Mondoo 9.8 is out!
🥳 Mondoo 9.8 is out! This release includes automated compliance inventory gathering, AIX support, a new CVE view, plus a whole lot more!
Get this release: Installation Docs | Package Downloads | Docker Container
🎉 NEW FEATURES
Automated compliance inventory gathering
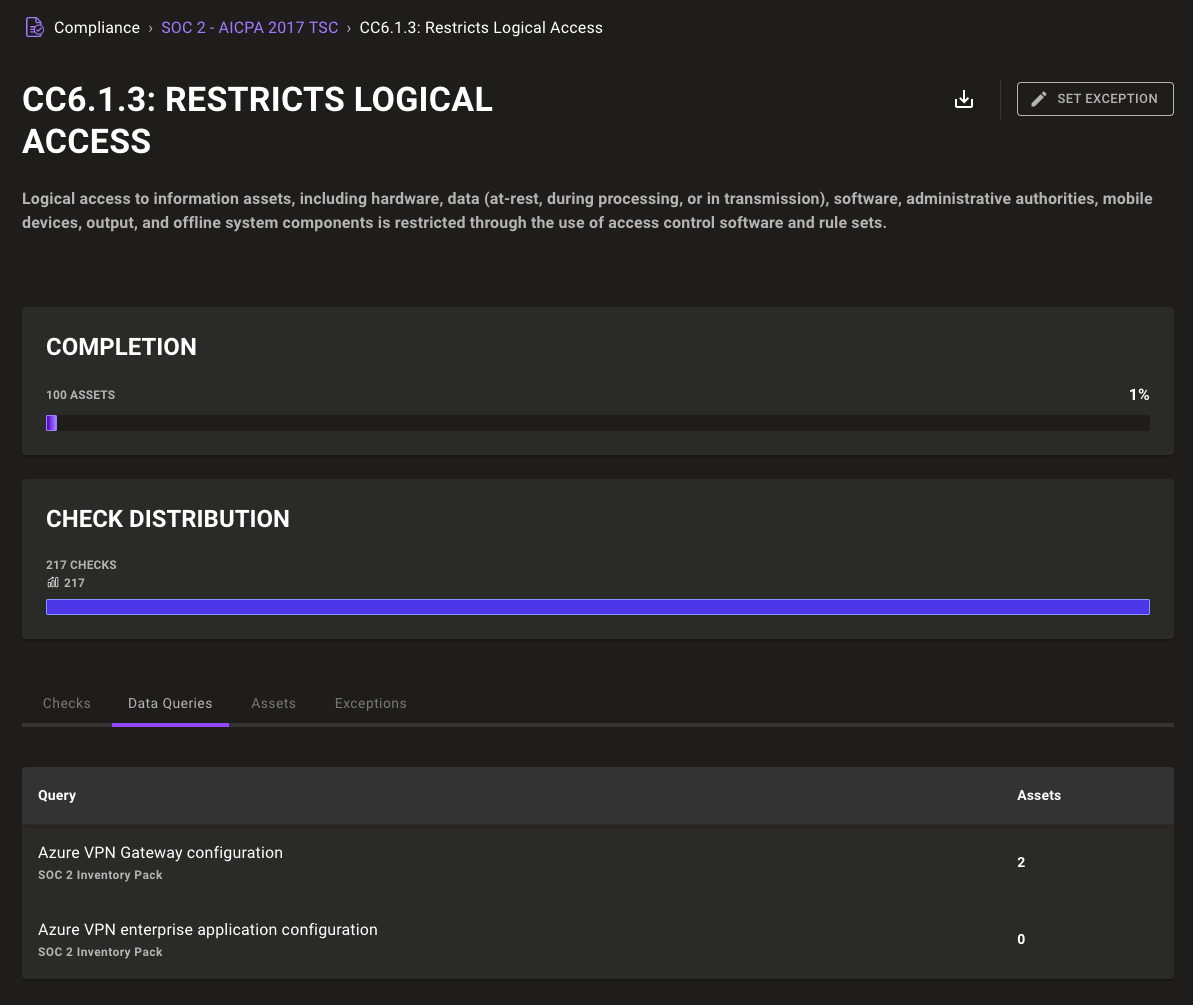
Your audit goes beyond security checks; now so does Mondoo, with continuous infrastructure inventory gathering mapped automatically to top compliance frameworks. Compliance Hub controls now include a Data Queries tab listing inventory data from query packs. This inventory data is gathered automatically from the cnspec CLI or from integrations like AWS, GitHub, or Kubernetes. Inventory data fills key requirements from auditors to ensure your infrastructure is compliant, such as gathering AWS VPC configuration to prove SOC 2 CC6.1.5 or asset inventory data for CC6.1.1.
