Mondoo 11.2 is out!
🥳 Mondoo 11.2 is out! This release includes a whole new compliance as code experience, new tools to prioritize findings, and more!
Get this release: Installation Docs | Package Downloads | Docker Container
🎉 NEW FEATURES
Compliance as code in Compliance Hub
Every audit is different. Now you can customize the Mondoo Compliance Hub experience to match the exact evidence required by your auditor.
Start by downloading one of our top industry compliance frameworks to your local system directly from Compliance Hub
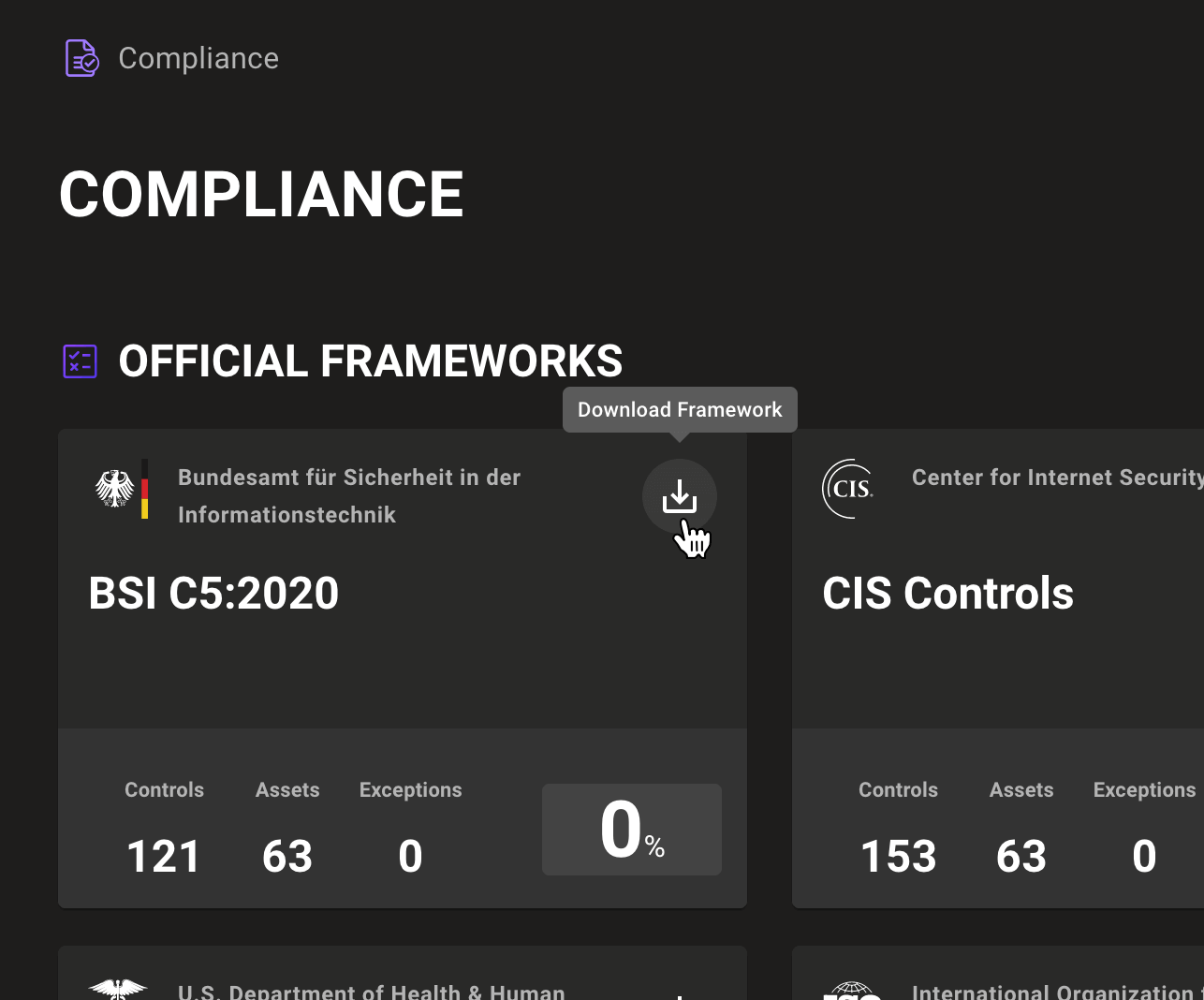
This Compliance as Code framework file is pre-customized for your space with compliance evidence mappings from policies you've enabled and any exceptions you've defined. Want to edit a mapped check or perhaps add a new population control your auditor is asking for? You can customize this file with any additional controls or specific evidence items your auditor has asked for.
