Mondoo 10.1 is out!
🥳 Mondoo 10.1 is out! This release includes application CVE detection, CIS M365 benchmark 3.0, expanded asset overview data, and more!
Get this release: Installation Docs | Package Downloads | Docker Container
🎉 NEW FEATURES
Application CVE detection
We've all been on the Zoom meeting when our coworkers share their screens and every browser window shows the "relaunch to update" badge. How long has Bob in accounting been browsing the web with that unpatched browser? A day? A week? A month? It's hard to know your organization's level of exposure if vulnerability scanning stops at the OS. Go further with new application CVE detection for non-OS installed packages, starting with the detection of vulnerable Mozilla Firefox and Google Chrome releases.
A new Software tab on the asset detail page shows Mondoo-detected software vulnerabilities. Details include impact level and additional risk factors if known exploits exist for the application.
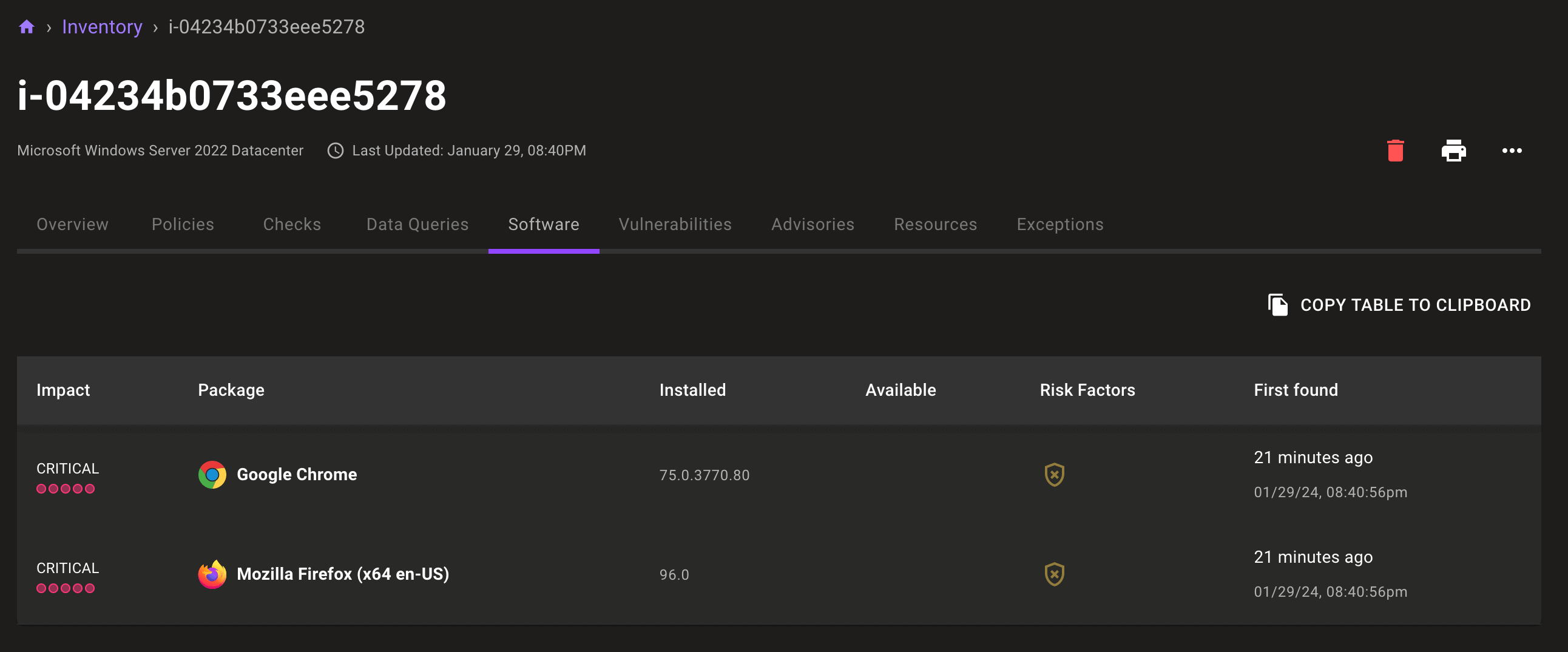
Want to view data on an asset's individual vulnerabilities? New Vulnerabilities and Advisories tabs let you dive directly into the individual risks on your assets.
