Mondoo 7.0 is out!
🥳 Mondoo 7.0 is out!
I you have been following our past releases, you'll have seen a ton of improvements that were added during the last months, including:
- Major new features for Kubernetes
- Kubernetes resource, workload, node, pods, and control plane scanning
- Automatic discovery of assets and related resources
- Mondoo Kubernetes Operator 1.0
- New and updated compliance policies, including:
- NSA, NIST, BSI, AKS, EKS, Best Practices and too many updates to mention here
- New UI for fleet views, asset relationships, recommended actions, control and policy views
- Supply chain security, including GitHub and GitLab
- Deeper CI/CD integrations (new UI, better filtering)
- support for Azure pipelines, Jenkins, CircleCI
- Extended integration for Terraform and Packer
- AWS side scanning, GCOS, and GitHub Actions
Breaking changes
- The previously deprecated features from v5.x have now been removed. If you have any old clients running v5.x, they will stop working with this release. Please upgrade to the latest version. All v6.x clients continue to be supported.
- During v5.x policies were compiled differently. The changes are behind the scenes. Simply re-run policies with a new version of Mondoo.
- Previously scanned results that were collected as
nullmay now show up as empty values. Once the asset is re-scanned, this is fixed.
Deprecations
All deprecations will be supported throughout the lifetime of Mondoo v7. We will remove them when we release Mondoo v8.
- We have a major open-source announcement coming next week. After it, we will start to deprecate the current
mondooCLI in favor of the new commands. Don't worry: it's a drop-in replacement and smooth transition. - We are removing the need to call
.listfor many resources that have required it so far. For exampleusers.listnow becomesusers,ports.listbecomesportsand so on. Please note, that blocks are now automatically applied to the child elements of such lists. For exampleusers { name }is valid, butusers { list }is now deprecated and will be removed in v8. This is relevant for e.g.ports.listening { ... }. Since the block applies to individual blocks, you don't want to write e.g.ports { listening }anymore.
Get this release: Installation Docs | Package Downloads | Docker Container
🎉 NEW FEATURES
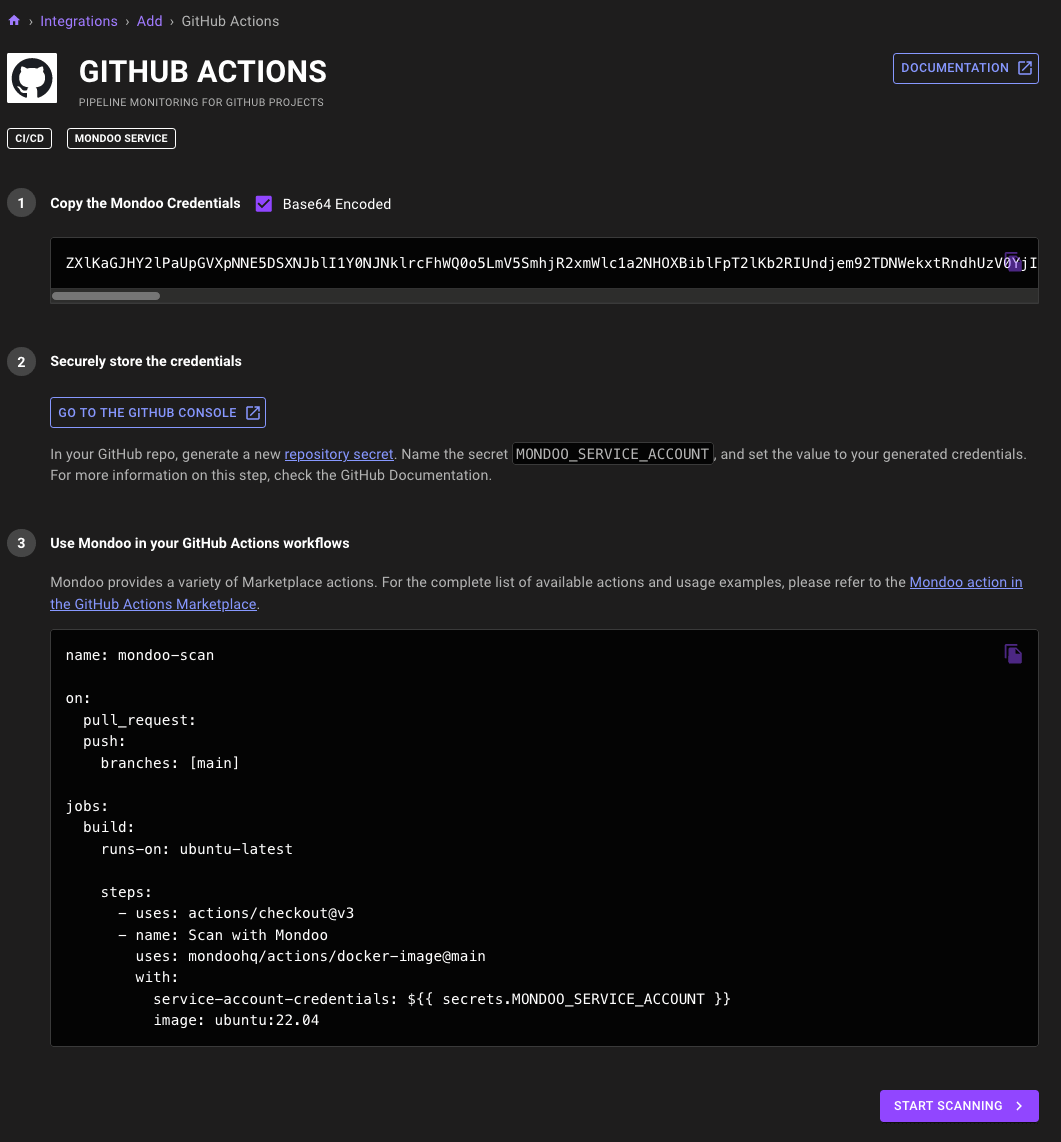
CI Setup in Integration
Problem: You want to set up Mondoo to scan projects through your favorite CI systems, but the setup is manual and requires jumping between the Mondoo Console and documentation.
