Mondoo 6.11.1 is out!
🥳 Mondoo 6.11.1 is out! This release includes supply chain security resources/policies, updated CIS policies, and Kubernetes enhancements!
Get this release: Installation Docs | Package Downloads | Docker Container
🎉 NEW FEATURES
Supply Chain Security Resources and Policies
Problem: In the aftermath of numerous high profile software supply chain hacks, you want to secure your software supply chain against attackers. Mondoo provided initial resources, but didn't offer a security policy out of the box.
Solution: Mondoo now includes a preview of the CIS Software Supply Chain Security Guide policy. This policy includes 18 controls to help you secure your GitHub organization and repositories. It includes important guidelines like ensuring all organization members enable MFA and limiting repository deletion to particular users. This policy is in preview as we work to implement more controls and improve the remediation guidance for failures.
As part of the development of this policy we've also greatly expanded the Mondoo git and GitHub resources. We've expanded the data returned in the github.repository, github.file, and github.branchprotection resources and added the following new resources:
github.teamgithub.collaboratorgithub.packagegithub.webhookgithub.workflowgit.commitgit.commitAuthorgit.gpgSignature
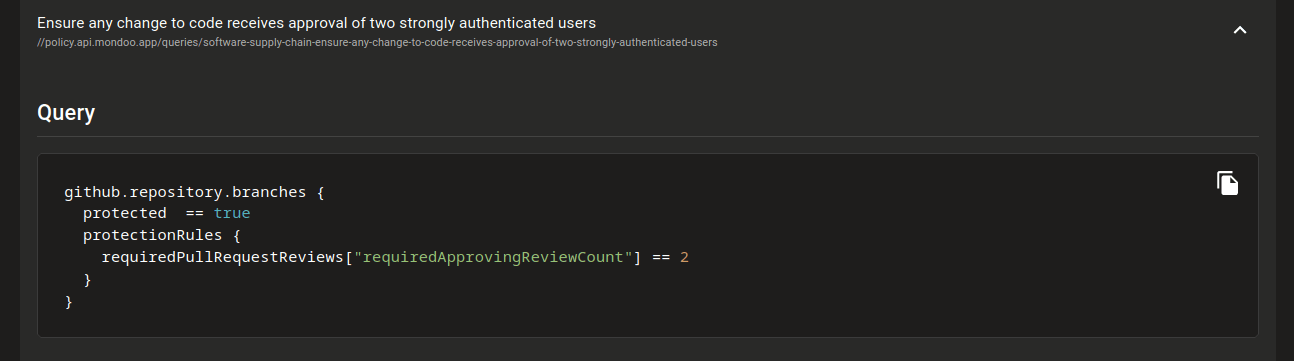
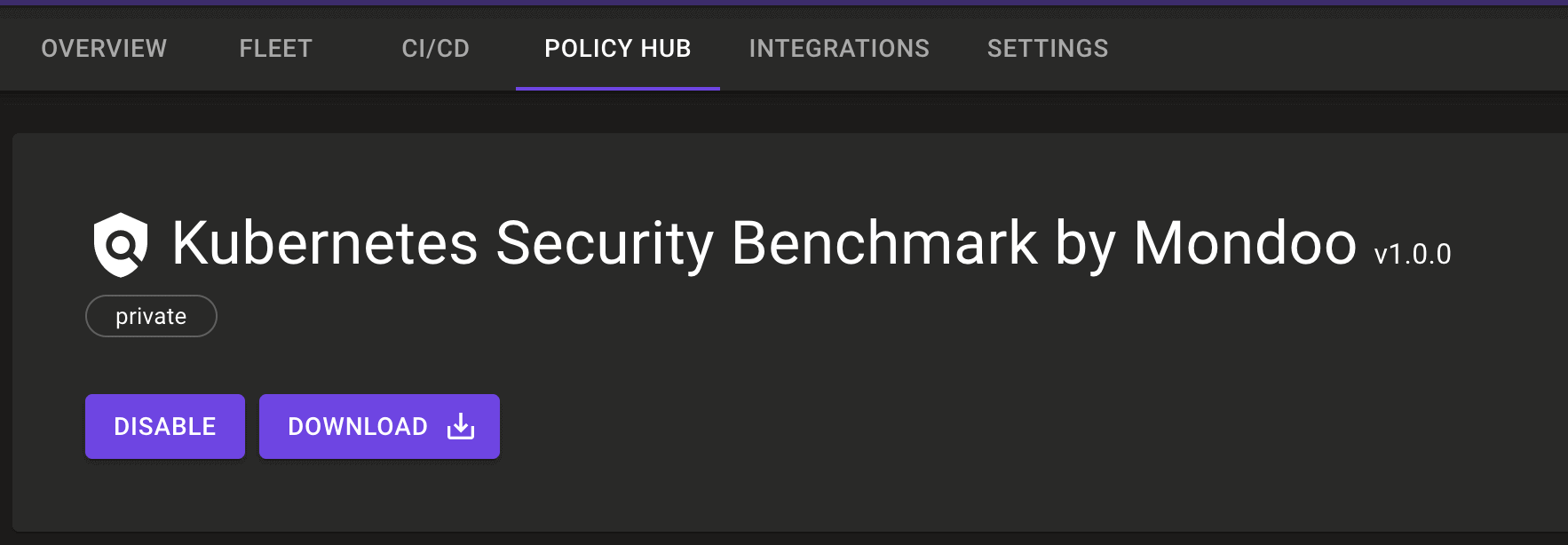
Policy Downloads
Problem: You want to download policies from the Mondoo Policy Hub to customize the policies for your own organization
Solution: You can now download policies from the Policy Hub's policy pages.
