Mondoo 6.10 is out!
🥳 Mondoo 6.10 is out! This release includes Kubernetes resource scanning and expanded OS support.
Get this release: Installation Docs | Package Downloads | Docker Container
🎉 NEW FEATURES
Kubernetes Resource Scanning
Problem: You want to secure not just your Kubernetes cluster control plane and nodes, but also the workloads you deploy to your cluster. You need visibility into the security of each of the running workloads.
Solution: Mondoo now scans each workload type as a dedicated asset, with new security and best practice policies applied to each asset. This means you'll now get not only scans of your cluster nodes and overall cluster control plane configuration, but also Pods, CronJobs, StatefulSets, DaemonSets, Jobs, and Deployments. These new assets provide more granular visibility into the workloads deployed onto your clusters and make it easy to disable or skip controls on particular workloads.
Results of Pod Scans:
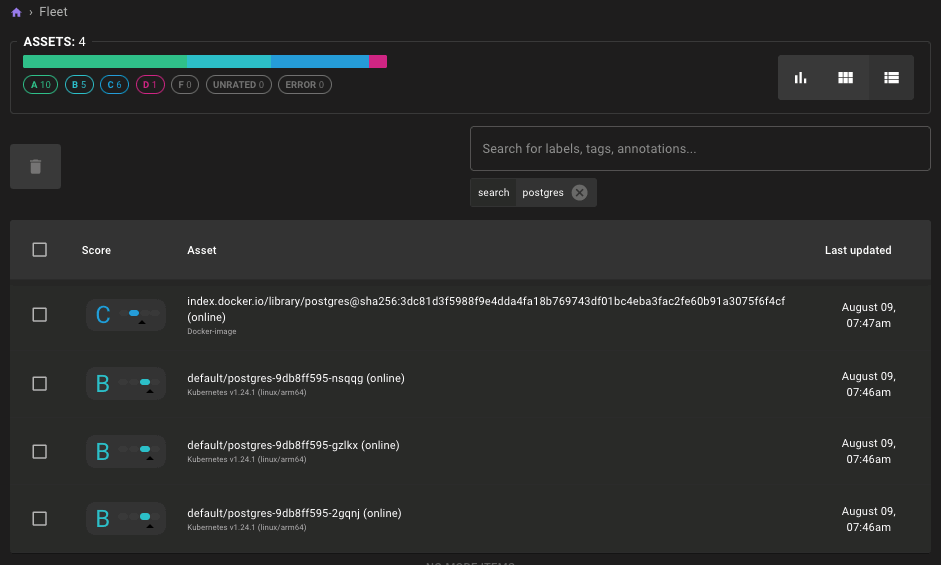
In addition to these new assets we're also shipping new Kubernetes Security and Kubernetes Best Practice policies. These new policies replace the existing Kubernetes Application Benchmark policy and apply only to the new Kubernetes resource assets. We decided to break out our combined security and best practices policy so that it would be easier to determine security vs. best practice violations at a glance. Since these policies scan individual Kubernetes assets instead of the cluster as a whole, they also feature greatly improved scan output and new remediation steps, so you can more easily resolve findings.
