Mondoo 8.2 is out!
🥳 Mondoo 8.2 is out! This release includes GCP BigQuery exports, new Azure resources, and more!
Get this release: Installation Docs | Package Downloads | Docker Container
🎉 NEW FEATURES
Google BigQuery data exports
Love your security data, but need to analyze it more deeply? Now you can automatically export your Mondoo data directly to Google BigQuery.
Exports are configured just like other integrations in Mondoo, and run daily without the need to install anything into your infrastructure.
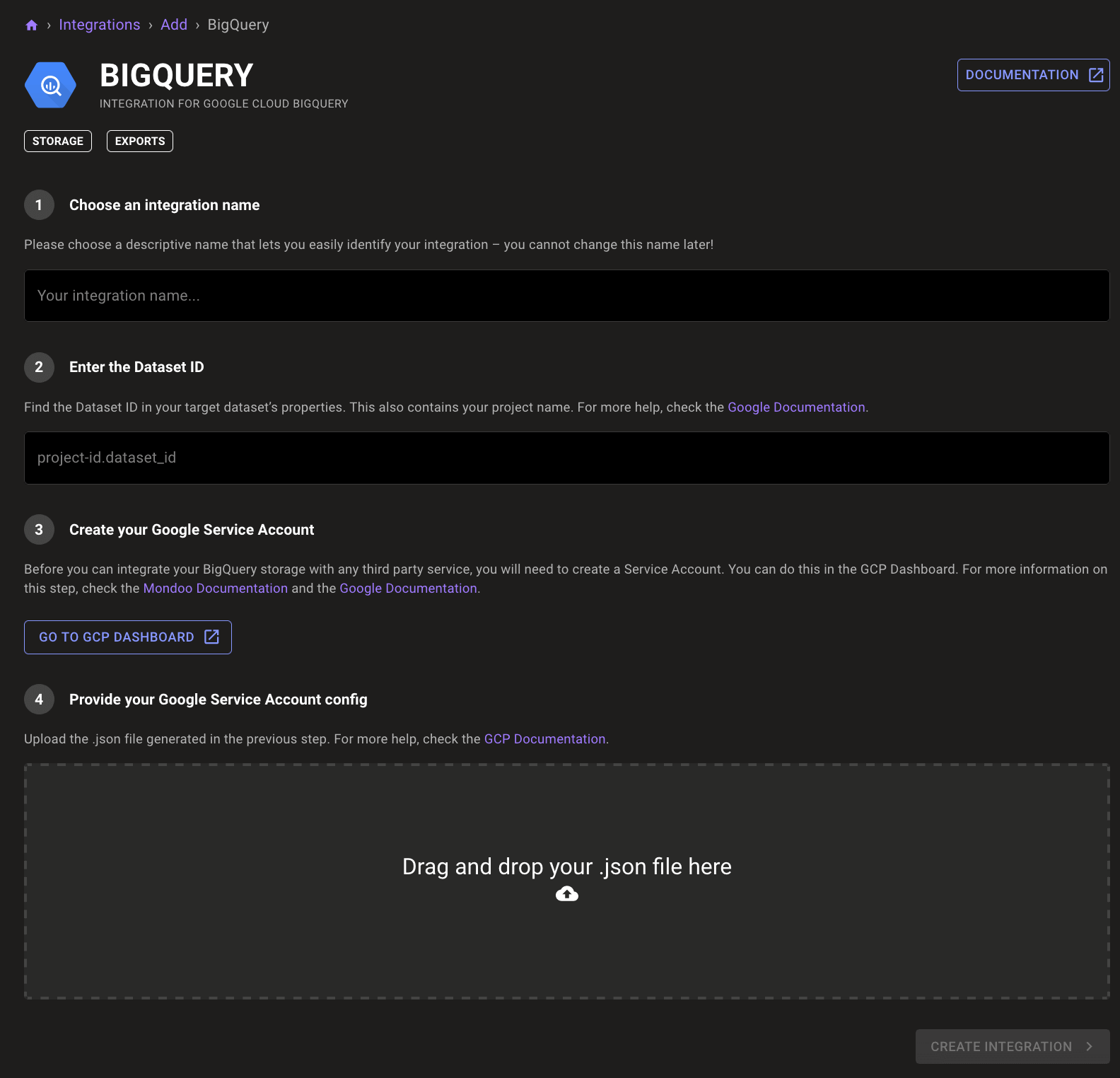
Once the data is exported it can be combined with other data in BigQuery and analyzed with BigQuery's machine learning and BI features.
