Get this release: Installation Docs | Package Downloads | Docker Container
🎉 NEW FEATURES
Continuous OCI scanning
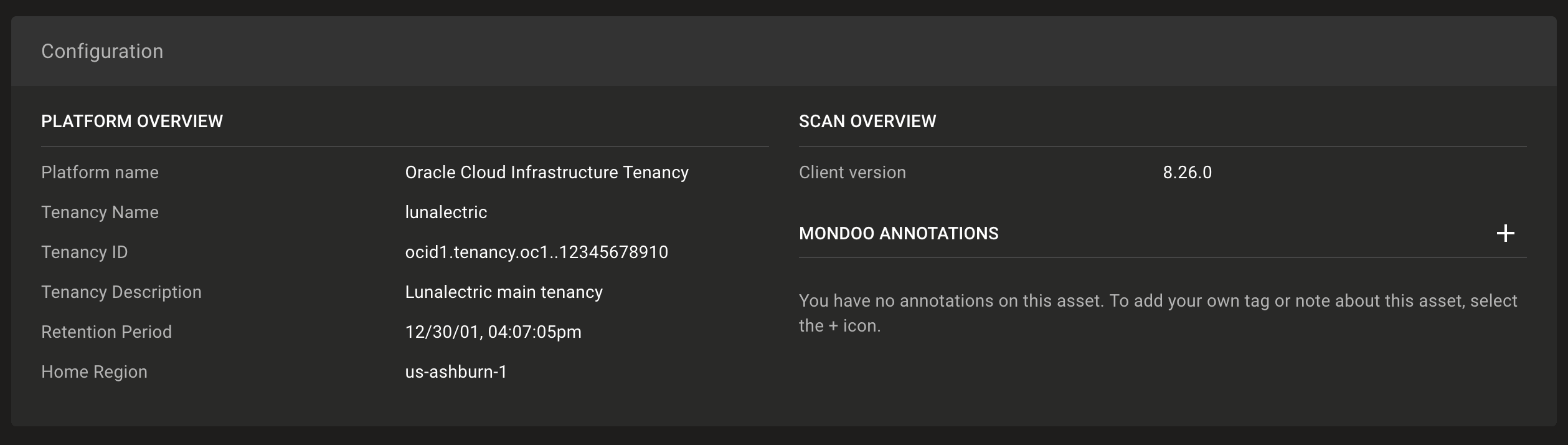
Continuously scan your Oracle Cloud Infrastructure (OCI) services, all without an agent installation. Set up continuous scanning using your existing local OCI configuration file, and we'll do the rest with full infrastructure scans every 4 hours.
Organization-wide service accounts
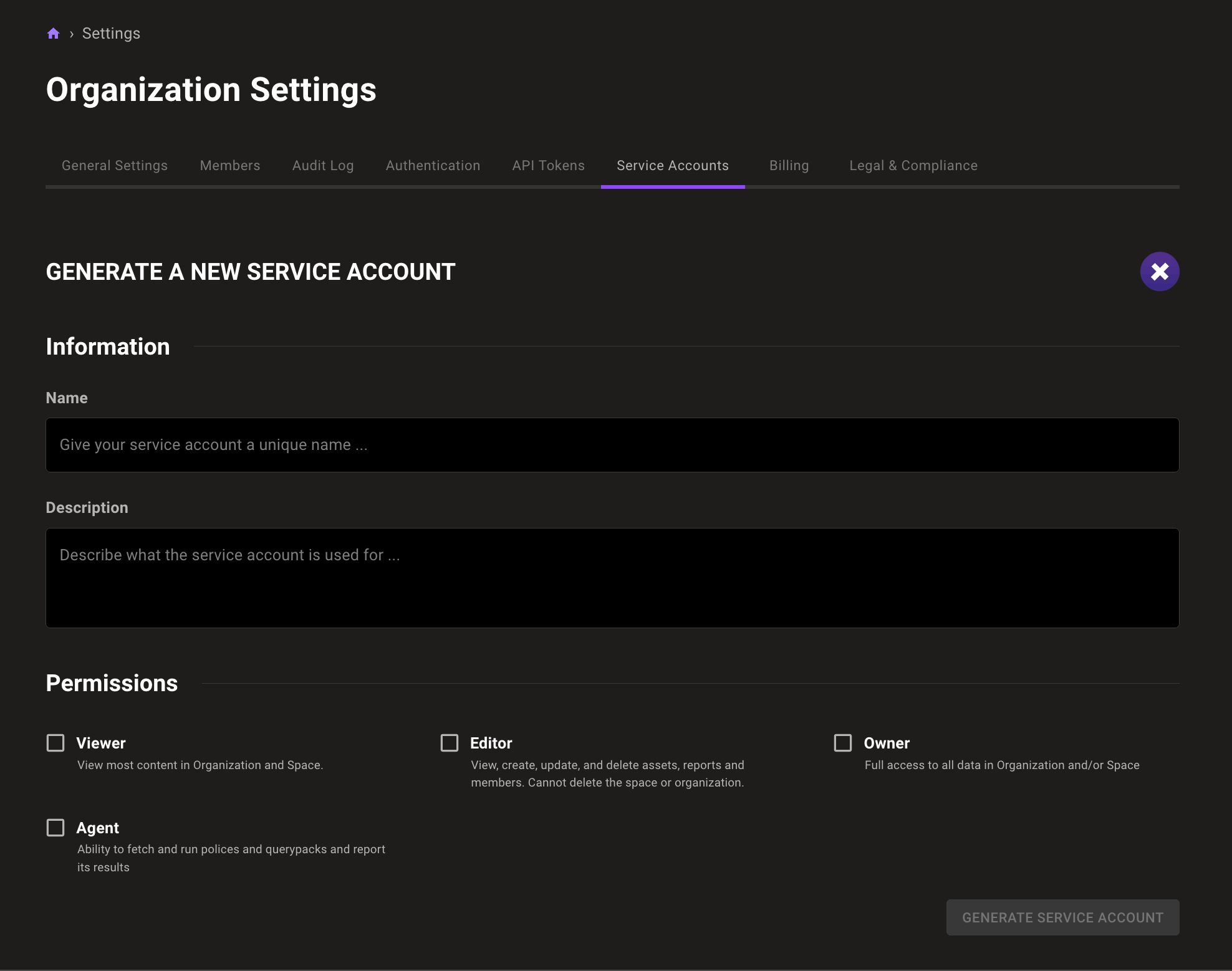
Need a service account for all your spaces? Now you can create one with organization-wide service accounts, available on the organization settings page. Create new accounts or manage existing accounts with an improved UI to help with cross-team collaboration.
Scan AWS using assumed roles
Now you can scan your AWS infrastructure by assuming an AWS role:
cnspec scan aws --option role-arn=ROLEARN
cnspec scan aws --option role-arn=ROLEARN --option external-id=EXTERNALID
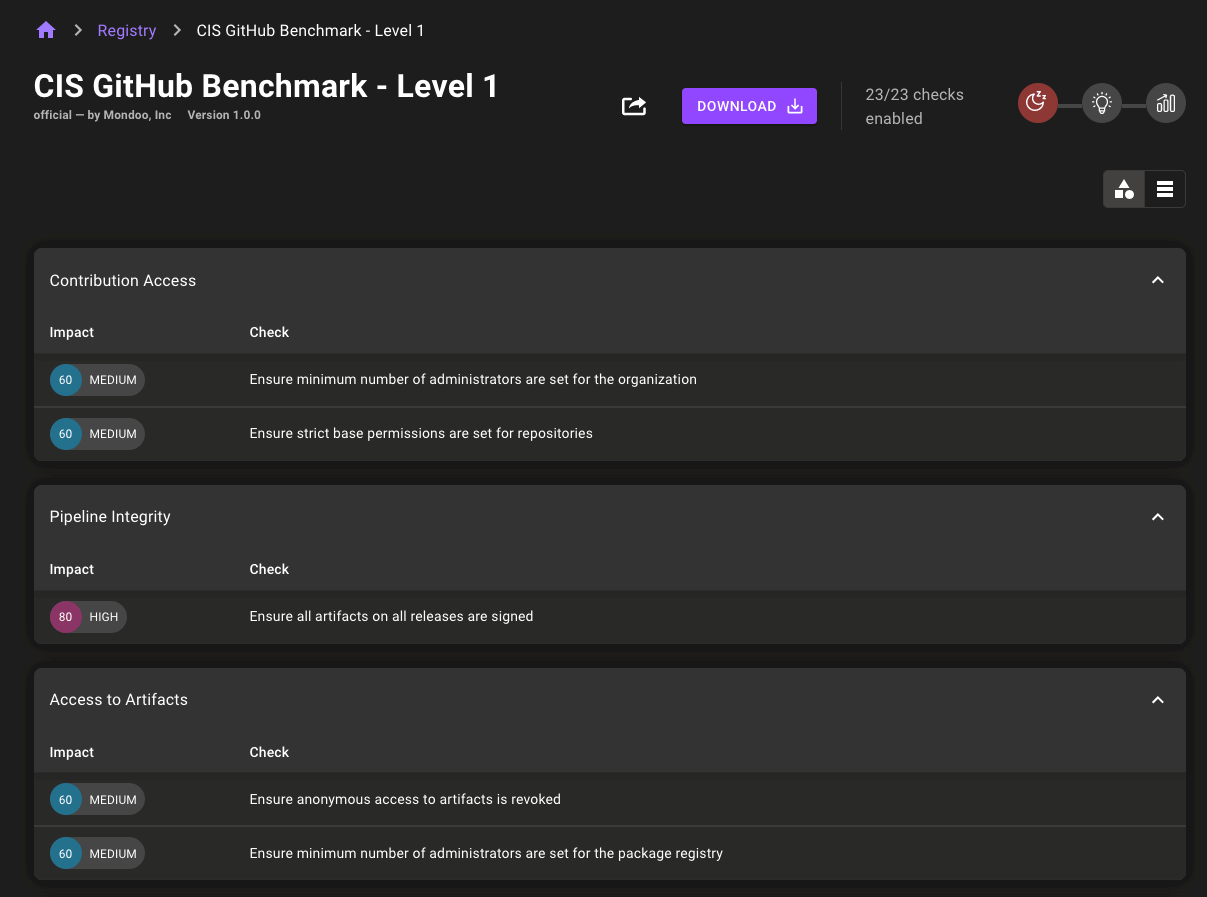
CIS GitHub Benchmark policy
Secure your GitHub organizations and repos with Mondoo and the new CIS GitHub Benchmark 1.0 policy.
🧹 IMPROVEMENTS
4.5x Windows speedup with registry improvements
