Mondoo 7.14 is out!
🥳 Mondoo 7.14 is out! This release includes expanded GitHub support, new GCP resources, and more!
Get this release: Installation Docs | Package Downloads | Docker Container
🎉 NEW FEATURES
Dive deeper into GitHub
Problem: You need out-of-the-box functionality to help you secure your GitHub organization, repositories, and users.
Solution: We've been busy improving nearly every aspect of the GitHub experience with cnspec, making it easier to apply out-of-the-box policy to secure your GitHub infrastructure and providing the resources and UI experience you need to create custom policies.
The GitHub Organization Security by Mondoo policy has been rewritten from the ground up to focus on critical security settings in your organization and repository. Existing queries focused on open source repository best practices have been removed and replaced with additional security queries to ensure settings like important branch protections are in place.
While building out this updated policy, we realized the various GitHub resources were missing important data necessary to write our out-of-the-box policy and custom policies for your organizations. We made the following changes to improve the GitHub resources:
github.repositoryresources now support repository stargazer counts, repo fork resolution, and support for repository issues.github.organizationresource now includes avatar, followers and following datagithub.userresource is greatly expanded to help examine user accountsgithub.organizationandgithub.usernow support collecting information on gists
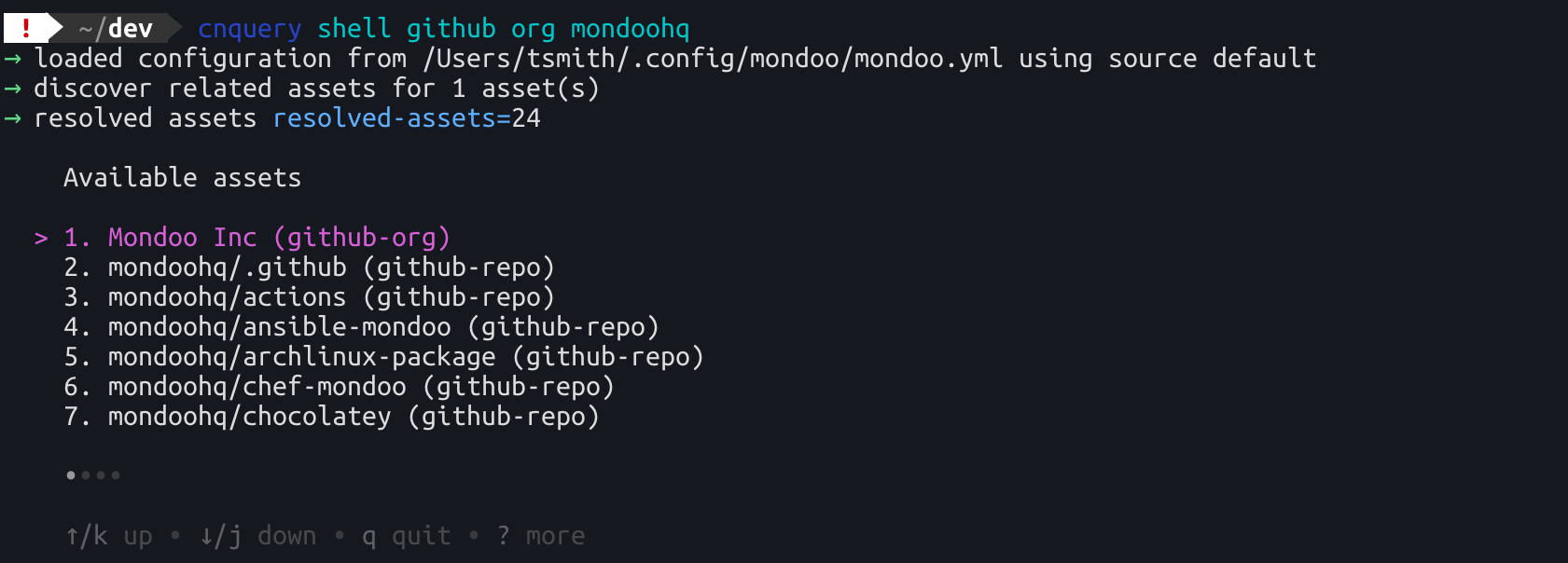
Finally, we improved cnquery to make exploring your GitHub infrastructure easier. The cnquery shell github command now shows a list of repositories to examine, making it easier to find the repository you want to explore. We also added a new cnquery shell github user command allows you to examine details on GitHub users using the expanded github.user resource.