SOC 2 control with data queries:
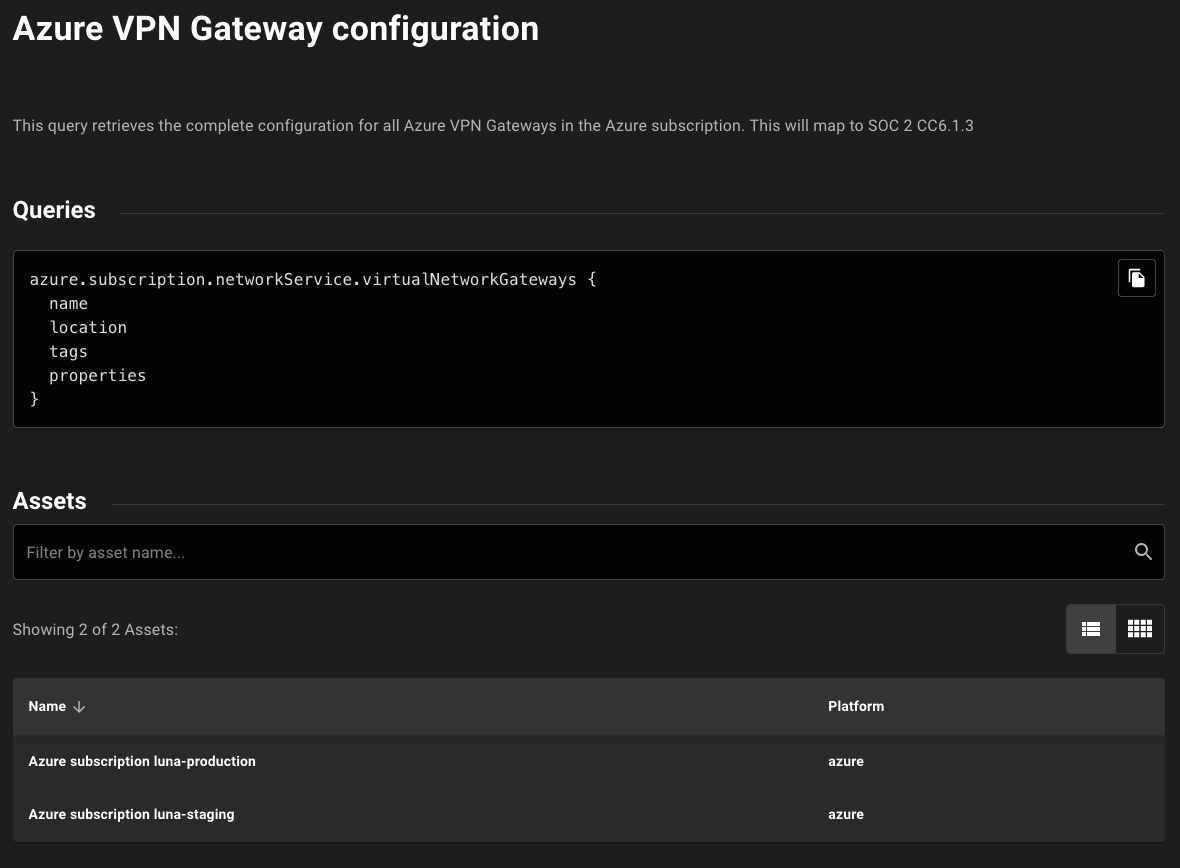
Drill into a data query to see the query detail and the assets for which it gathered data:
New result scoring design
The list of security findings was often presented and sorted in a confusing way. Successful security checks would often be listed above failed checks and errors and skipped checks were mixed into the list at seemingly random. This was due to the previous prioritization focusing more on the impact of checks, rather than the success or failure of its finding.
