Mondoo 9.10 is out!
🥳 Mondoo 9.10 is out! This release includes compliance evidence PDF reports, exceptions for policies/assets, and more!
Get this release: Installation Docs | Package Downloads | Docker Container
🎉 NEW FEATURES
Compliance evidence report generation in PDF format
Prove compliance to your auditors with PDF evidence reports. Now you can export reports from any control page or export an archive containing controls for your whole compliance framework.
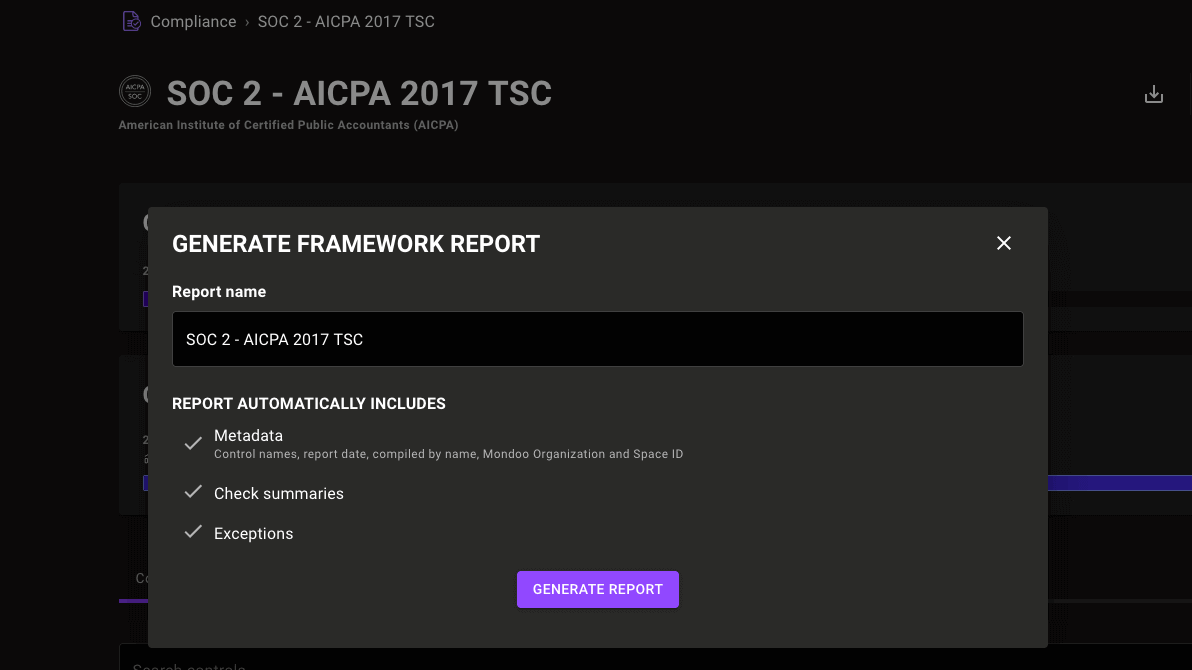
These reports are specifically formatted for auditors and ready for attachment to GRC systems or other auditor evidence upload solutions.
