Mondoo 10.2 is out!
🥳 Mondoo 10.2 is out! This release includes key improvements in known exploitable vulnerability tracking, Slack team scanning, improvements to the space overview screen, and more!
Get this release: Installation Docs | Package Downloads | Docker Container
🧹 IMPROVEMENTS
Additional sources for CVEs and advisories
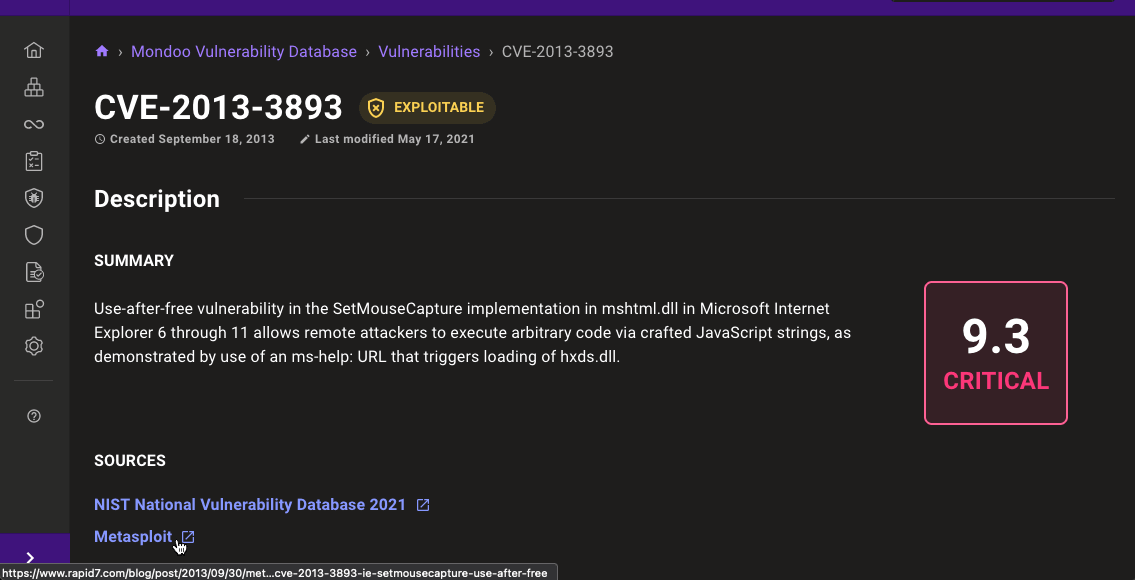
For vulnerabilities that have known exploits in the wild, Mondoo now provides a link to the external citation from the CVE page:
-
For software vulnerabilities listed in the CISA Known Exploited Vulnerability (KEV) catalog, Mondoo now provides a link to the catalog entry.
-
For software vulnerabilities listed in Metasploit, Mondoo now provides a link to exploit in the Metasploit source repository.