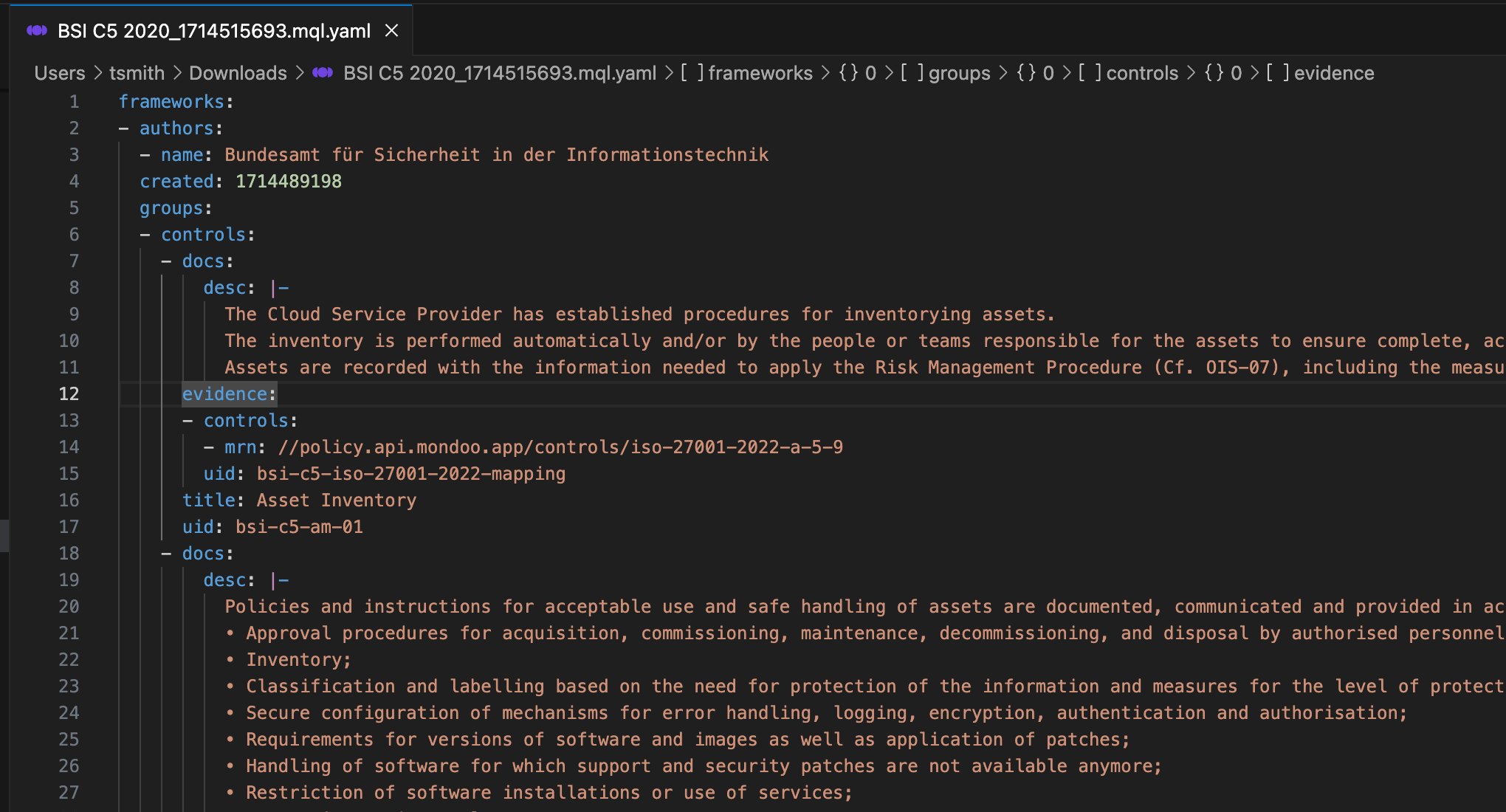
With your compliance framework fully customized for your auditor's requirements, upload it to Compliance Hub and track your progress just as you would using an out-of-the box framework. Need to make a change? Don't worry: You can replace the framework with an updated version at any time or remove it altogether.
