Mondoo 6.0 is out!
🥳 Mondoo 6.0 is out.
Get this release: Installation Docs | Package Downloads | Docker Container
We have just hit a major milestone - Mondoo's 6.0 release! This version includes many changes we're eager to share with you:
Most of these changes have been available hidden behind feature flags and CLI options for a while now. This release changes the default experience to make them available to everyone.
Is it difficult to upgrade?
Not at all! We have kept most things backwards-compatible with v5. In most cases you should only see a few deprecation warnings asking you to use new CLI options. The few breaking changes are outlined below.
Breaking changes
mondoo scannow uses the exit code 0 whenever the scan is successfully executed. Previously we used non-zero exit codes when a scan didn't achieve a perfect score. This change makes it easier to use Mondoo in a CI/CD. See [the section on exit codes] below.mondoo scanwithout additional arguments no longer automatically scans your local system. We changed this to prevent you from accidentally scanning your local OS. Runmondoo scan localto scan your local system. Check out our new [scan providers] for more targets below.- The default CLI reporter has changed to
compactmode, which doesn't rely on pagination and prints a much shorter summary. See [CLI reports] for more information. - When you run
mondoo scanwith a--policy-bundle, the option--incognitois now used by default instead of printing an error and aborting.
Deprecations
All deprecations will be supported throughout the lifetime of Mondoo v6. We will remove them when we release Mondoo v7.
- The
-tand--connectionoptions formondoo scan,mondoo execandmondoo shellhave been deprecated. Please use [scan providers] instead. - The
--exit-0-on-successoption has been deprecated and is the new default. Feel free to remove it. See [the section on exit codes].
🎉 NEW FEATURES
CLI scan providers
Problem: Mondoo can scan many different targets, from your local machine, to remote machines via SSH or WinRM, to cloud systems like AWS or Azure, and even arbitrary APIs. These are specified via the --connection or -t option in the CLI. Unfortunately, it was difficult to use this option effectively, partly due to the wide range of targets and parameters that were supported.
Solution: We are providing a new way to target assets with this release. The scan command has changed from:
mondoo scan -t <schema>://<options>
mondoo scan --connection <schema>://<options>
to
mondoo scan <provider>
To access a list of all available providers, type:
mondoo scan -h
Usage:
mondoo scan [flags]
mondoo scan [command]
Available commands:
arista Scan an Arista endpoint
aws Scan an AWS account or instance
azure Scan a Microsoft Azure account or instance
container Scan a container, an image, or a registry
docker Scan a Docker container or image
gcp Scan a Google Cloud Platform (GCP) account
github Scan a GitHub organization
gitlab Scan a GitLab group
host Scan a host endpoint
k8s Scan a Kubernetes cluster
local Scan a local target
mock Scan a mock target (a simulated asset)
ms365 Scan a Microsoft 365 endpoint
ssh Scan a SSH target
terraform Scan all Terraform files in a path (.tf files)
vagrant Scan a Vagrant host
vsphere Scan a VMware vSphere API endpoint
winrm Scan a WinRM target
You can find more information on every provider with the -h or --help option. For example:
mondoo scan container -h
Here are a few more examples of mondoo scan with different providers:
mondoo scan local
mondoo scan ssh user@host
mondoo scan container b62b
mondoo scan container image ubuntu:20.04
mondoo scan aws
CLI reports overhaul
Problem: The default CLI reports used a lot of screen space to convey their findings. They also printed from top to bottom, with a summary and a lot of information below, which forced us to default to pagination for these reports to avoid scrolling. These reports are helpful for security audits, but they didn't help most other CLI users.
