Mondoo 8.29 is out!
🥳 Mondoo 8.29 is out! This release includes improved table views, a new Inventory navbar item, and more!
Get this release: Installation Docs | Package Downloads | Docker Container
🧹 IMPROVEMENTS
Improved UI tables
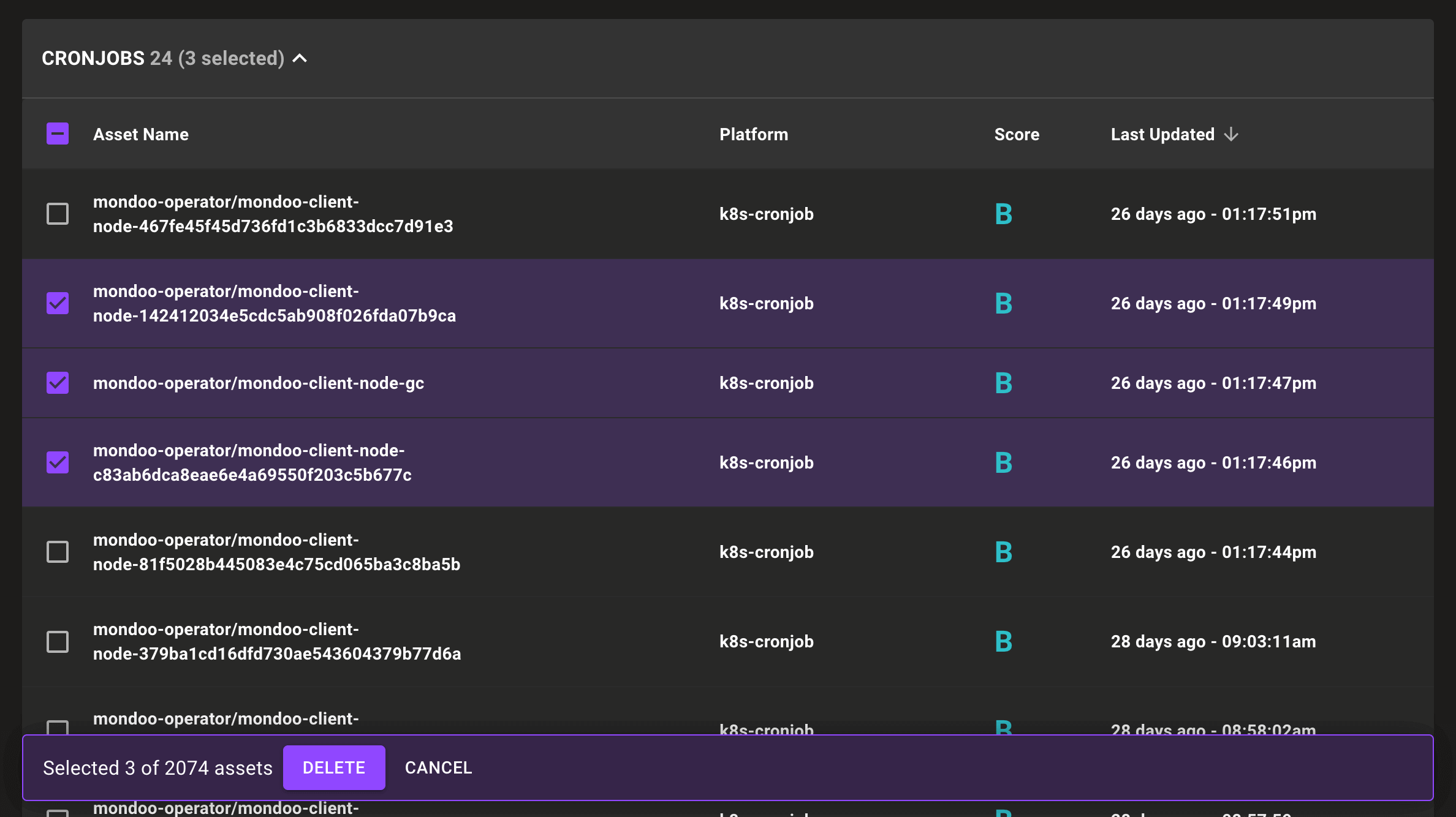
At Mondoo we take pride in not just collecting security information, but also displaying it in a meaningful way. If you've been using the product long enough you may have noticed we've gone through many iterations of our table view. It never felt quite right, until we introduced the new table in Compliance Hub that lets you easily view, sort, and multi-select data without pull down menus or multiple clicks. This week the team revamped all of our existing views to update them with this improved UX. Give it a try and keep an eye out for pagination improvements coming soon!
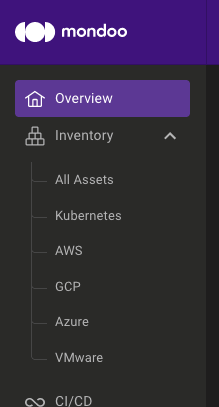
Fleet is now Inventory
When we first built Mondoo, the Fleet view was where you found all of your servers or workstations. As we expanded Mondoo to include Kubernetes workloads, cloud accounts, and even SaaS services, this name made less sense. This week we renamed Fleet to Inventory to better represent Mondoo's cross-platform asset inventory capabilities. It's just a rename, but we think this will make it easier to jump right in and begin exploring all your inventory.