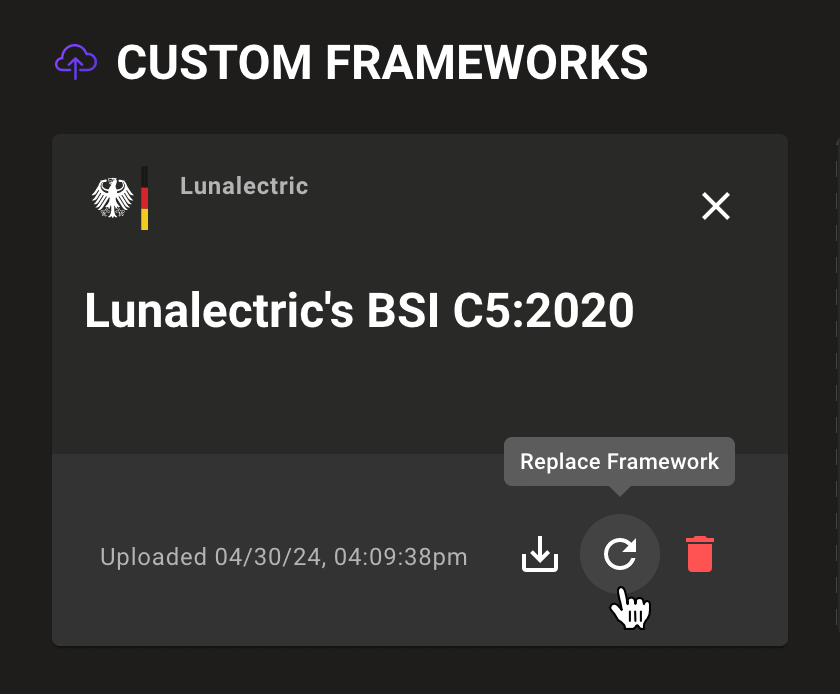
New policy check detail pages
New policy check pages allow you to better understand critical impacts to your business. Score tiles bring risk front and center and include risk factors and blast radius, so you can understand the priority of findings. With refactored query descriptions it's easier to understand why a check is important, how Mondoo evaluates your assets, and what risk factors mean to the safety of your infrastructure.
