Mondoo 7.1 is out!
🥳 Mondoo 7.1 is out! This release includes UI and policy improvements!
Get this release: Installation Docs | Package Downloads | Docker Container
🎉 NEW FEATURES
Local Provider by Default
Problem: You just want to scan your local system for security misconfigurations without needing to think about scan providers.
Solution: We've made mondoo scan default to the local system once again. With this change you can easily scan your local system without the need to specify the local provider.
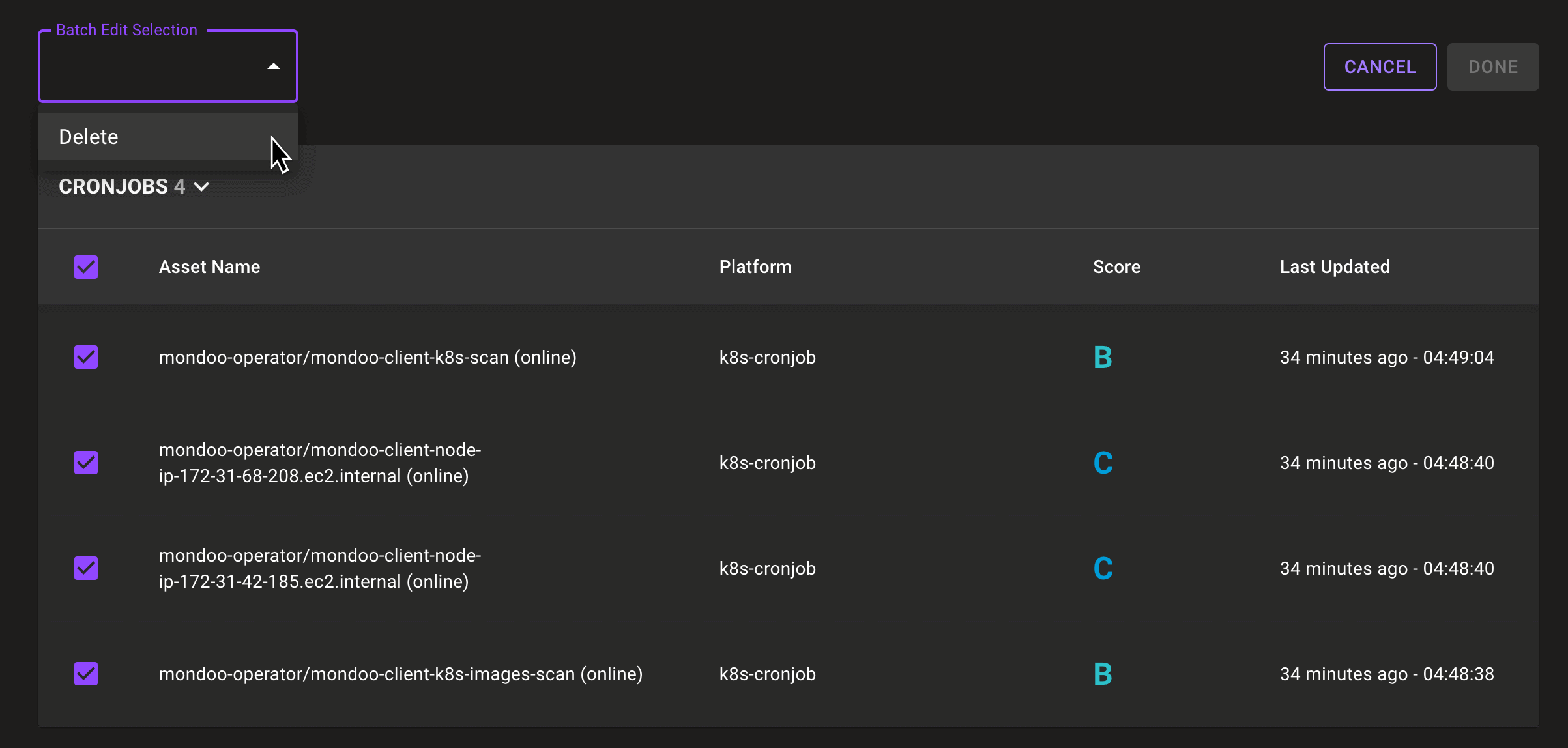
Bulk Delete Assets
Problem: You have a large number of assets that you want to clean up, but deletion involves opening each asset and selecting the delete icon.
