Mondoo 6.18 is out!
🥳 Mondoo 6.18 is out! This release includes new policies and better out-of-the-box Kubernetes scanning!
Get this release: Installation Docs | Package Downloads | Docker Container
🎉 NEW FEATURES
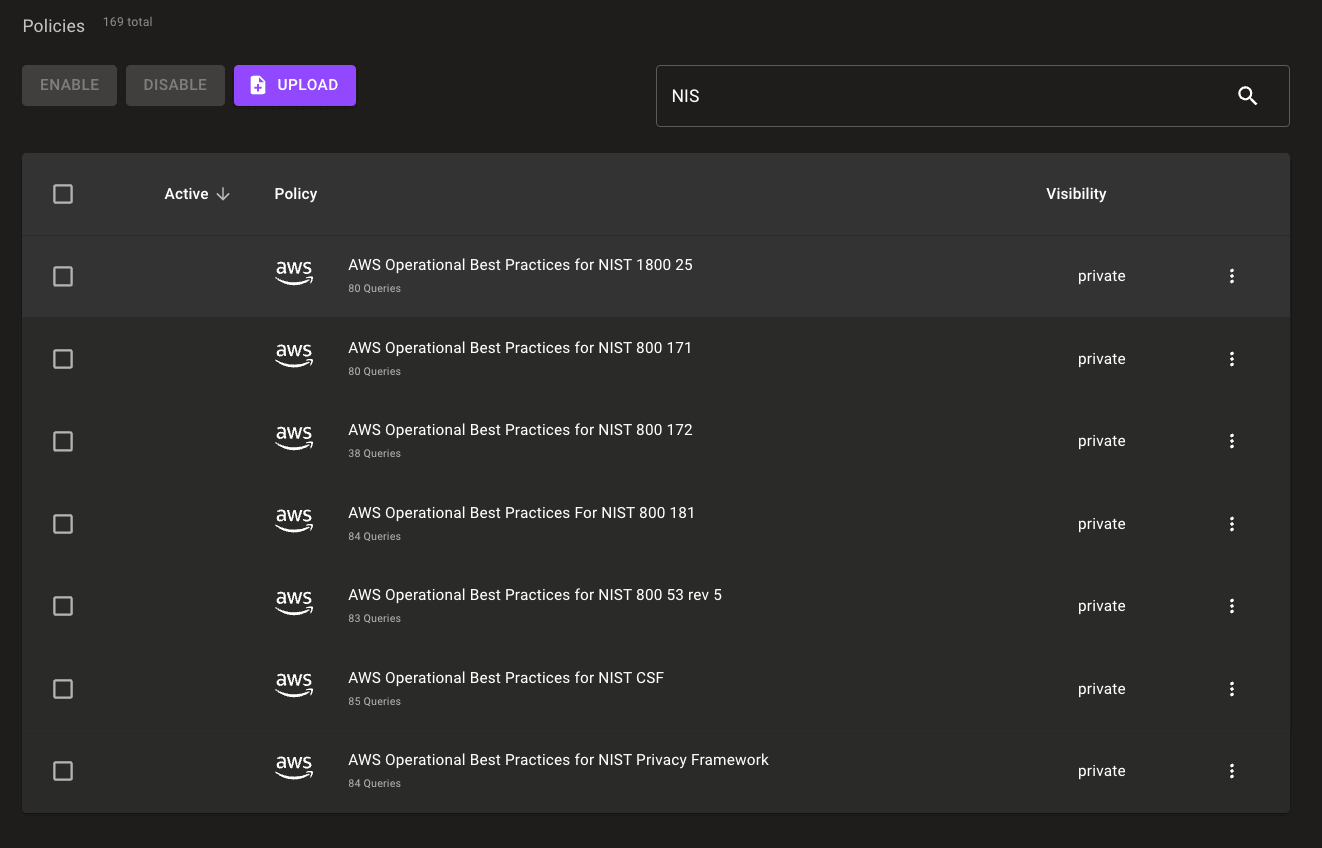
NIST Special Publication 800 Preview Policies for AWS
Problem: You need to comply with NIST Special Publication 800 guidance in your AWS environment.
Solution: We're introducing a preview of five new NIST SP 800 policies to help you keep your systems in compliance with US federal government requirements.