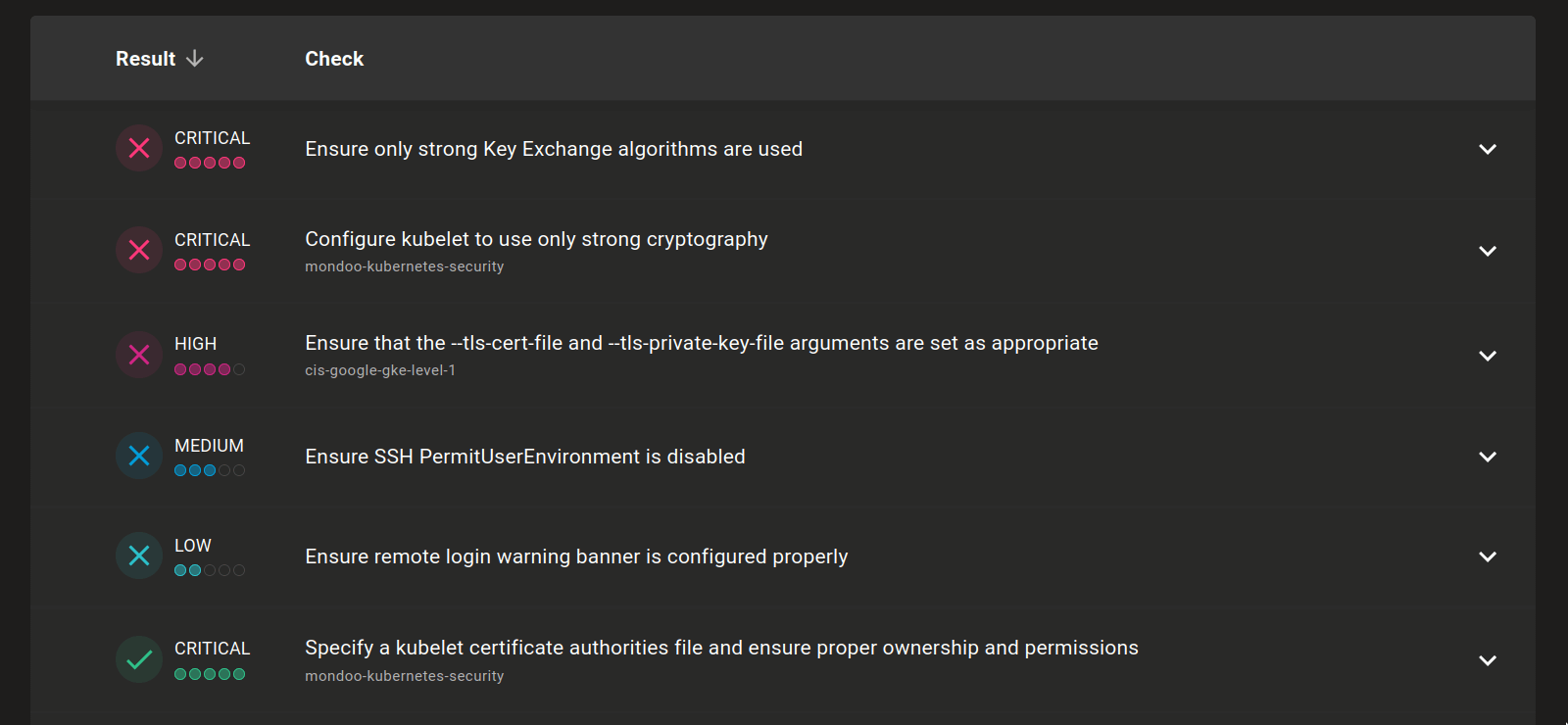
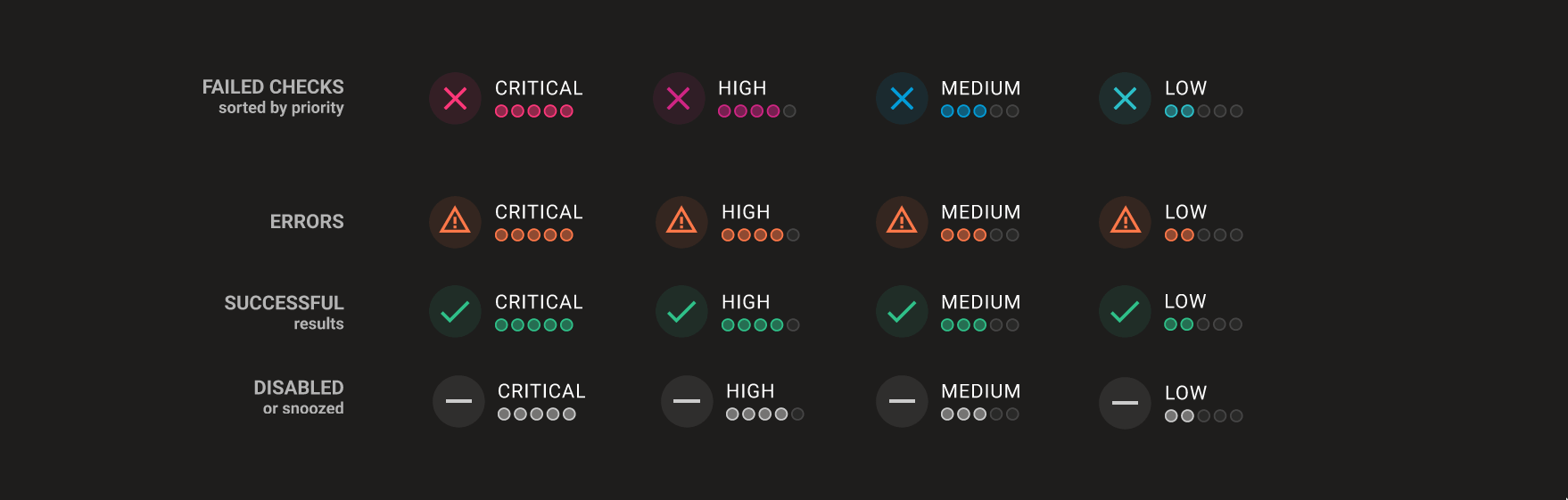
The new system is focused on prioritizing the most impactful actions. We now sort everything by failed checks first, followed by errors, then successful checks, and finally anything that is ignored or disabled. This means that the list now prioritizes the most critical failed findings.