Solution: You can now multi-select and delete assets directly from the fleet view. Select the pencil icon in the top-right corner of the asset list, check each asset to delete. From the Batch Edit Selection pull down menu, select Delete.
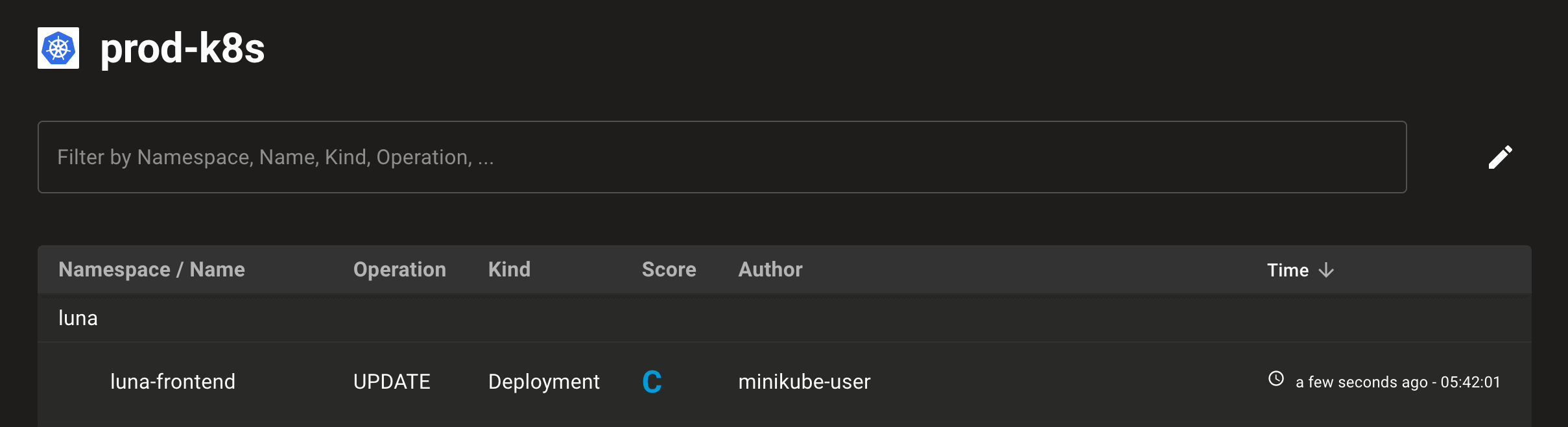
Group Kubernetes Admissions Controller Scans by Namespace
Problem: New deployments come into Kubernetes clusters at a dizzying pace and it's often hard to see which new workflows are being deployed to which namespaces.
Solution: We've reworked the Kubernetes admission controller UI in the CI/CD tab to better show which namespaces workflows are being deployed into. This helps group similar scans so you can more easily escalate issues to the proper teams.
