Mondoo 11.16 is out!
🥳 Mondoo 11.16 is out! This release includes a new compliance framework experience, updated policies, and more!
Get this release: Installation Docs | Package Downloads | Docker Container
🎉 NEW FEATURES
New compliance framework experience
We've reworked the Compliance Hub to make it easier to start and manage audits with Mondoo. A new welcome page helps you pick your very first framework.
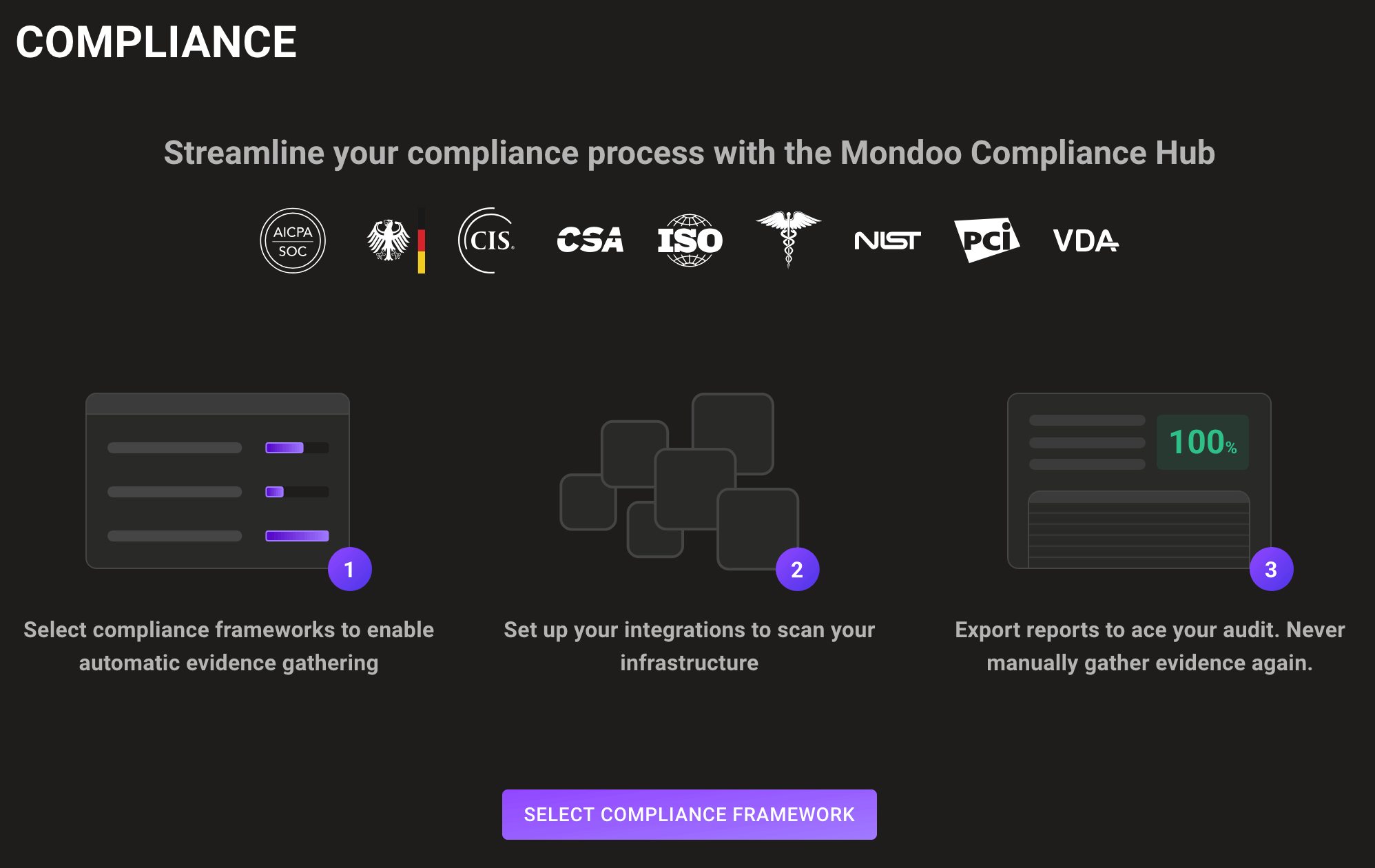
Choose from our ever-growing list of out-of-the-box compliance frameworks, now with helpful descriptions.