We also improved the colors. If it looks like a successful check, it is now consistently green. If it looks like a red alarm, it's definitely a critical failed check.
Here's an overview of this new scoring system:
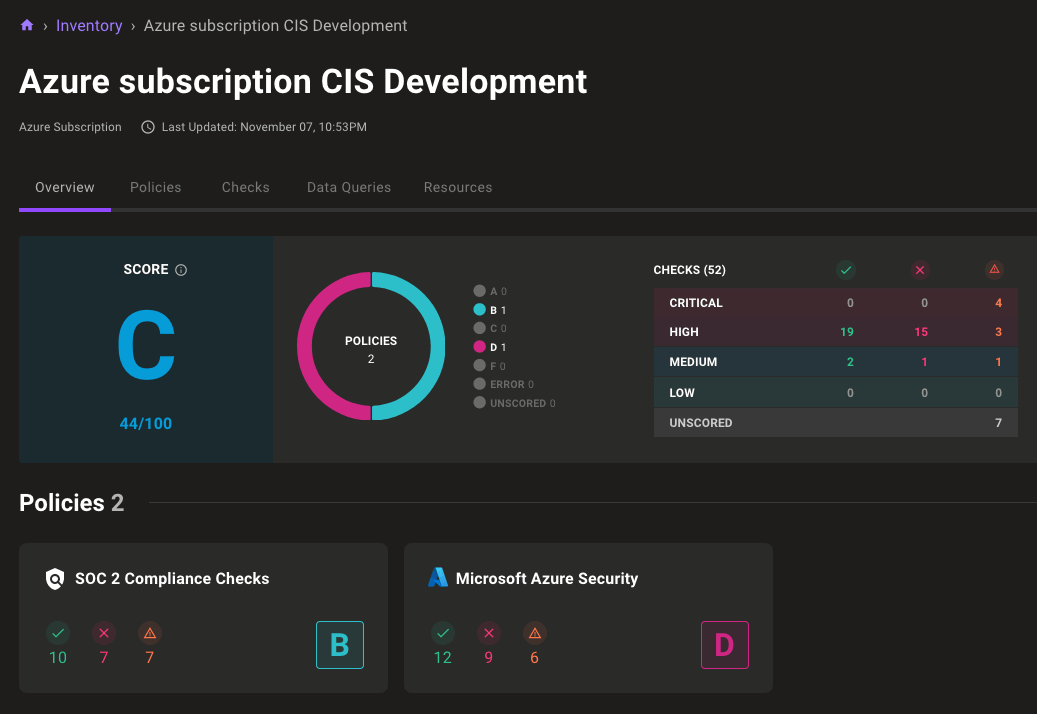
New asset scorecard design
When progress isn't lightning-fast, it's important to track small wins. With this in mind, we've redesigned our asset policy cards to better show progress made towards securing systems. The new design removes the score number from the cards and instead shows the number of passing and failing checks, so you can track progress without the need to dive into the list of all checks on an asset.