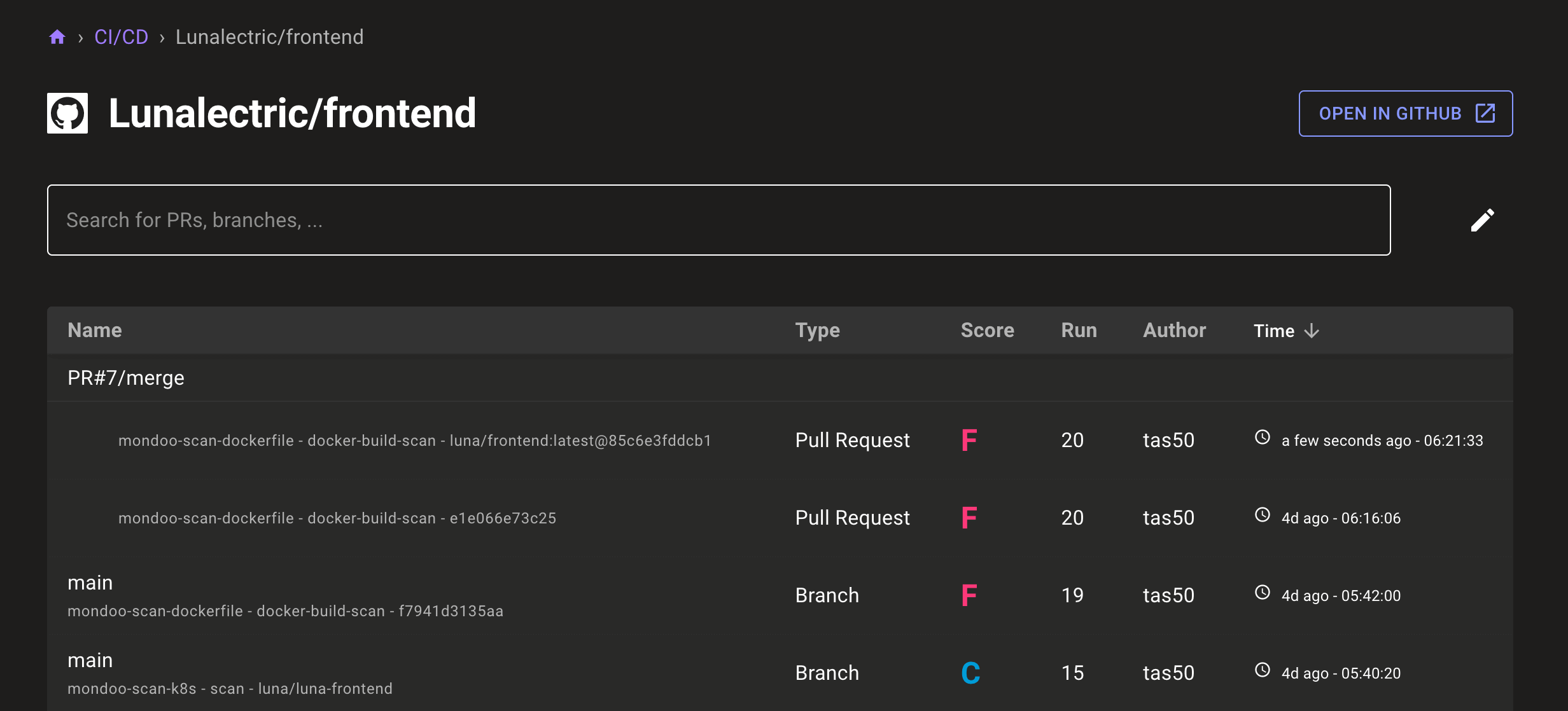
Group Multiple CI Scans
Problem: It's often useful to run multiple Mondoo scans in your CI/CD pipelines, but the scans don't show up together in the Mondoo CI/CD project pages.
Solution: Scans are now grouped together in the CI/CD project pages so you can better tell which scans ran in the same branch commits or PRs.
Ignore Kubernetes Namespaces in Scans
Problem: You have a large Kubernetes cluster with different namespaces owned by different teams, and you don't want to scan the entire cluster at once.
Solution:
We've added two new CLI flags to allow you to control which namespaces to scan and which to skip. To scan all namespaces except ones that you specify, use the --namespaces-exclude flag. To scan just the namespaces you specify, use the --namespaces flag.
Shellmondoo scan k8s --namespaces-exclude mondoo-operatormondoo scan k8s --namespaces luna-ui,luna-backend
New Microsoft Azure Security by Mondoo policy
Problem: You want to secure your Azure infrastructure against common security misconfigurations
Solution: Mondoo now includes a new Azure Security by Mondoo policy. This policy provides guidance for establishing minimum recommended security and operational best practices for Azure. This policy includes ten controls, with new controls planned for future Mondoo releases.
🧹 IMPROVEMENTS
SSM Connections using Instance Name
You can now scan AWS instances using Amazon's SSM using either the IP or the instance name. This makes it easier to scan instances using the names shown in the awscli or the AWS Management Console.
Use Shorter Container Names
Mondoo now includes the shortened container SHAs to match the Docker experience. These short container names fit better in the UI and match the names shown when running Docker CLI commands.