Pod Asset with New Policies:
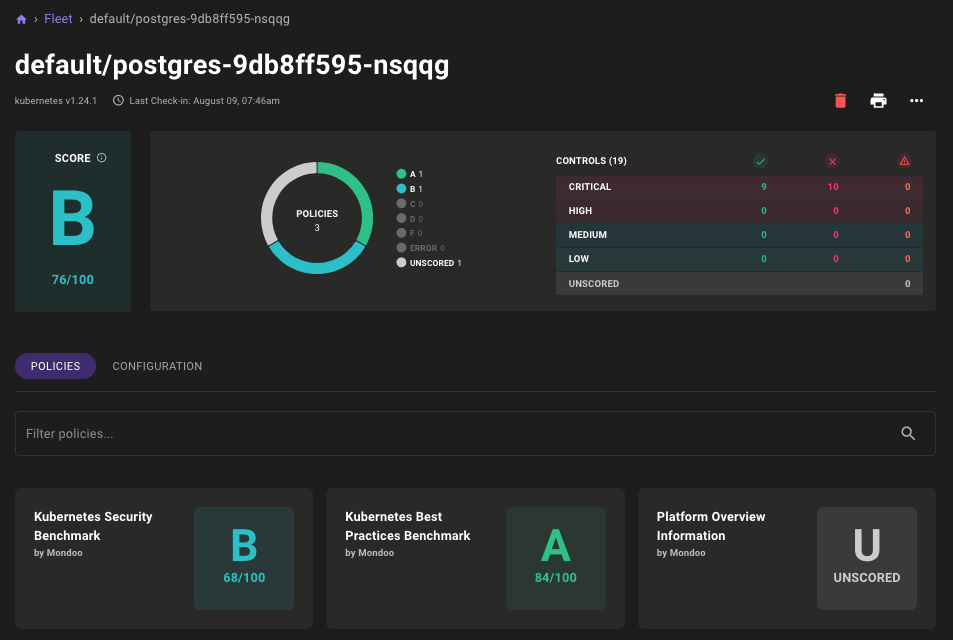
Improved Kubernetes Policy Controls:
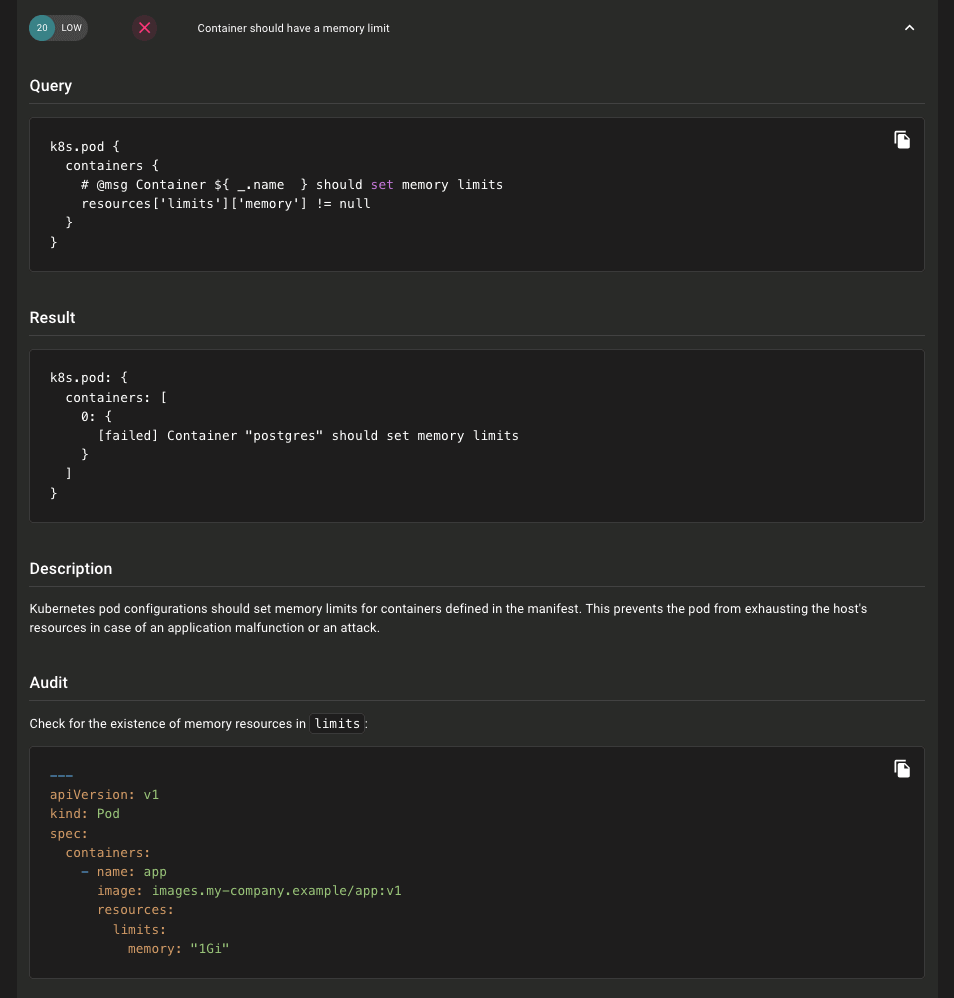
To enable scanning of all Kubernetes resources as individual Mondoo assets, pass the --discover all flag when scanning clusters:
mondoo scan k8s --discover all
Stay tuned for resource scanning directly in the Mondoo Kubernetes Operator and even more improvements to out-of-the-box Kubernetes policies in the coming weeks!