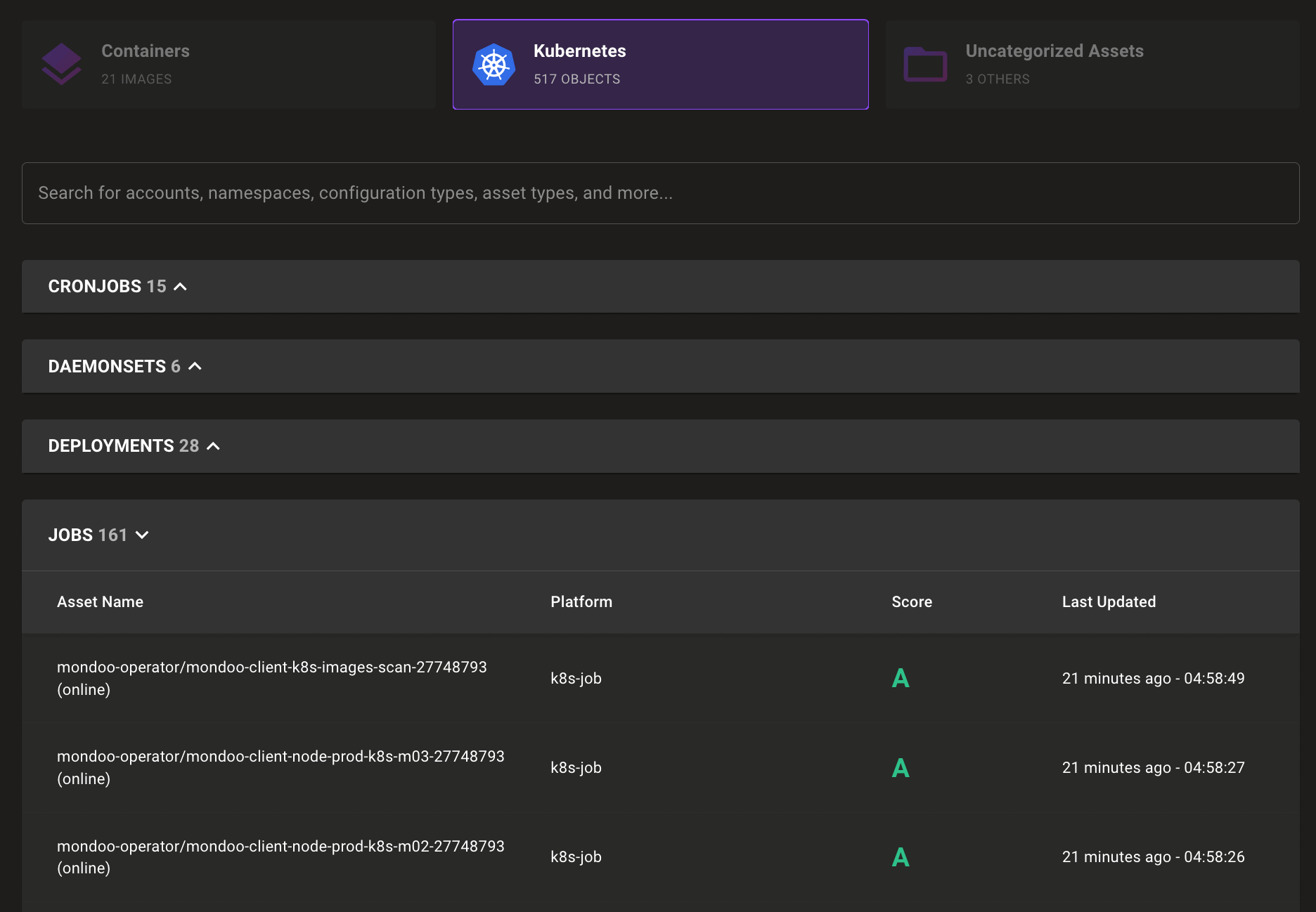
Kubernetes Asset Scanning By Default
Problem: You want to scan your Kubernetes cluster and apply the Mondoo Kubernetes Security and Kubernetes Best Practices policies to all of the workloads in your cluster. But without extra flags, only the cluster shows up and the new policies don't apply.
Solution: Mondoo Kubernetes scans now automatically scan cluster objects as assets. This provides a much more Kubernetes-friendly view of where security problems exist within your cluster. You can use our new policies with dozens of controls that aren't present in the legacy Kubernetes Application Benchmark policy.
Expanded HashiCorp Terraform GitHub Action Support
Problem: You want to set up the Mondoo GitHub Action to ensure the security of HashiCorp Terraform plans and state files so you can be confident in your changes before you apply them.
Solution: The Mondoo GitHub Action 0.7.0 now includes two new actions for scanning your Terraform code:
- Terraform State File Action scans Terraform state files for security configuration best practices.
- Terraform Plan Action scans Terraform plan repositories for security configuration best practices.
🧹 IMPROVEMENTS
Simplified Terraform State File Resource
Problem: You want to query out resources in Terraform state files without writing complex queries that dig deep into the files.
Solution: We've simplified MQL access to resources from the Terraform state files.
Before this release, you had to iterate over all Terraform modules to get access to the resources:
MQLcnquery> terraform.state.rootModule.resources { providerName == "registry.terraform.io/hashicorp/null" }terraform.state.rootModule.resources: [0: {providerName == "registry.terraform.io/hashicorp/null": true}
With this release, you can now access the resources directly from the state:
MQLcnquery> terraform.state.resourcesterraform.state.resources: [0: terraform.state.resource id = null_resource.ls]
🐛 BUG FIXES AND UPDATES
- Unknown scan status coloring is now always white throughout the console.
- Corrects control counts on the asset pages.
- Fixes small score donut charts on the asset pages.
- Searches of scans from the Kubernetes Admission Controller are now case insensitive.
- Adds missing breadcrumb links on the main Fleet page.
- Corrects sample PowerShell setup commands on the Workstation Integration page.
- Makes the asset type summary text more consistent.
- Properly detects an asset's platform.
- Improves the reliability and performance of removing policies and assets.
- Improves reliability of EBS volume scans with the AWS integration.
mondoo.versionqueries now return the correct Mondoo Client version.- Resolves errors deleting CI/CD jobs.
- Resolves Kubernetes cluster names reverting to UID from the friendly name in the CI/CD view.
- Improves the reliability of CIS Kubernetes controls that inspect the state of the Kubelet.
mondoo scan aws ec2 ebsnow respects the--option regionoption.- Resolves an error that could cause creation of empty AWS account assets when scanning instances.
- Prevents errors in the
Linux Security by Mondoopolicy when/etc/shadowis not present on a system. - Container images no longer show up in the fleet view as container registries during scans.
- Fixes parsing of OS uptime on some Linux distributions.
- Corrects reporting of Kubernetes Integration errors during cluster scans.
- Scanning a Kubernetes cluster with an invalid namespace specified no longer creates an empty cluster asset.