Mondoo 7.16 is out!
🥳 Mondoo 7.16 is out! This release includes new Azure, GCP, and Microsoft 365 integrations plus a whole new UI experience!
Get this release: Installation Docs | Package Downloads | Docker Container
🎉 NEW FEATURES
New UI navigation experience
Problem: There are many things you can do in the Mondoo Console, but sometimes it's hard to find what you need.
Solution: We rebuilt the navigation in the Mondoo Console from the ground up to make finding information and navigating your infrastructure easier. We replaced the top navigation tabs with a new navigation menu on the left side of the page. This menu includes frequently accessed sections of the UI that were previously tabs, such as Fleet, CI/CD, Integrations, and Policy Hub.
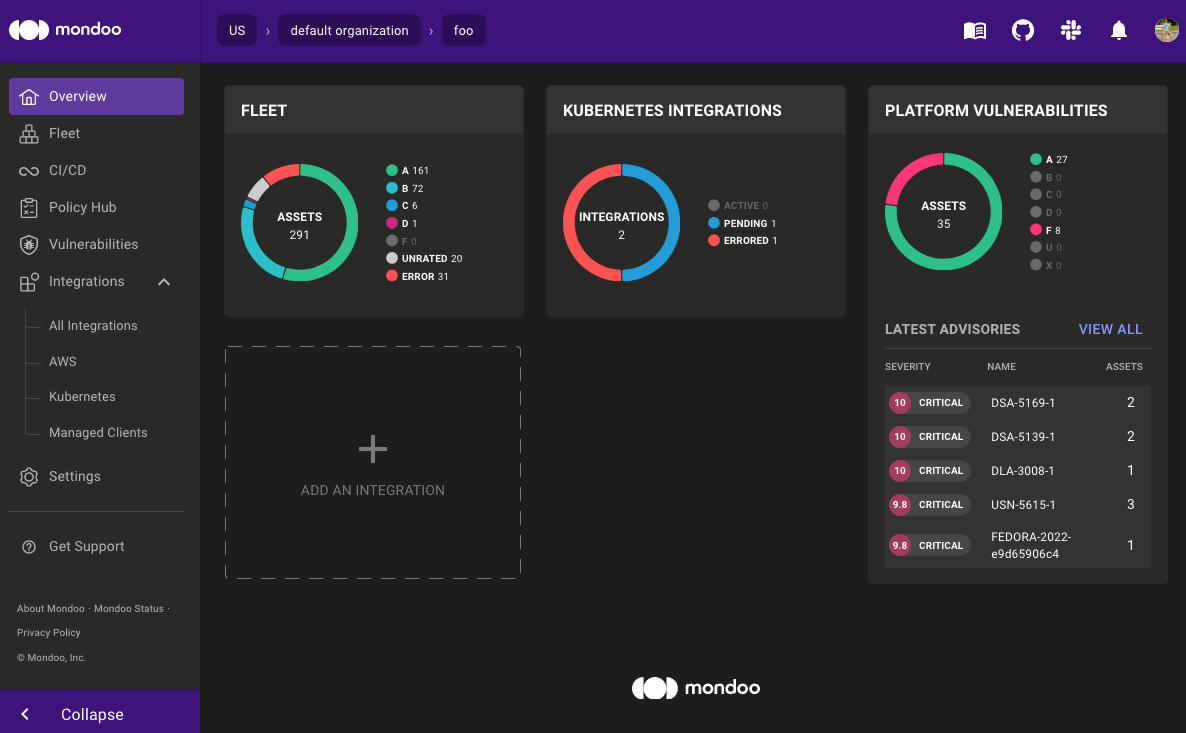
Sub-items in the menu make it easier to find what you're looking for without having to navigate through multiple pages. For example to view Kubernetes integrations you can select Integrations -> Kubernetes in the menu instead of loading the Integrations page and then selecting Kubernetes. This new menu also includes quick access to the Mondoo Vulnerability Database, which was previously buried deep in the Policy Hub. If you're thinking "I didn't know there was a Mondoo Vulnerability Database," well, that's why we have new menu.