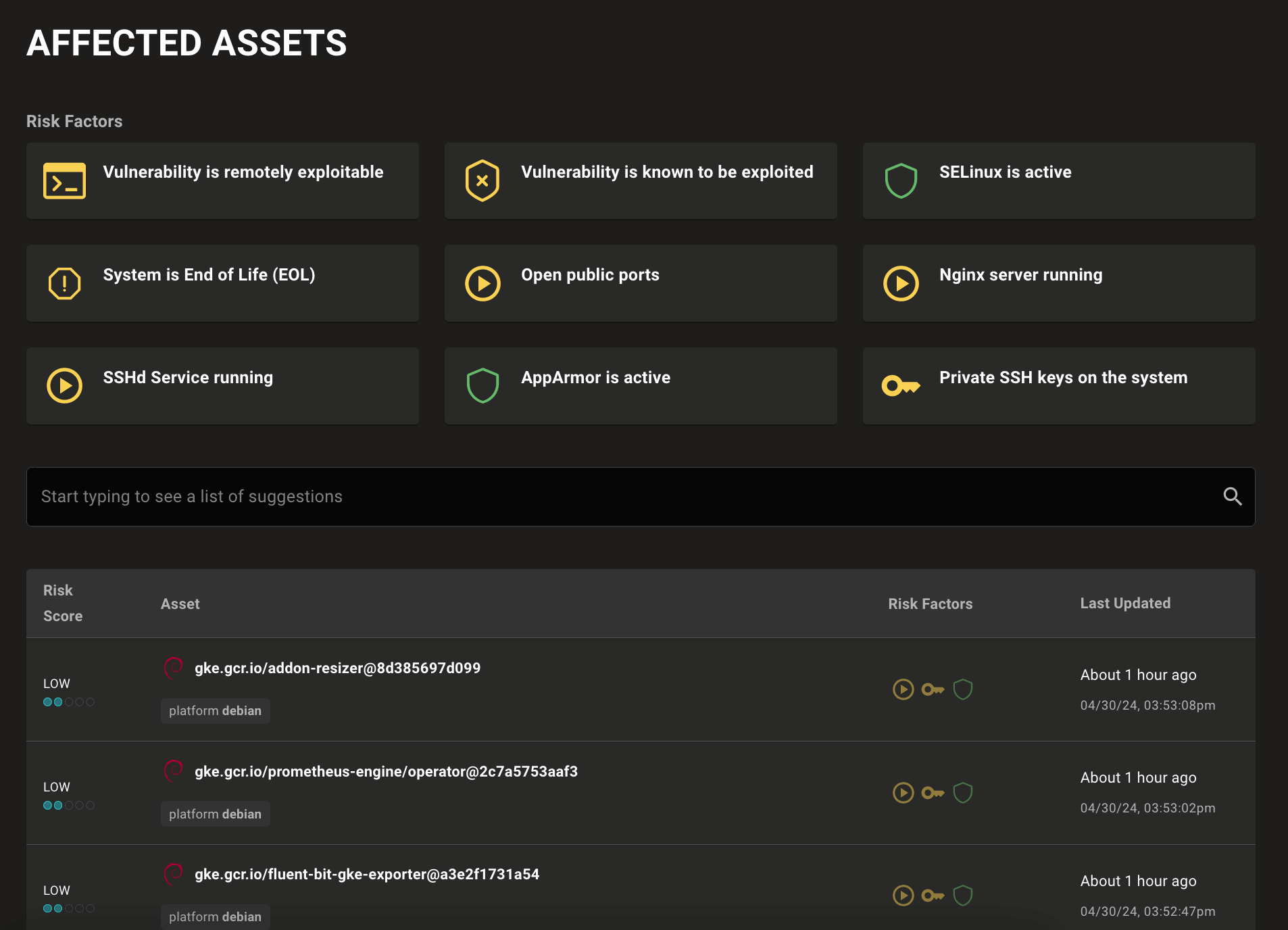
New Affected Assets vulnerabilities page
A whole new vulnerabilities Affected Assets page lets you better prioritize assets in your environment with critical vulnerabilities. Top-of-page filters allow to drill into individual risk factors that increase or decrease the threat that vulnerabilities present.
Automated integration setup in Terraform
Sprinkle some IaC on your Mondoo deployment with the latest capabilities in Mondoo's Terraform provider 0.6.0. With this new release of our Terraform provider you automate the setup of Azure, Slack, and domain integrations. You can even tie in the Azure setup with the Mondoo setup to make managing Azure applications easier than ever. Thanks you @mati007thm and @Pauti for all your fantastic work making this provider possible!
