Mondoo 11.4 is out!
🥳 Mondoo 11.4 is out! This release includes loads of new CIS benchmark policies, new AWS resources, and more!
Get this release: Installation Docs | Package Downloads | Docker Container
🎉 NEW FEATURES
New CIS Debian 12 benchmark policies
Secure Debian 12 systems with new CIS Debian Linux 12 Benchmark Levels 1 & 2 policies. These policies include 284 checks specifically tuned for this latest release of Debian.
Expanded AWS network inspection capabilities
New AWS resources provide detailed insights into your AWS network infrastructure.
| Use this resource... | To gather information on... |
|---|---|
| aws.ec2.eip | Elastic IPs, including attachment status and the individual IPs of instances to which they're attached |
| aws.vpc.natgateway | VPC NAT gateways, including the IP addresses and VPCs associated with them |
| aws.vpc.peeringConnection | VPC peering connections, to understand how VPCs in different AWS accounts relate |
| aws.vpc.serviceEndpoint | VPC service endpoints, to better understand connectivity to AWS PrivateLink |
🧹 IMPROVEMENTS
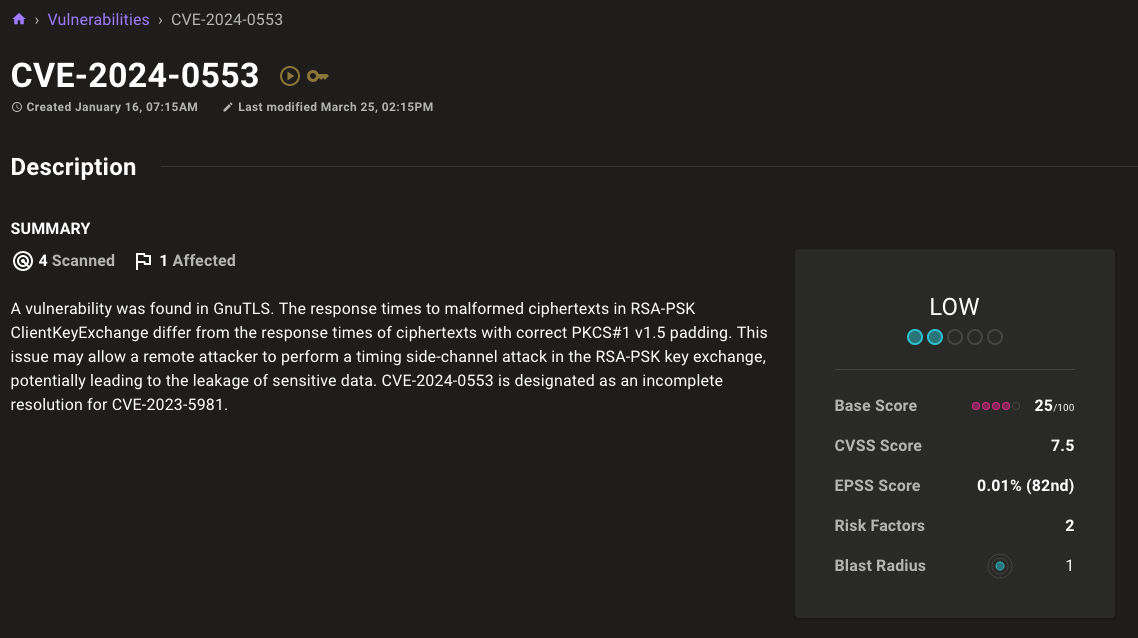
Improved risk score display for CVEs
Understand the true risk of CVEs at a glance with a new risk score box on CVE pages. The risk score box includes the overall risk of the CVE as well as the CVSS score, EPSS score, risk factors, and blast radius so you can quickly understand whether a CVE needs attention.
Updated Windows and Linux CIS benchmark policies
Scan your infrastructure with the very latest CIS benchmark policies for Linux and Windows. These updated policies include improved descriptions, remediation steps, and new checks to keep your systems secure against the latest threats.
- CIS Benchmark RHEL 7 v4.0.0
- CIS Benchmark CentOS 7 v4.0.0
- CIS Benchmark Oracle Linux 7 v4.0.0
- CIS Benchmark Amazon Linux 2 v3.0.0
- CIS Benchmark Windows 2019 v3.0.0
- CIS Benchmark Windows 2022 v3.0.0
Improved container policy application
From SSH configuration to interactive user permissions, many traditional security checks aren't applicable in a container world. To reduce noise and help you prioritize what matters, CIS benchmarks no longer apply to container workloads. Instead, we've modified our existing Mondoo Linux Security policy to better execute on containers. We highly recommend enabling this policy to scan your containerized workloads.
If you have any suggestions for how we can improve this policy, reach out at hello@mondoo.com.
Fedora AWS instance snapshot scanning
Scan Fedora workloads in AWS without deploying the Mondoo package. New snapshot scanning support for Fedora instances makes this possible.
Improved control of SSH policy application
Tune Mondoo's SSH security checks to meet your particular business needs with new reworked SSH checks that include properties. With properties, you can set your allowed SSH key exchange algorithms, ciphers, and message authentication codes (MACs) without the need to write your own checks.
Validate user account domains in internal Slack channels
Our new Ensure domain is enforced on internal channels check lets you make sure all users in your internal channels signed up to Slack using an approved email domain. This check includes a property so you can add one or more allowed domains to ensure that all employees use work email accounts.
Proxy support for Kubernetes container scans
Running an air-gapped Kubernetes cluster? Don't worry; we've got you covered with new support for scanning workload container images using a proxy server. Update to the 11.2 release of the Mondoo Kubernetes Operator and set your proxy URL in the new ContainerProxy configuration option.
Resource improvements
aws.dynamodb.export
- New resource for Amazon DynamoDB exports to S3
aws.ssm.parameter
- New resource for parameters in the AWS Systems Manager Parameter Store
docker.file
- New
userfield
🐛 BUG FIXES AND UPDATES
- Improve the application of chrony and timesyncd checks in CIS Linux benchmarks.
- Improve handling of API token creation.
- Add a helpful message for users when a space has no prioritization data due to older Mondoo scans.
- Don't show the risk factors heading on the Affected Assets page if there are no risk factors.
- Add break-out links for top CVEs and security misconfigurations on space dashboards.
- Improve formatting of downloaded compliance frameworks.
- Improve reliability of checks in the CIS Azure Foundations benchmark policies.
- Fix a failure fetching the
docker.file.fileresource field. - Fix querying subnetworks for a network on GCP.
- Improve rendering of the ellipsis menu in AWS integration pages.
- Fix navigation bar links to Slack scanning integrations failing to load.
- Add new asset overview information for Azure assets when scanning with
--discover all. - Fix failures scanning Dockerfiles not in the current directory.
- Fix scans of some Windows assets not showing results.
- Update the exceptions count on assets to not include rejected exceptions.