Mondoo 10.0 is out!
🥳 Mondoo 10.0 is out! This release includes detection of known exploited vulnerabilities, EPSS scores for CVEs, a new light mode, and more!
Get this release: Installation Docs | Package Downloads | Docker Container
🎉 NEW FEATURES
Expose exploitable CVEs
Mondoo now flags CVEs found in CISA's Known Exploited Vulnerabilities Catalog. These CVEs are critically important to patch in your environment. Now you can track the patching status across your fleet to prioritize work.
Individual CVE pages include an exploitable badge when a CVE is in the CISA Known Exploited Vulnerabilities Catalog:
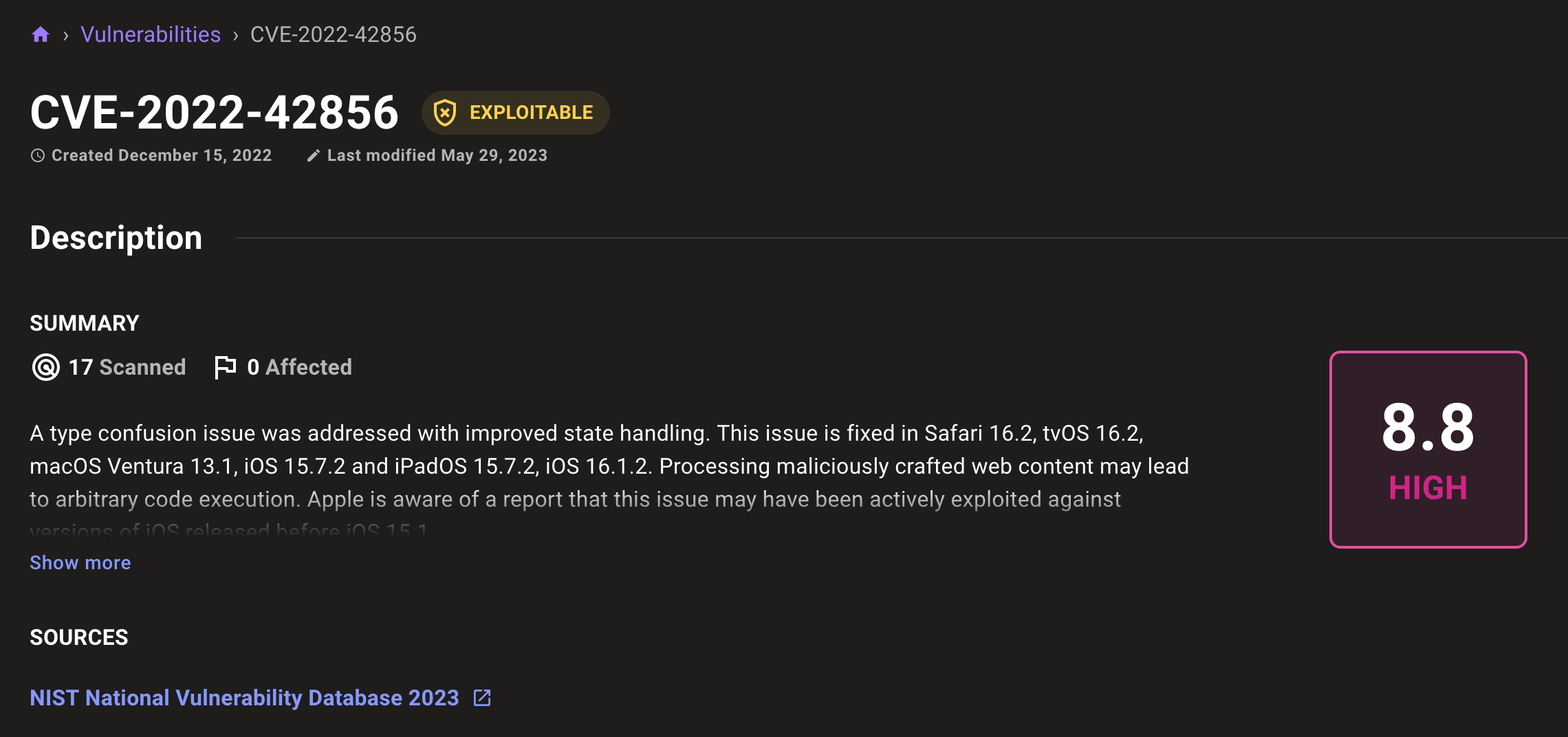
From the CVEs page, a new yellow shield badge designates Known Exploited Vulnerabilities Catalog CVEs.
