Mondoo 5.17.1 is out!
🥳 mondoo 5.17.1 is out!
🎉 NEW FEATURES
Terraform Policy
- Added
Terraform Static Analysis Policy for AWS (Early Access)

Network targets
We first released the tls resource back in 5.12.2,
and the dns resource in 5.13.0.
This was 1 month ago and today we are taking the next step at making them applicable
by adding new ways to target assets.
First, we added the host:// target:
Bashmondoo shell -t host://mondoo.com
Once connected, you can run queries like this:
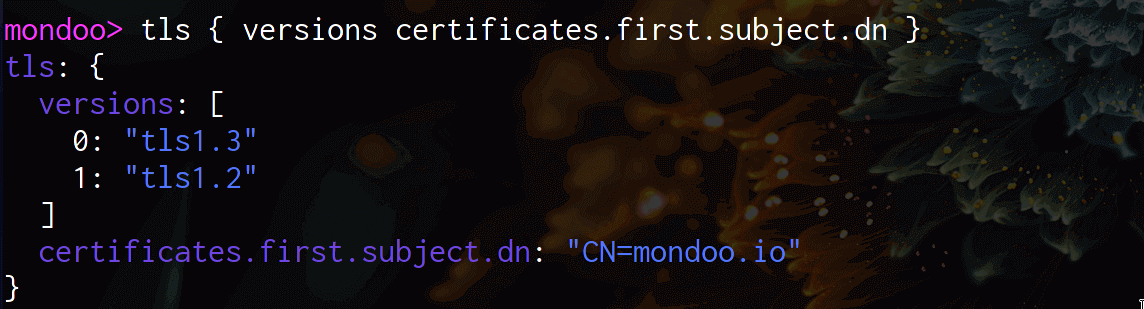
Additionally, we expose this information via the platform resource:
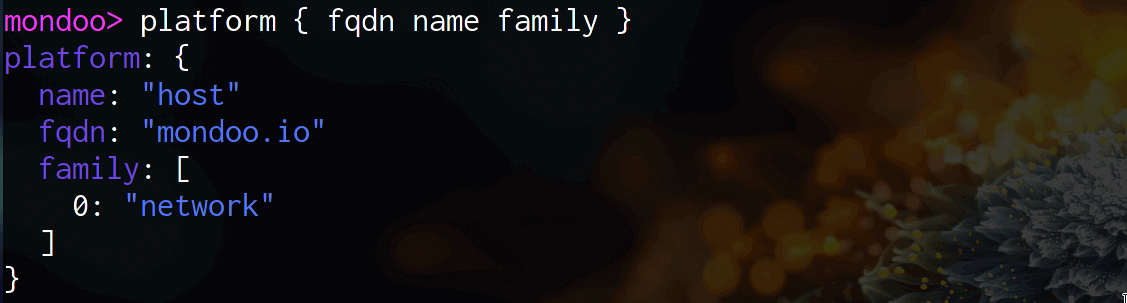
Alternatively you can also use the tls:// target for this use-case as well, and we
are planning to expand these to provide contextual information to the MQL engine.
DNS policy
We added a baseline policy to check your DNS security called: Mondoo DNS Baseline (Early Access).
As you can see, it's still in early access and we'd love to hear what else you
might want to see!
To scan mondoo.com for DNS, run the following:
Bashmondoo scan -t host://mondoo.com --incognito --policy '//policy.api.mondoo.app/policies/mondoo-dns-baseline'
TLS policy
We also added a policy for TLS security called: Mondoo TLS/SSL Baseline.
This policy will be expanded over the course of time with more tests. Check out
our community channel and let us know if you want to test more features!
To scan mondoo.com for TLS, run the following
Bashmondoo scan -t host://mondoo.com --incognito --policy '//policy.api.mondoo.app/policies/mondoo-tls-baseline'
Scanning multiple Hosts
To scan multiple hosts, create a new domainlist.txt file that includes domains separated by newlines:
mondoo.com
google.com
Then you can pipe that domain inventory to mondoo:
cat domainlist.txt | mondoo scan --domainlist-inventory
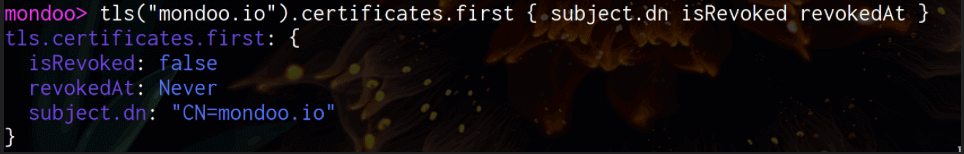
Certificate resource
You can now check if a certificate has been revoked. This is done via OCSP requests
to see if that certificate has been revoked. In all cases where OCSP information
has not been provided, the value for this field will be null.
When a certificate is revoked, you can additionally access the revocation time
via the field revokedAt.
Note: This feature is currently limited to TLS checks. Please ping us in our community channel if you need it for standalone certificates as well!
TLS extensions
Additionally, we added tests for a few TLS extensions. Amongst others, we now support 3 extensions:
server_nameWhether the server supports Server Name Indication (SNI). You can access all SNI certificates via thecertificatesfield and non-SNI certificates vianonSniCertificatesfake_server_nameWhen a fake SNI name is sent to the server, this indicates that we get a response without any alerts from the server. This means that the server doesn't leak information about the name.renegotiation_infoShows that the server supports secure TLS renegotiations (via TLS 1.2 and 1.3)

🧹 IMPROVEMENTS
- Map fields via the
#map( .. )function to flatten list. For example:users.map(name)to get a flat list of user names. - Include tags on more AWS resources for discoverability
- Allow machineid as a platform identifier
- More AWS resource MQL documentation
🐛 BUG FIXES AND UPDATES
- Use numbers for the
entry.shadowresource (was string) - Properly detect AWS arm instances
- Ensure asset state and asset name are always updated
- Only update platform name when valid
- Fix ec2-managedinstance-association-compliance-status-check query
- Ensure incognito runs do not try to report to Mondoo Platform
- Resolve refs in arrays
- Fix recursive operator with arrays and maps
- Array to nil comparison
- Fix url parsing on domain list inventory
- Fix displayed errors for missing upstream policies