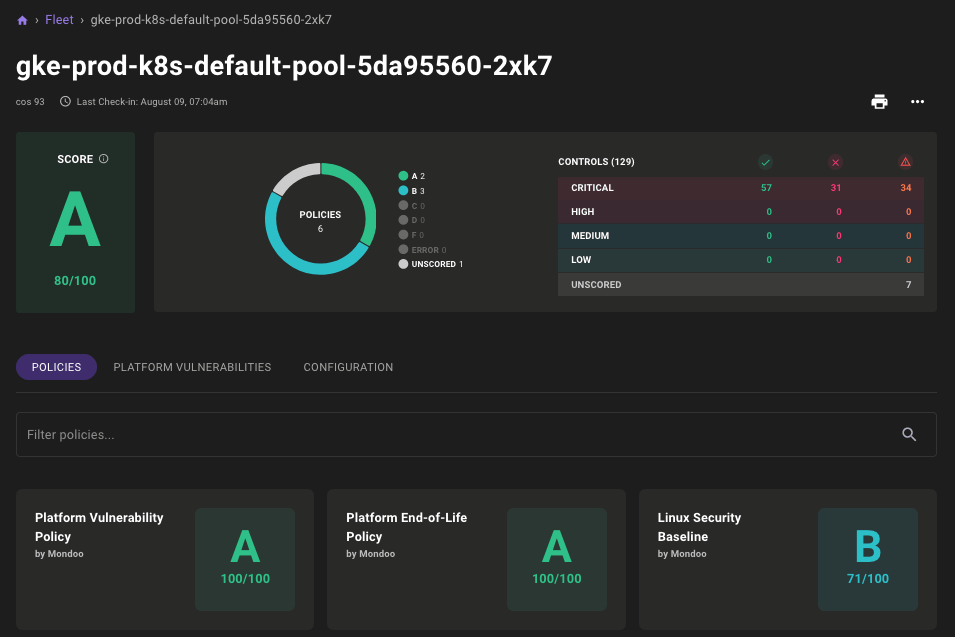
Google Container Operating System Support Preview
Problem: When scanning Google Kubernetes Engine (GKE) clusters, you want to ensure the security of the cluster nodes running the Google Container OS Linux distribution.
Solution: Mondoo now includes preview support for the Google Container Operating System (GCOS). With this release, you will now see GCOS hosts properly report their release version, EOL date, and package/service states. Stay tuned for improved detection and policy support in the coming weeks.
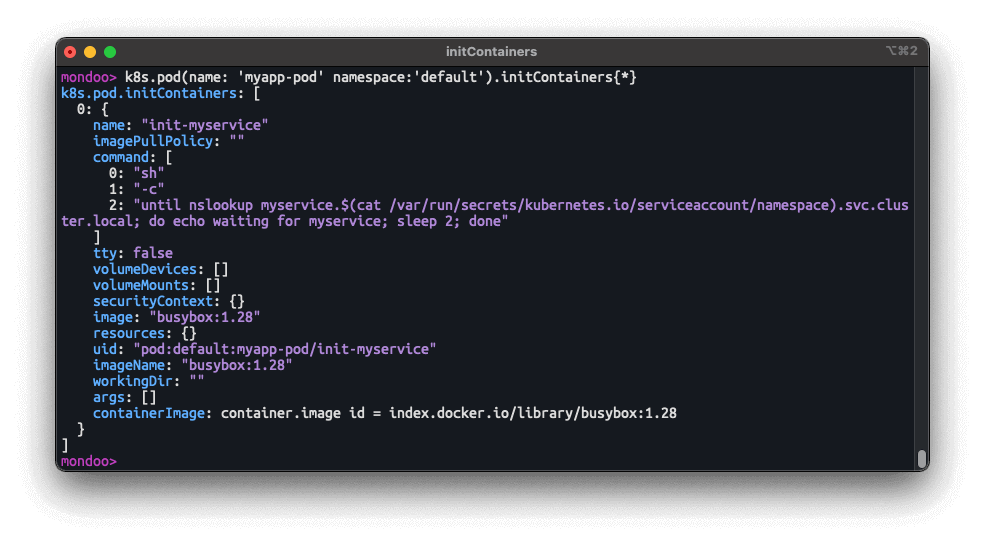
Kubernetes k8s.initContainer Resource
Problem: You want to write Mondoo policies that examine the configuration of Kubernetes Init Containers in your workloads.
