Mondoo 8.24 is out!
· 3 min read
🥳 Mondoo 8.24 is out! This release includes NIST SP 800-171 compliance, CIS AWS Foundations Benchmark 2.0, and more!
Get this release: Installation Docs | Package Downloads | Docker Container
🎉 NEW FEATURES
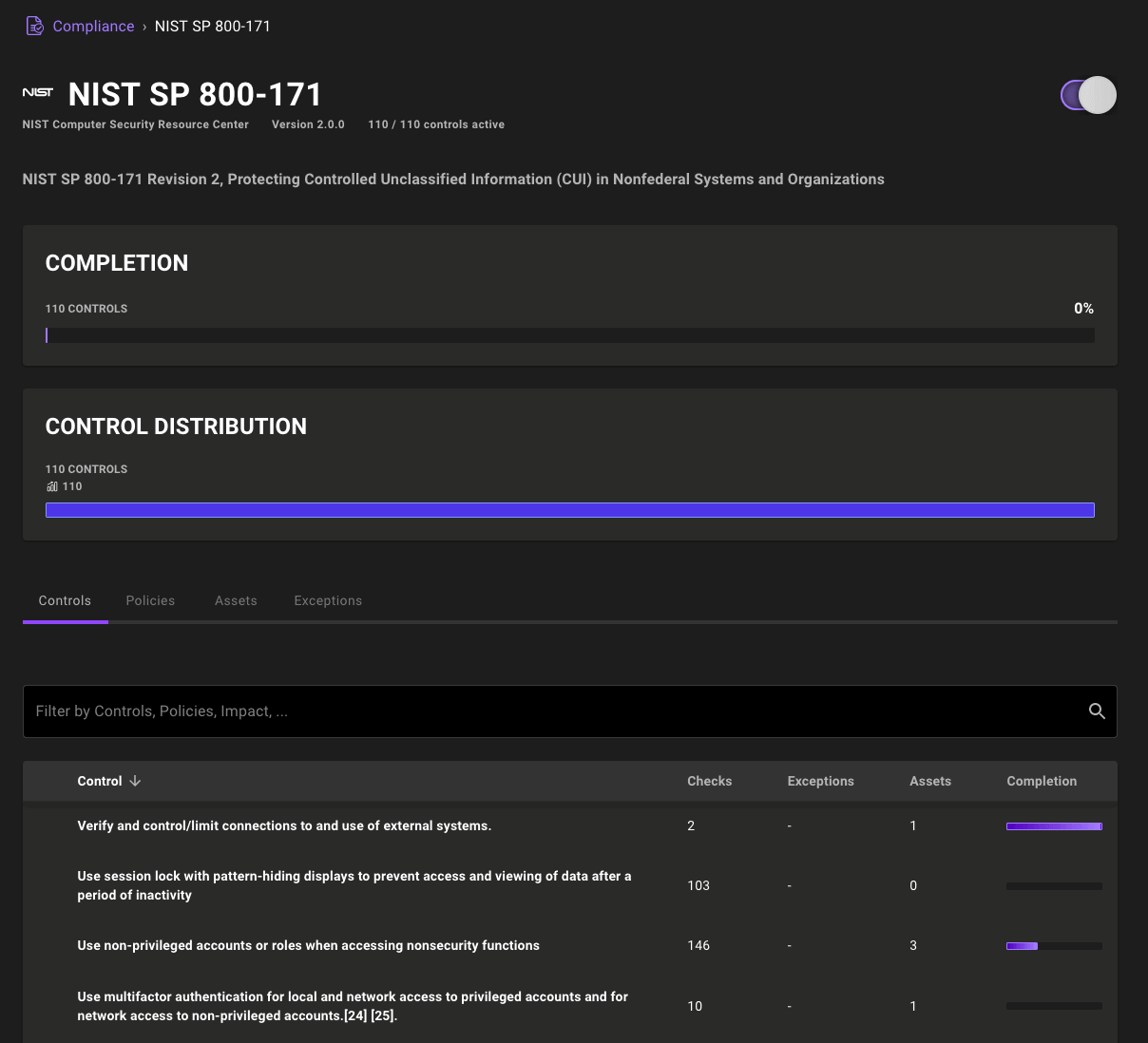
NIST SP 800-171 Framework
Mondoo Compliance Hub now includes the NIST SP 800-171 framework, raising the total number of out-of-the-box compliance frameworks to ten. Each of the 110 controls in this framework automatically map to the checks in your infrastructure, so with a flip of a switch you can start your NIST SP 800-171 and see where you stand.
🧹 IMPROVEMENTS
Improved asset configuration data for GCP projects
GCP project assets in the fleet now include additional asset configuration data, so you can always understand what's being scanned at a quick glance.
CIS Amazon Web Services (AWS) Foundations Benchmark 2.0
The CIS Amazon Web Services (AWS) Foundations Benchmark is updated to the latest 2.0 release. This updated benchmark includes a number of important updates to make securing your AWS environment easier:
- Adds a new check to ensure that EC2 metadata service requires IMDSv2
- Adds a new check to restrict the usage of AWS CloudShell
- Removes the check that ensures all S3 buckets have encryption at rest enabled because this feature is now enabled automatically
- 22 updated checks with improved audit and remediation steps
🐛 BUG FIXES AND UPDATES
- Fix errors determining cloud configuration for containers.
- Improve slow scan times while waiting on policy data.
- Resolve a panic loading some queries in the resource explorer.
- Fix organization overview dashboard to ignore data below 0.
- Improve reliability of queries in the CIS Distribution Independent Linux Benchmark policy.
- Update CIS Windows policy scoring to match that of non-Windows CIS benchmarks.
- Improve the reliability of the GitHub Organization Security and GitHub Repository Security policy SECURITY.md checks.
- Fix incorrect text on the org and space level service account pages.
- Improve padding in the asset page configuration tiles.
- Improve the display of various compliance pages when there is not data.
- Fix an error in the asset overview data when the cloud could not be properly detected.
- Fix failures scanning OCI via the integration.
- Adjust impact scores in the Mondoo Linux Security and CIS Distribution Independent Linux Benchmark policies.
- Don't show buttons to create new spaces when users only have Viewer privileges.
- Fix the Kubernetes operator to properly garbage collect old node scans when only node scanning is enabled.
- Display CVSS 3.1 CVE scores when available.