Solution: We've revamped how Mondoo CI integrations are set up to make them faster and more intuitive to set up. Gone is the manual service account setup process and documentation site, and in its place are CI projects set up through the Integrations tab in the console, just like other integrations. Service account tokens are automatically created, and the integration setup process now suggests helpful policies for use with your CI projects.
🧹 IMPROVEMENTS
Updated EOL Data
We've updated our platform EOL data with new platform versions, so you always have the most up-to-date data:
- Added Google Container OS 101 with a release date of Sept 15, 2002, and an EOL date of Sept 1, 2024.
- Added Google Container OS release date information for milestone 97, 93, and 89.
- Added macOS 13.0 with a release date of Oct 24, 2022.
- Updated macOS 10.14 with an EOL date of Jul 21, 2021 when the last security update was released.
Improved Mondoo Operator Security
We've improved the security of the Mondoo Kubernetes Operator by dropping unnecessary privileges from any pods that are created by the operator.
New and Improved Policies
- All Mondoo policies now include additional usage guidance with examples of how to run the policies using cnspec.
- Linux Security by Mondoo policy's auditd controls now fail instead of erroring if auditd configs are not found.
- Policy control UIDs in
Mondoo TLS/SSL Security Baseline,Linux Workstation Security by Mondoo, andLinux Security by Mondoopolicies better describe what is being checked. - Kubernetes Cluster and Workload Security by Mondoo policy's
Ensure that the Kubernetes PKI/SSL directory is owned by root:rootcontrol properly handles paths on Minikube. - CIS Kubernetes Worker Node Level 1 policy's
Ensure that the Kubelet only makes use of Strong Cryptographic Cipherno longer results in a query error on Minikube. - CIS Kubernetes Master Level 1 policy's Pod Security Standards controls have been updated to not run against workloads.
- CIS Ubuntu 20.04 Server Level 1 policy's
Ensure password creation requirements are configuredno longer errors if PAM is not installed, such as when Mondoo is scanning a container or container image. - CIS Ubuntu 20.04 Server Level 1 policy's
Ensure chrony is configuredno longer errors if chrony's config is not found. - Terraform HCL Security Static Analysis for Google Cloud policy's
Ensure that Cloud Storage bucket is not publicly accessiblecontrol was updated to improve reliability. - NSA Kubernetes Hardening Guide Version 1.2 policy's
Ensure that the --audit-log-maxsize argument is set to 100 or as appropriateandEnsure that the --audit-log-maxbackup argument is set to 10 or as appropriatechecks now check for the proper values. - NSA Kubernetes Hardening Guide Version 1.2 policy now includes new controls to check for secure cryptographic ciphers on the API Server and Kubelets.
🐛 BUG FIXES AND UPDATES
- Add links to download Mondoo Client to the manual setup instructions on the Workstation integration page.
- Add missing breadcrumbs to the Policy Hub pages to make it easier to navigate
- Avoid a scan failure when a
/proc/sysfile cannot be read. - Don't show controls skipped due to conditionals in policies as being
disabledon assets. - Don't show double asset scans in the CI projects.
- Fix container images being incorrectly classified as operating system assets.
- Fix incorrect breadcrumb names on some integration pages.
- Fix incorrect Kubernetes namespace IDs in
k8s.namespaces{ id }if Kubernetes objects have no namespace. - Fix the
--sudoflag not being honored when runningmondoo scan - Fix the
mondoo.versionMQL query not returning the correct version - Google Container OS systems are now properly categorized as operating systems instead of "Uncategorized Assets"
- Mondoo Platform links for CI/CD jobs on the CLI now go to the proper CI/CD asset view.
- Only show asset scheduled EOL warning if the vendor has scheduled the EOL for less than one year in the future.
- Performing an empty search in the Fleet view no longer goes to an error page.
- Policy descriptions on Policy Hub no longer suggest the legacy
mondoo scan -tCLI format. - Policy Hub no longer lists potentially incorrect manual scan instructions.
- Properly render the list of assets when navigating through the pagination.
- Remember the previous fleet filter selection when returning to the fleet page after viewing an asset.
- Resolved failures running
mondoo scan gitlab - Resolved multiple errors when running CIS Kubernetes Master Level 1 policy on Minikube clusters.
- The initial load of the Mondoo Console no longer flashes white when dark mode is enabled.
- Updates the VMware and Azure integration pages to use the latest
mondoo scansyntax. - Warn when using
mondoo scan k8s --namespaceif the namespace was not found on the cluster.