Solution: We have designed a new report whose primary audience is developers and operations experts. This means that we now print a list of controls and data queries first, then list vulnerabilities, and then finish with a short summary. We deactivated the pagination. The default report is also much more compact:
mondoo scan local
# OR
mondoo scan local -o compact
To get more information about individual controls, use the full formatter:
mondoo scan local -o full
Here is an example of compact (left) versus full (right) output side-by-side for the scan scan:
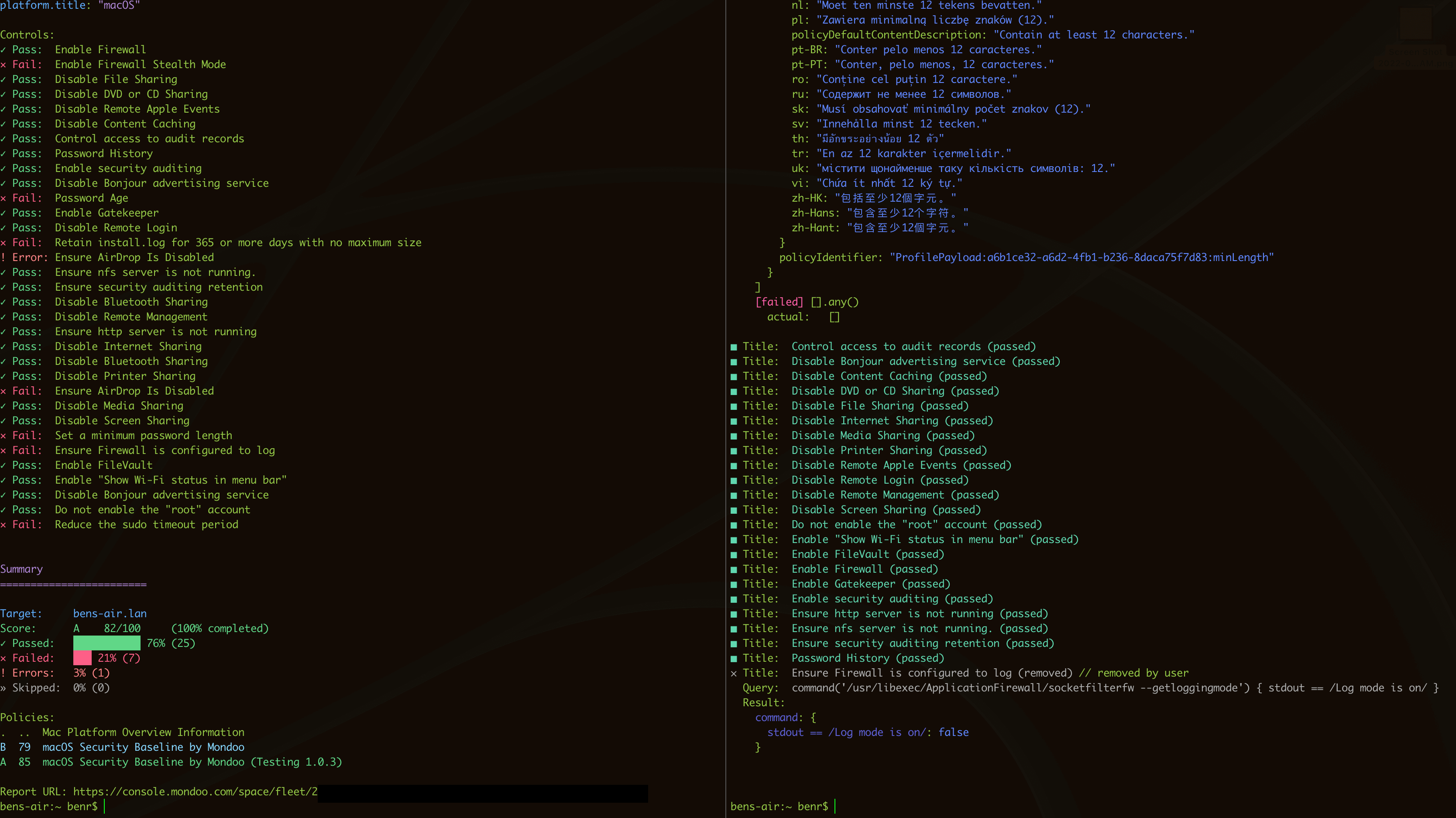
You can access the auditor- and security-centric report via -o report. This was the default output before v6.
You can list all output formats:
mondoo scan -o help
Available output formats: junit, compact, full, report, json, csv, yaml
Exit codes and score thresholds
Problem: Whenever Mondoo scans ran in CI/CD pipes, unless they had perfect scores (an A+ with a score of 100), they finished with a non-zero exit code. This caused the pipeline to fail, even with only minor issues.
We had previously introduced the --exit-0-on-success option to address this use case. It changed the behavior to always finish with an exit code of 0 whenever the scan was successful—even if it produced an F.
While this helped remedy the original problem with failing pipeline runs, it didn't help users who wanted to fail their tests if certain conditions were met. This was technically possible, by knowing all the available exit codes mondoo scan generated, but was impractical and hard to use.
Solution: Mondoo scans now always return an exit code of 0 by default when a scan is successful. Both As and Fs show a successful run.
With the previously introduced --score-threshold you can change this behavior to fail the execution (exit code 1) whenever the score falls too low. For example, this command fails all scans that result in an F (if their score is below 10):
mondoo scan … --score-threshold 10
AWS Organization integration
We are excited to release the AWS Organization integration, which allows you to set up AWS integrations across your entire AWS Organization or organizational unit.