New and updated GCP Resources
Problem: You want to explore and secure your GCP projects using cnquery and cnspec.
Solution: cnquery and cnspec now include new and improved resources for exploring and securing GCP services:
- New
gcp.project.compute.backendServicesresource - New
gcp.project.monitoring.alertPoliciesresource - Add
accessdata togcp.project.bigquery.datasetsresource - Add
accessApprovalSettingsdata togcp.organizationsandgcp.projectsresources - Add
cryptokeysdata togcp.project.kms.keyringsresource - Add
networkdata togcp.project.dns.policiesresource - Add
storageBucketdata togcp.project.logging.sinksresource - Add
retentionPolicydata togcp.project.storage.bucketsresource - Fix errors when using
gcp.project.kmswhen key status is not available - Rename
gcp.storageresource togcp.project.storage
Updated Azure CIS Policy
Problem: You need CIS policies to keep your Azure subscriptions secure and compliant.
Solution: Mondoo now includes the latest CIS Microsoft Azure Foundations Benchmark version to 1.5.0. This updated policy utilizes the latest new resources shipped with the latest versions of cnspec and includes many new queries as well as audit and remediation steps for all queries.
Store GCP service account in an inventory file vault
Problem: You want to use an inventory file to store a set of GCP assets to scan, but you don't want to insecurely store credentials in the yaml config.
Solution: You can now store your GCP service account data in a secure inventory vault so you can share inventory files without worrying about credentials. This example inventory file stores the credentials used to access GCP infrastructure using the GCP Berglas project.
YAMLapiVersion: v1kind: Inventorymetadata:name: inventoryspec:assets:- name: cool-stuffconnections:- backend: 13credentials:- secret_id: storage/random-bucket2/footype: 1secret_encoding: 3options:discover:targets:- autovault:name: gcp-berglastype: gcp-berglasoptions:project_id: mondoo-dev-262313