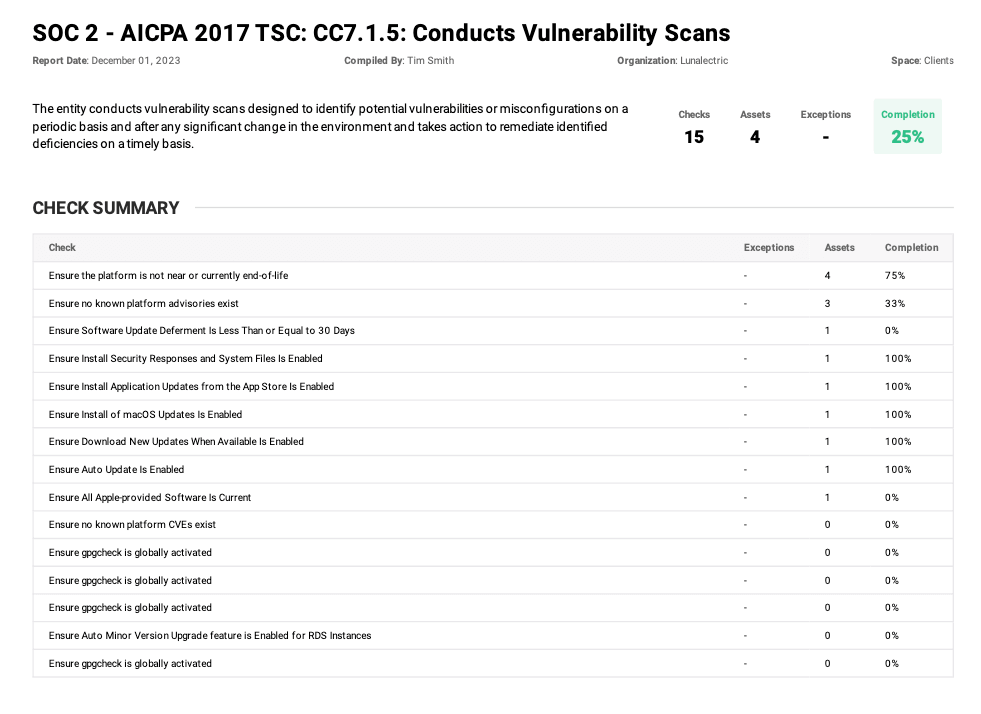
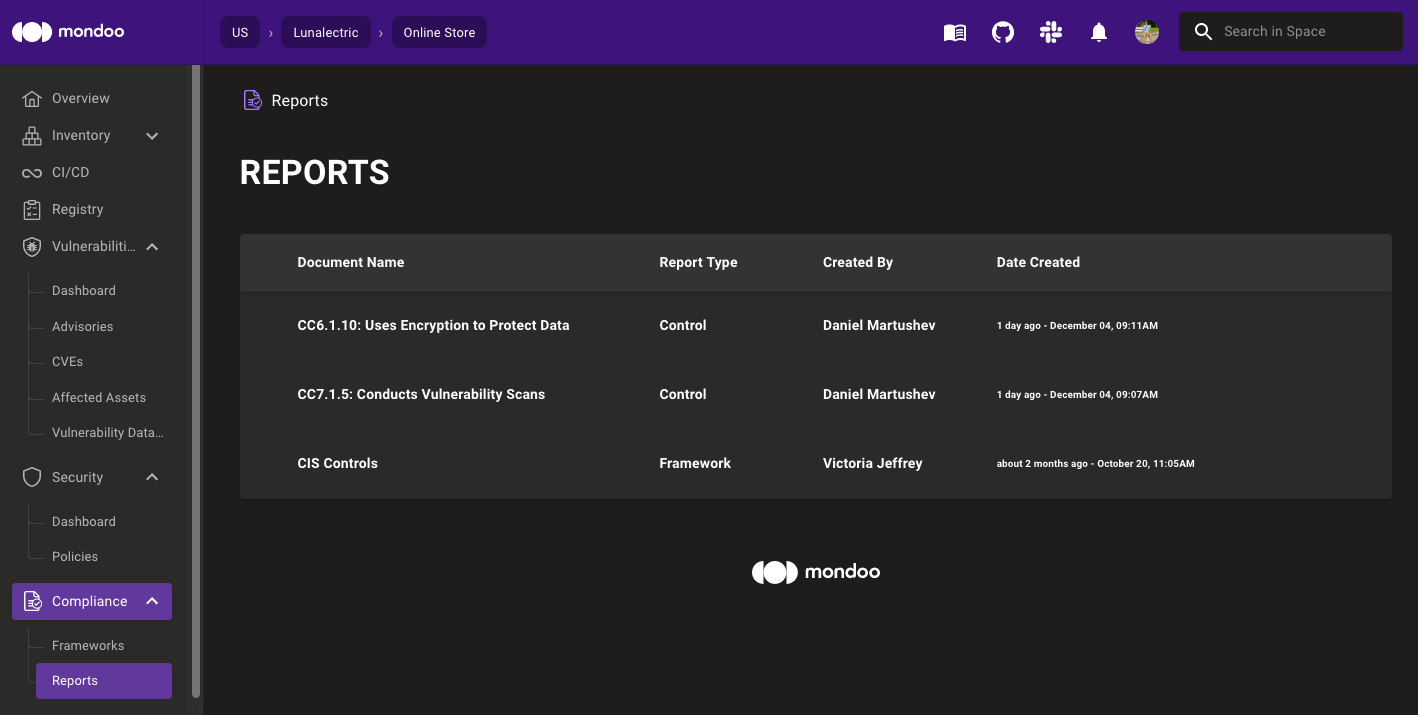
We've got you covered with secure storage as well, so you can share reports between team members without insecure email attachments or unauthenticated URLs.
