Mondoo 6.16 is out!
🥳 Mondoo 6.16 is out! This release includes new policies and always-up-to-date Kubernetes results.
Get this release: Installation Docs | Package Downloads | Docker Container
🎉 NEW FEATURES
Scan Kubernetes Resources on Add/Update
Problem: You rapidly deploy new and updated workloads to your Kubernetes cluster and you want to know that the Mondoo scan results reflect the latest state of your cluster.
Solution: Mondoo now scans your Kubernetes resources as they are updated or added to the cluster, so the fleet view always has the latest information on cluster-wide security.
Note: This requires the Mondoo Operator for Kubernetes 1.5 or later. To update to this new release run:
kubectl delete --ignore-not-found -n mondoo-operator deployment mondoo-operator-controller-manager
kubectl apply -f https://install.mondoo.com/k8s/operator
Mondoo Policy for Google Cloud Terraform Plans
Problem: You want to find Google Cloud security issues early in your infrastructure development cycle to prevent insecure changes from ever reaching production.
Solution: This week, we're introducing a new policy, Terraform Plan - CIS Google Cloud Platform Foundation Benchmark. It lets you run Mondoo security scans directly against HashiCorp Terraform plans for your Google Cloud infrastructure.
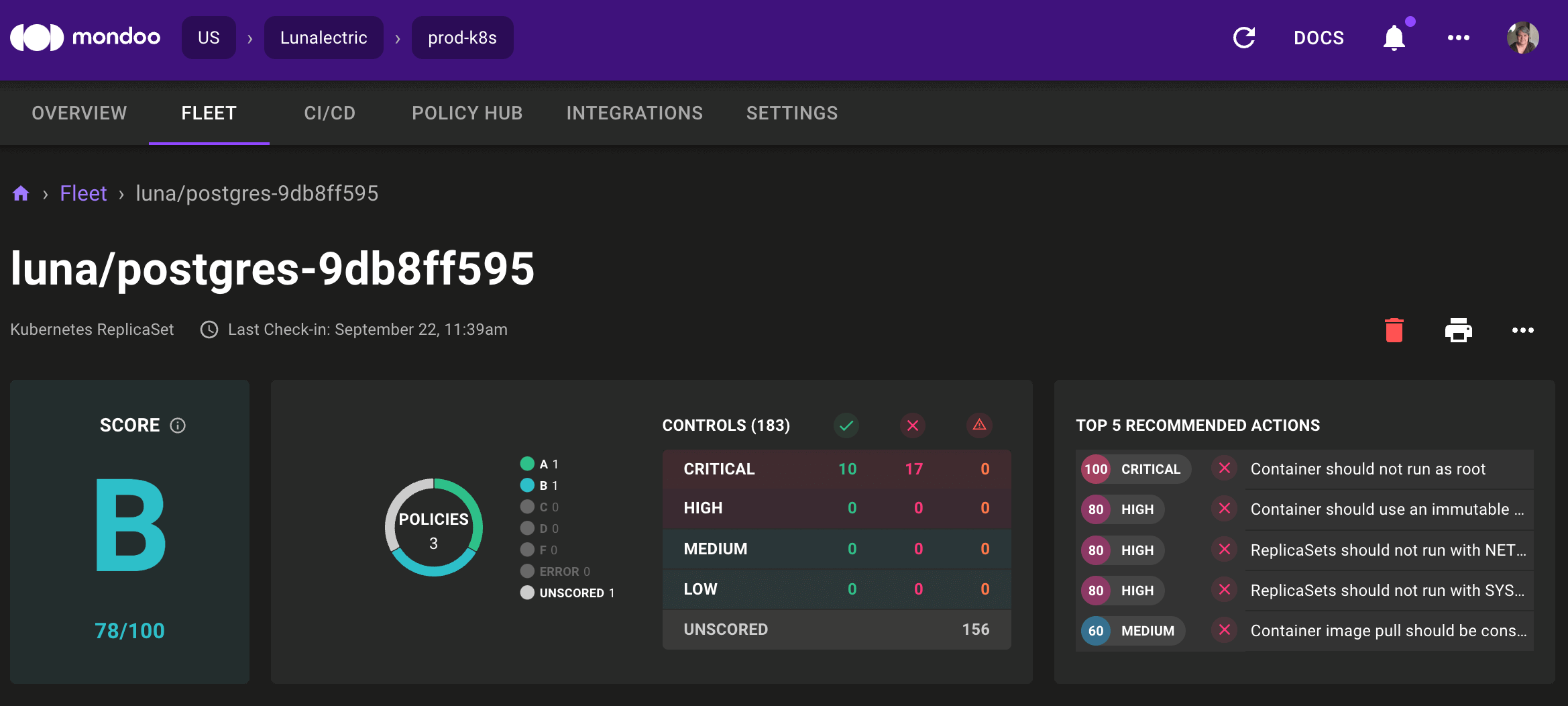
Top Five Recommended Actions
Problem: Mondoo found a lot of security issues for your asset and you're overwhelmed. It's hard to know what to fix first.
