Mondoo 11.12 is out!
🥳 Mondoo 11.12 is out! This release includes a new way to track security tasks within your team's existing workflow, compliance framework management in the CLI, and more!
Get this release: Installation Docs | Package Downloads | Docker Container
🎉 NEW FEATURES
Track and remediate vulnerabilities with cases
Cases are a new feature of Mondoo that allow you to turn security findings into tasks to complete. They integrate with Atlassian Jira to fit into your existing workflow.
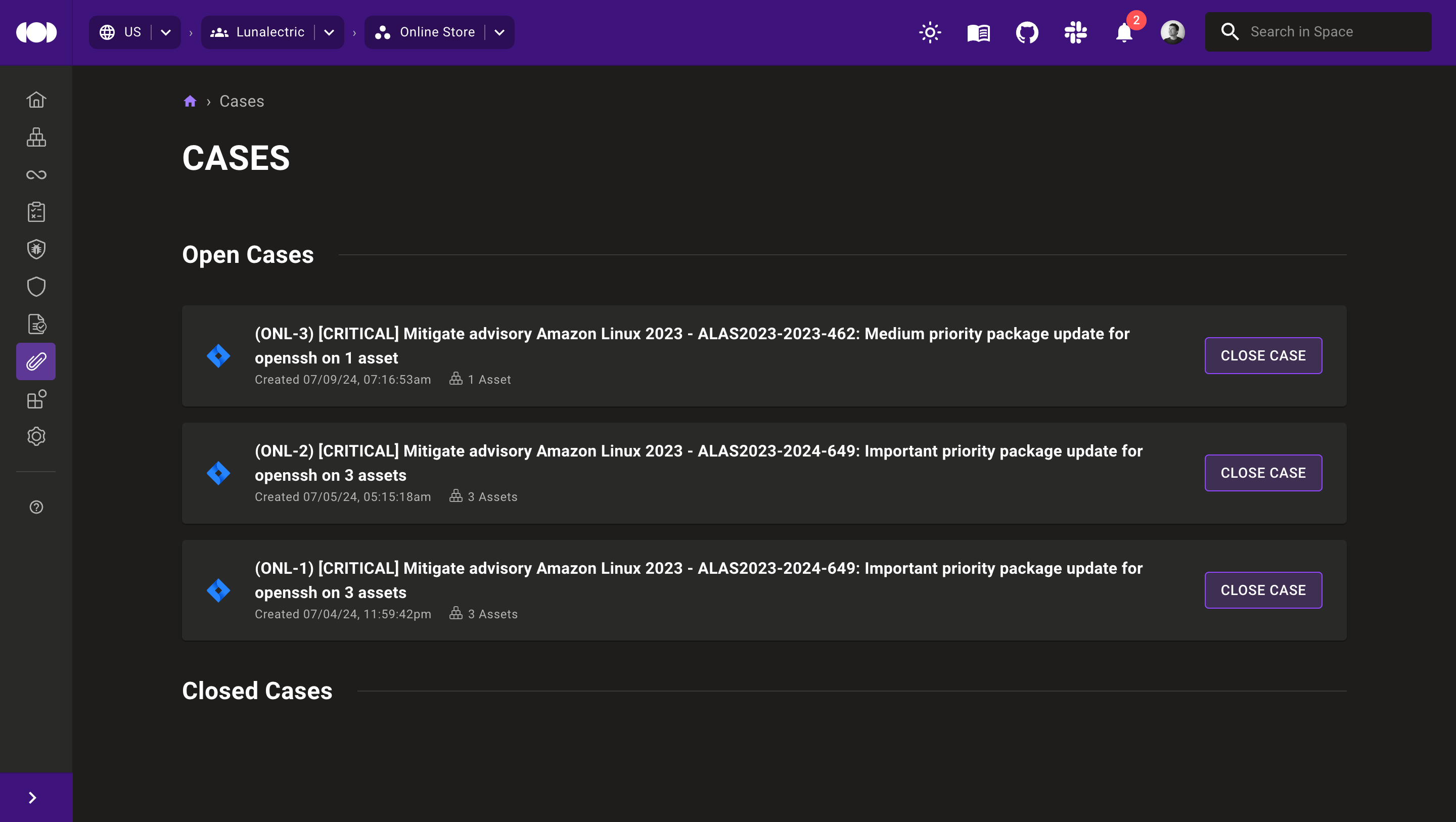
When you see a security finding that requires fixing, you create a case for that finding. Mondoo automatically includes the details of the finding, information on the asset(s) that contain the finding, and instructions for fixing it. When you save the case, Mondoo automatically creates an issue containing all the same information in your Jira project.
The Jira issues that Mondoo creates from cases include all the details necessary for infrastructure owners to remediate findings, even if they don't have access to Mondoo.
In the Mondoo Console, if a security finding or an asset has a case associated with it, you can view the case from the finding or the asset. You can also see a list of all cases in a space.
You can also close cases in the Mondoo Console and (optionally) also automatically close the corresponding issue in Jira.
Open the cases management page in the Mondoo Console to get started, or check out the documentation.
Manage compliance frameworks in the CLI
Whether you're iterating on a custom compliance framework locally or automating the management of frameworks stored in source control repos, the new cnspec framework command makes managing frameworks a breeze. Now you can list, download, upload, and change the state of frameworks entirely on the command line.
Usage:
cnspec framework [command]
Available Commands:
active Change a framework status to active
download Download a compliance framework
list List available compliance frameworks
preview Change a framework status to preview
upload Upload a compliance framework
Flags:
-h, --help help for framework
Global Flags:
--api-proxy string Set proxy for communications with Mondoo API
--auto-update Enable automatic provider installation and update (default true)
--config string Set config file path (default $HOME/.config/mondoo/mondoo.yml)
--log-level string Set log level: error, warn, info, debug, trace (default "info")
-v, --verbose Enable verbose output
🧹 IMPROVEMENTS
Rocky Linux AppStream advisories
Mondoo now includes Rocky Linux AppStream package advisories, so you can secure assets that use AppStream to get the latest language and server releases.
Expanded Terraform policy support
Catch critical security issues before they reach production with expanded Terraform support in the CIS AWS Foundations and CIS GCP Foundations benchmark policies.
Resource updates
aws.ec2.securitygroup.ippermission
- New
prefixListIdsfield - New
userIdGroupPairsfield
aws.iam.policy
- New
policyIdfield to replace the now deprecatedidfield
aws.rds.dbinstance
- New
subnetsfield
aws.vpc.routetable
- New
associationsfield using the newaws.vpc.routetable.associationsresource
🐛 BUG FIXES AND UPDATES
- Add asset overview information for the
k8s-serviceplatform. - Add
servicesto the discovery help incnspec scan k8s --help. - Allow users with organization permissions (but no space permissions) to invite users to a space.
- Improve application of the CIS GitHub benchmark policy on individual repositories.
- Give discovered AWS ECR images a runtime value of
aws-ecr. - Improve and expand checks in the CIS AKS benchmark policy.
- Improve handling of non-English Windows systems in Mondoo, BSI, and CIS policies.
- Update Mondoo, BSI, and CIS Windows policies to better handle settings defined via GPO.
- Improve reliability of some CIS checks on Debian 12 hosts.
- Fix EPSS score values in advisory and CVE summary boxes.
- Make the GitHub Enterprise URL optional during integration setup.
- Don't show private resources in the shell auto complete.
- Don't error when scanning personal GitHub repositories.
- Allow scanning read-only Windows volumes.
- Improve filtering of boot partitions during snapshot scanning.