EPSS scores for CVEs
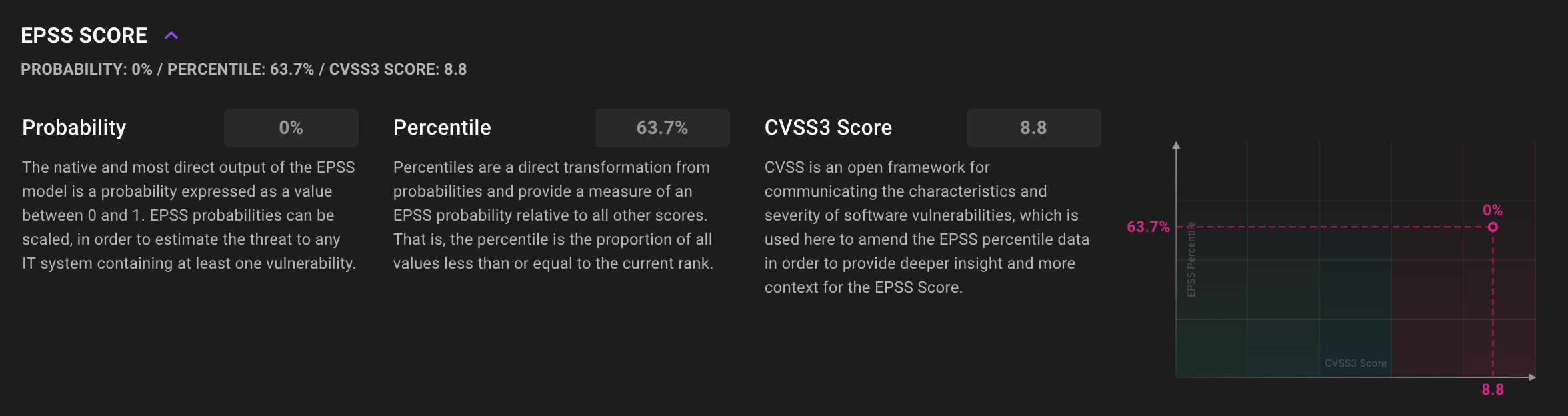
Now that you're done patching all the actively exploited vulnerabilities in your environment, what should you do next? What if you could identify vulnerabilities with a high likelihood of being exploited in the wild in the near future? That's the focus of the Exploit Prediction Scoring System (EPSS). Now Mondoo CVE pages include EPSS data so you can see how likely a vulnerability is to be exploited soon, along with the risk when that occurs. Use this additional data to spend your precious time patching the right systems before attackers hit.
Console light mode
Do you feel like you merely adopted the dark instead of being born into it? Maybe it's time for change. Now you can switch from the Mondoo's Console's default dark mode to a new light mode.
Enable light mode by selecting the sun icon in the toolbar.
With light mode enabled, enjoy a brighter Mondoo!