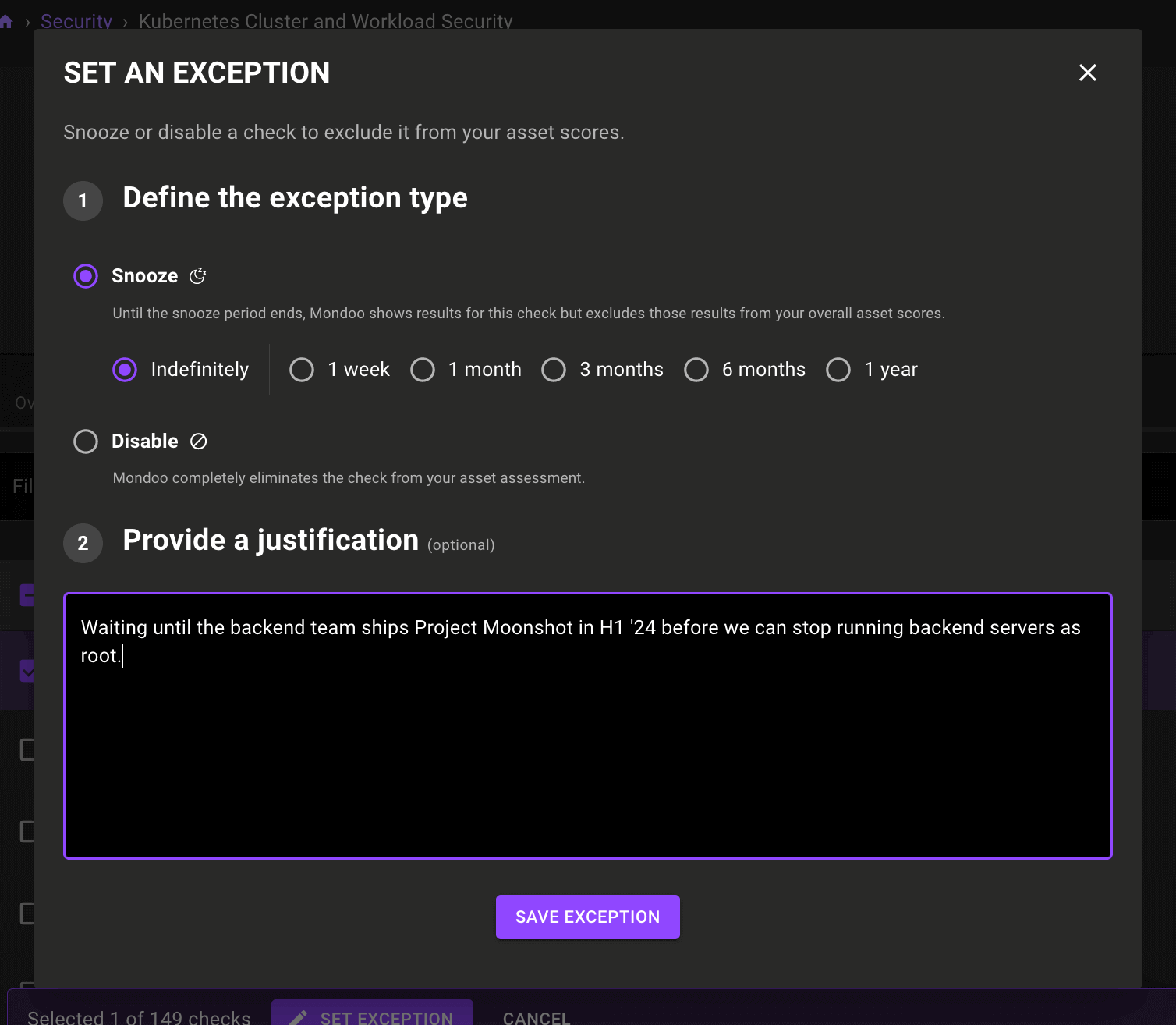
Exceptions for assets and policies
The power and visibility of compliance exceptions is now available outside of compliance: You can now set exceptions for checks on assets and security policies. Asset and policy exceptions enable cross-team visibility and allow more granularity in how you prioritize your work.