You can then run this inventory on the CLI without passing credentials on the CLI or within env vars:
Bashcnquery scan --inventory-file inv.yaml
Junit output format for cnspec
Problem: You want to run cnspec in your CI pipelines, but the output is hard to understand.
Solution: The cnspec CLI can now produce JUnit output on the CLI for integration with popular CI/CD platforms such as Jenkins or GitLab:
Bashcnspec scan docker debian:10 --output junit > report.junit
HTML<?xml version="1.0" encoding="UTF-8"?><testsuites><testsuite name="Policy Report for debian:10@edcf96f9d9d9" tests="85" failures="43" errors="0" id="0" time=""><testcase name="Ensure auditd is installed" classname="score"><failure message="results do not match" type="fail"></failure></testcase><testcase name="Ensure no duplicate UIDs exist" classname="score"></testcase><testcase name="Ensure root group is empty" classname="score"></testcase><testcase name="Ensure no duplicate group names exist" classname="score"></testcase><testcase name="Ensure source routed packets are not accepted" classname="score"><failure message="results do not match" type="fail"></failure></testcase>...<testcase name="Ensure login and logout events are collected" classname="score"><failure message="results do not match" type="fail"></failure></testcase></testsuite></testsuites>
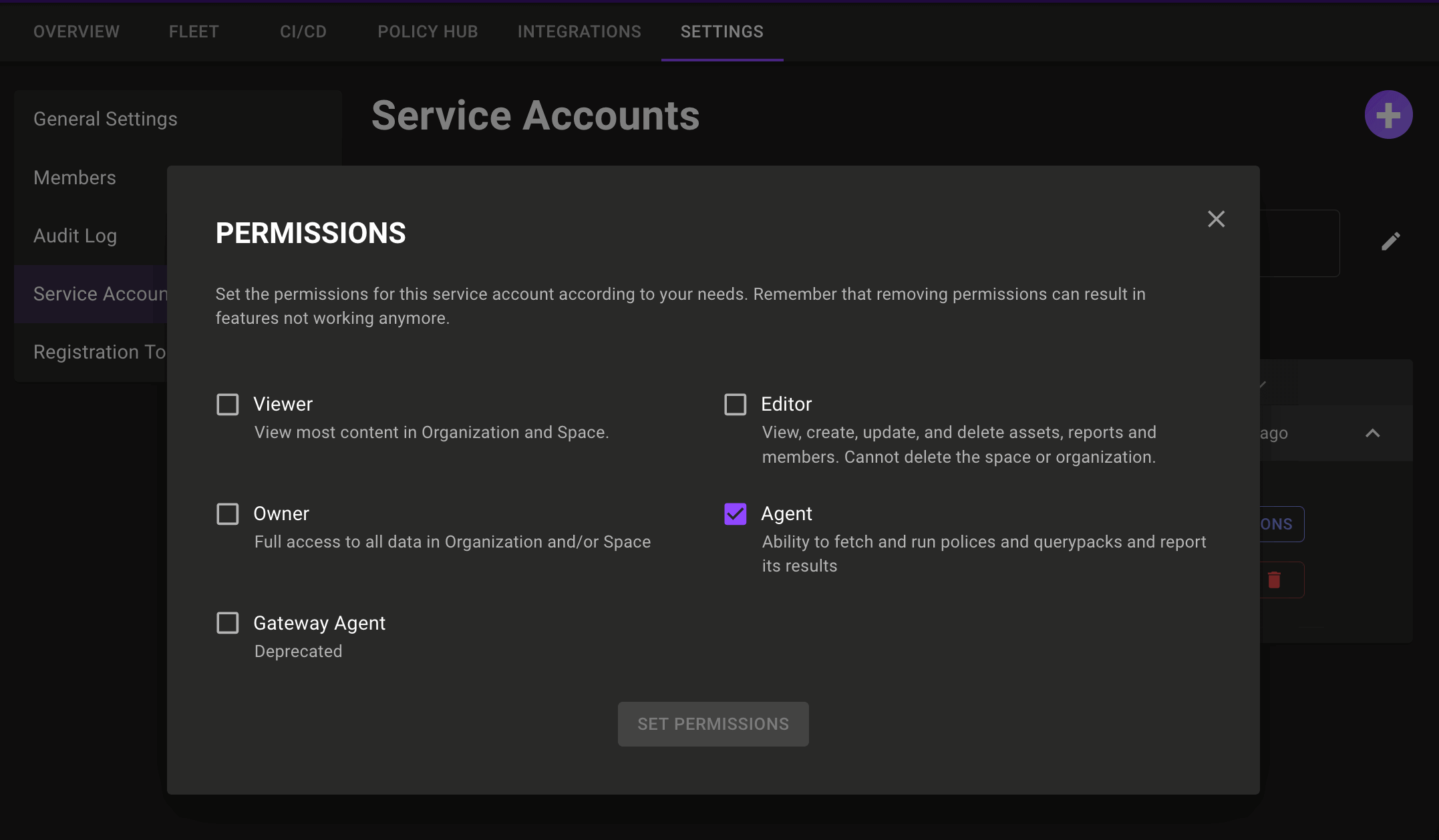
Multi-Role service accounts
Problem: You need to set additional permissions for your service accounts, but you don't want to give unnecessary permissions by using the owner role.
Solution: You can now assign more than one role to a service account in the console to provide more fine grained permissions for service accounts. To set permissions on a service account select the Settings tab, select Service Accounts, select the account you wish to edit, and then select the Permissions button.