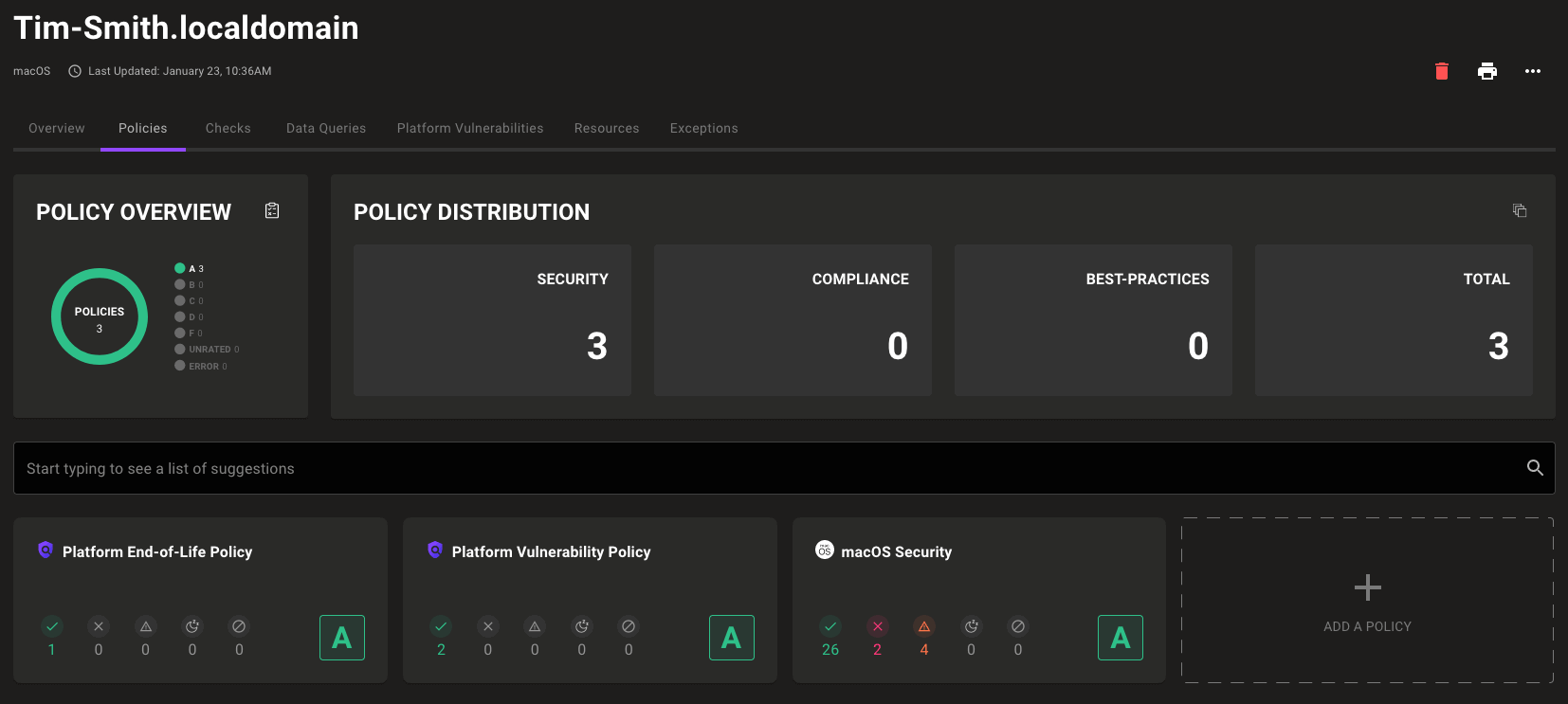
Policy stats on asset policy pages
The asset page's Policy tab now includes overview information summarizing the policies and results for an asset.