Terraform State File Resource Preview
Problem: Instead of scanning the security of various Terraform configuration files, you'd rather go straight to the source and inspect the Terraform state file.
Solution: Mondoo now includes new preview resources for scanning the security of Terraform state files.
These new resources can be used as part of your Terraform development and deployment cycle:
Shellterraform initterraform applyterraform show -json > state.jsonmondoo shell -t tfstate --path state_file.json
MQLmondoo> tfstate { * }tfstate: {terraformVersion: "1.2.6"rootModule: tfstate.module id = tfmodulemodules: [0: tfstate.module id = tfmodule]formatVersion: "1.0"outputs: []}# root modulemondoo> tfstate.rootModule { * }tfstate.rootModule: {address: ""childModules: []resources: [0: tfstate.resource id = aws_instance.app_server]}# recursive list of modulesmondoo> tfstate.modules { * }tfstate.modules: [0: {address: ""resources: [0: tfstate.resource id = aws_instance.app_server]childModules: []}]
🧹 IMPROVEMENTS
Updated CIS Policies
We've been hard at work to get you the latest and greatest CIS benchmarks to secure your systems. This week we've updated the following policies to the latest releases with new and updated controls:
- AlmaLinux OS 8 Benchmark - Level 1 and Level 2 updated to 2.0
- Apple macOS 10.15 Catalina Benchmark - Level 1 and Level 2 to 2.1.0
- Apple macOS 11.0 Big Sur Benchmark - Level 1 and Level 2 to 2.1.0
- Apple macOS 12.0 Monterey Benchmark - Level 1 and Level 2 to 1.1.0
- Amazon Elastic Kubernetes Service (EKS) Benchmark - Level 1 and Level 2 to 1.1.0
AWS Best Practices Policies
We've massively revamped our AWS Best Practices policies with over 8000 lines of improved queries, expanded descriptions, and remediation steps that include Terraform code to correct AWS misconfigurations.