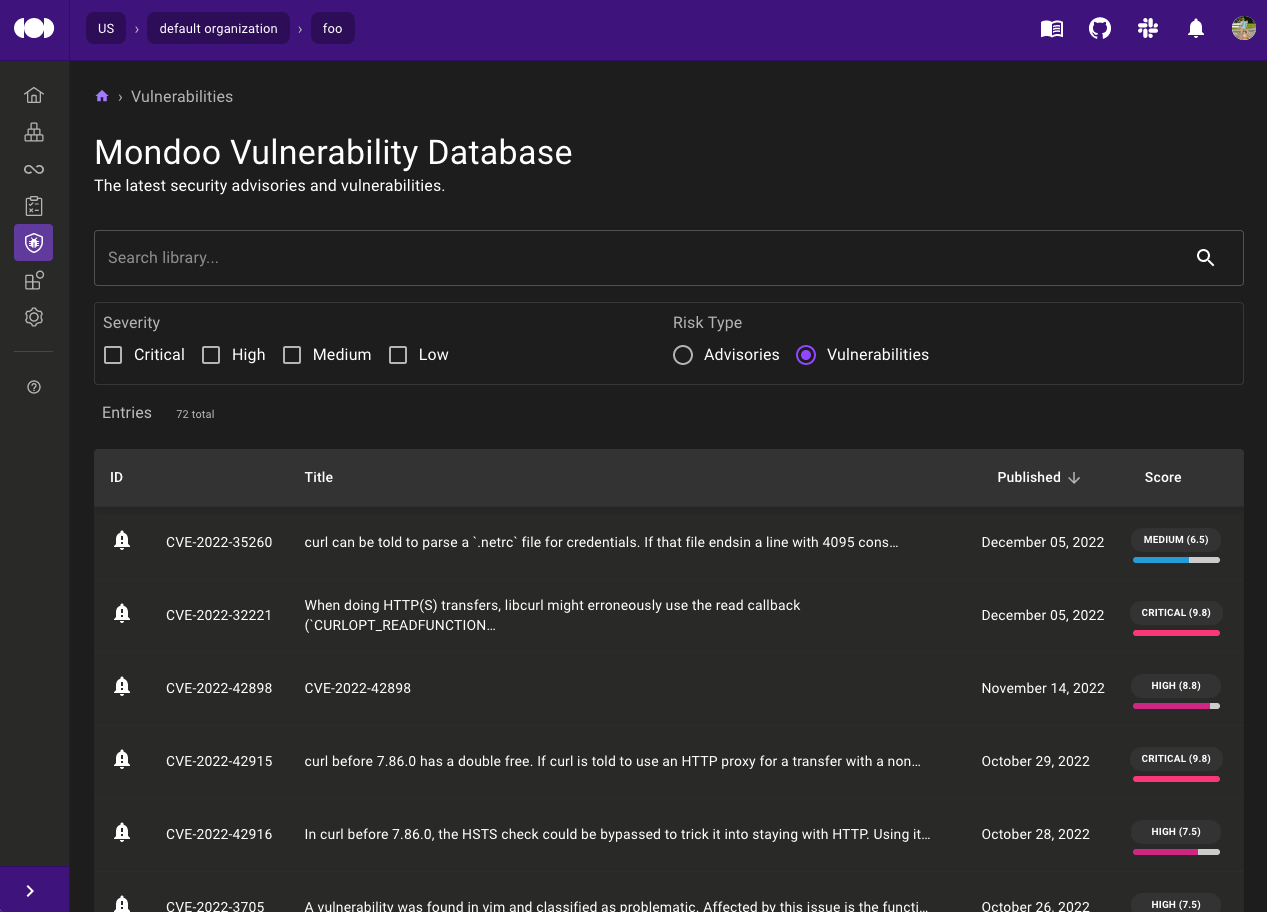
We have plenty more planned to fill out this new navigation menu, so stay tuned for new releases.