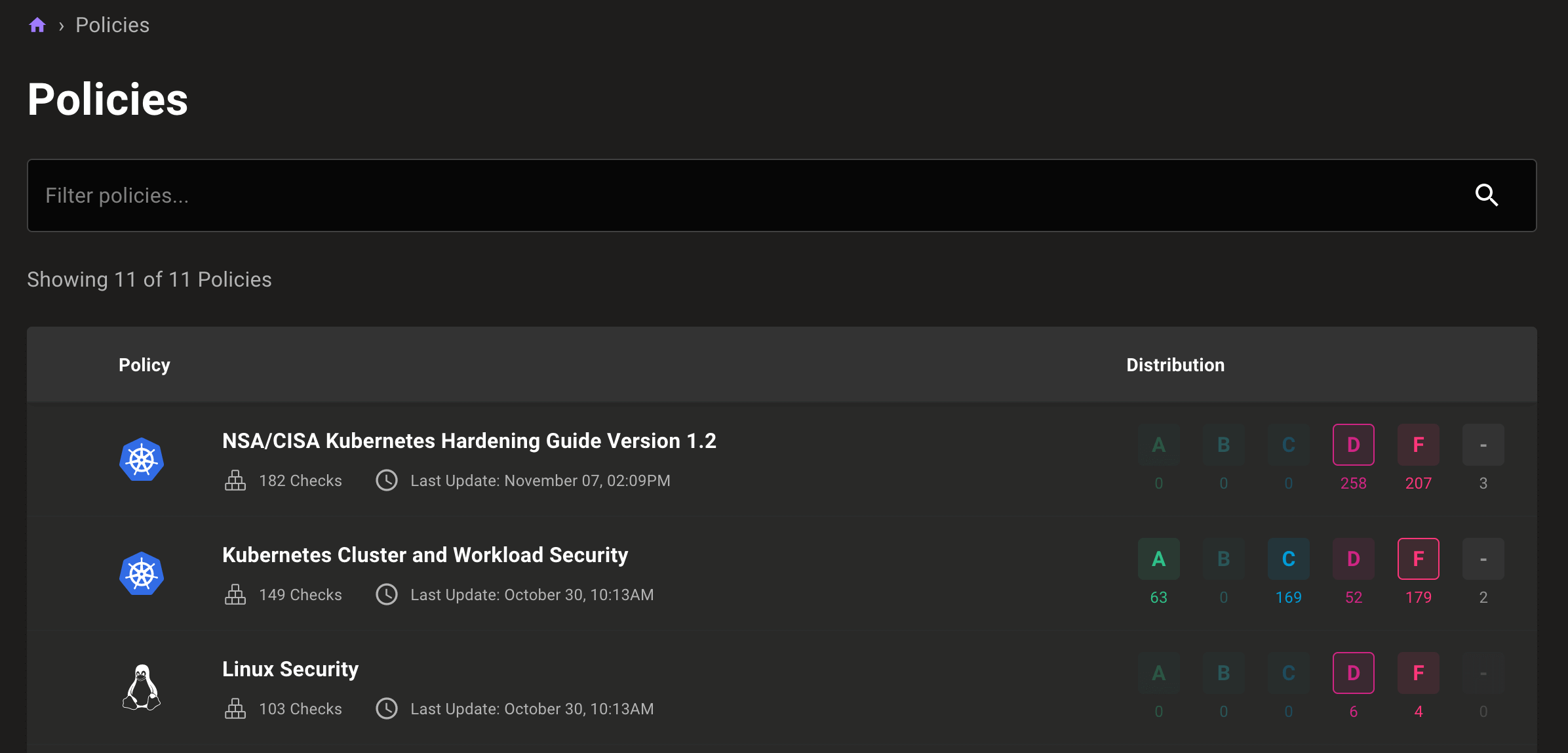
New security policies page
When we built the security policies page, our goal was to give users a single location where they could see all asset scores for policies in their space and control how those policies ran.
