Manually Set Up Azure Continuous Scanning
Are you sure you want to set up Azure manually?
Mondoo offers two approaches to setting up an integration for continuous Azure scanning: automated and manual.
Follow the manual setup described below only in these rare cases:
-
You want to integrate Mondoo with all subscriptions in a management group
-
You use the legacy access policy permission model for your key vaults (instead of RBAC)
-
Your Azure environment is unusually large
All other users can follow the automatic Azure integration setup, which takes a fraction of the time.
Prerequisites
Before you manually integrate Microsoft Azure with Mondoo, be sure you have:
-
A Mondoo account with Editor or Owner permissions for the space in which you want to add the integration.
-
An Azure account with an active subscription and permission to manage applications in Microsoft Entra ID (formerly Active Directory). Any of these Entra built-in roles include the required permissions:
In the Azure portal you can see what roles your user account has: Go to Microsoft Entra ID > Users > (your user account) > Assigned roles.
-
Command-line access to Azure using either:
-
The Azure CLI in either the Linux shell or the macOS shell
Install the Azure CLI.
Log into the Azure CLI from PowerShell or a Linux/macOS CLI by entering:
az loginAzure opens your web browser and prompts you to log in. After you do so, you can return to the CLI.
Register and grant permissions to an Azure app
Like any service that integrates with Azure, Mondoo must have Microsoft Entra ID app registration in your Azure tenant. To learn more about creating a new app registration and service principal, read App registration, app objects, and service principals in the Azure documentation.
Registering Mondoo with Entra establishes a trust relationship between Mondoo and the Microsoft identity platform. The trust is unidirectional: Mondoo trusts the Microsoft identity platform, and not the other way around. The Entra app registration creates a service principal to represent Mondoo in any tenants and subscriptions.
The app registration you create gives Mondoo read-only access to Azure resources, web apps, key vault, and Graph API.
To configure your Azure resources, you must:
Step A: Register an app with Microsoft Entra ID and create a service principal
Step B: Grant permissions to access Microsoft Graph (API permissions)
Step C: Grant required READ permissions to the app
Step D: Grant web app READ permissions to the app
Step E: Grant permissions to access Azure key vault
Step F: Upload the application certificate
Step A: Register an app with Microsoft Entra ID and create a service principal
Like any service that integrates with Azure, Mondoo must have an app registration. To learn more about creating a new app registration, read App registration, app objects, and service principals in the Azure documentation.
-
Log into the Azure portal as a global administrator, application administrator or cloud application administrator.
-
Find and select Microsoft Entra ID.
-
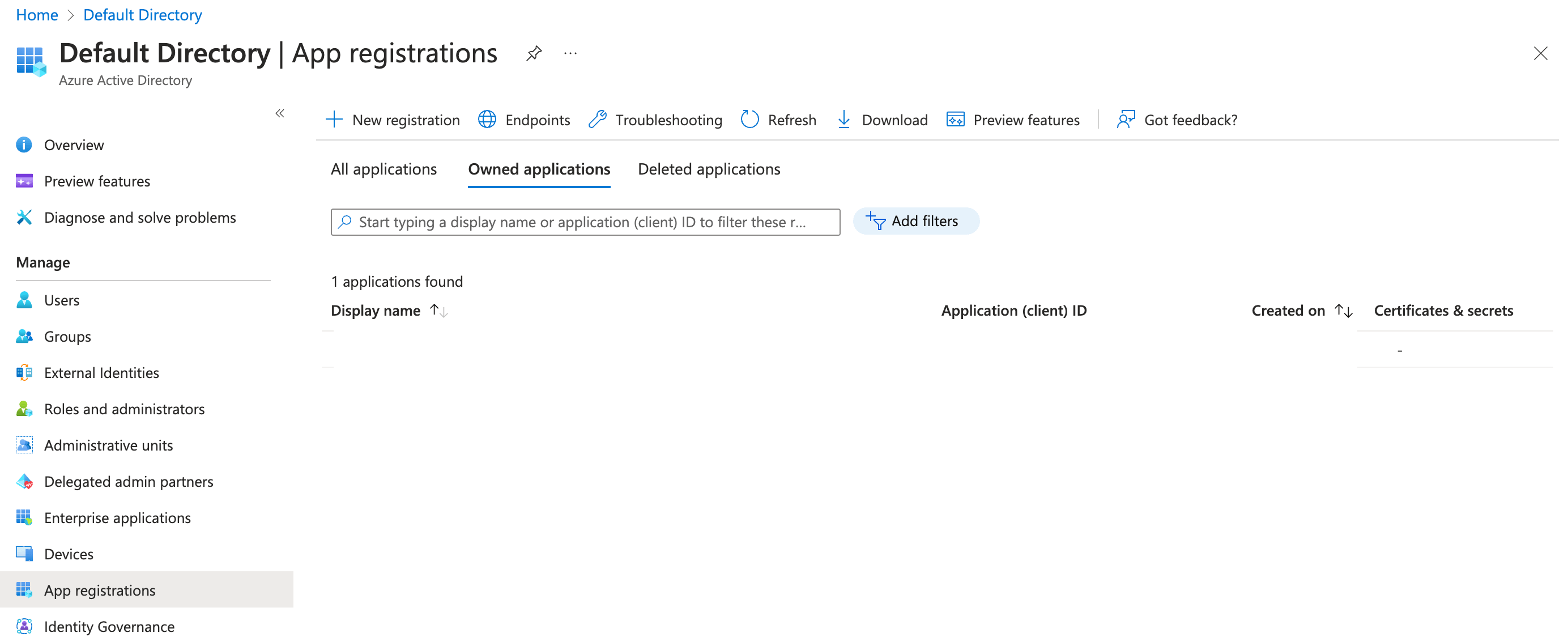
In the navigation sidebar, select App registrations.
