Mondoo 11.35 is out!
🥳 Mondoo 11.35 is out! This release includes Microsoft Defender for Cloud findings in Mondoo, Nmap scanning, performance improvements, and more!
Get this release: Installation Docs | Package Downloads | Docker Container
🎉 NEW FEATURES
Microsoft Defender for Cloud findings in Mondoo
Mondoo now imports vulnerabilities discovered by Microsoft Defender for Cloud, so you can prioritize them alongside vulnerabilities discovered by Mondoo. Mondoo helps security teams quickly make sense of security findings regardless of where those findings originate, prioritize the most critical risks, and easily assign them to IT and DevOps with detailed remediation steps. This means that Mondoo significantly speeds up time to resolution and bolsters overall security posture.
Vulnerabilities discovered by Microsoft Defender for Cloud appear in the Mondoo console alongside those discovered by Mondoo's own scans. Mondoo automatically enriches all vulnerabilities found by Microsoft Defender with additional risk data and remediation advice, and prioritizes them based on the actual risk posed in the environment.
Mondoo enriches the findings generated by Microsoft Defender for Cloud with severity, known exploit data, exploit prediction scoring, asset exposure, and business impact, to make sure your security teams are focused on resolving the most important problems.
Network security with Nmap scanning
Nmap, short for Network Mapper, is a powerful and versatile open source tool used for network discovery and security auditing. Network administrators, security professionals, and penetration testers rely on Nmap to map out network structures, discover hosts, identify services, and detect vulnerabilities. Now you can integrate Nmap results with Mondoo findings using our new cnquery/cnspec Nmap provider.
Scan active IP addresses in a network:
MQLnmap.network("192.168.178.0/24").hosts { name ports { * } }nmap.network.hosts: [0: {ports: [0: {service: "http"version: ""method: "probed"state: "open"protocol: "tcp"port: 443product: "FRITZ!Box http config"}1: {service: "sip"version: ""method: "probed"state: "open"protocol: "tcp"port: 5060product: "AVM FRITZ!OS SIP"}]name: "192.168.178.1"}1: {ports: [0: {service: "rtsp"version: "770.8.1"method: "probed"state: "open"protocol: "tcp"port: 5000product: "AirTunes rtspd"}1: {service: "rtsp"version: "770.8.1"method: "probed"state: "open"protocol: "tcp"port: 7000product: "AirTunes rtspd"}]name: "192.168.178.25"}]
Scan a specific host IP:
MQLnmap.network(target: "192.168.178.25").hosts { ports }nmap.network.hosts: [0: {ports: [0: nmap.port port=5000 service="rtsp"1: nmap.port port=7000 service="rtsp"]}]
🧹 IMPROVEMENTS
Performance improvements
No one wants to wait, so we made Mondoo faster than ever.
- 4x faster compliance report generation
- 7x faster asset discovery during large scans
- 20x faster GitHub repository discovery in large organizations
- Reduced GitHub API call usage during organization scans
New checks in Mondoo DNS Security
The Mondoo DNS Security policy now includes full descriptions and impact scores for each check. There are also new checks to ensure DNSSEC is enabled and no DNS wildcard entries exist.
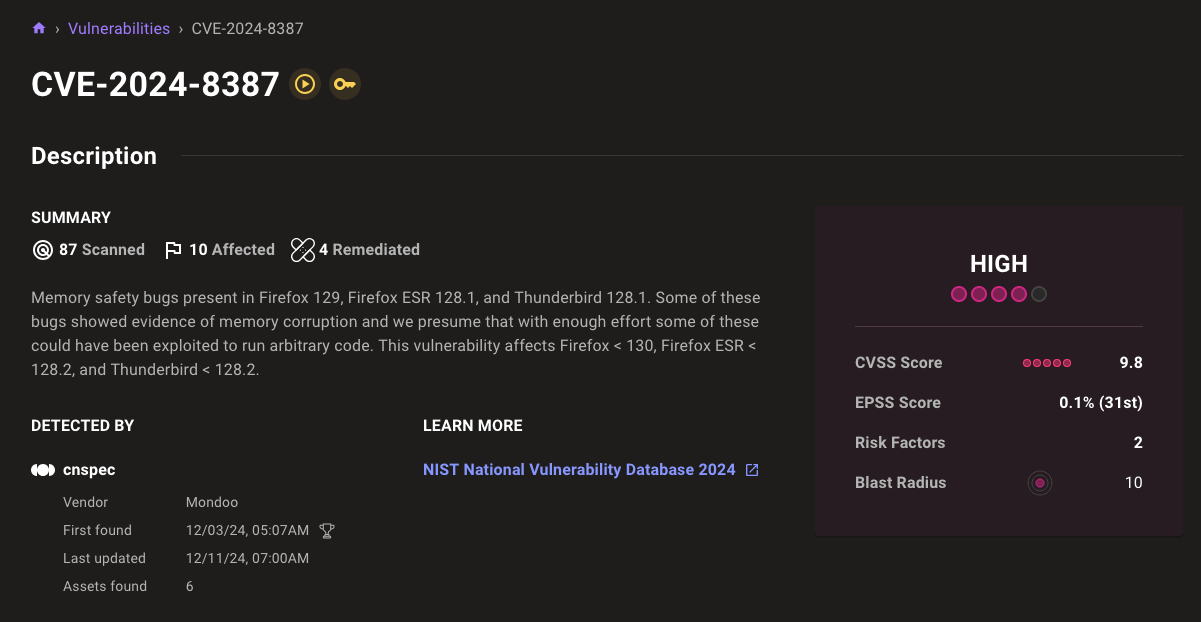
Display remediated asset count on CVEs
It's important to observe not just the current state of CVEs, but also the work you've done to resolve them. Remediated counts on CVE and advisory pages provide the full scope of information.
Expanded Terraform Provider Mondoo resources
You can automate more of your Mondoo Platform configuration than ever with new resources in the Terraform Provider Mondoo. Thanks for these great contributions @mati007thm!
- New
mondoo_exceptionresource - New
mondoo_integration_emailresource - New
mondoo_integration_gitlabresource - New
mondoo_integration_jiraresource - New
mondoo_integration_msdefenderresource - New
mondoo_integration_zendeskresource
Resource updates
aws.cloudfront.function
- Deprecate
createdTimein favor of a newcreatedAtfield
aws.dynamodb.table
- Deprecate
createdTimein favor of a newcreatedAtfield
aws.elb.loadbalancer
- Deprecate
createdTimein favor of a newcreatedAtfield
aws.rds.dbcluster
- Deprecate
createdTimein favor of a newcreatedAtfield
aws.rds.dbinstance
- Deprecate
createdTimein favor of a newcreatedAtfield
aws.s3.bucket
- Deprecate
createdTimein favor of a newcreatedAtfield
github.organization
- New
totalPublicReposfield
🐛 BUG FIXES AND UPDATES
- Fix affected assets lists not containing assets scanned by older custom policies.
- Fix failures in the
files.findresource with container image scans. - Improve display of VMware assets in the inventory overview.
- Simplify the asset print view headers.
- Rename "Sources" to "Learn More" on CVEs to better describe the purpose of the links.
- Fix policy check metrics when exceptions are set.
- Fix search for low security CVEs returning zero results in the vulnerability database.
- Update CIS NTLM checks to also accept the "Deny All" setting.
- Adjust scores in Windows policies to improve prioritization.
- Ensure Kubernetes assets always contain asset overview information.