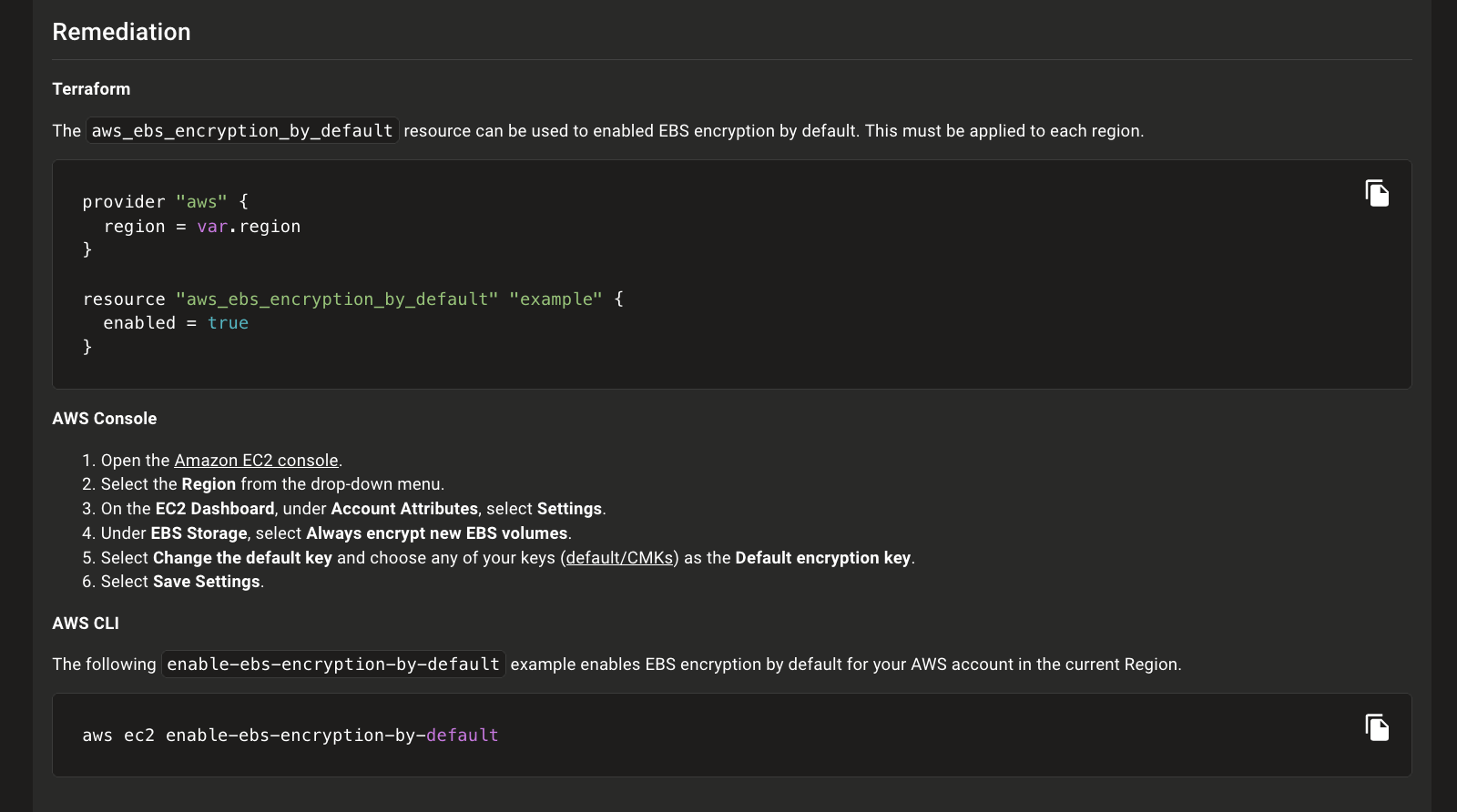
Elevate Privileges with --sudo flag in Local Mondoo Scans
You can now use the --sudo flag with mondoo scan local. This gives you a consistent way to execute scans with elevated privileges, regardless of the type of Mondoo scan you run.
Improved Platform Information
The Mondoo Fleet view now includes more detailed information on each asset's platform and where that asset is running. This information helps you trace assets scanned in Kubernetes/cloud integrations to the infrastructure code that is responsible for their creation. We've also broken out each Kubernetes resource so you can more easily distinguish between Deployments and the resulting ReplicaSets or Pods they spawn. This new information makes it easier to tell running containers apart from container images or server instances.