-
Select + New registration.
-
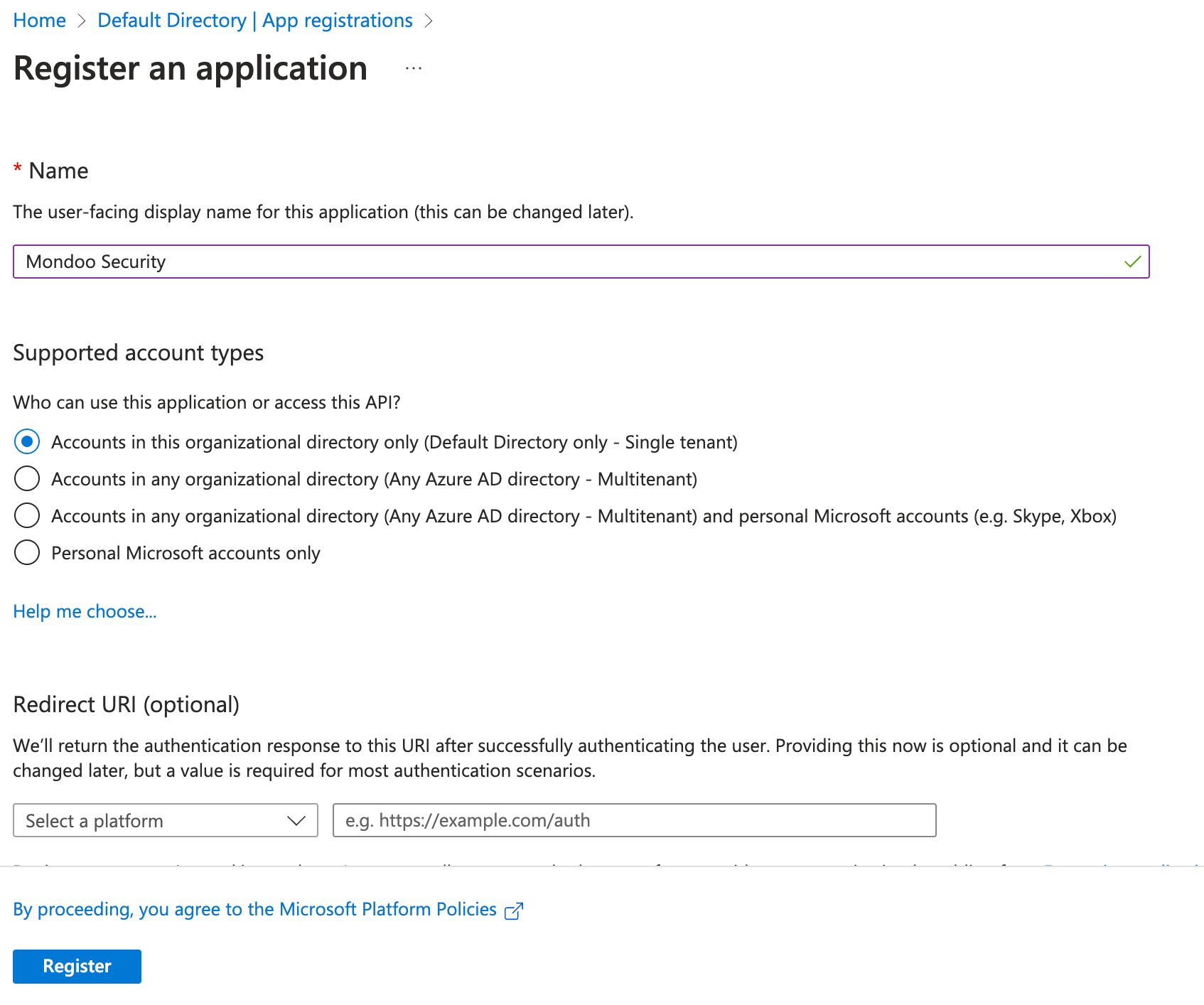
Enter an application name (such as
mondoo-security) and select Accounts in this organizational directory only as the supported account type. Mondoo does not require an application redirect URI. -
Select the Register button.
Microsoft creates the application ID and displays it in the application registration overview.
