Mondoo 10.4 is out!
🥳 Mondoo 10.4 is out! This release includes improved VMware CVE detection, NPM package detection, performance improvements, and more!
Get this release: Installation Docs | Package Downloads | Docker Container
🧹 IMPROVEMENTS
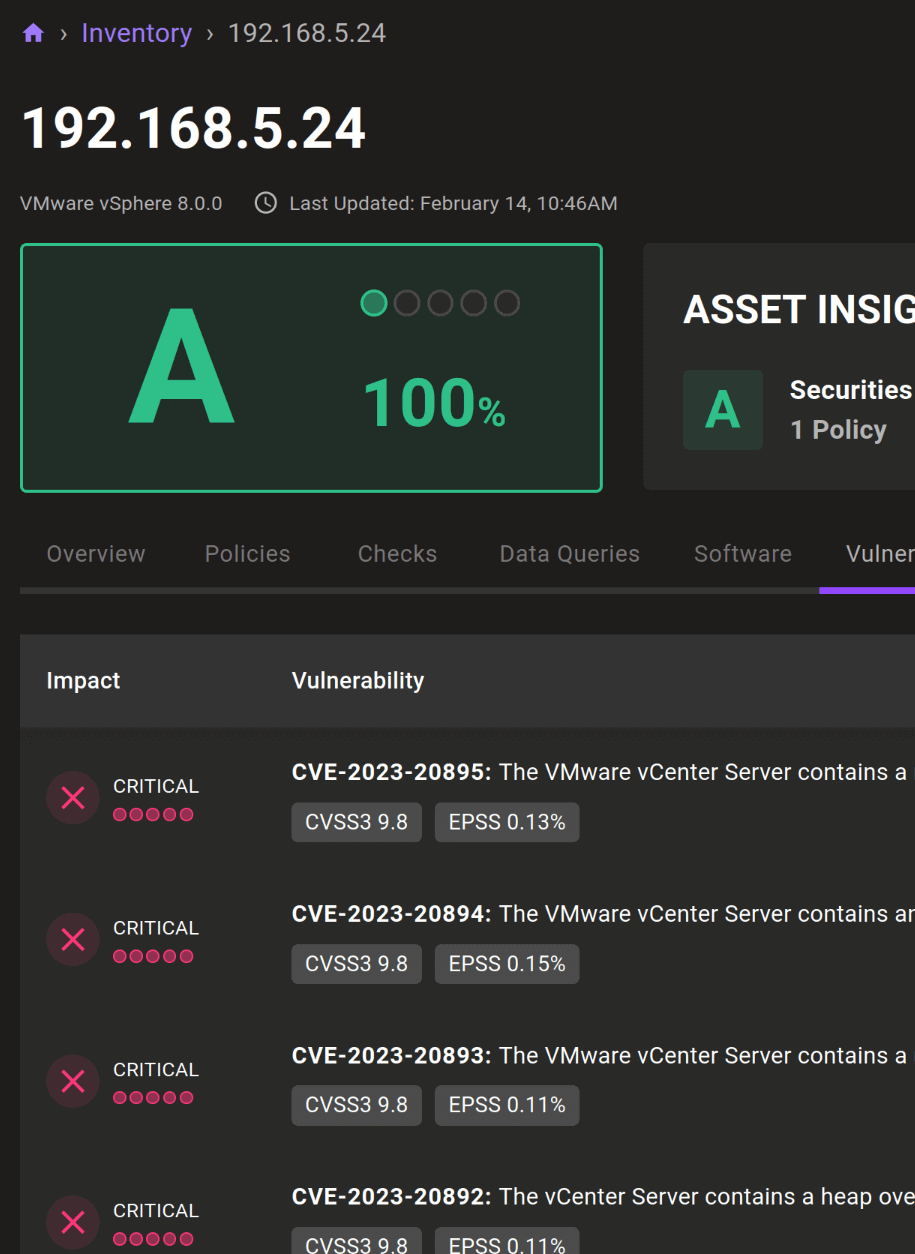
VMware vSphere advisory & CVE detection
Improved VMware vSphere advisory and CVE detection ensures you always have the latest advisories and CVEs flagged on both ESXi and vSphere assets.
Resource Updates
aws.cloudtrail
- New
cloudWatchLogsLogGroupArnfield
gcp.project.pubsubService.snapshot
- Fix fetching the
expirationfield
npm.packages
- New resource for fetching NPM packages installed on an asset
packages
- New
filesfield - New
cpefield on Windows assets
Performance improvements
Who doesn't like getting something for free? With Mondoo 10.4, you get your scan results not only faster, but using significantly less memory at the same time. In testing with large asset scans, memory usage has dropped from ~950MB to just ~200MB, while scan times were cut in half.
Save SBOMs to disk
Export SBOMs to a file with a new --output-target flag:
Plain Text$ cnquery sbom docker debian:12 -o cyclonedx-json --output-target debian-12.json→ discover related assets for 1 asset(s)debian:12 ━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━ 100%$ head debian-12.json{"$schema": "http://cyclonedx.org/schema/bom-1.5.schema.json","bomFormat": "CycloneDX","specVersion": "1.5","serialNumber": "urn:uuid:1685df36-e3f4-4174-b469-6bd9974a8c41","version": 1,"metadata": {"timestamp": "2024-02-20T10:49:41-08:00","tools": {"components": [
New Azure snapshot scanning options
New options for Azure snapshot scanning give you additional control over how Mondoo performs the scan:
- Skip the cleanup and instead rely on Azure to perform the cleanup with a new
--skip-snapshot-cleanupflag. - Scan snapshots that have already been attached to the VM with new
--skip-snapshot-setupand--lunflags.
Expanded NIST 800 compliance evidence
AWS NIST Best Practices policies now feed directly into Compliance Hub, so NIST security findings can be part of your automatic evidence gathering for audits.
🐛 BUG FIXES AND UPDATES
- Fix failures scanning container images.
- Fix fetching CPEs on VMware platforms.
- Display the correct SSH keys when remotely scanning hosts.
- Fix failures in the EOL policy and improve output when a system approaches EOL.
- Show just the severity icon for vulnerabilities instead of severity and scan result.
- Fix failures running the
shellandruncommands. - Improve reliability of console results pagination.
- Fix failures scanning Microsoft 365 and GitHub assets.
- Improve display of scan results in Azure and Microsoft 365 when the result is nil.
- Improve scan results output in the CIS AWS Foundations and Microsoft 365 Foundations benchmarks.
- Don't error if a Kubernetes container cannot be discovered.
- Add a property to the CIS AWS Foundations benchmark to allow controlling which ports are blocked on instances.
- Improve rendering of the asset page on wide displays.
- Fix incorrect CVE detection in .NET Runtime.
- Prevent empty titles in CVEs when the published CVE is incomplete.