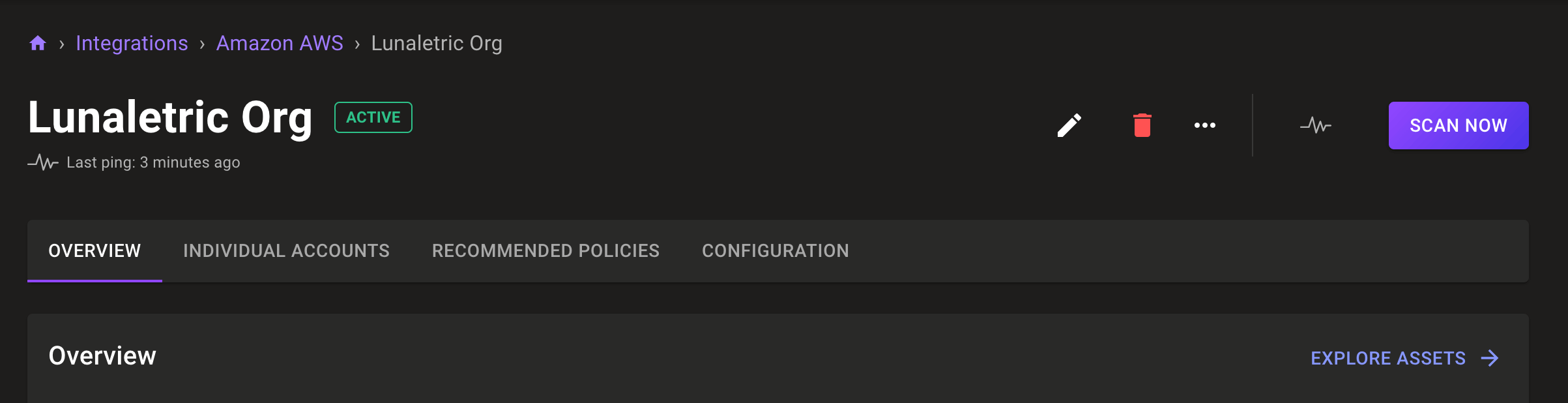
Trigger AWS integration scans directly in the console
Problem: Hassle free continuous scanning of your AWS accounts is great, but sometimes you need to trigger a scan to evaluate the current security state.
Solution: Now you can trigger a one-time scan of your AWS account in the AWS Integration page.
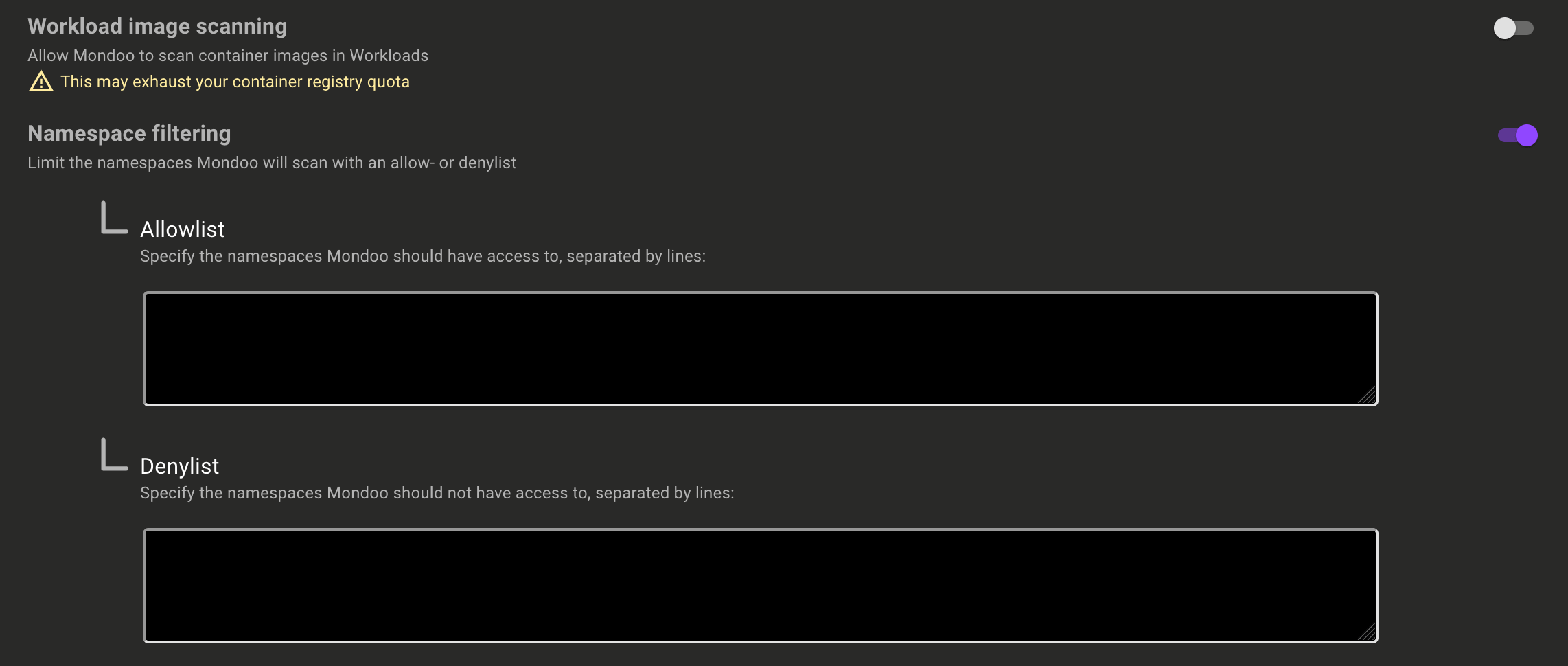
Filter namespaces to scan in the Kubernetes Operator
Problem: Different teams are responsible for different parts of a Kubernetes cluster and you need to control which namespaces the Mondoo Kubernetes Operator scans.