What's better than improvements to the Windows registrykey resource? How about improvements that also make CIS benchmark scans on Windows nearly 4.5 times faster, all while using 25% less memory? It seems like a tall order, but we've entirely reworked registrykey under the hood to give you some huge new benefits Mondoo-wide.
First off, there's a whole new way to interact with registry data. The registrykey resource includes a new items property that greatly improves how data is returned (versus the now deprecated properties field). This new format allows us to return more than just string values, including new binary and multi-line registry value support.
The existing registrykey.properties data that returned just key/value data:
cnspec> registrykey(path: 'HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\LanManServer\Parameters').properties
registrykey.properties: {
EnableAuthenticateUserSharing: "0"
Guid: ""
NullSessionPipes: ""
ServiceDll: "%SystemRoot%\\system32\\srvsvc.dll"
ServiceDllUnloadOnStop: "1"
autodisconnect: "15"
enableforcedlogoff: "1"
enablesecuritysignature: "0"
requiresecuritysignature: "0"
restrictnullsessaccess: "1"
}
With registrykey.items you'll get back a wealth of data on each registry key that looks more familiar to regedit users:
cnspec> registrykey(path: 'HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\LanManServer\Parameters').items { * }
registrykey.items: [
0: {
value: "0"
type: "dword"
name: "EnableAuthenticateUserSharing"
path: "HKEY_LOCAL_MACHINE\\SYSTEM\\CurrentControlSet\\Services\\LanManServer\\Parameters"
data: 0
exists: true
}
1: {
value: ""
type: "multistring"
name: "NullSessionPipes"
path: "HKEY_LOCAL_MACHINE\\SYSTEM\\CurrentControlSet\\Services\\LanManServer\\Parameters"
data: [
0: ""
]
exists: true
}
2: {
value: "%SystemRoot%\\system32\\srvsvc.dll"
type: "expandstring"
name: "ServiceDll"
path: "HKEY_LOCAL_MACHINE\\SYSTEM\\CurrentControlSet\\Services\\LanManServer\\Parameters"
data: "%SystemRoot%\\system32\\srvsvc.dll"
exists: true
}
3: {
value: "1"
type: "dword"
name: "ServiceDllUnloadOnStop"
path: "HKEY_LOCAL_MACHINE\\SYSTEM\\CurrentControlSet\\Services\\LanManServer\\Parameters"
data: 1
exists: true
}
...
What about those under-the-hood improvements? registrykey is entirely rewritten to natively query the Windows registry directly instead of going through PowerShell. This increases performance, reduces memory usage, and works better with antivirus systems that could block Mondoo's use of PowerShell.