Fedora 39 vulnerability scanning
Fedora 39 is right around the corner, with the first beta released this week. Not to be left behind we've added Fedora 39 vulnerability scanning to Mondoo, so fire up cnspec and keep that beta install secure.
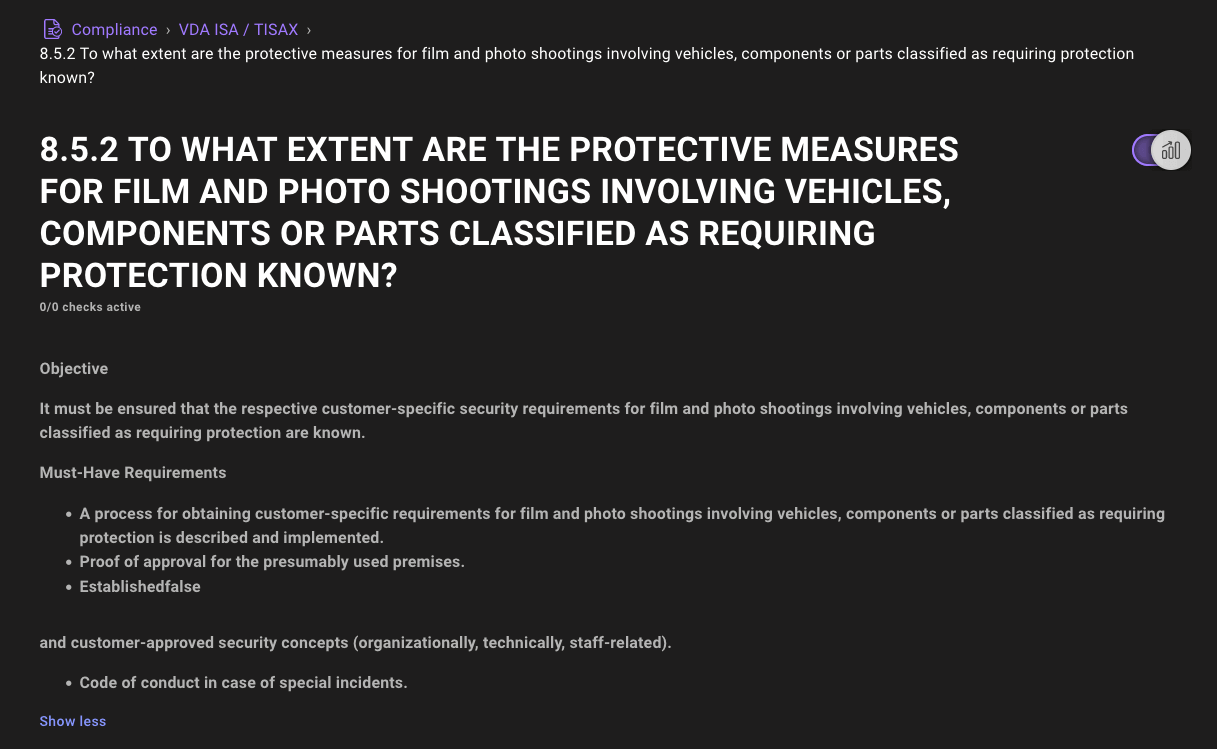
Improved compliance control descriptions
We've expanded the data that can be displayed in Compliance Control pages, so you'll always have all the details to keep your infrastructure secure. This new view includes improved description rendering and the ability to expand extra long descriptions.
🐛 BUG FIXES AND UPDATES
- Reduce API usage for GitLab scans to avoid API rate-limiting.
- Avoid some authentication failures when scanning GitLab projects.
- Fix incorrect GitLab asset runtime values.
- Improve the usage instructions in the GitLab policy with project scanning instructions.
- Fix errors in the CIS
Ensure GDM login banner is configuredcheck when GDM files don't exist. - Improve output of the CIS
Ensure journald is not configured to receive logs from a remote clientcheck. - Add GitLab Group ID and Project ID to the asset configuration overview data.
- Fix failures loading certain assets in the console.
- Change the "Rational" sections in policies to "Rationale."
- Only run the
Linux Workstation Securitypolicy whenxorg-xserveris installed to prevent it from evaluating servers. - Update the registry to consistently refer to "query packs" as two words.
- Improve query descriptions in the
Azure Asset Inventory Packquery pack. - Remove a duplicate query from the
Azure Asset Inventory Packquery pack. - Fix some query pack and policy bundle categories/authors to make filtering in the registry more consistent.
- Support Rsyslog 7+ syntax in the CIS
Ensure rsyslog is configured to send logs to a remote log hostcheck. - Don't display the
Assetsbutton in Kubernetes integration pages when no assets have been scanned. - Allow updating the token in GitLab integrations.
- Don't display compliance control checkboxes when a user only has view permissions in a space.