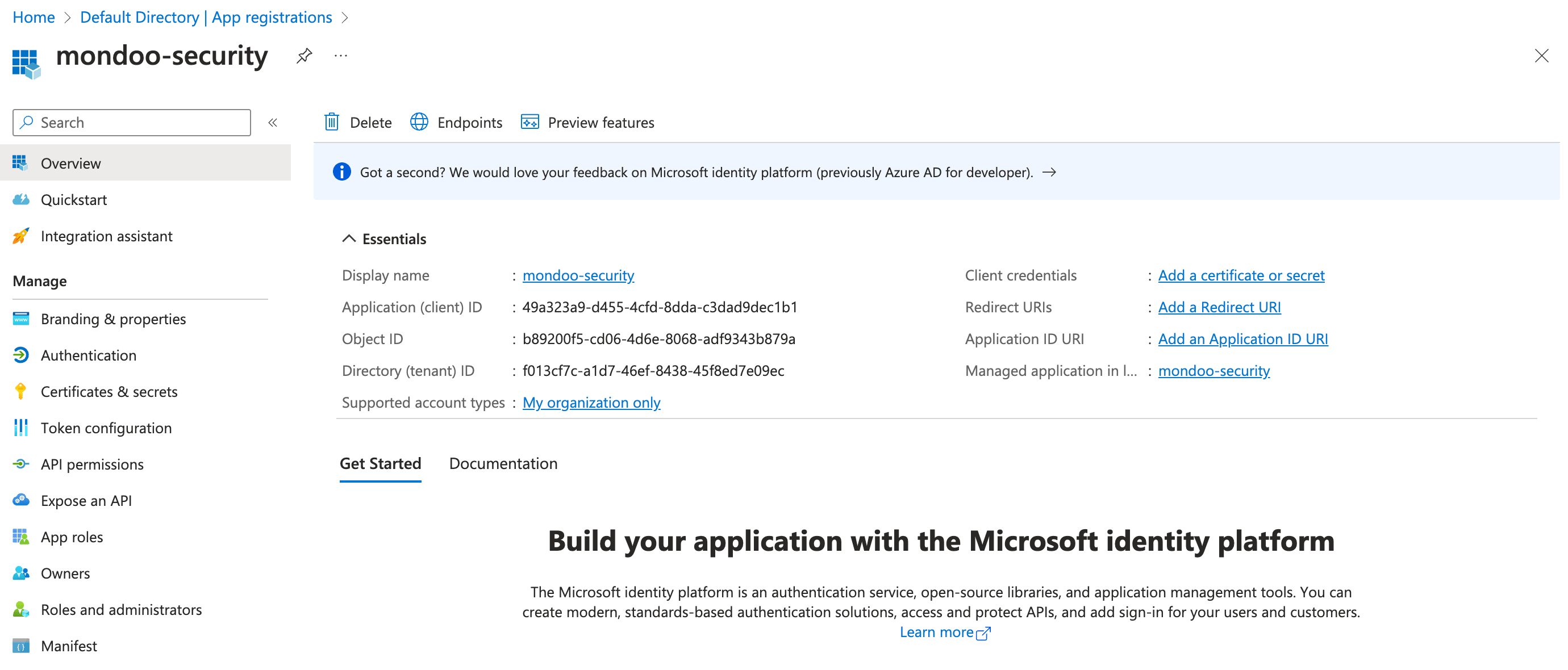
Keep the page open as you continue to the next step.
Step B: Grant permissions to access Microsoft Graph (API permissions)
-
In the navigation sidebar, select API permissions.
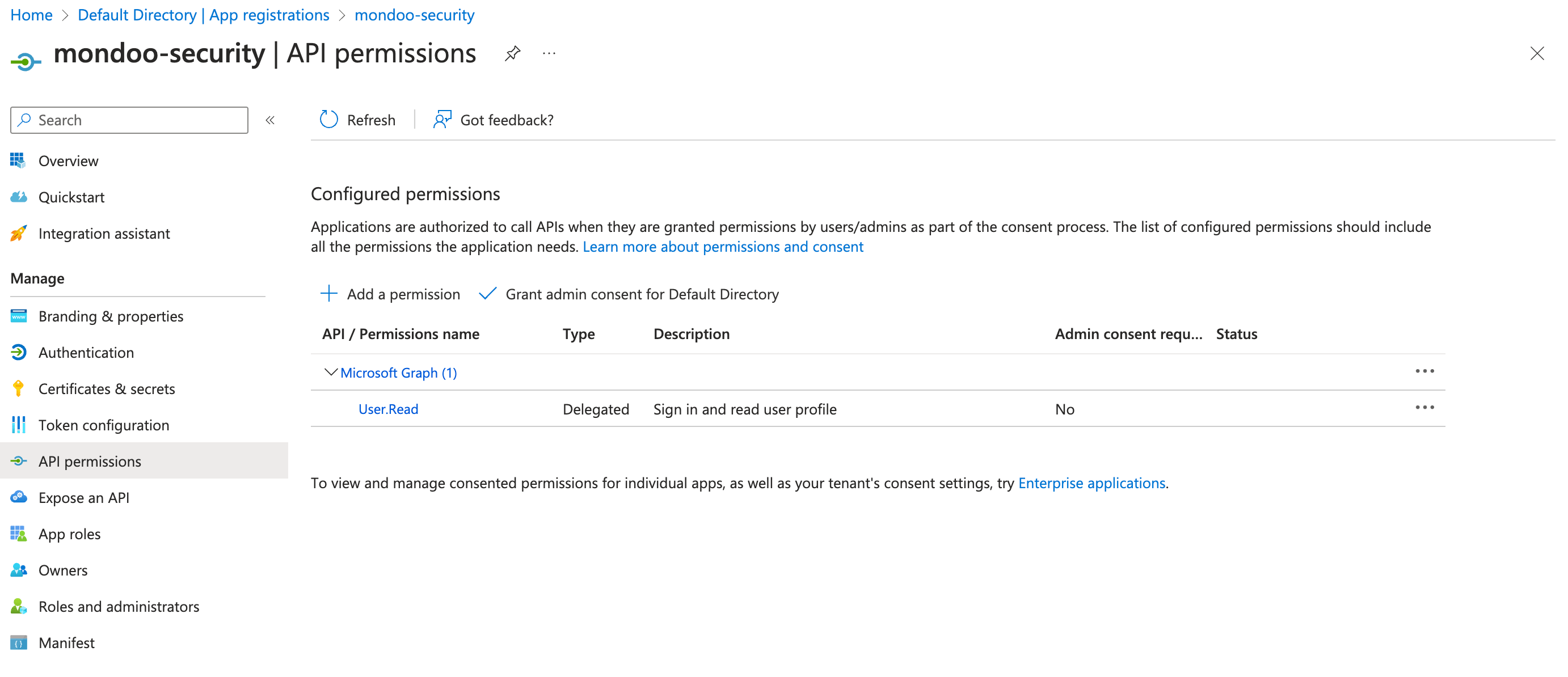
By default, Microsoft grants your new application
User.Readpermission for Microsoft Graph. It's not required for Mondoo, so you can remove it. -
Select + Add a permission.