Solution: A new k8s.initContainer allows you to write policy against Kubernetes Init Containers.
🧹 IMPROVEMENTS
Expanded Operating System Support
We've updated Mondoo with enhanced platform end-of-life and package vulnerability data so you can scan the latest and greatest operating systems:
- Added Alpine 3.16, Fedora 33/34/35, and VMware Photon 4 package vulnerability data.
- Updated Amazon Linux 2022 vulnerability data for the latest preview release packages.
- Added EOL date detection for openSUSE Tumbleweed and Clear Linux OS.
- Updated EOL date detection for the new patch version format of VMware 7.x.x.
Linux Baseline Policy Improvements
We continue to improve our out-of-the-box Linux Baseline policy to provide better remediation steps and to support different Linux distros.
- Skips the
Ensure permissions on /etc/shadow- are configuredcontrol instead of failing when/etc/shadow-doesn't exist on the system. - Updates the query in the
Ensure Samba is stopped and not enabledcontrol to support Debian/Ubuntu-based Linux distros. - Updates the query and remediation steps for the
Ensure core dumps are restrictedcontrol to support more distros. - Updates the query in the
Ensure login and logout events are collectedcontrol to support Ubuntu. - Improves remediation steps and formatting throughout the policy.
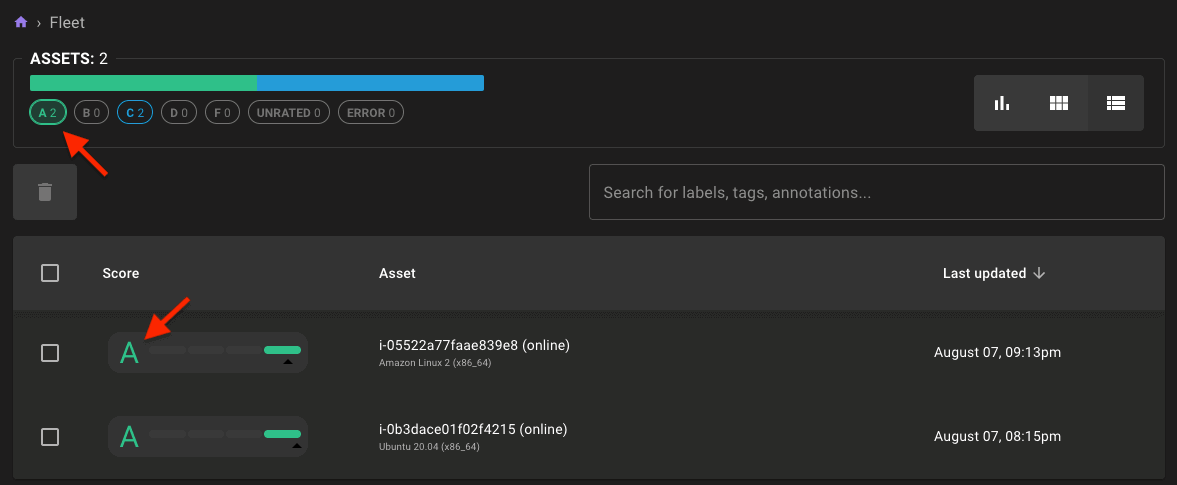
Filtering in Asset Lists
You can now quickly filter assets by their score by selecting the A-F values at the top of the fleet page.
🐛 BUG FIXES AND UPDATES
- Resolves failures running scans in the Kubernetes Operator.
- VMware Mondoo appliance now includes timesyncd to prevent platform registration failures due to time drift.
- Resolves duplicate AWS resource counts in the AWS integration pages.
- Resolves potential failures in Mondoo Client when reporting scan results.
- Reports all Mondoo Client scans within GitHub Actions when running the Mondoo action in multiple jobs or steps within the same workflow.
- Resolves incorrect steps in the VMware Integration page.
- Resolves failures in MQL when using if/else statements that have single-valued blocks.
- Resolves the fleet summary pages sometimes showing an incorrect summary breakdown of asset scores.