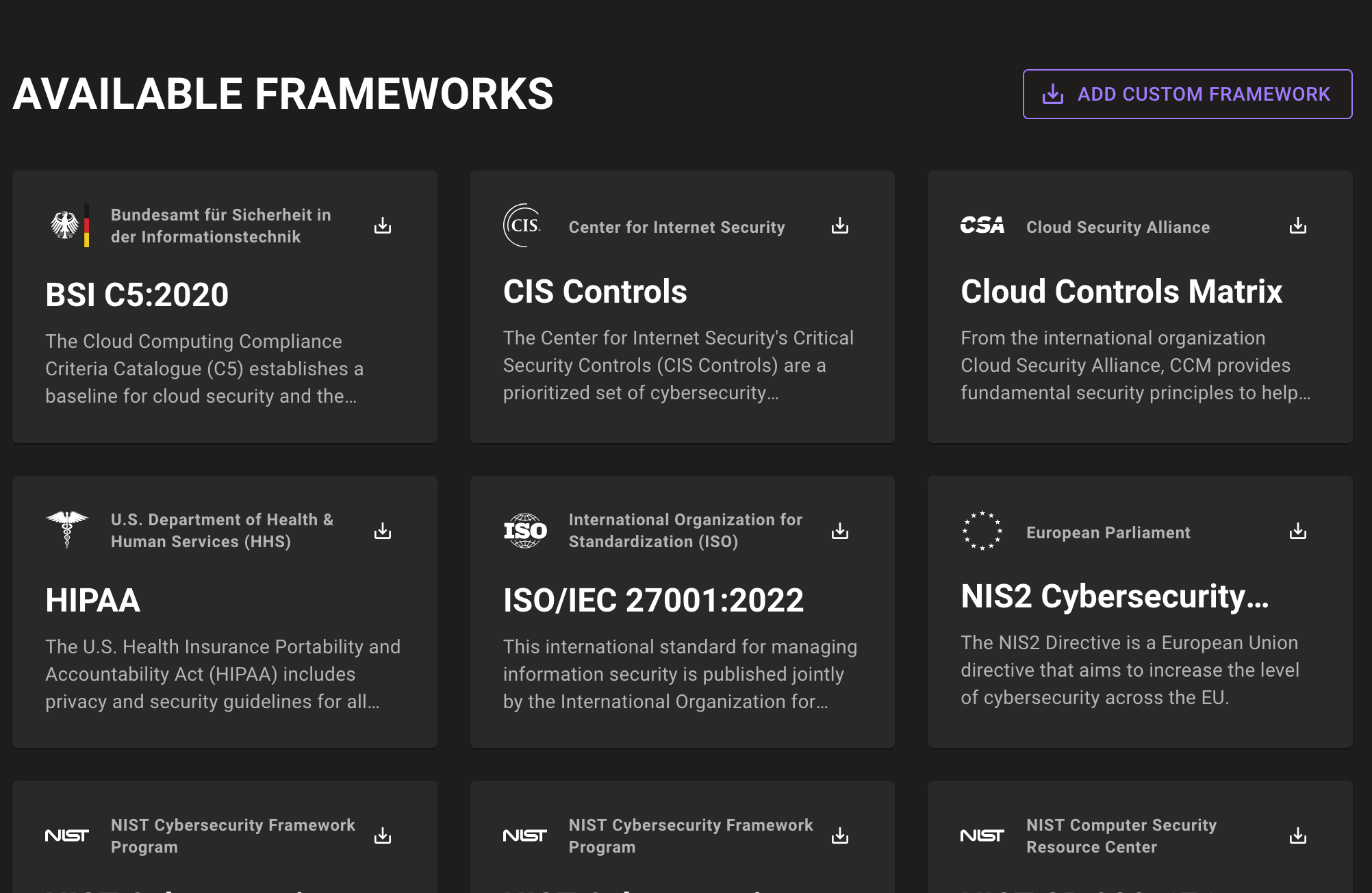
To make it easier to manage in-progress audits, we've introduced preview and active states for audits. Only frameworks in those states display in Compliance Hub, which helps you get right to what you need.