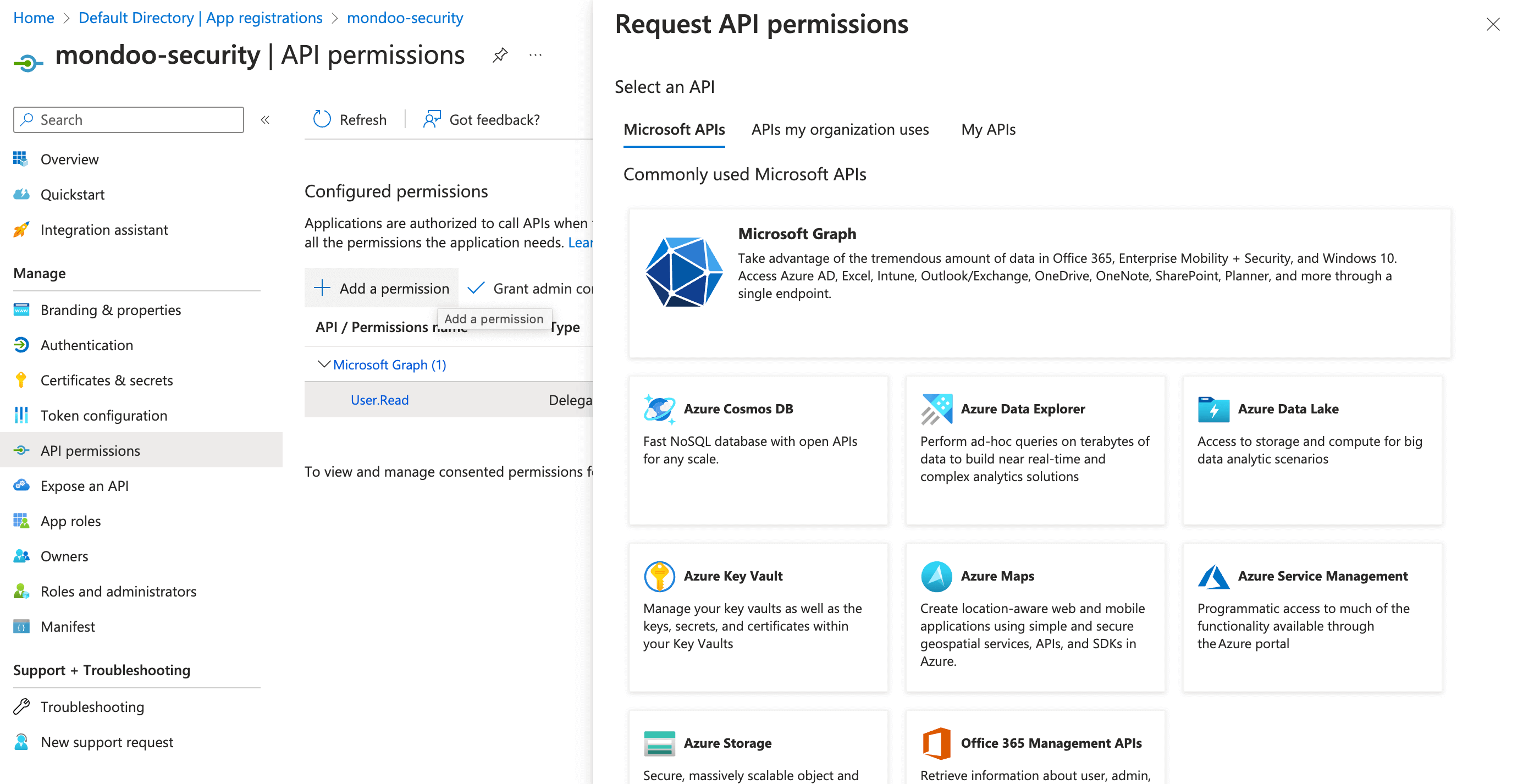
-
From the list of Commonly used Microsoft APIs, select Microsoft Graph.
