Mondoo 11.11 is out!
🥳 Mondoo 11.11 is out! This release includes GitHub Enterprise support, automated IaC file discovery in code repositories, EU NIS2 Cybersecurity Directive Framework support, and more!
Get this release: Installation Docs | Package Downloads | Docker Container
🎉 NEW FEATURES
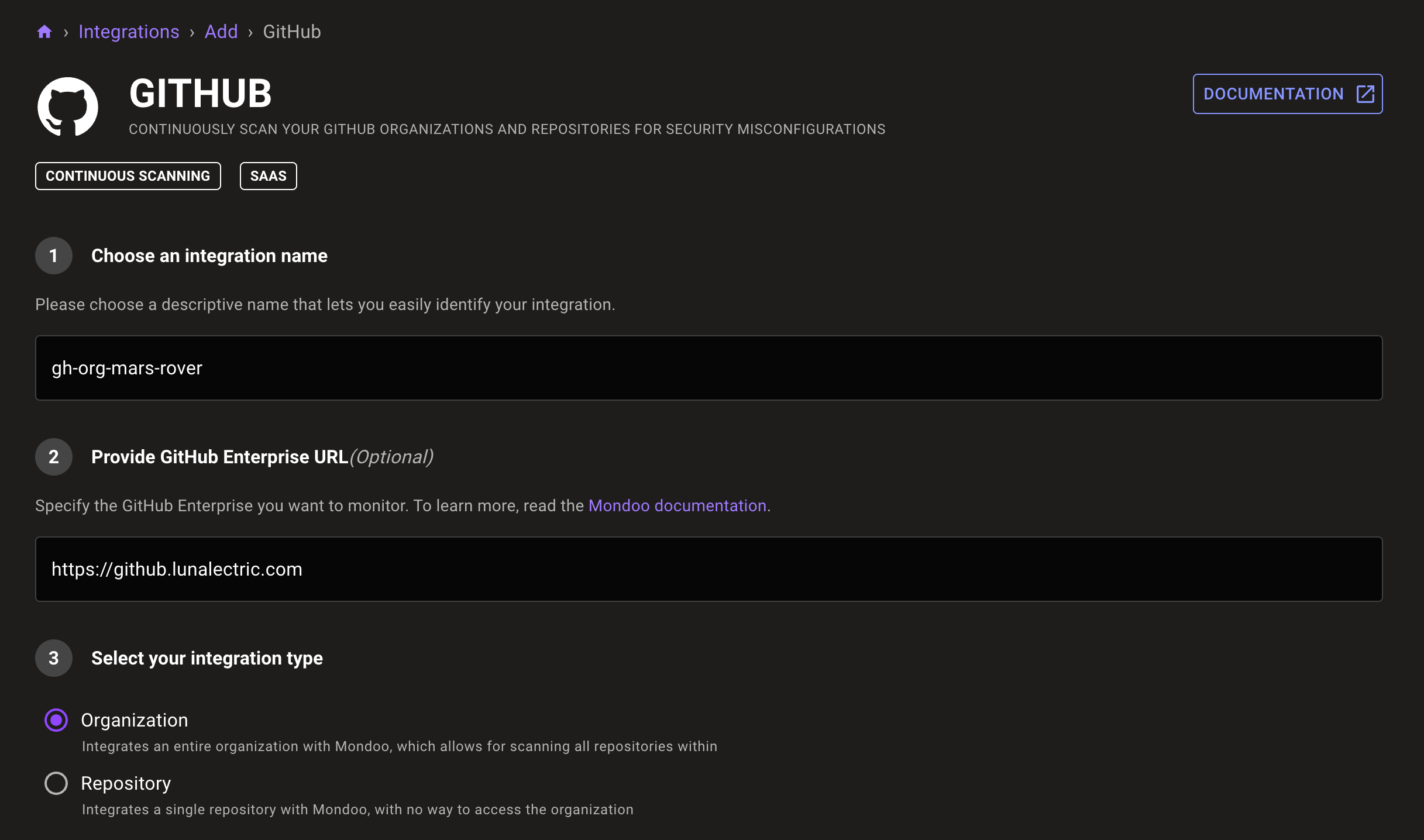
Continuous GitHub Enterprise scanning
Mondoo's GitHub integration has expanded to support GitHub Enterprise as well. GitHub Enterprise users can now get all the Mondoo GitHub features for their private instances, including scans of their GitHub configuration and automatic discovery of Terraform code and Kubernetes manifests in GitHub repositories.
Check out the documentation to learn more about integrating Mondoo Platform with GitHub Enterprise.
IaC file discovery in GitHub and GitLab
Mondoo now automatically discovers and scans Terraform code and Kubernetes manifests in GitHub and GitLab. If any static Terraform (HCL) or Kubernetes manifest files exist in a repo, Mondoo can detect and scan them for security misconfigurations. This option lets infrastructure developers responsible for writing and maintaining infrastructure as code detect security issues before they create problems in production.