Improve visibility with detailed explanations of why exceptions were created, approvals, and detailed logging. You never have to ask again who made a change and why.
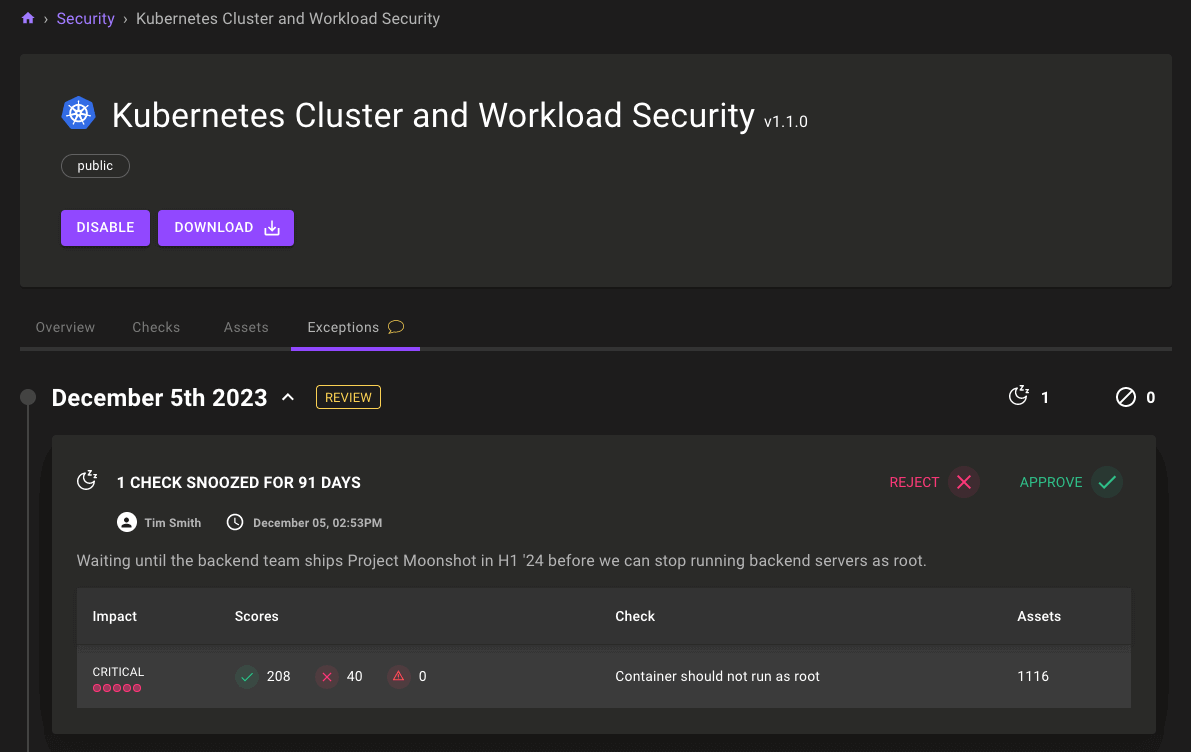
Prioritize your work with time-based snoozing: Turn off a check temporarily while you work on more important issues, but don't let it fall through the cracks.