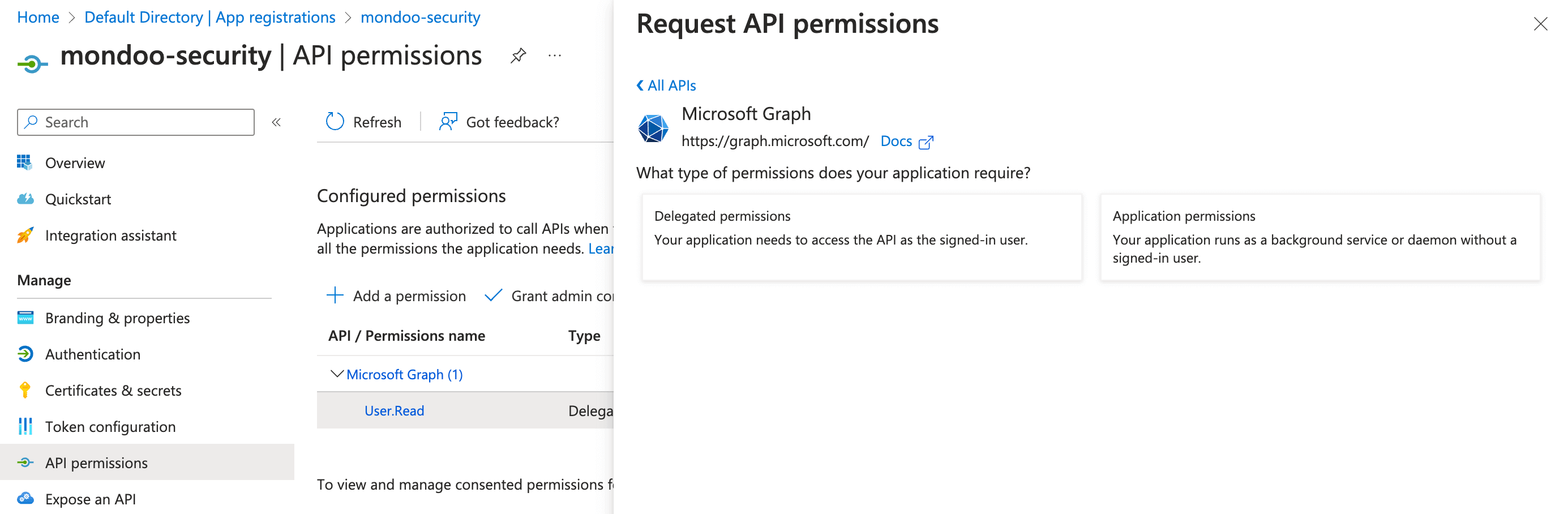
-
Because Mondoo acts as a service, select Application permissions.
-
Select expand all to see all permissions. Then select the required API permissions:
| Microsoft Graph | Type | Description |
|---|---|---|
| Application.Read.All | Application | Read all applications |
| Domain.Read.All | Application | Read domains |
| IdentityProvider.Read.All | Application | Read identity providers |
| IdentityRiskEvent.Read.All | Application | Read all identity risk event information |
| IdentityRiskyUser.Read.All | Application | Read all identity risky user information |
| Policy.Read.All | Application | Read your organization's policies |
| Policy.Read.ConditionalAccess | Application | Read your organization's conditional access policies |
| Policy.Read.PermissionGrant | Application | Read consent and permission grant policies |
| RoleManagement.Read.All | Application | Read role management data for all RBAC providers |
| SecurityActions.Read.All | Application | Read your organization's security actions |
| SecurityEvents.Read.All | Application | Read your organization's security events |
| ThreatAssessment.Read.All | Application | Read threat assessment requests |
| ThreatIndicators.Read.All | Application | Read all threat indicators |
-
Select the Add permissions button.
-
To complete the process, select Grant admin consent for (your tenant name) and select the Yes button to confirm.
Step C: Grant required READ permissions to the app
These steps guide you through setting the READ permissions and "Key Vault Reader" permissions for a single subscription. If you want to scan several subscriptions, you must repeat the same steps for each subscription.
If you want Mondoo to monitor an entire management group, you can perform these steps at the management group level: Search for "management groups" in the Azure portal and then select the management group you want to monitor. To monitor the entire directory, select the tenant root group.
Set subscription-level permissions for your new app registration:
-
From the Azure portal home, select Subscriptions.
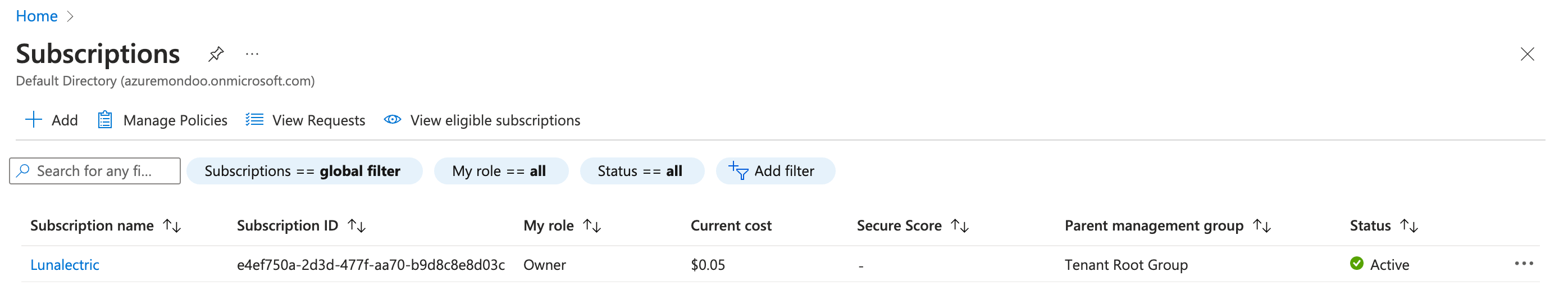
-
Select the subscription you want to integrate with Mondoo.