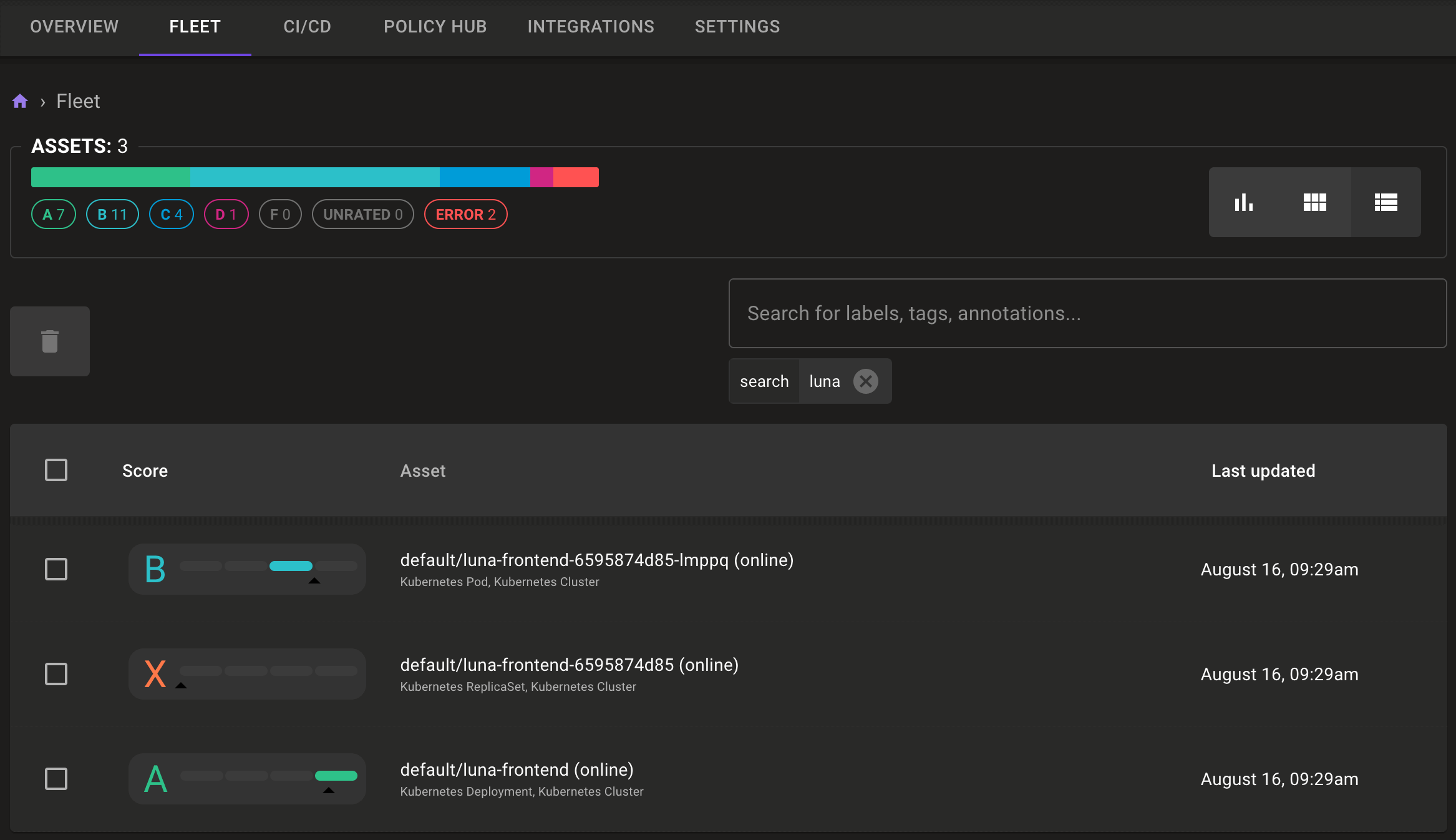
Kubernetes Clusters Now Match Integration Name
The Kubernetes clusters listed in the Mondoo CI/CD view now match the name configured in the Kubernetes Integration, making it easier to find your cluster when multiple integrations have been set up.
Add podSpec and containers to Kubernetes Resources
All Mondoo Kubernetes workloads resources now include podSpec, initContainers, and containers values, allowing you to better secure these resources.
MQLmondoo> k8s.deployment(name: 'luna-frontend' namespace:'default').podSpec{}k8s.deployment.podSpec: {containers: [0: {image: "nginx:1.14.2"name: "nginx"ports: [0: {containerPort: 80.000000}]resources: {}}]}
Simpler Kubernetes Manifest Scanning
You can now scan Kubernetes manifests files without the need to specify the --path flag:
Shellmondoo scan k8s my_deployment.yml
Scanning of Single Terraform Files
You can now scan just a single Terraform configuration file instead of a whole directory of files:
Shellmondoo scan terraform my_tf_deploy.tf
🐛 BUG FIXES AND UPDATES
- Resolves incorrect CRI-O and containerd socket check titles in the Kubernetes Security policy.
- Updates remediation steps for some auditd checks in the Linux Baseline to work with Debian/Ubuntu systems.
- Resolves errors querying Kubernetes rolebindings or clusterrolebindings.
- Mondoo Kubernetes Security and Kubernetes Best Practices policies now appear as recommended policies when setting up a Kubernetes integration.
- Resolves page rendering problems in the
...menu on the AWS Integrations page. - Resolves buttons rendering too close together on Policy Hub pages.
- Resolves failures in some
if/elseblocks in MQL queries. - Resolves failures delivering some Mondoo invites.
- Properly detects busybox when in containers.