8s.kubelet resource. The resource parses all three configuration locations, handles defaults, and understands the changing default values when config files are loaded. With this resource, you can write simple queries to check for Kubelet config options and let Mondoo handle the heavy lifting of parsing Kubernetes configuration logic.
A manual query that does not account for default values:
if (props.kubeletconfigpath != null) {
cfg = parse.yaml(props.kubeletconfigpath).params
cfg["featureGates"]["RotateKubeletServerCertificate"] != null
cfg["featureGates"]["RotateKubeletServerCertificate"] == true
} else {
processes.where( executable.contains("kubelet")).all(flags["feature-gates"] == "RotateKubeletServerCertificate=true")
}
An updated query that includes default value evaluation:
k8s.kubelet.configuration["featureGates"]["RotateKubeletServerCertificate"] == true
We've also updated our existing Kubernetes policies to use this new resource. This dramatically improves the reliability of configuration parsing in these policies, removing potential false positives.
🧹 IMPROVEMENTS
env and envFrom in Kubernetes Container Resources
Problem: You want to write policies to ensure that only secure environment variables are passed into your Kubernetes workloads.
Solution: Container resources now expose the env and envFrom configs. This allows you to inspect manifests with plain text secrets being passed in via env vars like this:
apiVersion: v1
kind: Pod
metadata:
name: luna-frontend
namespace: prod
spec:
containers:
- name: luna-frontend
image: lunalectric/frontend:1.0
env:
- name: LOGIN
value: "oh_no"
- name: PASSWORD
value: "they_are_really_doing_this!"
Using a query to check for env var names:
k8s.pods.all(
containers.all(
env["LOGIN"] == null && env["PASSWORD"] == null
)
)
Expanded Kubernetes Security & Best Practices Policies
We continue to expand our Kubernetes Security Benchmark policy to better secure workloads in your clusters. This week we added two new controls:
Pods should mount any host path volumes as read-only: Ensures that pods don't have write access to paths on the cluster node, which would allow modifying the host configuration.Pods should not bind to a host port: Ensures pods aren't binding directly to cluster nodes where they can bypass network controls.
mondoo exec Is Now mondoo run
We've updated the mondoo exec command to be mondoo run. The existing command will still work, but help will show just mondoo run. We're making this change to align CLI options for some exciting new releases coming soon. Stay tuned for more updates!
🐛 BUG FIXES AND UPDATES
- GitHub, Terraform, and cloud Kubernetes policies in the Policy Hub now include custom icons.
- Updates
Pods should not run with NET_RAW capabilityandPods should not run with SYS_ADMIN capabilitycontrols in the Mondoo Kubernetes Security policy to not fail when nosecurityContextorcapabilitiesare defined. - Resolves failures in
Minimize the admission of root containersandMinimize the admission of containers with the NET_RAW capabilitycontrols in CIS Kubernetes policies. - Asset view once again includes the state of the asset's Mondoo Client.
- Long policy names now truncate better in the asset view.
- The
--optioncommand line flag is now properly passed through to AWS EBS-based scans. - The
--tokencommand line flag is now properly set when scanning GitHub organizations or repositories. - Scans in the CI/CD view no longer appear unscored.
- Kubernetes cluster nodes are no longer part of the
k8s-workloadfamily. - Prevents failures checking kernel parameters if files in
/proc/syscannot be read.