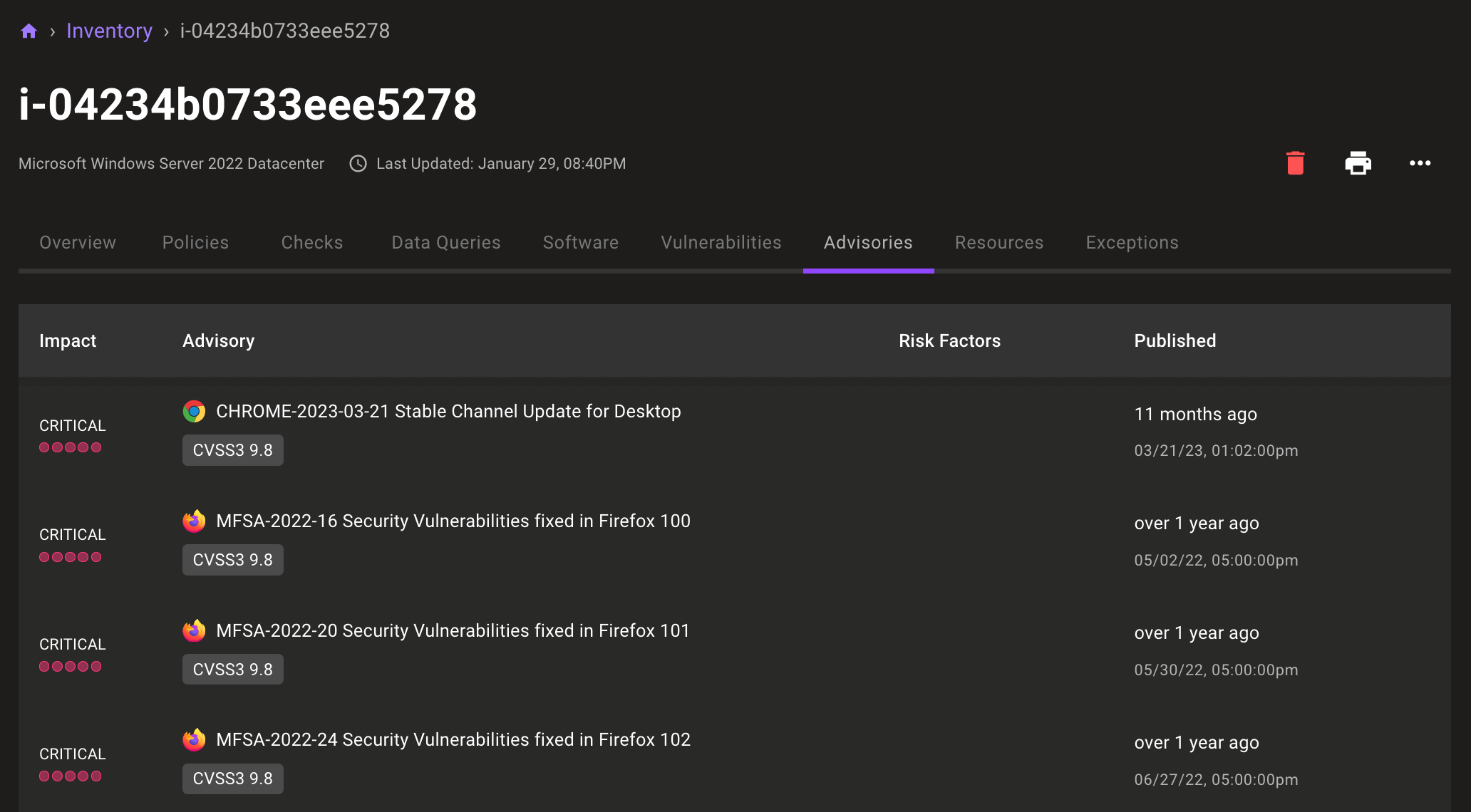
🧹 IMPROVEMENTS
CIS Microsoft 365 Foundations 3.0 policy
Mondoo now includes version 3.0 of the CIS Microsoft 365 Benchmark policy. This updated policy includes new and updated checks to keep your Microsoft 365 environment secure, including:
- 10 new Microsoft Teams checks
- 8 new Microsoft SharePoint checks
- 6 new Microsoft Power BI checks
- 15 updated checks with improved descriptions, remediations, and query values
Improved CIS Azure Foundations policy queries
Reworked queries in the CIS Azure Foundations Benchmark policy provide more reliable results and improved output so you can quickly find and secure your Azure resources.