VMware Appliance Now Auto Upgrades Mondoo
We know you want the latest Mondoo Client capabilities so you can run updated policies, so we've updated the Mondoo VMware appliance to automatically pull in the latest client releases. No more compatibility concerns or time spent manually updating the instance.
Better Examples in CI Integration Pages
The CI/CD integration setup pages now include additional example configuration files, making it easier to setup Mondoo in your CI pipelines.
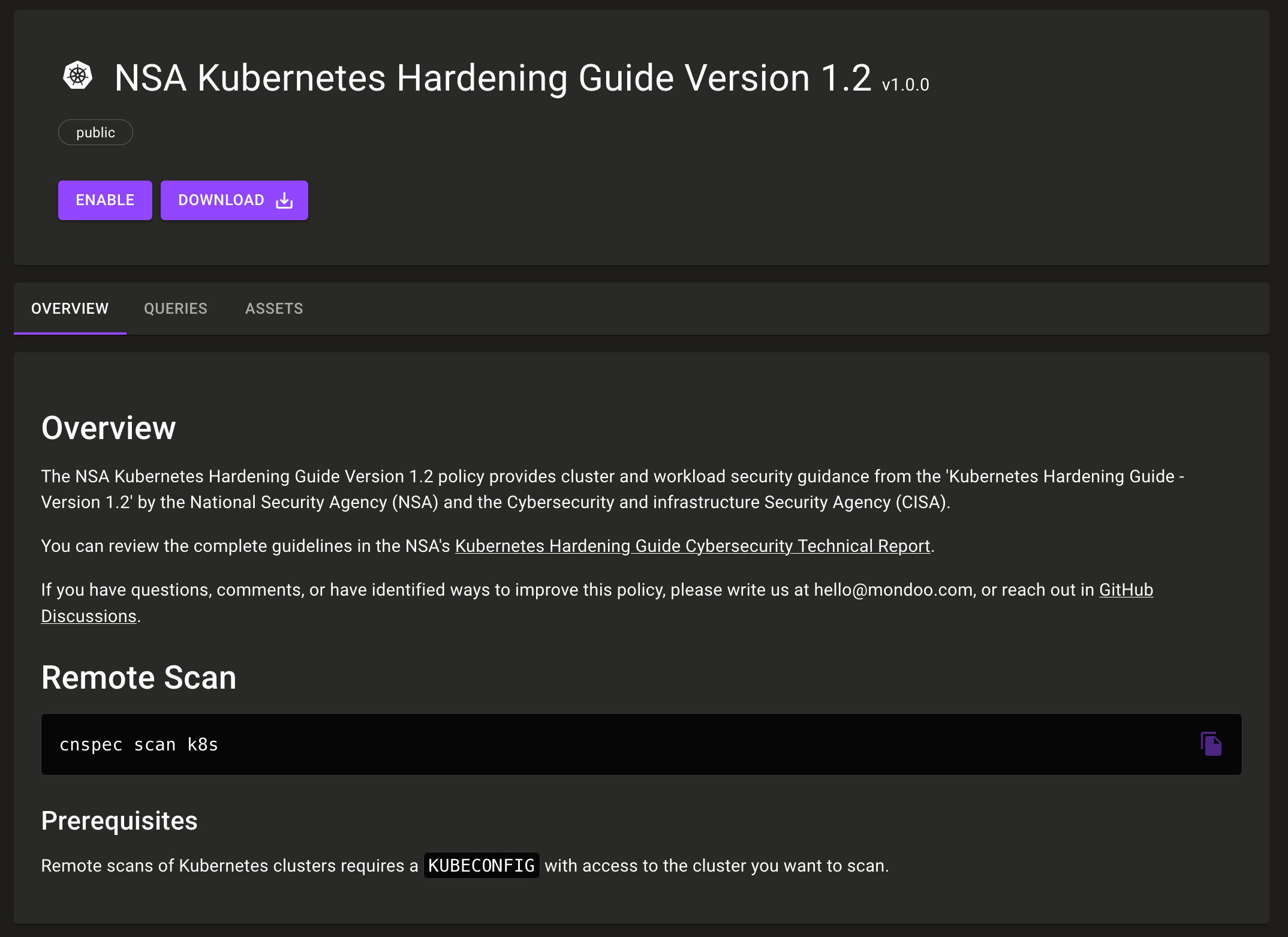
NSA Kubernetes Hardening Guide Version 1.2 Generally Available
The NSA Kubernetes Hardening Guide Version 1.2 policy is no longer considered to be a preview release after the addition of several new controls and fixes:
- Add an improved policy description with example usage information.