Execution of the CIS Windows 2022 Level 1 Member Benchmarks policy running on an AWS t2.large instance:
| Mondoo Release | Execution Time | Memory Usage |
|---|
| 8.18 | 1 minute 56 seconds | 140.19 MB |
| 8.19 | 21 seconds | 104 MB |
Updated CIS AKS Benchmark policy
Both the CIS AKS Benchmark policies are updated from 1.2.0 to 1.3.0. These new versions improve audit/remediation steps and remove checks for the deprecated --protect-kernel-defaults kubelet flag.
🐛 BUG FIXES AND UPDATES
- Add missing impact scores to CIS GKE policy.
- Support policy variants in query packs.
- Improve check titles in Mondoo inventory packs.
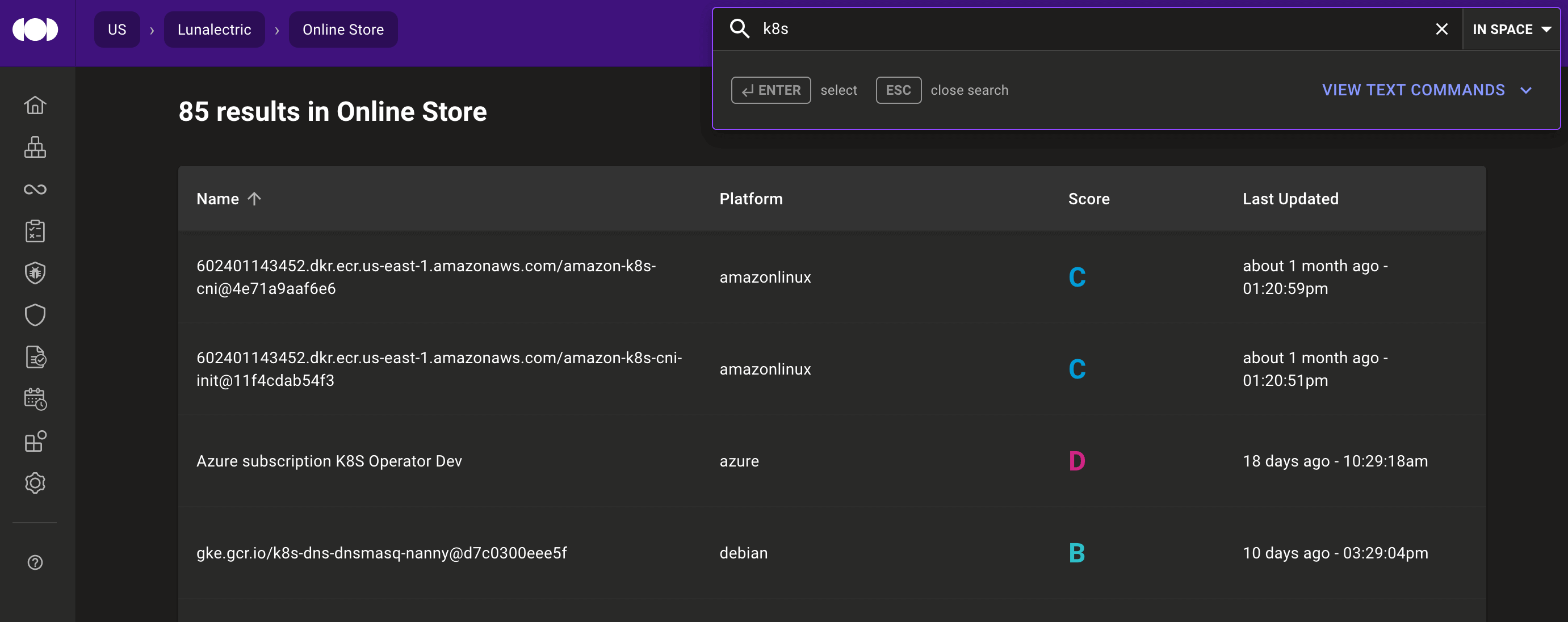
- Improve search results in the security registry.
- Resolve errors loading CI scan results.
- Fix errors executing local policies containing variants.
- Display the create time for export integrations.
- Fix incorrect EOL date for Windows 2016.
- Fix failures when setting plans in Risk Actions.
- Resolve occasional failures logging in using Safari.
- Fix a failure in certain uses of
files.find in policies.