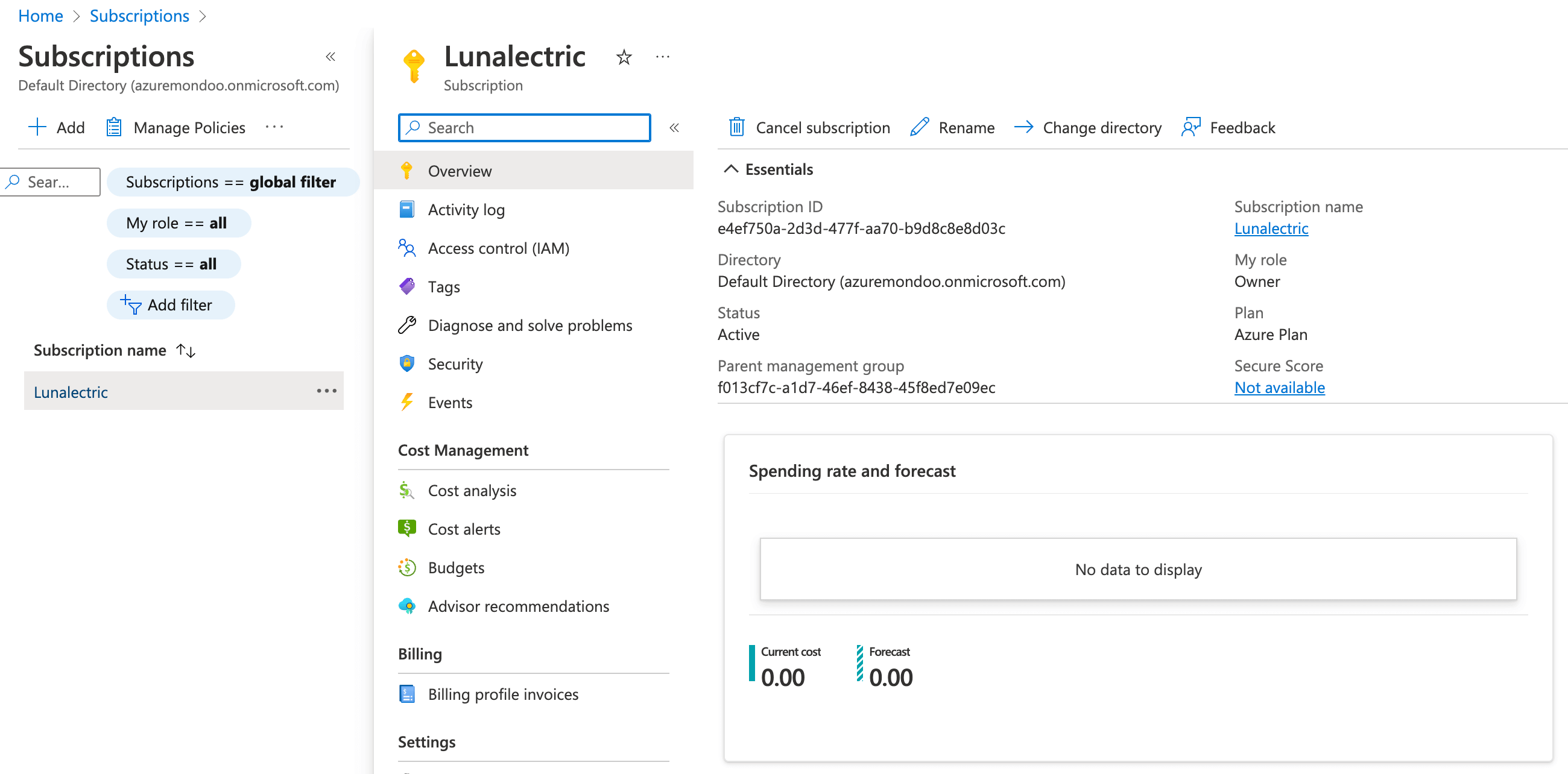
-
In the sidebar under the subscription name, select Access control (IAM).
-
Select the Add role assignment button.
-
Select the Reader role and then select the Members tab (or Next button).