This week, we updated that page to make it easier to identify failing assets for each policy quickly:
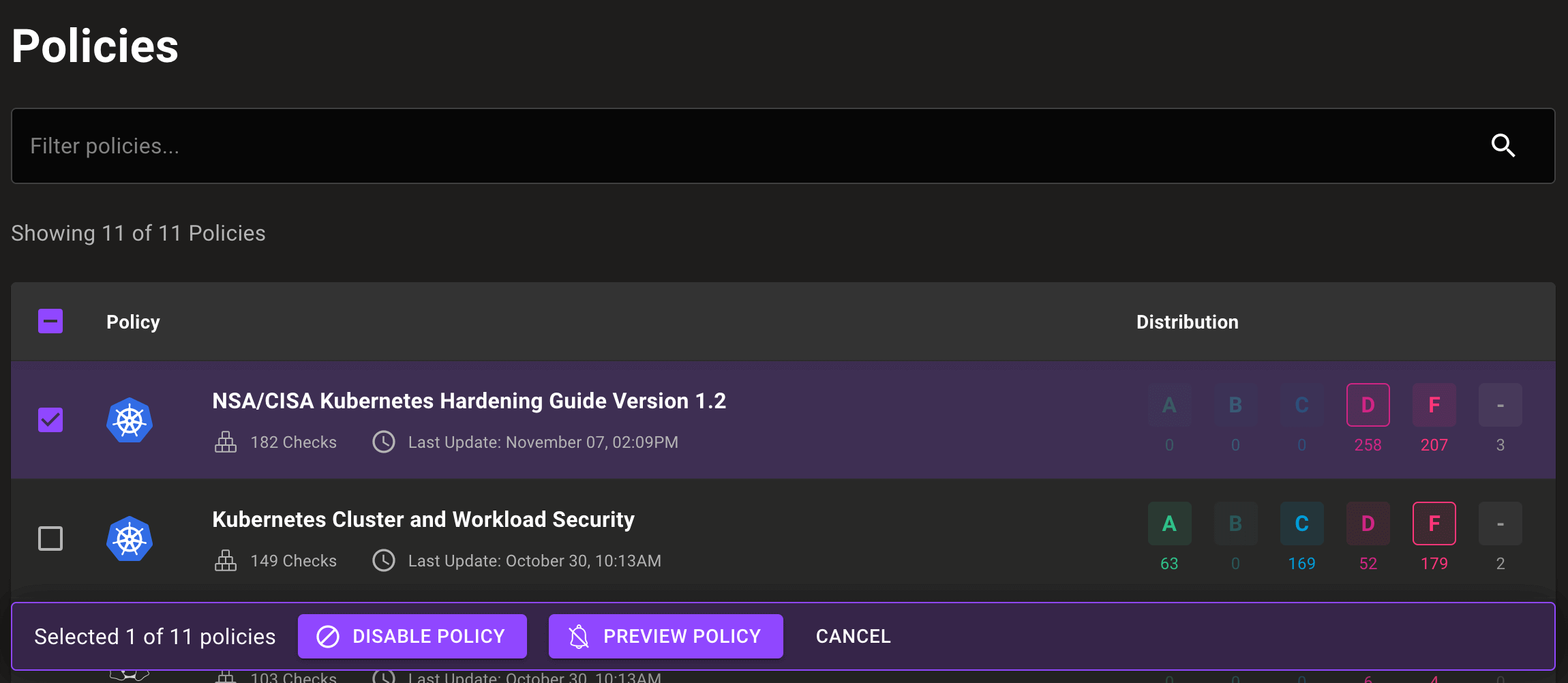
The updated page also allows you to disable a policy or set it to preview without leaving the policies page:
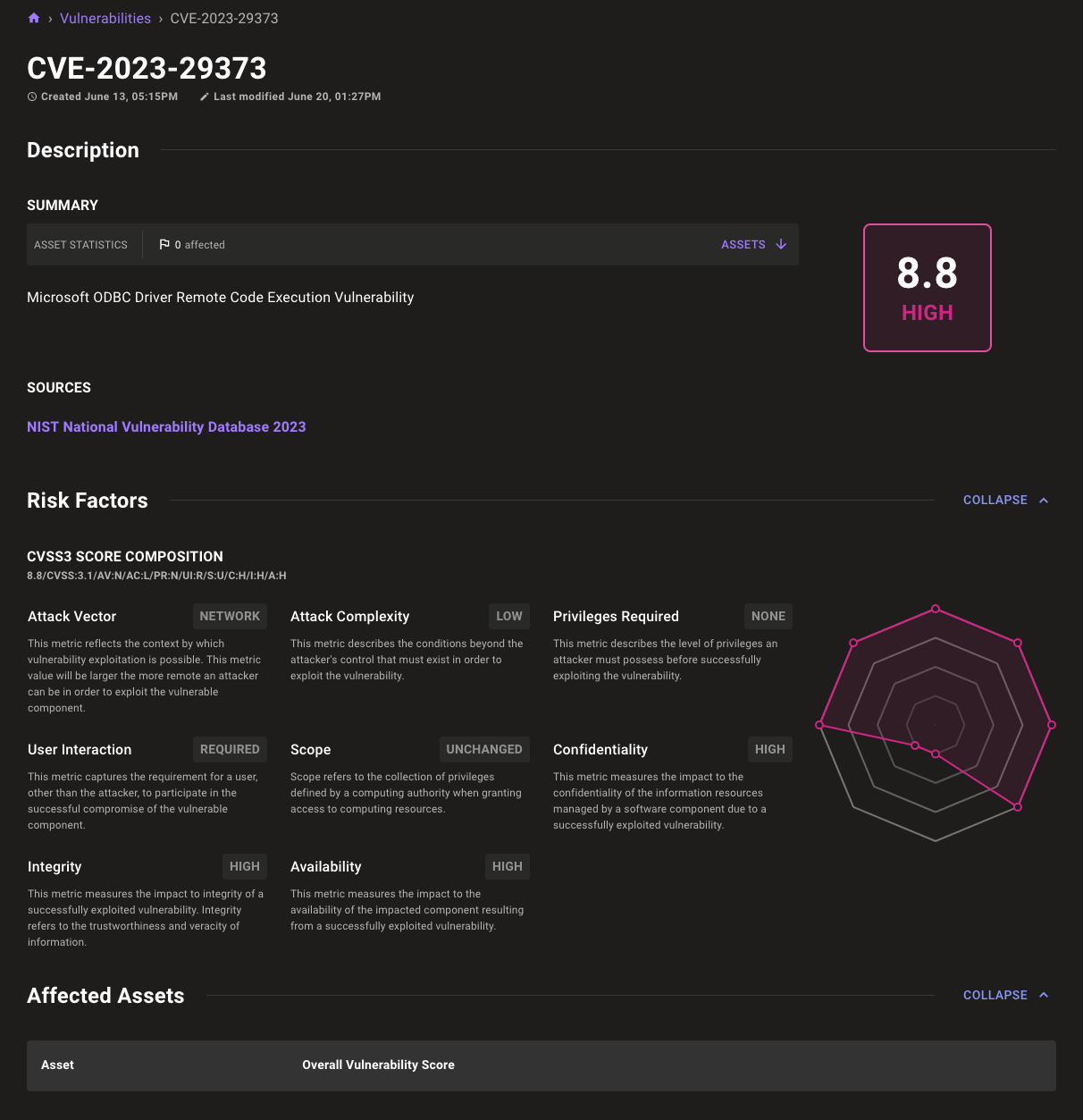
New CVE view
Out with the old and in with the new is the theme of the Mondoo 9.8 release, so why not update one of our oldest components? It's time for a whole new CVE page! A fresh, new design makes it easier to understand the impact of a CVE.
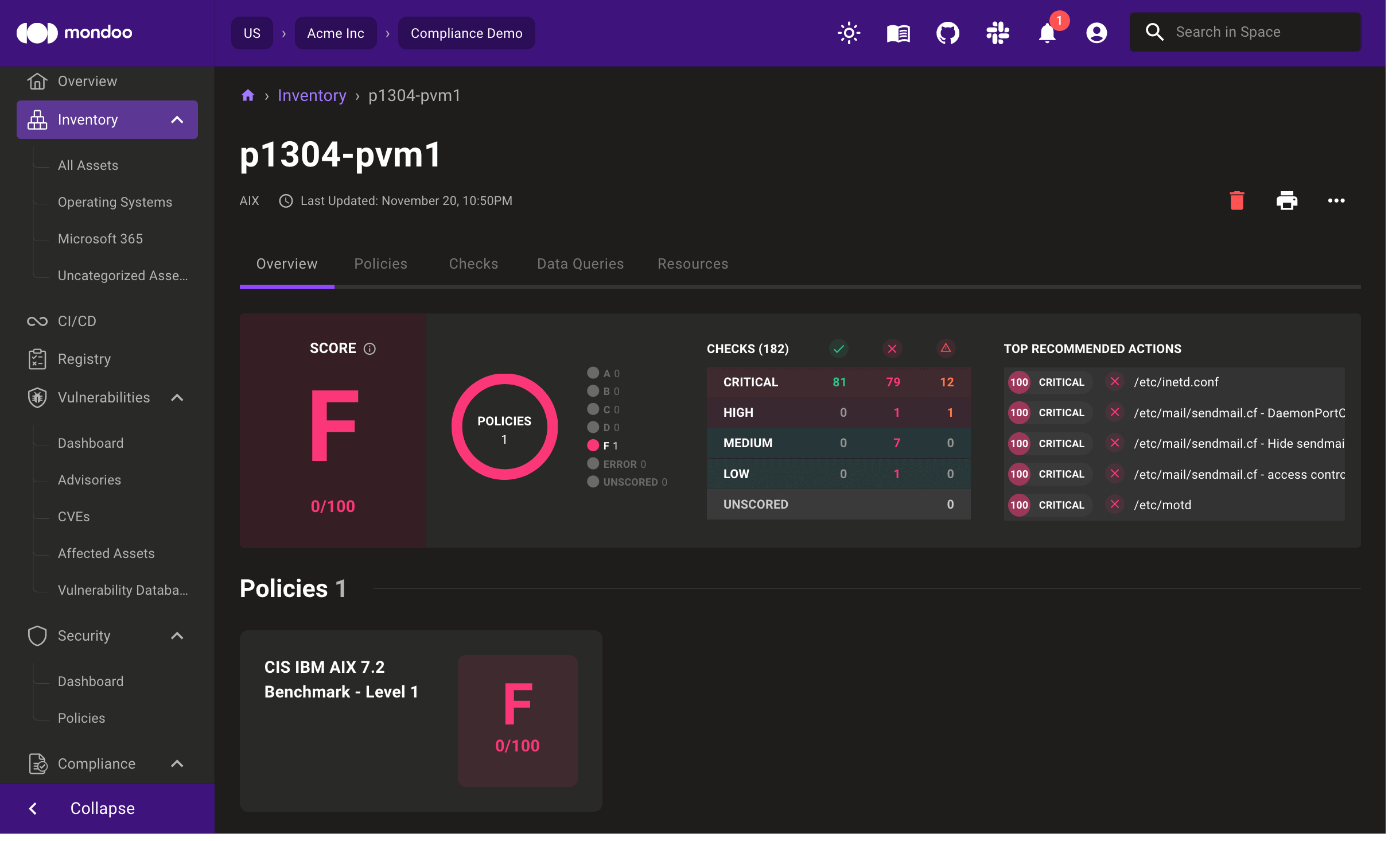
AIX 7.1 and 7.2 support
Kubernetes and serverless may be all the rage, but mainframes power the world. Now you can secure your AIX mainframes with Mondoo. We've updated cnquery and cnspec with new remote scan capabilities for AIX and bundled CIS AIX 7.1 and 7.2 benchmark policies, allowing you to quickly evaluate the security and compliance of your AIX systems.
New BSI SiSyPHuS Windows 10 policy
Mondoo now includes a new BSI SiSyPHuS Windows 10 policy based on BSI's SiSyPHuS Win10 - Study on system design, logging, hardening and security features in Windows 10 - Configuration Recommendations document. This policy includes 363 queries with impact scores and remediation steps. The checks map to all Mondoo supported compliance frameworks, including BSI's Cloud Computing Compliance Controls Catalog (C5) framework.
🧹 IMPROVEMENTS