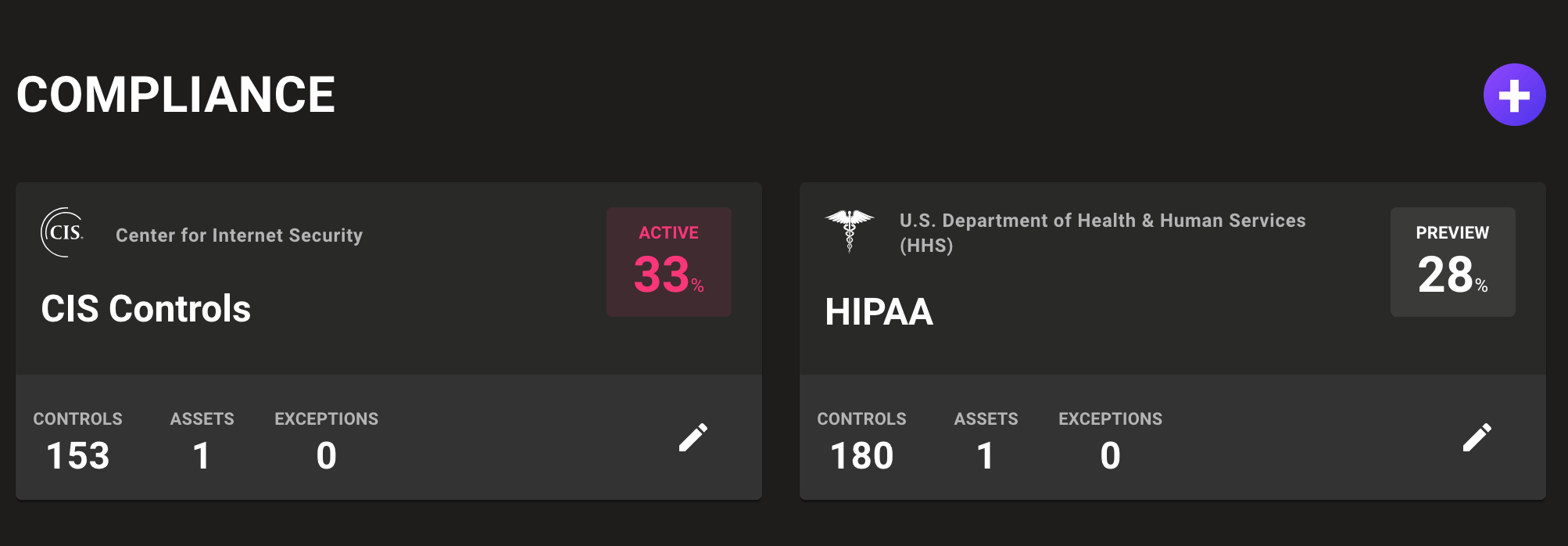
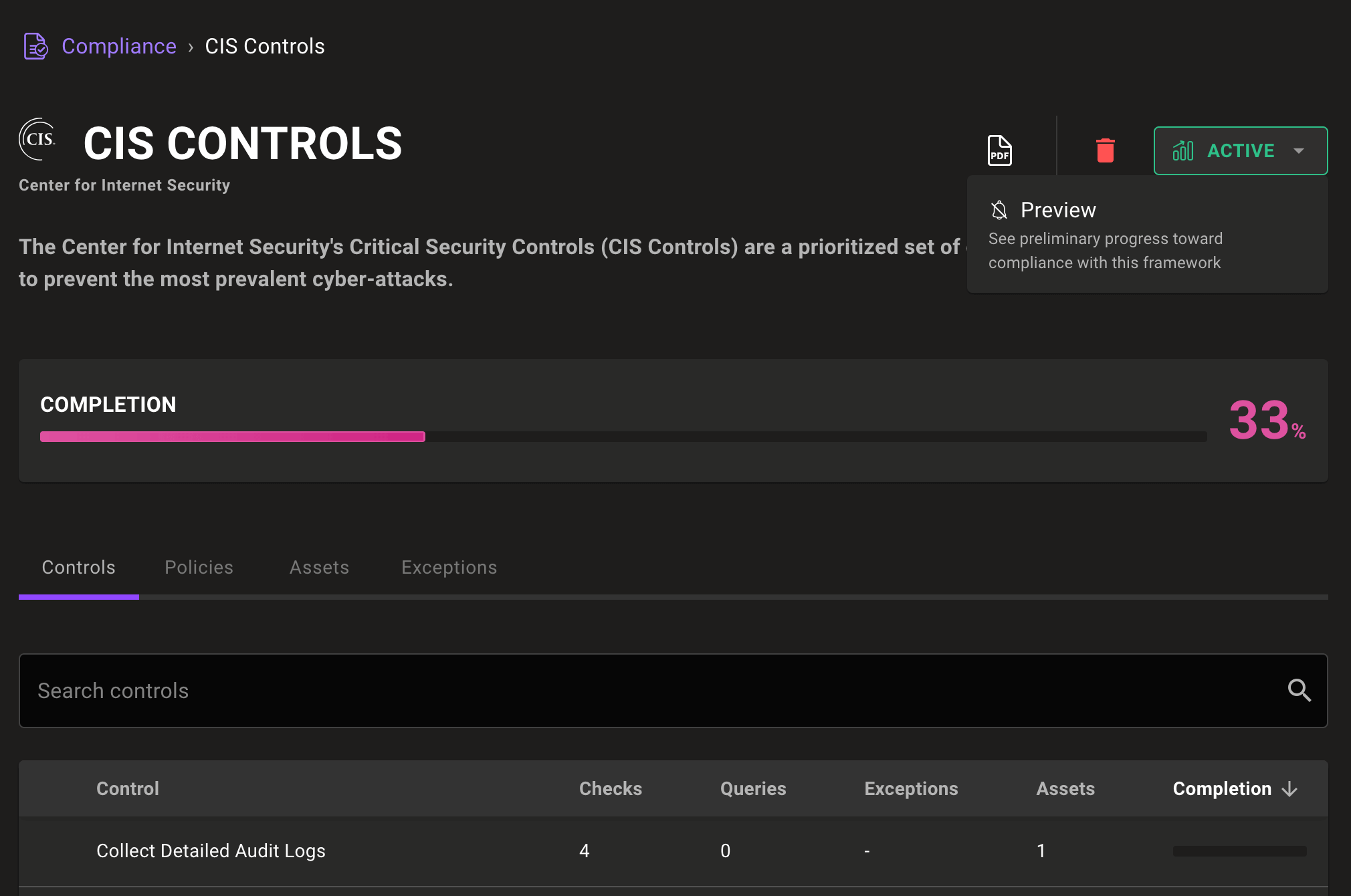
Reworked framework pages include helpful descriptions, a simpler progress indicator, and a quick selector so you can control the state of an audit.
Sample compliance evidence with MQL
Provide sample data to auditors with a new sample helper in MQL. Use this helper to randomly sample a set number of items from any list or map data:
MQL> [1,2,3,4,5,6,7,8,9,10].sample(3)sample: [0: 21: 102: 9]
🧹 IMPROVEMENTS
CIS enterprise Linux 9 benchmarks 2.0
Bring the latest security recommendations to your enterprise Linux infrastructure with the new 2.0 release of CIS benchmarks for AlmaLinux, Oracle Linux, Rocky Linux, and Red Hat Enterprise Linux 9. This major new policy update includes 630 total changes, including dozens of all-new recommendations to keep your systems secure.
Newly certified CIS benchmark policies
Our RHEL 7, Amazon Linux 2, Oracle Linux 7, CentOS Linux 7, and GitLab CIS benchmarks have all passed the rigorous CIS benchmark validation process and received full certification for their quality and completeness. These policies add to the 130+ Mondoo CIS benchmarks already certified, making Mondoo a top vendor for CIS certified content.
Improved Kubernetes integration setup
More easily manage workload scanning with updates to the Kubernetes integration page. These include a pre-populated namespace filter to skip scanning the operator itself and a simpler flow for enabling or disabling workload image scanning.