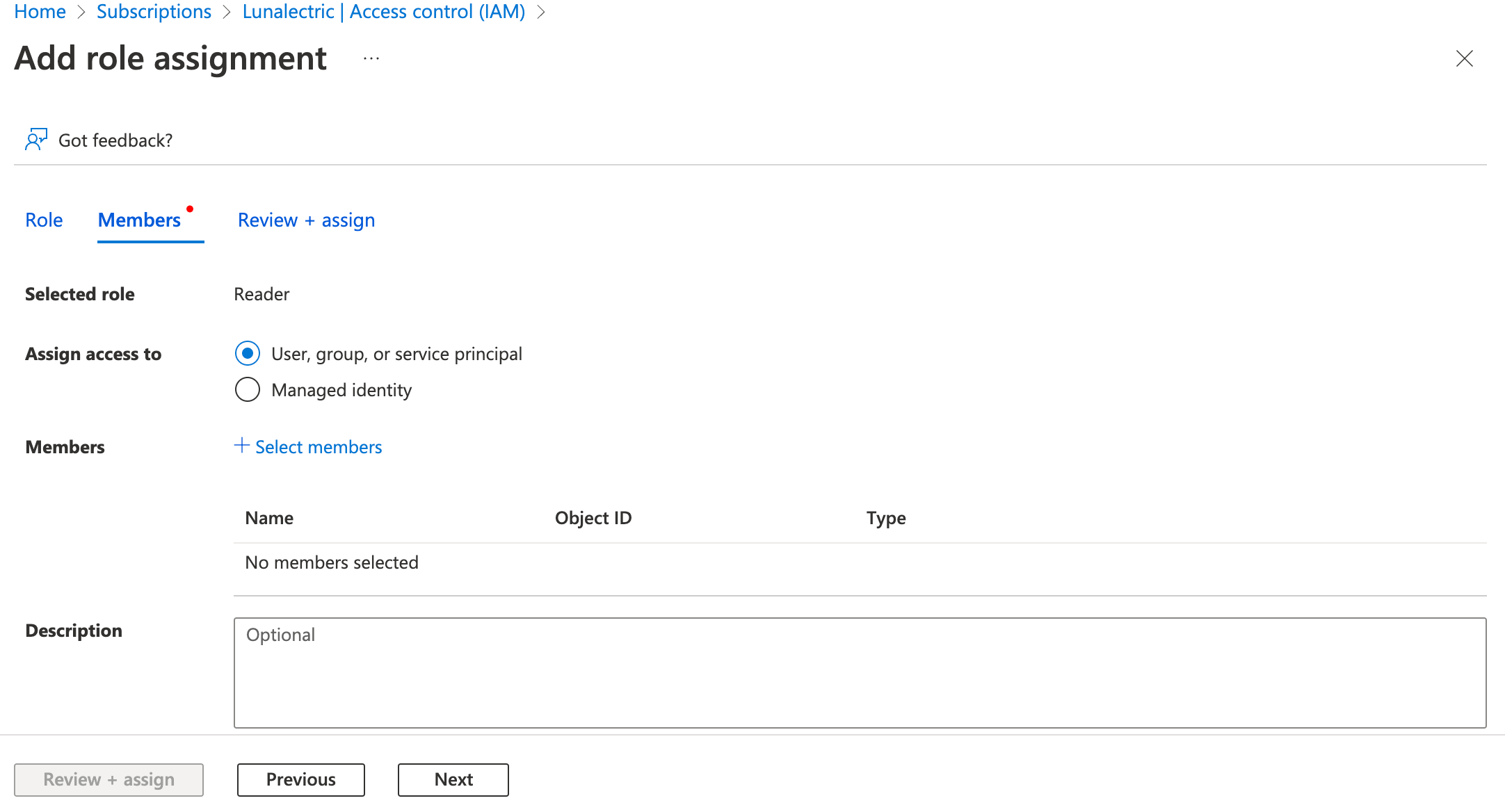
-
Select + Select Members, find and select your Mondoo app registration, and select the Select button.
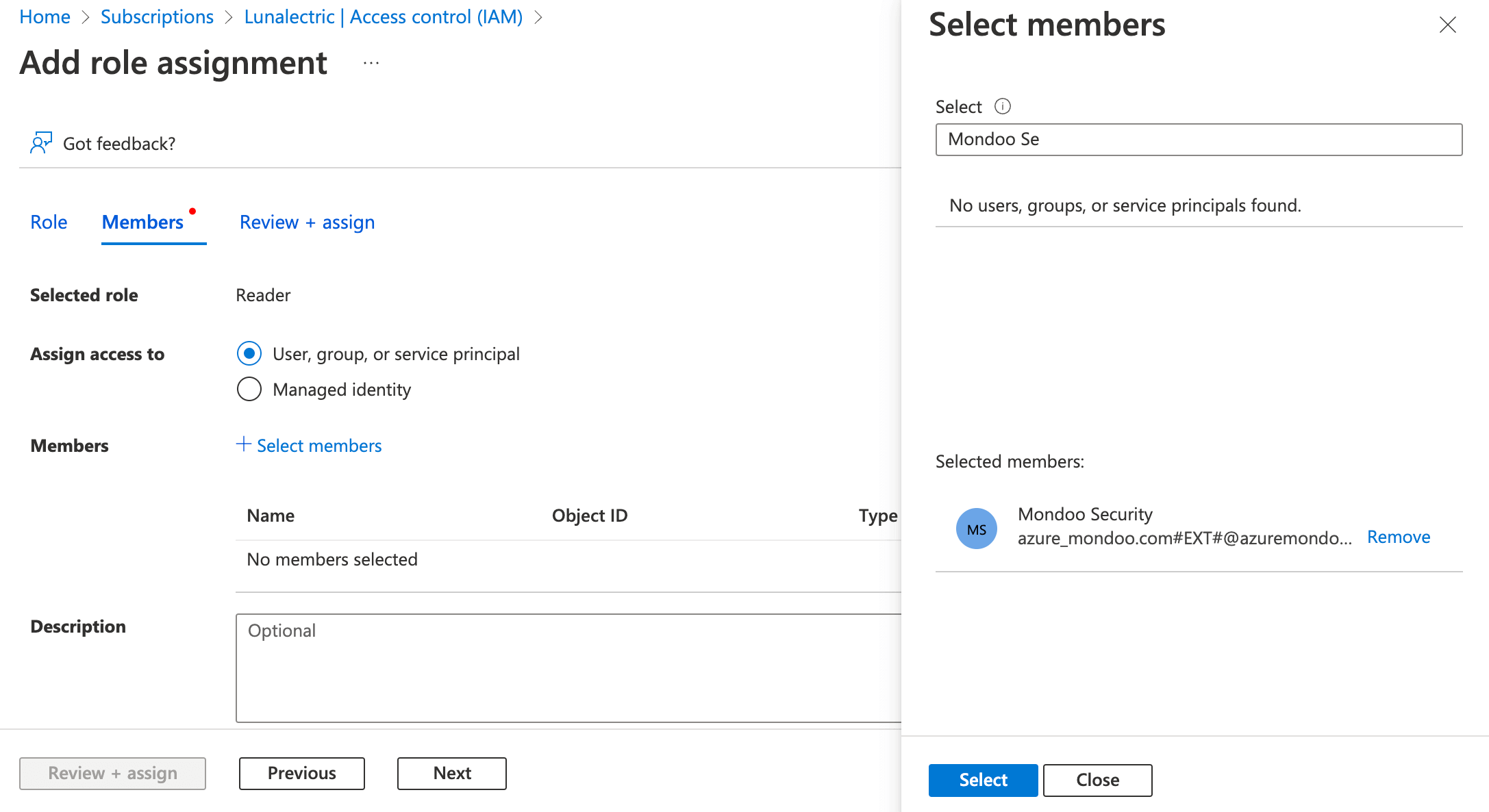
-
Select the Review + assign button (or Next button), check your work, and then select the Review + assign button again to assign the Reader role to your Mondoo app registration.