New CIS Azure Compute Microsoft Windows Server 2019 and 2022 benchmarks
Secure your Windows Azure environment using the new Azure Compute Microsoft Windows Server 2019 and 2022 benchmarks. These benchmarks specifically target the security of Windows 2019 and 2022 Datacenter editions, using Azure's secure configuration guide settings. Each benchmark consists of domain and member server policies containing over 200 Azure-tailored checks.
New CIS ESXi 8.0 Benchmark v1.0.0
Are you upgrading your VMware deployments to version 8.0? Mondoo has you covered with the new CIS ESXi 8.0 Benchmark version 1.0. This updated policy includes 86 checks tailored to the latest VMware release.
🧹 IMPROVEMENTS
Updated RHEL/Oracle/Rocky/AlmaLinux 8 Benchmarks
Keep your RHEL 8 compatible servers secure with the new 3.0 release of CIS benchmarks for Red Hat Enterprise Linux, Oracle Linux, AlmaLinux, and Rocky Linux. These new policies are complete reworks of the existing CIS benchmarks with hundreds of new and updated checks.
MQL containsNone with an array of regular expressions
Now you can avoid long, chained MQL queries that check multiple regular expressions. Instead, specify an array of regular expressions:
field.containsNone( [ /a/, /.*b/ ] )
🐛 BUG FIXES AND UPDATES
- Provide friendly error messages if invalid time values for token expiration are entered.
- Clarify what search values are supported on the compliance controls page.
- Improve table headings for affected assets on the vulnerabilities pages.
- Don't reset the pagination back to the first page when enabling/disabling a policy in the registry.
- Update all policy icons to be full-color for consistency.
- Fix different scan behaviors between
containeranddockerproviders that caused failures when scanning containers. - Don't fail when using
.containsin queries if the dict value is empty. - Fix container image asset names changing between 8.x and 9.x client scans.
- Fix an error in the
aws.iam.policiesresource when fetchingattachedGroupsdata. - Support quitting the cnquery/cnspec shells with the
quitcommand. - Fix failures when running
cnquery login. - Add additional data to the
aws.iam.attachedPoliciesresource. - Improve
cnspec bundle fmtto format markdown in documentation fields and optionally sort checks by name. - Fix a failure in cnspec if two policies use the same query UID.
- Don't show rejected exceptions as active exceptions when scanning in cnspec.
- Fix the width of the scanning progress bar to show the score result.
- Fix the
Ensure updates, patches, and additional security software are installedquery in the CIS Distribution Independent Linux policy to work with Photon. - Fix a failure when running
asset{ * }on some non-operating system assets. - Improve the titles of many inventory query pack queries.
- Improve the form validation behavior in Azure, Okta, OCI, Microsoft 365, and GitHub integration pages.
- Add missing badges and a description to the Slack integration setup page.
- Fix failures in the
aws.acm.certificatesresource. - Don't run the TLS security policy on non-host network assets.
- Ensure that AIX, FreeBSD, Fedora, Kali Linux, Scientific Linux, Pop!_OS, and EuroLinux assets are grouped as operating systems in inventory.
- Fix rejected compliance exceptions still showing as exceptions on the controls.
- Improve performance throughout the Mondoo Console.
- Add EOL detection for EuroLinux assets.
- Add platform vulnerability detection for the Windows 23H2 release.
- Ensure audit logs are generated for space create/delete events and add logging when changing space and organization owners.
- Improve asset group display for GitLab assets.
- Fix a failure running the
cnspec vulncommand. - Display all spaces when an organization includes more than 25 spaces.
- Allow the network provider to run with an inventory file.
- Improve the policy page UI when a policy is enabled, but hasn't yet run on any assets.
- Fix a UI error when generating a non-expiring registration token.