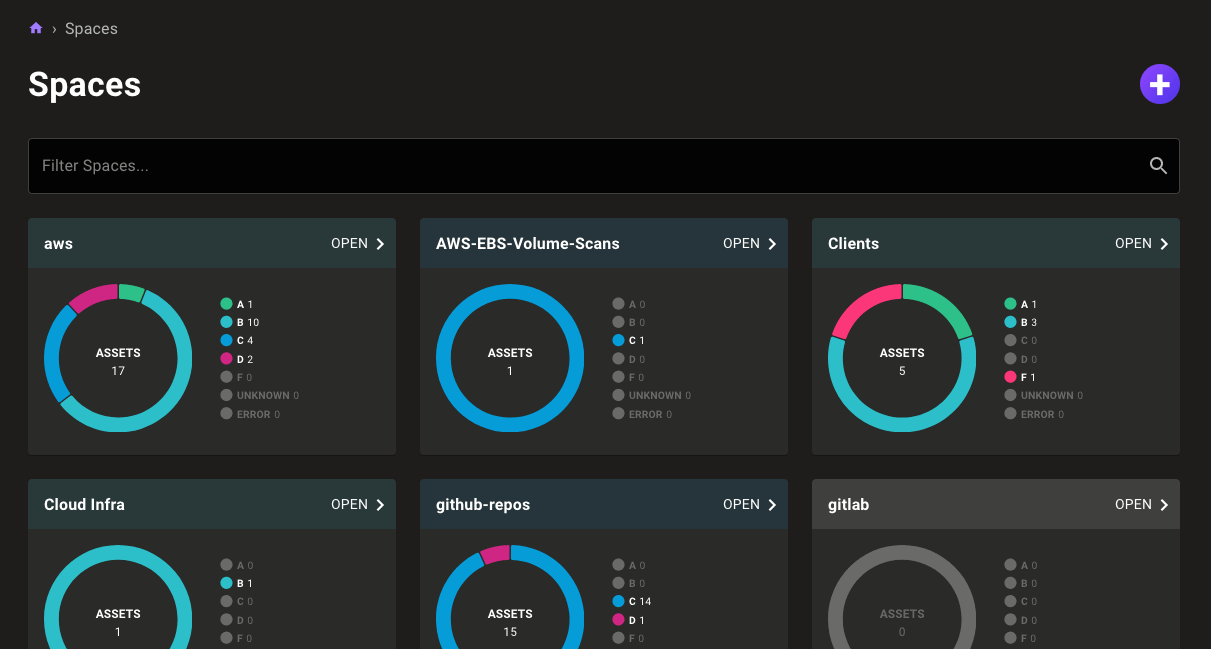
Find your spaces with ease
Are you accumulating spaces as you secure more and more of your infrastructure? Now a space search makes it easy to find the space you need. The Spaces page for an organization also now includes pagination.
Control policies using the CLI
Consider yourself a CLI wizard? You'll be happy to know you can now use the CLI to set how your policies execute on assets. The new cnspec policy commands give you complete control within the CLI:
Usage:
cnspec policy [command]
Available Commands:
delete Delete a policy from the connected space
disable Disables a policy in the connected space
download download a policy to a local bundle file
enable Enables a policy in the connected space
format Apply style formatting to one or more policy bundles
info Show more info about a policy from the connected space
init Create an example policy bundle
lint Lint a policy bundle
list List enabled policies in the connected space
upload Upload a policy to the connected space
🔨 BREAKING CHANGES
As this is a major release of Mondoo's cnspec and cnquery tools, we have made two relatively small breaking changes:
- We removed the
--shareflag in cnspec. To learn about other ways to report scan results, read Report Results. - We renamed
aws-ec2-volumeandaws-ec2-snapshottoaws-ebs-volumeandaws-ebs-snapshotwhen using asset discovery to scan AWS accounts.
🧹 IMPROVEMENTS
Scan performance improvements
New policy fetching and reporting optimizations in Mondoo 10 mean complex scans now execute nearly twice as fast and use 1/3 the network bandwidth as previous 9.x releases.
MQL improvements
New helpers in MQL make it simpler to write and interpret complex security queries.
recurse helper for dicts
The recurse helper makes it easy to extract data from a dict structure made up of mixed value types.
For example, suppose you need to retrieve all users from this JSON data structure:
{
"users": [{ "name": "bob" }],
"owners": {
"admins": [{ "name": "joy", "isOwner": true }]
}
}
Because of the varying data types, finding users in this structure is difficult with traditional mechanisms. You need to understand the data structure and know where to search.
recurse eliminates that difficulty:
jdata.recurse( name != empty )
[
0: {
name: "bob"
}
1: {
isOwner: true
name: "joy"
}
]
You can then map the user names:
jdata.recurse( name != empty ).map(name)
[
0: "bob"
1: "joy"
]
Named arguments in functions
You can set a named argument in a function. This is useful in situations where you can only use one expression (such as with all or one). It also makes the code easier to understand, especially when nesting across multiple objects, as in this example:
users.all(user:
groups.contains(group:
user.uid == group.gid
)
)
in helper for lists of strings
For lists of strings, you can use the in assertion, which is the inverse of contains:
"anya".in(["abel","amos","anya"])
An ideal use for in is to combine it with properties. For example, if you define a property named allowedCiphers, you can assert that a configured cipher is in that list:
sshd.config.ciphers.in( props.allowedCiphers )
Resource improvements
This release includes new resources and resource fields to expose important details for asset inventory and custom security policies.