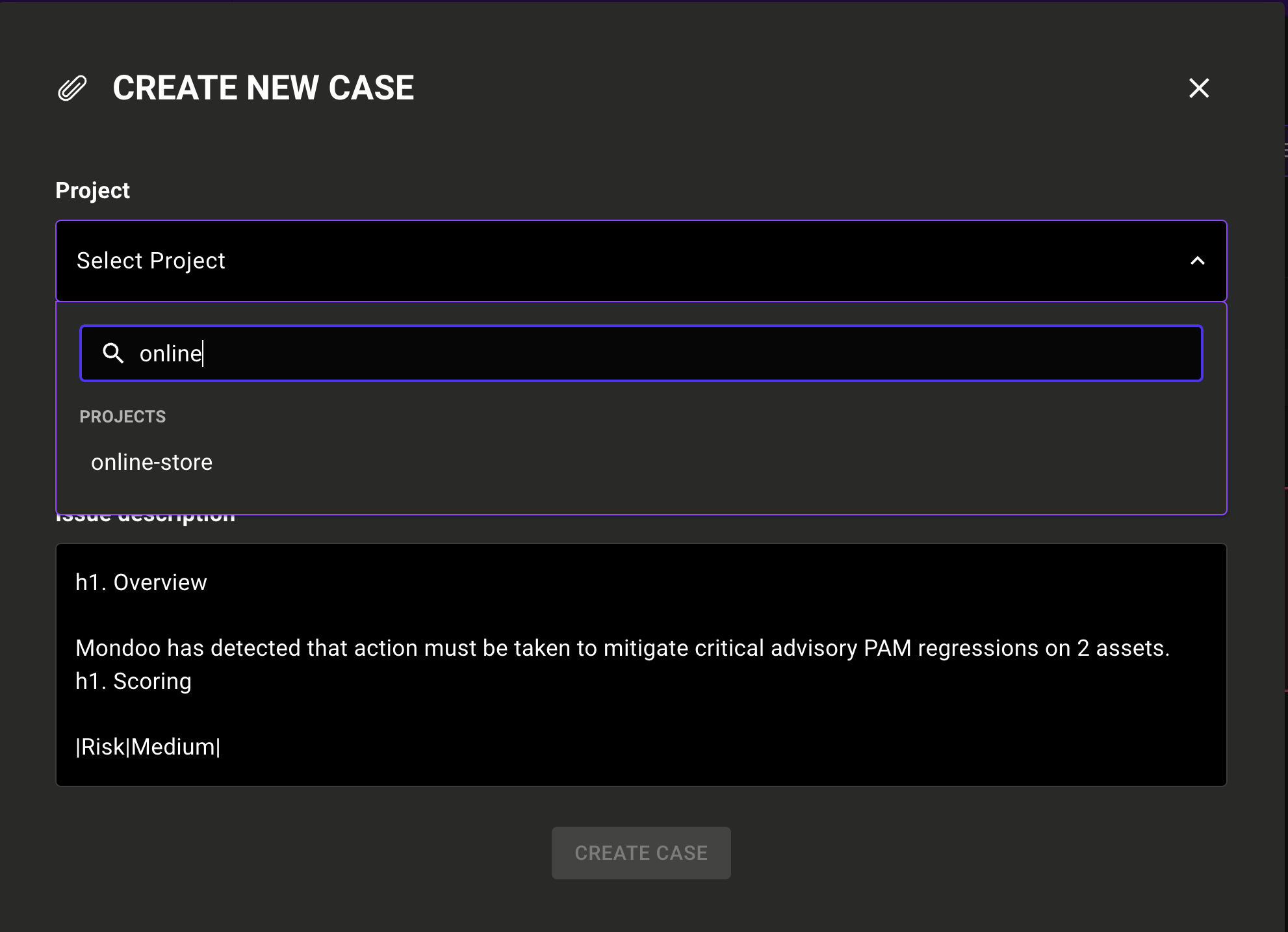
Manage large numbers of Jira projects with cases
Even customers with the largest of Jira installations can use Mondoo cases. We've improved support for fetching large project lists and added a new project selection page that includes quick, text-based filtering.
Expanded EDR policy support
The Mondoo Endpoint Detection and Response (EDR) policy now includes support for detecting the Sophos Endpoint Defense Agent as well as improved support for the SentinelOne agent.
Resource updates
atlassian.jira.issue
- New
createdAtfield - New pagination support for fetching large issue counts
azure.subscription.cosmosDbService
- New support for Cosmos DB, MongoDB, and PostgreSQL databases
github.repository
- New
defaultBranchfield
🐛 BUG FIXES AND UPDATES
- Improve help links in cases to go directly to cases documentation.
- Improve how CVSS and EPSS scores display on asset page lists.
- Don't display vulnerabilities with a CVSS score of 0 as critical.
- Allow assets to re-register to a different region when using the
--tokenflag. - Don't show expected errors when scanning GitHub repositories.
- Improve rate limiting when scanning GitHub.
- Improve navigation bar rendering on macOS systems when scroll bars are set to always show.
- Fix a failure listing data on containers in
k8s.deployments. - Improve rate limiting in the GitHub provider.
- Add a property for configuring the desired MFA enrollment time periods in CIS Google Workspace Foundations Benchmark policy.
- Improve text and links added to Jira issues when a case is resolved.
- Open all links to Jira issues in a new tab or window.
- Expand the "Use Entra ID Client Authentication and Azure RBAC where possible" check in the CIS Azure Foundations Benchmark policy to include additional services.
- Don't run kernel parameter checks on containers or container images.
- Improve integration setup steps for all integrations.