Improved asset overview information
Understand your assets at a glance using expanded asset overview information in Mondoo 10.1. New cloud, hardware manufacturer, hardware model, and serial number data are included for operating systems, allowing you to quickly track down assets.
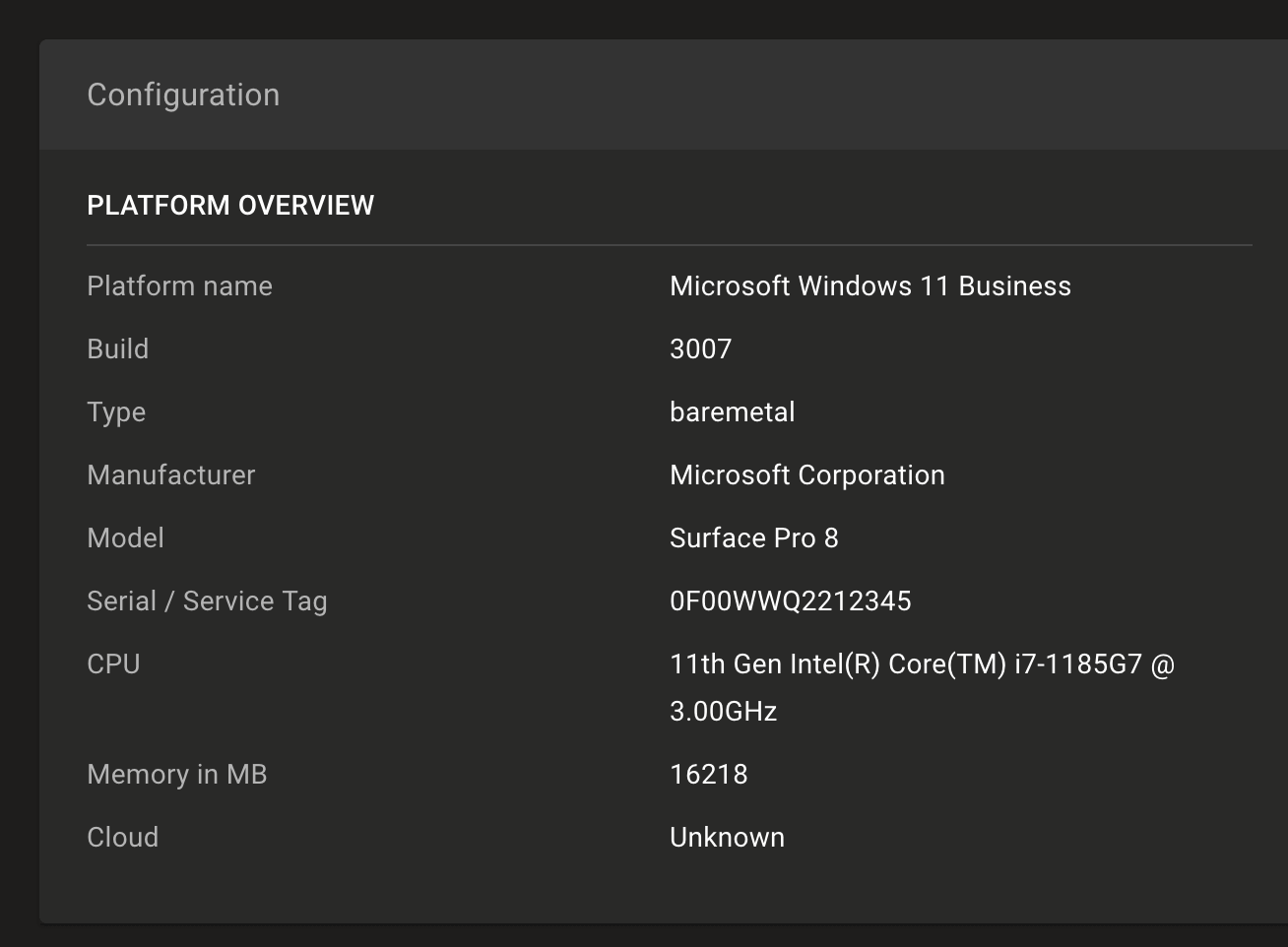
Expanded macOS and Windows inventory packs
We've expanded the Windows and macOS inventory packs to expose critical asset configuration data.
macOS queries
- SMBIOS system information
- Storage data
- Power data
- Network data
- Configuration profile data
- Uptime
- Running processes
- Kernel modules
- Mounts
- Active network connections
- SSHd configuration
Windows queries
- Uptime
- Running processes
- Scheduled tasks
- Expanded data for BitLocker volumes
- Expanded data for security products
- Expanded data for services
CVE detection on Linux Mint
Keep your Linux workstations fresh with expanded CVE detection support for Linux Mint.
Improved Azure authentication
No matter how you pass your authentication, Mondoo has your back with expanded authentication capabilities for scanning Azure subscriptions. Previously, running cnspec scan azure only loaded authentication credentials from the azure CLI. Now, scans can also load credentials from shell environment variables, workload identity, and managed identity, in addition to the CLI configuration.
CVSS scores in JSONL exports
Data integrations now export JSONL data with CVSS scores, so you can feed this critical risk data into external systems that consume your data exports.
Resource improvements
Dive deep into your Azure environment in the cnquery shell and create custom policies with an expanded MQL resource.