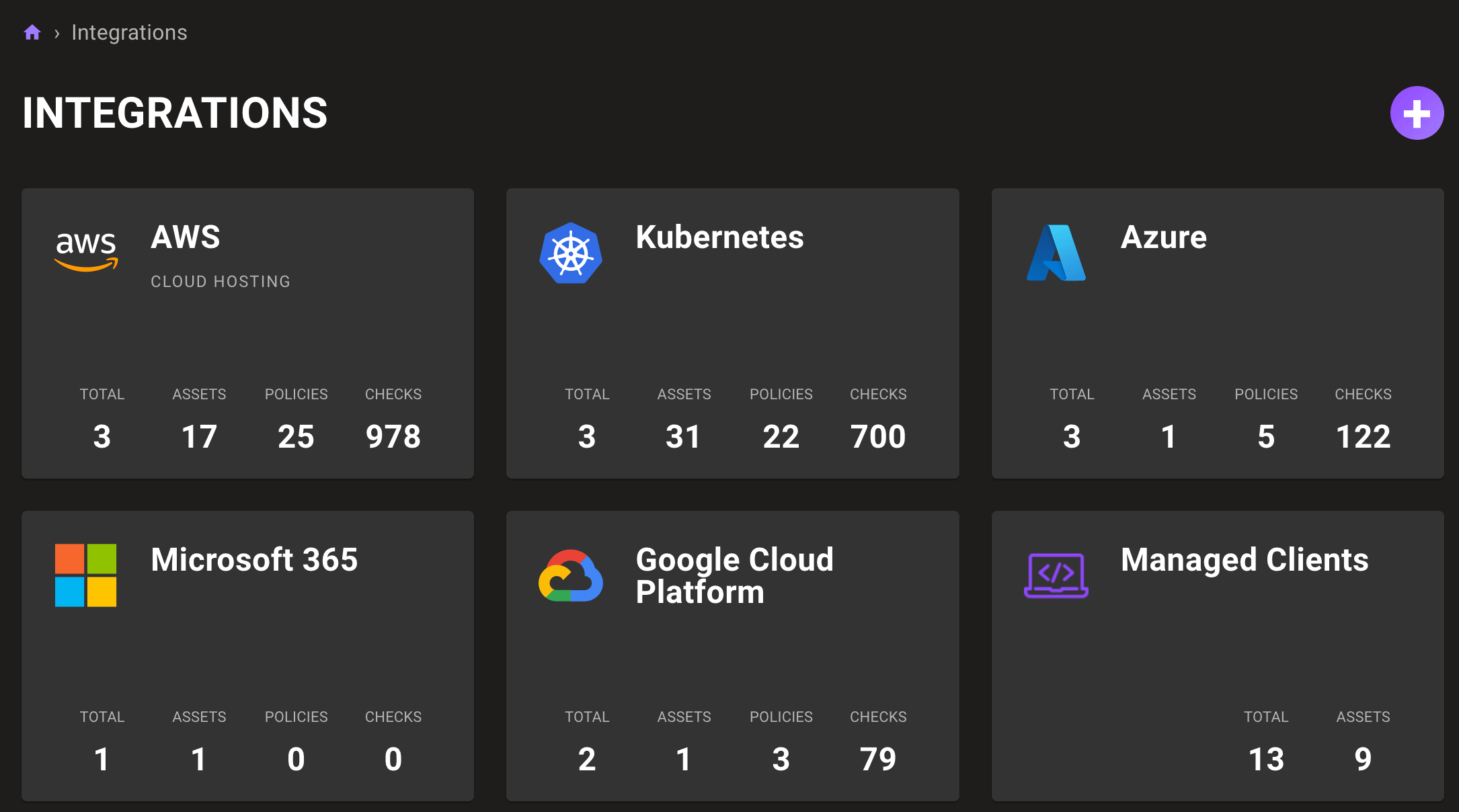
New GCP, Azure, and Microsoft 365 integrations
Problem: You need to continuously assess the security of all your cloud and SaaS resources.
Solution: You can now configure continuous scanning of GCP, Azure, and even Microsoft 365 services through the Mondoo Console. There's no need to download an agent or deploy any code into your infrastructure. Configure ready-only service credentials in the Mondoo Console and let Mondoo do the rest.
Manage vault secrets data with cnspec and cnquery
Problem: You want to use a Mondoo inventory file to scan multiple assets, but you also need to securely store any required secrets.
Solution: cnspec and cnquery now include the ability to manage secrets data in vaults directly using the command line.