aws.iam.loginProfile
- New resource with
createdAtfield
aws.rds.snapshot
- New
createdAtfield - New
engineVersionfield - New
portfield
azure.subscription.networkService.securityrule
- Add
directionfield
ms365.exchangeonline
- New
sharedMailboxesfield
ms365.exchangeonline.exoMailbox
- New resource with
identity,user, andexternalDirectoryObjectIdfields
Group vulnerable packages by architecture
Vulnerability advisory pages now group affected packages by architecture for easier discovery and evaluation.
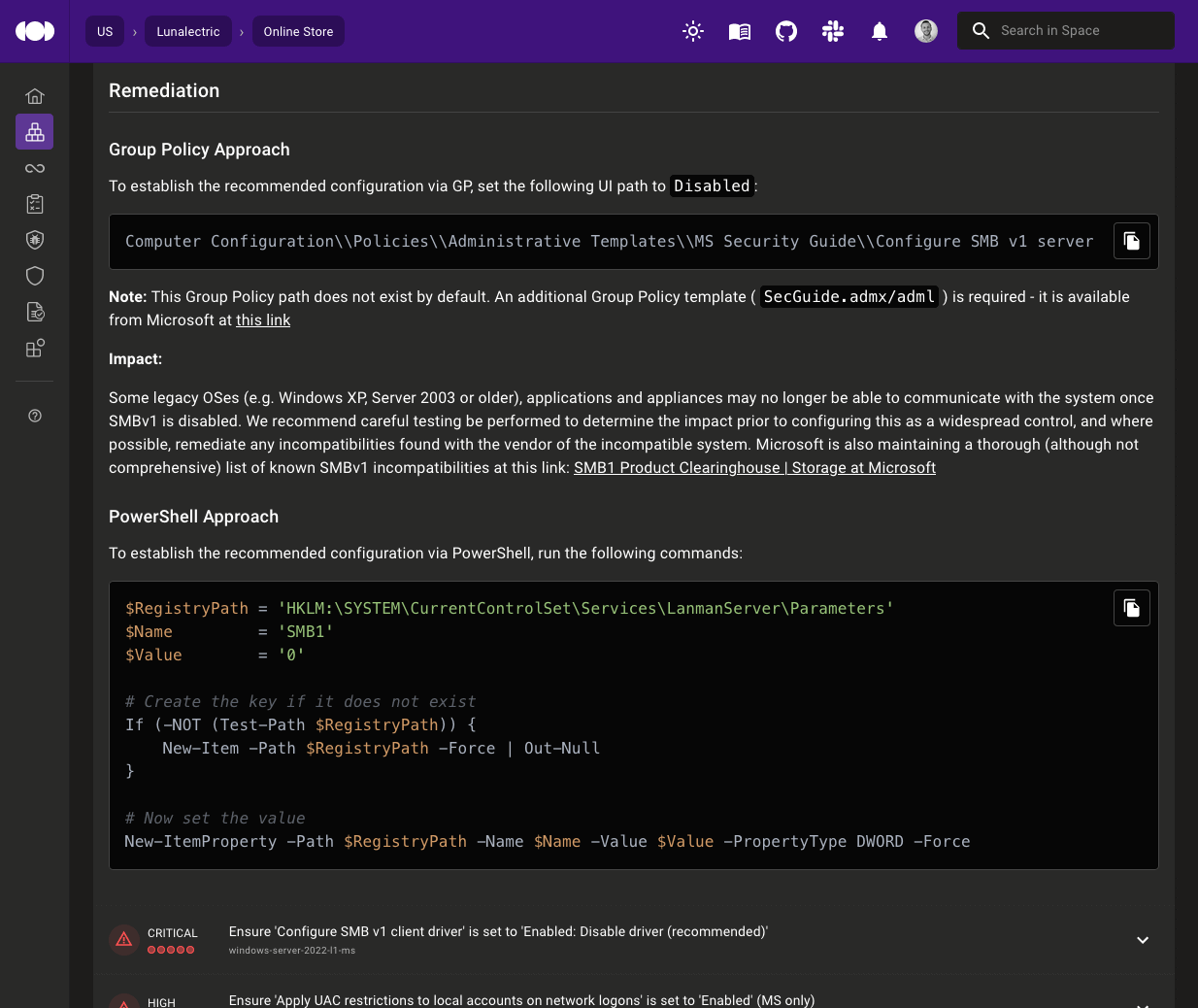
PowerShell remediation steps in Windows policies
Windows policy checks now include PowerShell remediation steps in addition to the existing Group Policy steps, so you can remediate findings whatever way works best for you.