- Update remediation steps to improve clarity.
- Switch policy scoring system so that the policy score on an asset matches the worst offense found rather than the average of all scores (which previously could mask critical issues).
- Update controls to properly run on the Kubernetes cluster asset itself when appropriate.
- Fix
Ensure that the Kubernetes PKI/SSL directory is owned by root:rootcontrol to work on Minikube. - Split
Pods should not run with NET_RAW or SYS_ADMIN capabilitiescontrol into two controls so it can be disabled at a more granular level. - Add new controls:
CVE-2021-25742 - checking nginx-ingress ConfigMaps for dangerous settingsDo not allow ClusterRoles that allow users execution privileges into containersDo not allow roles that allow users execution privileges into containersMinimize and verify access to cluster-admin binding via rolebindingsMinimize and verify access to cluster-admin binding
Policy Improvements
We continue to improve the descriptions, remediation steps, and reliability of our out-of-the-box Mondoo policies so you can secure your infrastructure with less effort. This week we've made the following policy improvements:
- Add improved descriptions and remediation steps to all Kubernetes Security controls.
- Add getting started guides to each Mondoo policy with usage information.
- CIS and BSI Linux policies now accept the
shadowgroup when checking permissions on/etc/shadowand/etc/shadow-. - Move additional queries in the CIS Kubernetes policies from the cluster asset to the individual workload assets. This helps more quickly identify the workload in question and allows for more granular skip/disables.
- Adjust impact levels in the CIS and Mondoo Linux policies to lower levels where appropriate.
- Disable alerting of Pod Security Standard policies in the mondoo-operator namespace as enabling PSS would break operator functionality.
- Improve descriptions and remediation steps for
/etc/*file check controls in Linux Security by Mondoo policy. - Remove
livenessProbeandreadinessProbechecks from CronJobs and Jobs inKubernetes Best Practices by Mondooas these recommendations don't apply to Job and CronJob workloads. - Update remediation steps in Linux Security policy's
Ensure system accounts are non-logincontrol to properly identify high UID system accounts. - Fix incorrect remediation step in Linux Security by Mondoo policy's
Ensure secure permissions on SSH private host key files are setcontrol. - Fix
AWS Security by Mondoopolicy'sEnsure there is only one active access key available for any single IAM usercontrol to properly check that one key is active.
Time + operator in MQL
We've added a new + operator to the Time resource so you can more easily manipulate time values in your MQL queries. This makes queries like the ones below possible:

🐛 BUG FIXES AND UPDATES
- Update the CI integrations pages to provide correctly encoded Mondoo credentials for use with CI platforms.
- Add missing icons to Mondoo policies in the Policy Hub.
- Improve alignment of enabled/selected policies in the Policy Hub.
- Fix the
MONDOO_CONFIG_PATHenvironmental variable not being honored in the Mondoo CLI. - Fix the progress bar not showing during Mondoo CLI scans.
- Update the AWS integration to skip creating an EBS snapshot if one already exists.
- Add workaround rate limiting with EBS snapshot scanning in large accounts.
- Better handle long asset names in the fleet view.
- Present the original case of the Kubernetes integration instead of uppercasing the name.
- Fix top recommended action links on CI job assets to load controls properly.
- Add missing page titles to some pages in the console.
- Fix minor UI alignment and spelling mistakes.
- Ensure that AWS account assets are created when scanning accounts.
- Don't create empty k8s-node assets when scanning Kubernetes clusters.
- Find GCP instances in all zones when scanning GCP accounts.
- Don't return an error if all policy controls are skipped.
- Add a friendly error message when trying to connect to assets over SSH without an identity file or password.
- Improve the reliability of Kubernetes asset garbage collection in the Mondoo Kubernetes Operator.