Given an existing Mondoo inventory file:
kind: Inventory
spec:
assets:
- id: 34.122.119.102
connections:
- host: 34.122.119.102
backend: ssh
credentials:
- type: password
user: chris
password: mypwd
You can use this inventory file to scan all defined assets:
cnspec scan --inventory-file inventory.yml
To securely store the secrets in this vault, you can define a keychain vault:
cnspec vault set mondoo-client-vault --type keyring
→ set new vault configuration name=mondoo-client-vault
→ stored vault configuration successfully
Then confirm that the vault is configured with the vault list command:
cnspec vault list
vault : mondoo-client-vault (keyring)
Next, add your secret to the keychain vault with the vault add-secret command:
cnspec vault add-secret mondoo-client-vault my-linux-user-secret '{ "user": "chris", "type": "password", "password: mypwd" }'
Now, you can reference the secret from the vault in your inventory:
kind: Inventory
spec:
assets:
- id: 34.122.119.102
connections:
- host: 34.122.119.102
backend: ssh
credentials:
- secret_id: my-linux-user-secret
vault:
name: mondoo-client-vault
type: keyring
Re-run the scan, and you will see that the secret was picked up:
cnspec scan --inventory-file inventory.yml
New AWS MQL resources
Problem: You want to write policies to secure your Amazon ECR images and Amazon CloudFront distributions.
Solution: Mondoo now includes new resources for Amazon ECR and CloudFront so you can explore and secure even more of your Amazon infrastructure using MQL.
Querying ECR images:
cnquery> aws.ecr.images { * }
aws.ecr.images: [
0: {
registryId: "172746783610"
tags: [
0: "latest"
]
digest: "sha256:0c78b32ef7f3b41e3ed3115488d64a6faf7a3cdade2a5eb720092b6e8e0a88ca"
repoName: "vjtestpriv"
mediaType: "application/vnd.docker.distribution.manifest.v2+json"
}
]
cnquery> aws.ecr.publicRepositories { * }
aws.ecr.publicRepositories: []
cnquery> aws.ecr.privateRepositories { * }
aws.ecr.privateRepositories: [
0: {
uri: "172746783610.dkr.ecr.us-east-1.amazonaws.com/vjtestpriv"
public: false
region: "us-east-1"
registryId: "172746783610"
name: "vjtestpriv"
arn: "arn:aws:ecr:us-east-1:172746783610:repository/vjtestpriv"
images: [
0: aws.ecr.image id = vjtestpriv/sha256:0c78b32ef7f3b41e3ed3115488d64a6faf7a3cdade2a5eb720092b6e8e0a88ca
]
}
]
Querying CloudFront distributions and functions:
cnquery> aws.cloudfront { distributions { *} functions { * } }
aws.cloudfront: {
distributions: [
0: {
origins: [
0: aws.cloudfront.distribution.origin id = 185972265011/test-1be01d1424077260.elb.us-east-1.amazonaws.com
]
status: "Deployed"
cacheBehaviors: []
domainName: "d1w4eig1i8et92.cloudfront.net"
arn: "arn:aws:cloudfront::185972265011:distribution/E3J92HBG5Z8S6Q"
defaultCacheBehavior: {
AllowedMethods: {
CachedMethods: {
Items: [
0: "HEAD"
1: "GET"
]
Quantity: 2.000000
}
Items: [
0: "HEAD"
1: "GET"
]
Quantity: 2.000000
}
CachePolicyId: "658327ea-f89d-4fab-a63d-7e88639e58f6"
Compress: true
DefaultTTL: null
FieldLevelEncryptionId: ""
ForwardedValues: null
FunctionAssociations: {
Items: null
Quantity: 0.000000
}
LambdaFunctionAssociations: {
Items: null
Quantity: 0.000000
}