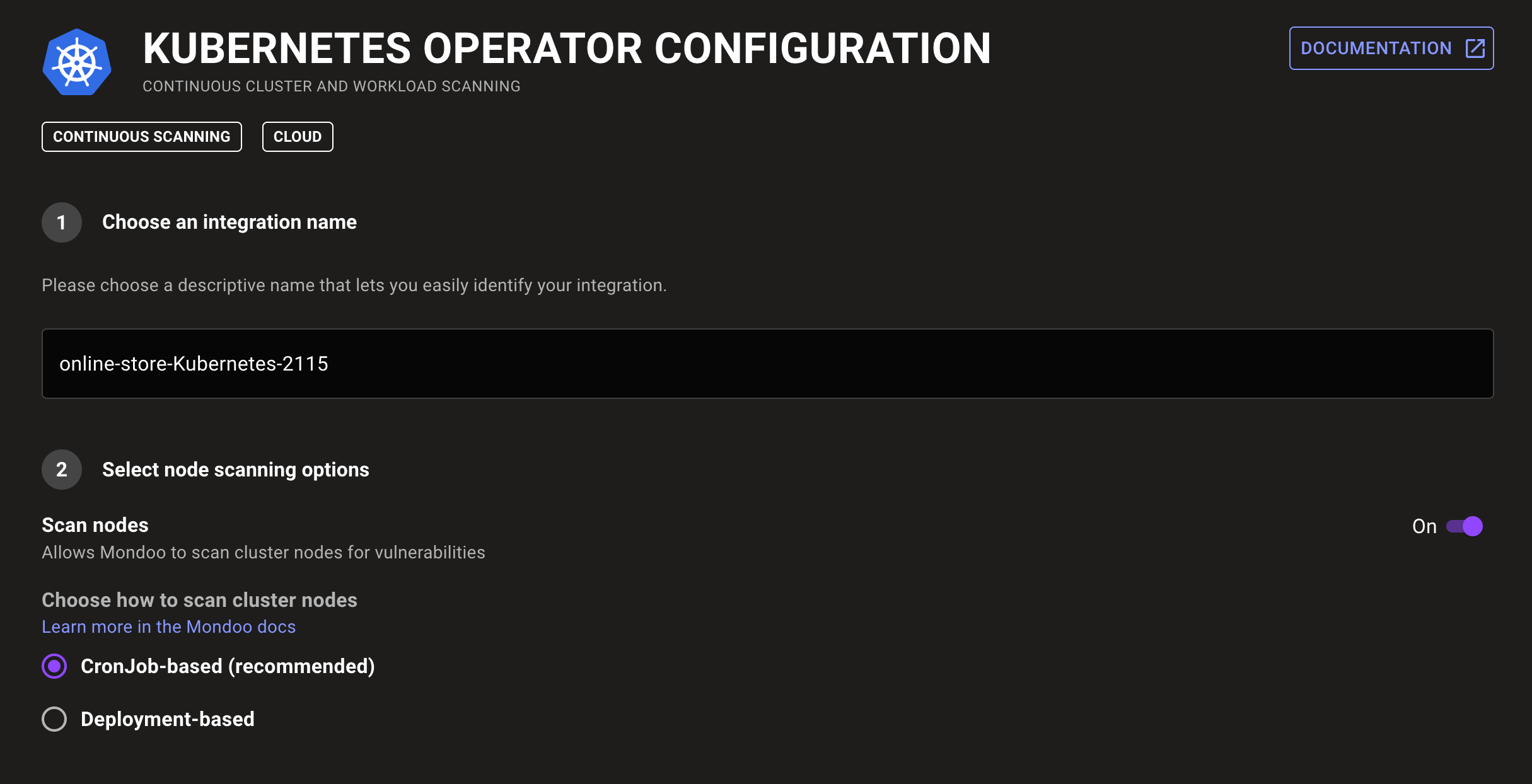
Kubernetes DaemonSet-based node scanning
With the new DaemonSet Kubernetes node scanning option you can scan Kubernetes cluster nodes with the Mondoo Kubernetes Operator even if the node utilization is too high for CronJob scheduling. If your clusters run high utilization you can either edit an existing integration to use DaemonSets or configure a new integration with DaemonSet node scanning.