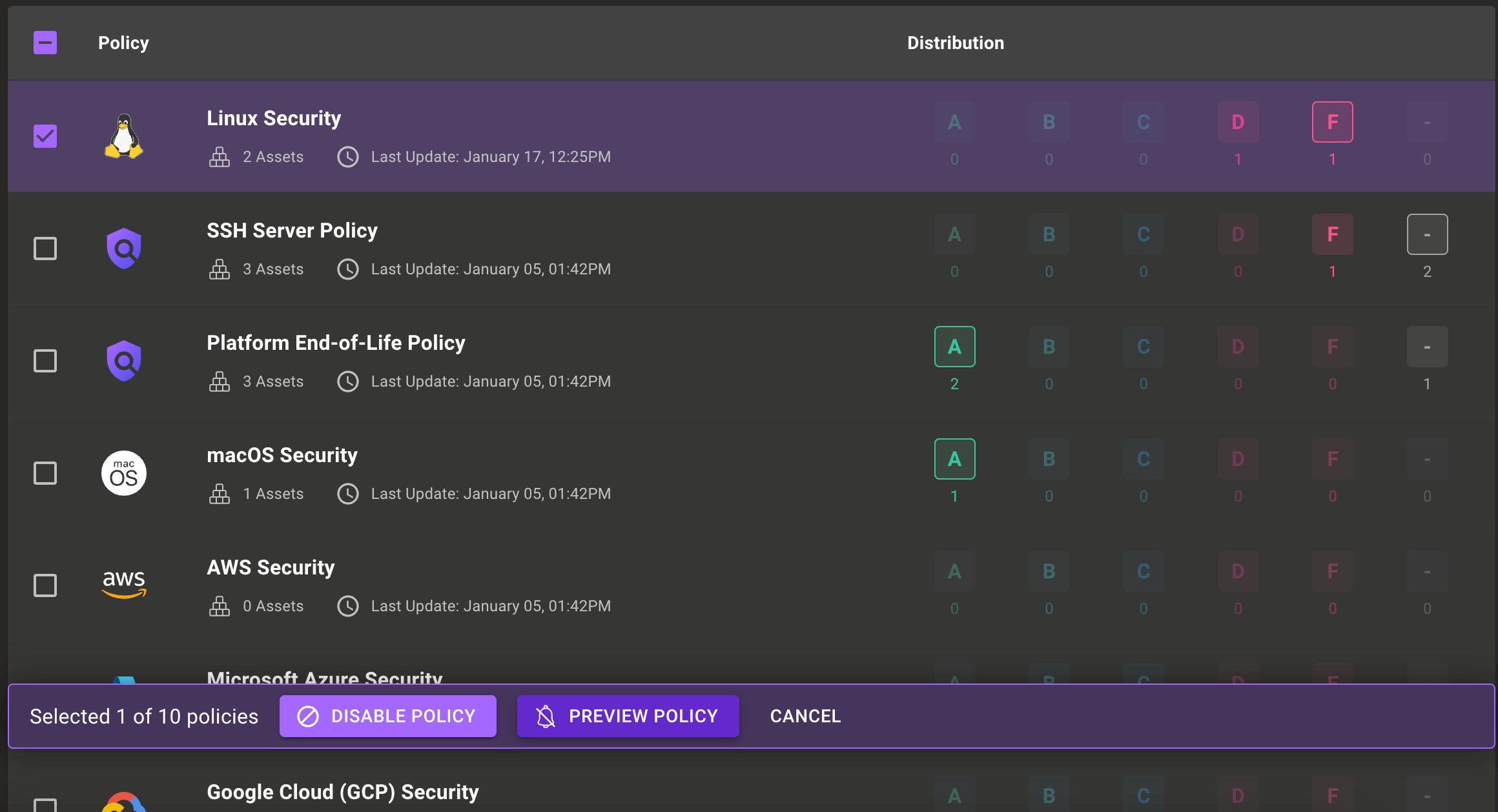
Simplified policy control
You can now change a policy's state directly from the Security Policies page. Now you can enable, disable, or preview policies without having to find them in the Registry.