Solution: Mondoo now gives you more control over which namespaces are scanned by the Kubernetes Operator. Scan all namespaces, scan all namespaces except a list of specific namespaces, or take full control and only scan specified namespaces.
🧹 IMPROVEMENTS
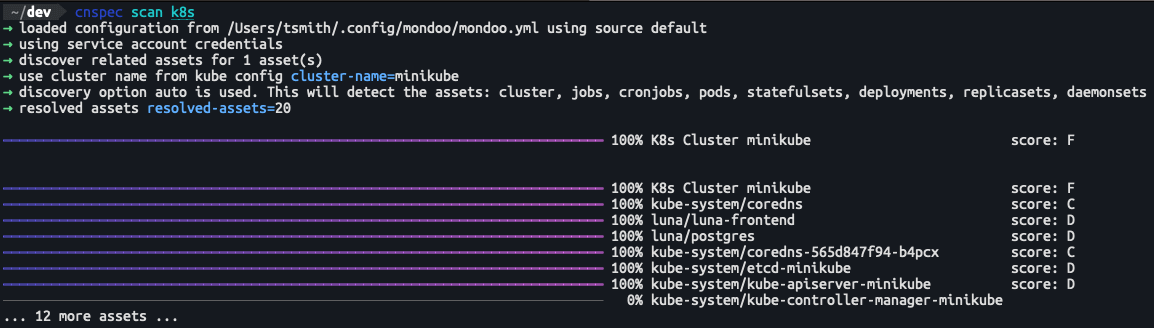
Improved multi-asset scanning CLI
We've reworked how progress bars behave when scanning complex, multi-asset infrastructure such as Kubernetes systems. The new progress bar format will allow you to see better what is currently scanning and the total progress for the cluster scan.
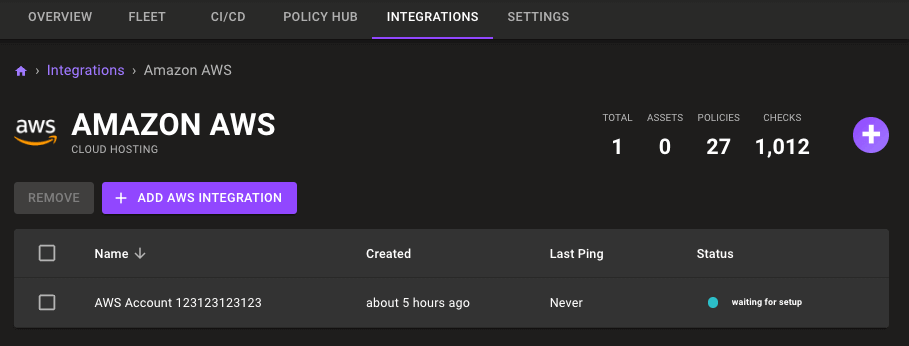
AWS integrations show asset counts
The AWS integration pages now show the total number of assets at the top of the page, similar to other integration pages.
🐛 BUG FIXES AND UPDATES
- Fix an issue where the fallback to ssh-agent authentication was not working properly
- Improve client setup instructions in the console to resolve failures
- Simplify the workstation setup instructions
- Update Packer integration instructions to use cnspec and the latest Mondoo packer plugin
- Update long-lived token instructions to use cnspec
- Make sure that query result data displays in the console scan results
- Improve the reliability of Kubernetes integration status data in the console
- Fix the loading of inventory files when cnspec is running in serve mode
- Fix BSI/CIS/Mondoo Windows policies to account for users on a system that have not yet logged in
- Improve remediation steps in Mondoo and CIS policies
- Resolves slow loading times on the integrations tab
- Fix vendor specific icons not always displaying for policies in Policy Hub
- Add alias for
mondoo loginto the existingmondoo registercommand so that cnspec and mondoo commands match