MaxTTL: null
MinTTL: null
OriginRequestPolicyId: null
RealtimeLogConfigArn: null
ResponseHeadersPolicyId: null
SmoothStreaming: false
TargetOriginId: "test-1be01d1424077260.elb.us-east-1.amazonaws.com"
TrustedKeyGroups: {
Enabled: false
Items: null
Quantity: 0.000000
}
TrustedSigners: {
Enabled: false
Items: null
Quantity: 0.000000
}
ViewerProtocolPolicy: "allow-all"
}
}
]
functions: [
0: {
status: ""
arn: "arn:aws:cloudfront:global:185972265011::/functions/vjtest"
comment: ""
stage: "DEVELOPMENT"
name: "vjtest"
runtime: "cloudfront-js-1.0"
lastModifiedTime: "2023-01-29T21:07:01Z"
createdTime: "2023-01-29T21:07:01Z"
}
]
}
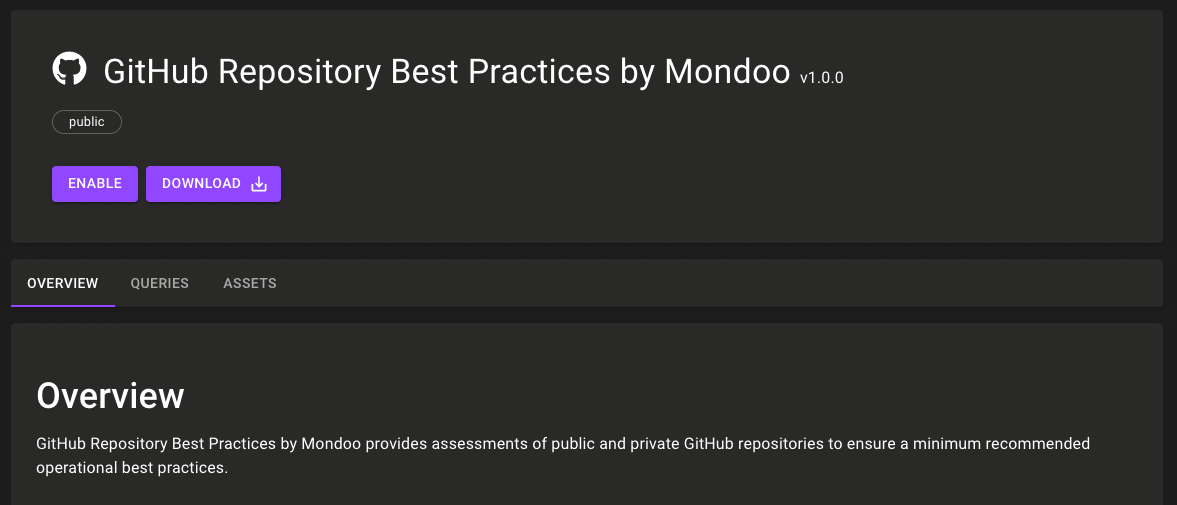
GitHub Repository Best Practices policy
Problem: You want to see the state of your GitHub repositories, including both security and best practices violations.
Solution: We split out non-security checks in the GitHub Repository Security by Mondoo policy into a new policy, GitHub Repository Best Practices by Mondoo, so you can report security and best practices issues independently from one another. We've also added a new query to the GitHub Repository Security by Mondoo policy to ensure repositories are configured to use Dependabot to report available updates for package management lock files, GitHub Actions, or Docker base images.
🧹 IMPROVEMENTS
Terraform configs now scan as terraform-hcl platform
It isn't always clear that the terraform platform in fleet view was Terraform HCL configuration files, so we've renamed the terraform platform to terraform-hcl. Existing assets will continue to scan and display as terraform until scanned with an updated client.
Add publicAccessPrevention to gcp.storage.buckets resource
The gcp.storage.buckets resource now includes publicAccessPrevention data. Here's an example of querying this data out for all buckets in a project:
gcp.storage.buckets { iamConfiguration['publicAccessPrevention'] }
gcp.storage.buckets: [
0: {
iamConfiguration[publicAccessPrevention]: "inherited"
}
1: {
iamConfiguration[publicAccessPrevention]: "inherited"
}
2: {
iamConfiguration[publicAccessPrevention]: "inherited"
}
3: {
iamConfiguration[publicAccessPrevention]: "inherited"
}
]
🐛 BUG FIXES AND UPDATES
- The + button on the Managed Clients page now properly links to "Server & Endpoint Security" integrations.
- The platform column in the Managed Clients page now displays platform values
- Notification bell now indicates the number of unread notifications.
- Update several integration logos to use high-resolution logos for retina displays.
- Update integration pages with more consistent headers.
- Handle errors when setting up integrations.
- Add back the missing link to documentation on the Kubernetes integration page.
- Change all references to Amazon AWS to be just AWS. No ATM machines here!
- Fix the AWS Integration counts on the overview page not always matching actual counts.
- Improve reliability of results in the CIS Microsoft Azure Foundations and CIS GCP Foundations policies
- Don't mention the legacy Library name in the Mondoo Vulnerability Database
- Update VMware examples in the console to use cnspec