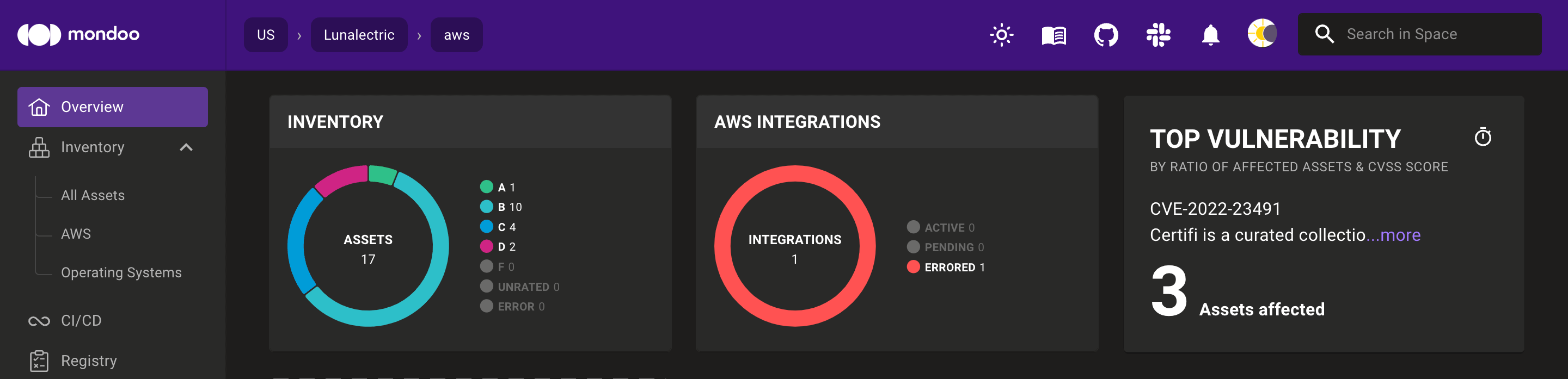
Find top vulnerabilities for spaces
The space overview now shows the top vulnerability in the space, as determined by the ratio of impacted assets and CVSS score.
slack.users performance improvements
We continue to optimize fetching Slack data for large Slack workspaces. New optimizations for user fetching result in query times up to 25x faster.
New sshd.config.blocks field
The ssh.config resource now includes a new blocks field that allows you to query configuration data defined in individual sshd match groups.
For example, if you have an sshd configuration file with a match group for sftp-users:
...
X11Forwarding yes
Match Group sftp-users
X11Forwarding no
PermitRootLogin no
AllowTCPForwarding yes
Previously using the sshd.config.params field would show you both instances of the X11Forwarding configuration without the context necessary to understand where this configuration is applied:
> sshd.config.params.X11Forwarding
"no,yes"
Using blocks you can dive deeper to see exactly which users get each configuration option:
> sshd.config.blocks { criteria params }
sshd.config.blocks: [
0: {
criteria: ""
params: {
X11Forwarding: "yes"
...
}
}
1: {
criteria: "Group sftp-users"
params: {
AllowTcpForwarding: "yes"
PermitRootLogin: "no"
X11Forwarding: "no"
}
}
]
🐛 BUG FIXES AND UPDATES
- More consistent asset names on *nix-based assets.
- Fix infinite loading of the integrations sidebar.
- Improve display of platforms in variant policies.
- Improve the description of EPSS data on CVE and advisories pages.
- Improve retries and timeouts for provider downloads.
- Fix malformed policy downloads from the registry when a policy contains variants.
- Fix missing platform icons for policies with variants.
- Fix an error hovering over policies in the registry when colorblind mode is enabled.
- Use a consistent font size for all exceptions in exception tabs.
- Ensure all unapproved exceptions are expanded by default in exception tabs.
- Remove the "Space created" item from the exceptions tabs.
- Improve rendering of the asset's software list in the print view.
- Removed failing Azure Entra ID checks from the Mondoo Azure policy.
- Improved the reliability and output of queries in the CIS Azure and MS 365 benchmark policies.
- Fix data queries showing as failing checks in the console.
- Add wrapping for long asset annotation text values on the asset page.
- Fix failures loading unscored assets.
- Improve the display of tooltips in light mode.
- Improve error messages due to authentication failures in the
ms365provider. - Fix authentication failures with
cnquery run ms365. - Avoid running a command more than once in some situations when using the
processesresource. - Resolve Microsoft 365 integration timeouts due to scan errors.
- Improve scan time performance by caching failures.
- Fix a crash in the
aws.iam.virtualMfaDevicesresource due to insufficient IAM permissions. - Fix an error fetching some fields in the
aws.cloudtrail.trailsresource. - Fix an error fetching Microsoft Teams policy data.
- Resolve a failure to fetch policies when scanning.
- Improve the counts of checks and queries displayed for assets.