Expanded resource fields
Whether you're writing custom security policies or exploring your infrastructure with cnquery shell, it's important to have all the data possible for assets. This week, we further expand some of our most popular assets with additional fields, giving you greater insight into your infrastructure.
atlassian.admin.organization.managedUser
productAccess- Product accessstatus- Status
aws.autoscaling.group
minSize- The minimum number of instances to scale down tomaxSize- The maximum number of instances to scale up todefaultCooldown- The time to wait after scaling up / down before the next scaling event is startedlaunchConfigurationName- The name of the launch configurationhealthCheckGracePeriod- The grace period in seconds before an instance with a failing health check will be replacedcreatedAt- Time when the autoscaling group was created
aws.ssm.instance
platformType- The type for the SSM Instance, as described by AWS (Windows, Linux, etc)platformVersion- Platform version for the SSM Instance, as described by AWS
aws.ec2.networkacl.entry
ruleNumber- The rule numbercidrBlock- CIDR block for the ACL entry
microsoft
tenantDomainName- The connected tenant's default domain name
package / python.package
purl- Package URL. See the purl-spec repository for more information on this data.
Expanded EOL date data
Mondoo includes the latest EOL dates for distributions so you can ensure your systems receive critical security updates.
- macOS 11 EOL date of September 26, 2023
- FreeBSD 12.4 EOL date of December 31, 2023
🐛 BUG FIXES AND UPDATES
- Fix the coloring of code blocks in print mode.
- Correct spelling of SOC 2 in policies and frameworks.
- Improved reliability in Windows CIS security checks.
- Improve SOC 2 security check mapping.
- Fix select all checkbox behavior in compliance frameworks to only select the visible controls on the page.
- Use the time datatype instead of string in the Atlassian provider for better resource output.
cnspec bundle fmtnow preserves comments on the first line of the policy file.- Update providers when cnspec is scanning as a service (serve mode).
- Fix CIS
Ensure 'User Account Control: Behavior of the elevation prompt for administrators in Admin Approval Mode' is set to 'Prompt for consent on the secure desktop'check failures. - Don't show the same policy twice for a single check in Compliance Hub.
- Fix example scan flags for Kubernetes on the workstation integration page.
- Only show the create space button on the organizations page if the user has permission to create a space.
- Don't require all data to be reentered when updating a Jira integration.
- Improve the performance of loading CVE and advisory data.
- Add new preview HTTP Security policy.
- Improve the reliability of organization dashboard graphs for some spaces.