🧹 IMPROVEMENTS
Resource updates
aws.ec2.images
- Add
createdAtfield
aws.elb.loadbalancer
- Add
availabilityZonesfield - Add
elbTypefield - Add
hostedZoneIdfield - Add
regionfield - Add
securityGroupsfield - Add
vpcfield - Deprecate
vpcIdin favor ofvpcfield which exposes theaws.vpcresource
aws.vpc.subnet
- Add
regionfield
docker.file
- Add
exposefield - Add
labelfield
gcp.project.gkeService.cluster
- Expand default fields to improve
cnquery shelluse - Add
shieldedNodesConfigfield - Add
costManagementConfigfield - Add
confidentialNodesConfigfield - Add
identityServiceConfigfield - Add
networkPolicyConfigfield
gcp.project.gkeService.cluster.addonsConfig
- Add
gcsFuseCsiDriverConfigfield - Add
statefulHaConfigfield
gcp.project.gkeService.cluster.networkConfig
- Add
enableMultiNetworkingfield - Add
enableFqdnNetworkPolicyfield - Add
enableCiliumClusterwideNetworkPolicyfield
sshd.config
An all-new sshd.config resource includes support for parsing the combined sshd_config and sshd_config.d/* configs. Now Mondoo can track the running state of your SSH daemon no matter where you define configuration options.
Mondoo now properly identifies match groups across include paths defined in the sshd_config file. We have extensively tested how SSHd handles the various edge-cases and have adjusted our parser accordingly. It now properly parses the different scenarios of match groups with or without include statements and adds them to the affected subgroups.
The content field is now deprecated. This is an old remnant that is no longer providing the best version of the raw SSHd config. As mentioned above, include and match statements actually behave differently based on their context. They cannot simply be aggregated into a single content file. Instead, please use the already provided file and files fields, which both have content as their subfields.
k8s
Multiple statements are now correctly treated in params. In the case of SSHd, the first statement usually wins (with a couple of edge-cases that are still aggregated, which have been added here as well).
Include statements now work with relative and absolute paths. We previously only supported relative paths (such as files inside of /etc/ssh). This limitation is no longer in place.
Ubuntu 24.10 CVE detection
Yesterday Canonical announced the start of development for Ubuntu 24.10, code named Oracular Oriole. If you're a risk taker and want to run this pre-alpha release of Ubuntu, Mondoo has your back with CVE support for this upcoming release.
More policies out of the box for new spaces
Get started more quickly with new out-of-the-box policies for DNS, Slack, and TLS for all newly created spaces.
🐛 BUG FIXES AND UPDATES
- Prevent failures scanning GCP BigQuery.
- Fix failures scanning Atlassian accounts.
- Improve display of Azure resources on the inventory page when resource discovery is used.
- Improve documentation for AWS and Azure resources within
cnquery shell. - Fix failures scanning GCP compute resources.
- Support scanning individual resources within a GCP org during scanning.
- Display CVEs linked to CentOS advisories.
- Switch Red Hat Enterprise Linux EOL dates to use the Maintenance Support 2 date because this is included with support by default.
- Improve performance of the advisories page.
- Don't include preview policies in an asset's score.
- Improve display of Atlassian group names on the inventory page.
- Don't group GCP Folders as "Others" on the inventory page.
- Fix warnings in GCP compute instance asset overview pages.
- Fix Azure compute VMs grouping under "Subscriptions" on the inventory page.
- Improve the icon for the remote execution risk factor.
- Collect the version of Microsoft Exchange to the Mondoo Windows asset inventory query pack.