Solution: The asset view now shows the five most important actions you should take to improve an asset's security.
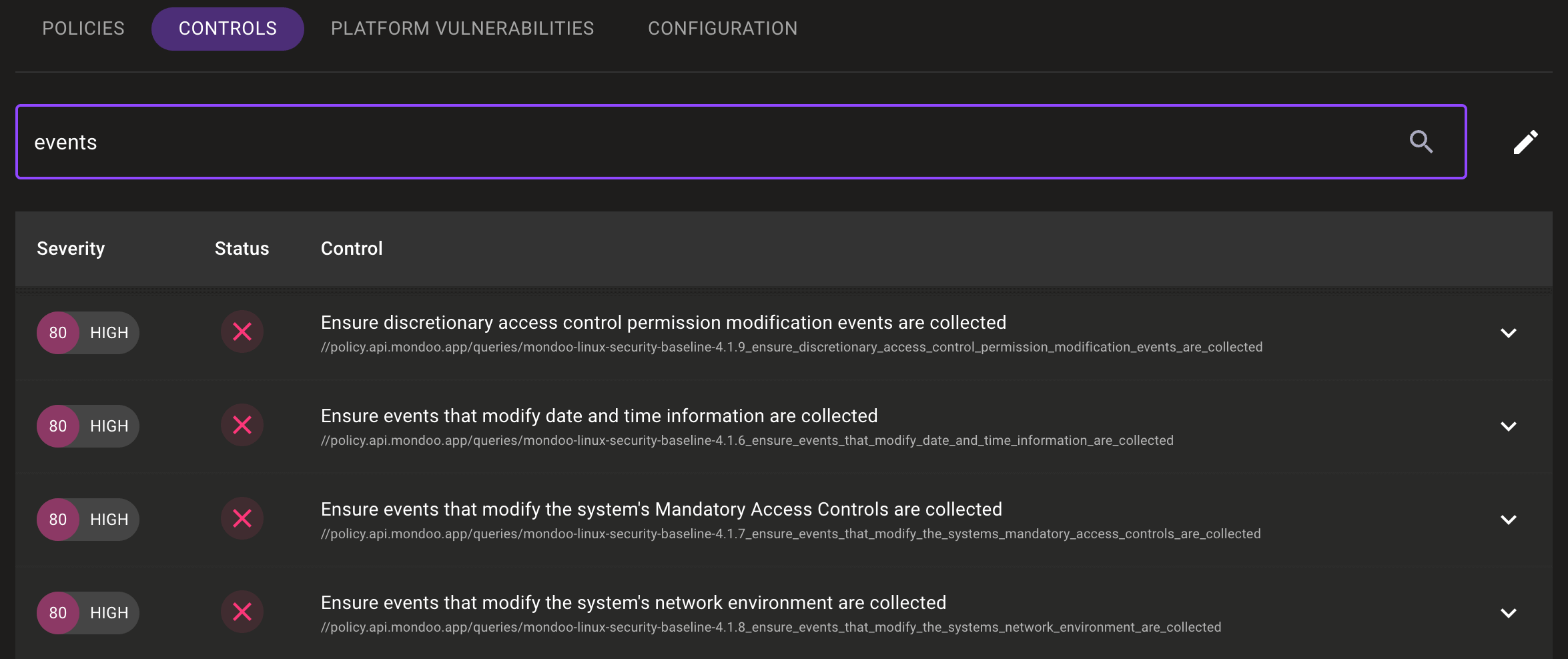
View All Controls for an Asset
Problem: You want to find a specific control that is applied to an asset, but you don't know which policy it's in.