azure.subscription.computeService.vm
- New
zonesfield - New
statefield - New
isRunningfield
🐛 BUG FIXES AND UPDATES
- Improve formatting in policy description fields.
- Fix crash on empty array.flat with no type information.
- Fix CIS Red Hat Level 2 policy queries applying to non-Red Hat assets.
- Improve reliability of Linux sudoers checks.
- Change Slack provider retry logging messages from info level to debug.
- Reduce network IO during CVE scans.
- Improve error messages if a provider crashes.
- Improve the reliability and readability of queries in the CIS Azure Foundations policy.
- Prevent M365 SOC 2 checks from running on non-M365 platforms.
- Fix exceptions incorrectly displaying in some situations.
- Fix long-lived token usage failures in the AWS integration.
- Prevent failures in the Linux Inventory query pack on container image scans.
- Added back support for scanning systems via WinRM.
- Reduce memory usage during asset scans.
- Improved logging when cnquery/cnspec fails.
- Improve scan results for large Slack accounts.
- Return a helpful error when the specified provider cannot be found.
- Fix failures running the
aws.efs.filesystemresource. - Fix failures in the
azure.subscription.sqlService.firewallruleresource. - Fix missing image for hosts in weekly spaces emails.
- Improve descriptions of EPSS scores on CVE pages.
- Fix a panic when trying to fetch AWS S3 bucket locations in some situations.
- Exit 1 when cnspec or cnquery can't connect to the asset to scan.
- Show a friendly message on the space settings page for API tokens when the user does not have permission.
- Avoid displaying partial scan results in the console.