Configure scanning in your existing GitHub and GitLab integrations.
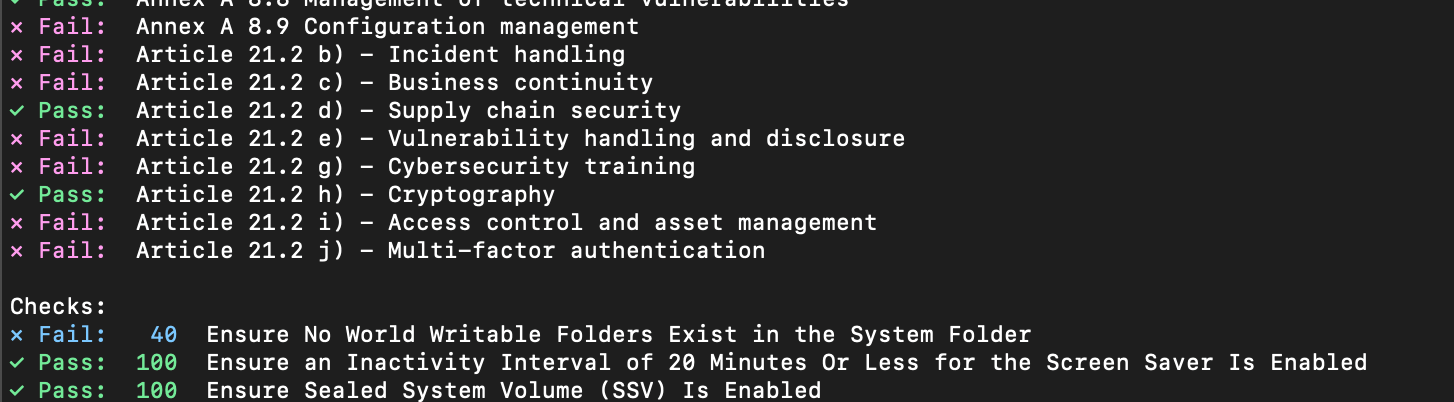
NIS2 Cybersecurity Directive compliance framework
Mondoo introduces a new NIS2 compliance framework for companies in the European Union that must comply with the NIS2 cybersecurity directive.
CIS Google Workspace benchmark policy
Secure your Google Workspace infrastructure with the new CIS Google Workspace Foundations Benchmark Level 1 and 2 policies including 58 important security checks.
🧹 IMPROVEMENTS
Oracle Linux Kernel CVE support
Mondoo now detects and reports vulnerabilities in the Oracle Unbreakable Enterprise Linux Kernel.
DaemonSet-based Kubernetes integration scanning
The Mondoo Kubernetes integration now supports running as either a DaemonSet, a Deployment or a CronJob, depending on your needs.
Improved GitHub organization scanning scalability
Multiple improvements to the GitHub organization scanner now better ensure that Mondoo does not accidentally trigger GitHub's API rate limits.
Improved Mondoo Terraform provider
The Terraform provider for Mondoo has several changes:
- The Terraform provider has full access to the asset list of a Mondoo space and can leverage those assets in Terraform HCL.
- The Terraform provider now has access to the full list of active policies via a data source.
- You can now use Terraform to enable Mondoo compliance frameworks and even upload custom frameworks.
Resource updates
aws.rds.dbinstance
- New
subnetsfield.
azure.subscription.aksService.cluster
- New
apiServerAccessProfilefield.
github.branch
- New
headCommitShafield.
github.packages
- New resource to fetch information on packages for a repository.
🐛 BUG FIXES AND UPDATES
- Add vendor source links to VMware and Visual Studio Code security advisories.
- Add security advisories for openSUSE Tumbleweed.
- Fix scans failing to cancel in the AWS serverless integrations.
- Fix sort ordering of Blast Radius in tables.
- Fix display of the empty credentials box on the Generate Long-Lived Credentials page.
- Don't reject
.indomains in the host integration setup page. - Fix the settings link in the navigation bar sometimes disappearing.
- Improve the reliability of EBS volume scanning in AWS.
- Improve reliability of VM scans in the Azure integration.
- Update Fedora and AlmaLinux EOL dates to match the latest vendor announcements.
- Update the EOL warning date to be when the date is 6 months out instead of 3.
- Fix an error displaying checks for some policies in the console.
- Fix a failure fetching the
attachedPoliciesdata in theaws.iam.usersresource. - Allow sorting compliance control checks in the console.
- Improve the reliability of CIS
Ensure default user umask is configuredandEnsure default user umask is 027 or more restrictivechecks. - Improve reliability of some Windows registry-based CIS checks.
- Simplify many Linux checks to improve result output.
- Reduce screen flickering when filtering checks on asset pages.
- Fix missing check counts in the asset check overview.