Solution: Mondoo now lists all of an asset's controls independently from their policies. You can filter controls by policy or by search string.
🧹 IMPROVEMENTS
New Security and Best Practices Controls for Kubernetes
Problem: You want to scan your workloads for common security and best practice misconfigurations before deploying them to your Kubernetes cluster.
Solution: We've expanded our Kubernetes Security Benchmark and Kubernetes Best Practices Benchmark to expose more common misconfigurations in Kubernetes workloads.
-
Workloads should not run in the default namespace—This new Kubernetes Best Practices Benchmark control discovers workloads that haven't defined a non-default namespace in which to run. It's best to group workloads into non-default namespaces to better organize work by teams and to isolate workloads.
-
Workloads should not run with SYS_ADMIN capability—This new Kubernetes Security Benchmark policy discovers workloads with the SYS_ADMIN or ALL capabilities. The SYS_ADMIN capability is risky because it provides a pod with root capabilities.
-
Workloads should not run with NET_RAW capability—This new Kubernetes Security Benchmark policy discovers workloads with the NET_RAW or ALL capabilities. Attackers can use the NET_RAW capability to craft fake packets on the host, which they can use to redirect network traffic bound for other pods.
-
Pods should have an owner—This new Kubernetes Best Practices Benchmark control discovers pods that do not have an owner. These pods, commonly called naked pods, don't respawn if the node they're running on fails or terminates.
BIOS Updates Control Added to Client Linux Security Baseline by Mondoo
Problem: To secure the boot process, you need to ensure that all Linux systems have the most up-to-date BIOS releases.
Solution: The Client Linux Security Baseline by Mondoo now includes a control to validate that systems have the most up-to-date BIOS when the fwupd utility is installed.
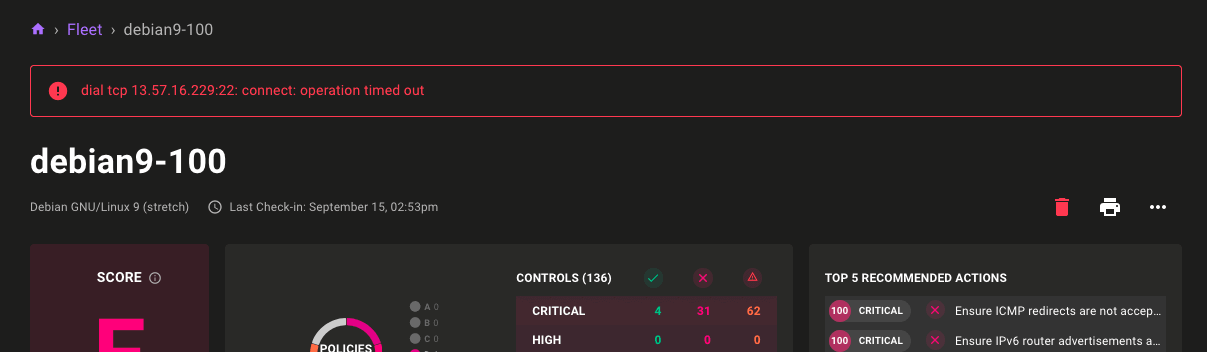
Error Messages for Unavailable Assets
Problem: You need to know when Mondoo can't connect to an asset. Solution: Mondoo now shows an error message on the asset page when it fails to reach the asset.
🐛 BUG FIXES AND UPDATES
- Renames potentially confusing control titles in Linux Security Baseline by Mondoo policy.
- Skips internal fields in the
mondoo shellhelp output. - Improves error handling in the AWS Lambda scans.
- Changes Mondoo agent searches to not be case sensitive.
- Returns more helpful error messages from Mondoo Client when a necessary environment variable is missing on CI platforms.
- Fixes missing available packages in asset Platform Vulnerabilities pages.
- Improves the handling of null data for regular data types: We now consistently return non-null data from the upstream service. In the next major release, we will support storing other null data.
- Fixes failures parsing Linux kernel parameters when files in
/proc/syscan't be read. - Networks and domains are now properly grouped in the fleet view.