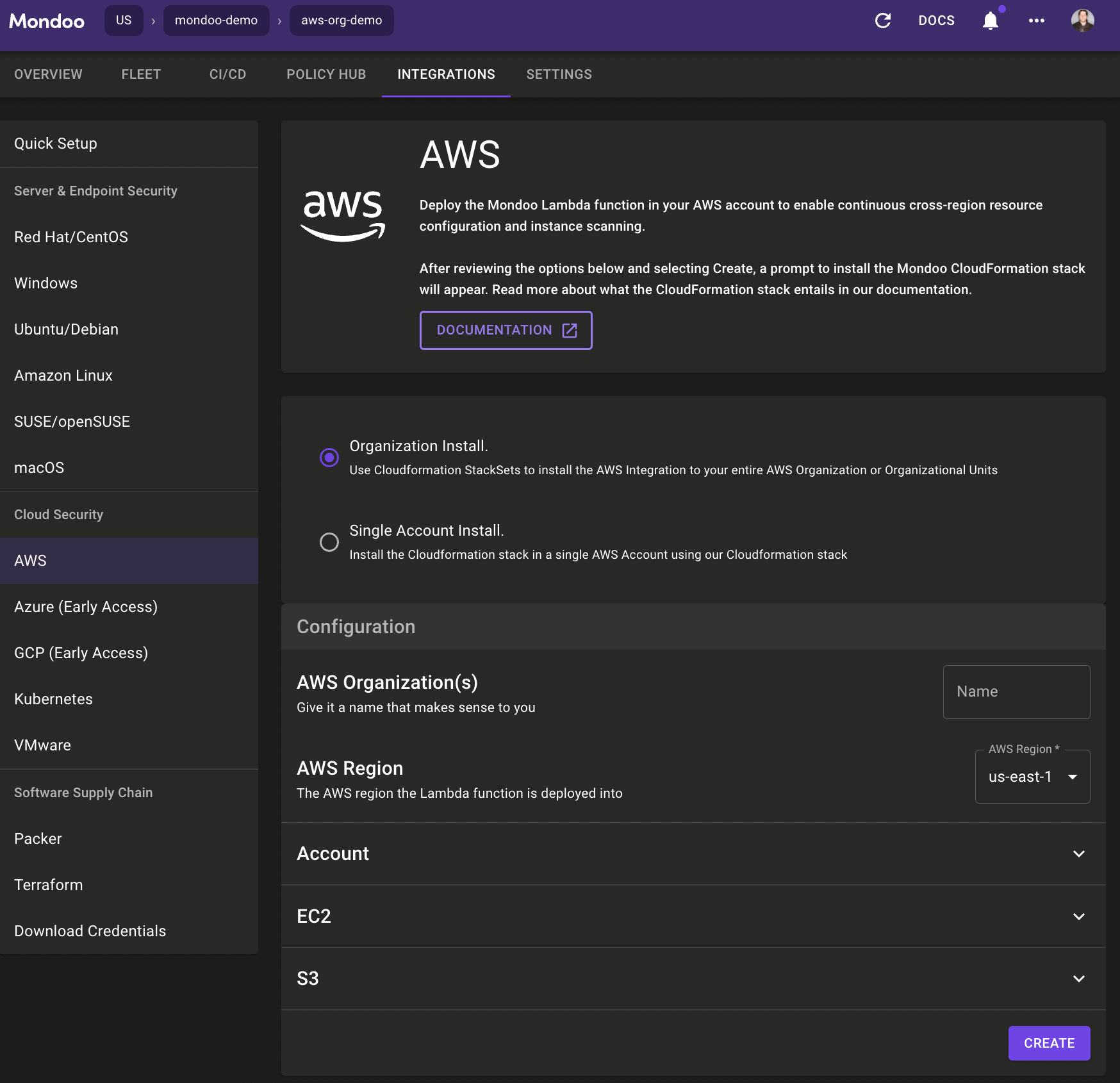
We previously only supported single account installs. With this change, you can use AWS CloudFormation StackSets to install the integration across all accounts in your AWS Organization and automatically have the integration be installed to all new accounts added to that AWS Organization.
🧹 IMPROVEMENTS
MQL improvements
Problem: It was impossible to use variables across blocks in MQL, which made a lot of queries more difficult to write. We have wanted to fix this issue for a while, which required a major change in MQL's execution engine.
Solution: Variables can now be used across blocks like you would in many other programming languages. Here is a simple example:
aws.dynamodb.tables {
x = region
aws.dynamodb.
limits.
where(region == x) { * }
}
In this example, we define a new variable x and set its value to the region of the table. We can then use the variable to access the limits entry that matches this region. Previously this was not possible, since both fields had the same name (region) and variables weren't accessible across blocks.
CI/CD detection
We now automatically detect the client running in CI/CD environments. Once detected, we collect more contextual information about the run, like the repository, PR/MR number, and git reference. This allows CI/CD runs to automatically show up in the CI/CD tab in the UI, where you can explore more details.
Today, we support this feature for GitHub, GitLab, and Kubernetes out of the box. We are expanding to other systems soon, so stay tuned!
🐛 BUGFIXES
- update Kubernetes doc links in the UI
- fix colors for the score display
- fix EBS volume scanning targeting incorrect instances in some cases
- fix "see your asset scores" (on aws integrations) button navigation
- ensure asset labels link out to AWS when appropriate
- ensure project jobs load more button loads more items
- added error msg for when a user tries to cancel an invitation that is not their own
- correct breadcrumb on CI/CD page
- default Kubernetes integrations admission controller to off