New Azure resources
cnspec and cnquery now ship with additional Azure resources so you can inventory and secure all aspects of your Azure infrastructure:
azure.subscription.monitor.applicationInsights
This new Azure resource lets you query each instance of Application Insights:
MQLcnquery> azure.subscription.monitor.applicationInsightsazure.subscription.monitor.applicationInsights: [0: azure.subscription.monitorService.applicationinsight id = /subscriptions/f1a2873a-6b27-4097-aa7c-3df51f103e96/resourceGroups/cloud-shell-storage-westeurope/providers/microsoft.insights/components/app-insight-test]cnquery> azure.subscription.monitor.applicationInsights {name kind location}azure.subscription.monitor.applicationInsights: [0: {name: "app-insight-test"location: "centralus"kind: "web"}]
azure.subscription.network.bastionHost
This new Azure resource lets you query all bastion hosts, including their names, locations, and product SKUs:
MQLcnquery> azure.subscription.network.bastionHostsazure.subscription.network.bastionHosts: [0: azure.subscription.networkService.bastionHost id="/subscriptions/f1a2873a-6b27-4097-aa7c-3df51f103e96/resourceGroups/cloud-shell-storage-westeurope/providers/Microsoft.Network/bastionHosts/test-bastion-host" name="test-bastion-host" location="uksouth"]cnquery> azure.subscription.network.bastionHosts{name location sku}azure.subscription.network.bastionHosts: [0: {name: "test-bastion-host"sku: {name: "Standard"}location: "uksouth"}]
azure.subscription.sql.virtualNetworkRule
This new Azure resource lets you query the virtual network rules on an Azure SQL Database service server and is similar to firewall rules resources:
MQLcnquery> azure.sql.servers[1].virtualNetworkRules{ * }azure.sql.servers[1].virtualNetworkRules: [0: {id: "/subscriptions/f1a2873a-6b27-4097-aa7c-3df51f103e96/resourceGroups/cloud-shell-storage-westeurope/providers/Microsoft.Sql/servers/sql-server-mondoo-test/virtualNetworkRules/newVnetRule1"properties: {id: "/subscriptions/f1a2873a-6b27-4097-aa7c-3df51f103e96/resourceGroups/cloud-shell-storage-westeurope/providers/Microsoft.Sql/servers/sql-server-mondoo-test/virtualNetworkRules/newVnetRule1"name: "newVnetRule1"properties: {ignoreMissingVnetServiceEndpoint: falsestate: "Ready"virtualNetworkSubnetId: "/subscriptions/f1a2873a-6b27-4097-aa7c-3df51f103e96/resourceGroups/DefaultResourceGroup-CUS/providers/Microsoft.Network/virtualNetworks/prelav-test-VN/subnets/default"}type: "Microsoft.Sql/servers/virtualNetworkRules"}virtualNetworkSubnetId: "/subscriptions/f1a2873a-6b27-4097-aa7c-3df51f103e96/resourceGroups/DefaultResourceGroup-CUS/providers/Microsoft.Network/virtualNetworks/prelav-test-VN/subnets/default"type: "Microsoft.Sql/servers/virtualNetworkRules"name: "newVnetRule1"}]
azure.subscription.cosmosdb
This new Azure resource lets you query the Azure Cosmos DB service.
Query databases:
MQLcnquery> azure.subscription.cosmosDb.accountsazure.subscription.cosmosDb.accounts: [0: azure.subscription.cosmosdbService.account name="test-cosmosdb-mondoo" location="West US"1: azure.subscription.cosmosdbService.account name="test-mondoo-cassandra" location="West US"]
Write assertions to secure configuration:
MQLcnquery> azure.cosmosDb.accounts{properties['isVirtualNetworkFilterEnabled'] name}azure.cosmosDb.accounts: [0: {properties[isVirtualNetworkFilterEnabled]: truename: "test-cosmosdb-mondoo"}1: {properties[isVirtualNetworkFilterEnabled]: truename: "test-mondoo-cassandra"}]
🧹 IMPROVEMENTS
Kubernetes namespace scoped scanning
You can now scan a single namespace in a Kubernetes cluster even if you don't have access to resources outside that namespace. This allows you to scan all workloads in your namespace and browse asset relationships under the namespace in the Mondoo Console.
Example cnquery query against a single namespace:
Shell./cnquery run k8s --namespaces default -c "k8s.pods" --discover namespaces→ loaded configuration from /Users/ivanmilchev/.config/mondoo/mondoo.yml using source default→ discover related assets for 1 asset(s)→ resolved assets resolved-assets=1k8s.pods: [0: k8s.pod namespace="default" name="nginx" created=2023-03-14 16:59:07 +0100 CET]
Homebrew now installs cnspec/cnquery along with Mondoo
The Mondoo Homebrew tap now installs both cnquery and cnspec as dependencies, giving you the complete power of Mondoo in one installation.

All macOS binaries are now signed and notarized
We now sign and notarize all binaries for macOS, not just those installed with the Mondoo .pkg file. This means no matter where you consume Mondoo packages, you will always have a fully secured binary that passes all of Apple's security requirements.
🐛 BUG FIXES AND UPDATES
- Fix failure if the
pscommandcolumn has no data and warn if data otherwise can't be parsed correctly. - Fix failures setting the AWS integration.
- Fix parsing of policies with arrays of remediations instead of simple strings.
- Improve the audit/remediation steps in Mondoo security policies.
- Update
cnspec bundle lintandcnspec bundle fmtcommands to support the Mondoo version 8.0+ policy structure. - Update the
Ensure events that modify the system's Mandatory Access Controls are collectedquery in theLinux Security by Mondoopolicy to support either SELinux or AppArmor. Thanks @micheelengronne! - Improve reliability of queries in the
Okta Organization Security by Mondoopolicy.