Control scan as service execution
You can now pass in alternative values to cnspec serve to configure the timer and its splay.
> cnspec serve --help
Start cnspec in background mode.
Usage:
cnspec serve [flags]
Flags:
-h, --help help for serve
--inventory-file string Set the path to the inventory file
--splay int randomize the timer by up to this many minutes (default 60)
--timer int scan interval in minutes (default 60)
Global Flags:
--api-proxy string Set proxy for communications with Mondoo API
--auto-update Enable automatic provider installation and update (default true)
--config string Set config file path (default $HOME/.config/mondoo/mondoo.yml)
--log-level string Set log level: error, warn, info, debug, trace (default "info")
-v, --verbose Enable verbose output
To run cnspec serve from the CLI:
> cnspec serve --timer 30 --splay 30
→ start cnspec background service
→ scan interval is 30 minute(s) with a splay of 30 minutes(s)
If cnspec is running as a service, it is easier to configure the timer and the splay in the configuration:
api_endpoint: https://us.api.mondoo.com
scan_interval:
timer: 5
splay: 10
auto_update: true
Custom provider paths
Define a custom path to store cnspec and cnquery providers with the new PROVIDERS_PATH variable. Set this variable in your shell profile or change the path one time directly on the CLI:
PROVIDERS_PATH=$PWD/.providers cnquery providers install os
Updated Linux EOL dates
We've updated many Linux distribution EOL dates based on vendor timeline updates:
- Extend EOL date of EuroLinux 9 to June 30, 2032
- Extend EOL date of Fedora 37 to December 5, 2023
- Extend EOL date of openSUSE Linux 15.4 to December 7, 2023
- Extend EOL date of Oracle Linux 7 to December 1, 2024
- Extend EOL date of Oracle Linux 9 to December 30, 2032
- Extend EOL date of Ubuntu Linux 23.04 to January 20, 2024
- Fix the EOL date of Red Hat Enterprise Linux 7 to be August 6, 2019
Apple model detection
Asset platform information now includes the human-friendly form of the Mac model designation, including the year of release, so you can more easily understand scanned IT assets.
🐛 BUG FIXES AND UPDATES
- Do not show unknown assets in the affected assets page.
- Immediately refresh the page after creating or removing an exception in Compliance Hub.
- Improve listing of CVEs and pagination to ensure all CVEs are always displayed.
- Respect the
--log-levelcommand line flag within provider plugins. - Fix
auditpolresource failures on non-English Windows systems. - Improve content alignment on the Compliance Hub frameworks page.
- Support vulnerable package data on the EndeavourOS Linux distribution.
- Fix technology naming and images in the weekly space overview email.
- Fix alignment of compliance framework tiles.
- Fix the exception creation dialog not always closing after creating an exception.
- Do not fail on time parsing errors.
- Fix failures shutting down providers in some scenarios.
- Fix fetching of the ID for Azure SQL Server firewall rules.
- Fix an error in the
attributesfield of theaws.elb.classicLoadBalancersresource when fetching classic ELBs. - Add an error message when using the
aws.elb.loadbalancerresource without a load balancer type argument. - Add an error message when using the
aws.applicationAutoscalingresource without a namespace argument. - Show managed clients (if present) in the Integrations section of the sidebar.
- Handle deprecated configurations in the Mondoo Kubernetes Operator.
- Resolve errors running the
files.findresource on containers. - Ensure any provider can run resources in the OS provider.
- Improve CVSS score rendering.