-
Repeat steps 4-7 and this time choose the "Key Vault Reader" role in step 5.
Keep the Access control (IAM) page open as you continue to Step D.
Step D: Grant web app READ permissions to the app
Grant web app permissions by creating a custom RBAC role for Mondoo and assigning the custom role to your new app registration.
-
In the sidebar under the subscription name, select Overview.
-
Copy the subscription ID and save it somewhere handy.
-
In the sidebar under the subscription name, select Access control (IAM).
-
On the subscription's Access control (IAM) page toolbar, select + Add and select Add custom role.
-
Name the new role
mondoo-role, provide a description, and then select the JSON tab. -
On the JSON tab, select the Edit button and delete all existing content from the edit box.
-
Copy this JSON content and paste it into the edit box on the JSON tab:
{
"Name": "mondoo-role",
"IsCustom": true,
"description": "Custom role for Mondoo integration",
"assignableScopes": [
"/subscriptions/YOUR-SUBSCRIPTION-ID"
],
"actions": [
"Microsoft.Authorization/*/read",
"Microsoft.ResourceHealth/availabilityStatuses/read",
"Microsoft.Insights/alertRules/*",
"Microsoft.Resources/deployments/*",
"Microsoft.Resources/subscriptions/resourceGroups/read",
"Microsoft.Support/*",
"Microsoft.Web/listSitesAssignedToHostName/read",
"Microsoft.Web/serverFarms/read",
"Microsoft.Web/sites/config/read",
"Microsoft.Web/sites/config/web/appsettings/read",
"Microsoft.Web/sites/config/web/connectionstrings/read",
"Microsoft.Web/sites/config/appsettings/read",
"Microsoft.web/sites/config/snapshots/read",
"Microsoft.Web/sites/config/list/action",
"Microsoft.Web/sites/read",
"Microsoft.KeyVault/checkNameAvailability/read",
"Microsoft.KeyVault/deletedVaults/read",
"Microsoft.KeyVault/locations/*/read",
"Microsoft.KeyVault/vaults/*/read",
"Microsoft.KeyVault/operations/read",
"Microsoft.Compute/virtualMachines/runCommands/read",
"Microsoft.Compute/virtualMachines/runCommands/write",
"Microsoft.Compute/virtualMachines/runCommand/action"
],
"notActions": [],
"dataActions": [
"Microsoft.KeyVault/vaults/*/read",
"Microsoft.KeyVault/vaults/secrets/readMetadata/action"
],
"notDataActions": []
}To integrate with more than one subscription, list them:
"assignableScopes": [
"/subscriptions/YOUR-SUBSCRIPTION-ID-1"
"/subscriptions/YOUR-SUBSCRIPTION-ID-2"
"/subscriptions/YOUR-SUBSCRIPTION-ID-3"
]To integrate at the management group level, copy this JSON content and paste it into the edit box on the JSON tab:
{
"properties": {
"roleName": "mondoo-role",
"description": "Custom role for Mondoo integration",
"assignableScopes": [
"/providers/Microsoft.Management/managementGroups/YOUR-MANAGEMENT-GROUP-ID"
],
"permissions": [
{
"actions": [
"Microsoft.Authorization/*/read",
"Microsoft.ResourceHealth/availabilityStatuses/read",
"Microsoft.Resources/subscriptions/resourceGroups/read",
"Microsoft.Web/listSitesAssignedToHostName/read",
"Microsoft.Web/serverFarms/read",
"Microsoft.Web/sites/config/read",
"Microsoft.Web/sites/config/web/appsettings/read",
"Microsoft.Web/sites/config/web/connectionstrings/read",
"Microsoft.Web/sites/config/appsettings/read",
"microsoft.web/sites/config/snapshots/read",
"Microsoft.Web/sites/config/list/action",
"Microsoft.Web/sites/read",
"Microsoft.Web/sites/*/read"
],
"notActions": [],
"dataActions": [],
"notDataActions": []
}
]
}
}For YOUR-MANAGEMENT-GROUP-ID, substitute the name of the management group you want to monitor. If you don't have management groups, you can use your tenant ID because your tenant is your root management group.
-
Select the Save button.
-
Select the Review + create button (or the Next button), check your work, and then select the Review + create button again.
-
Assign the created Custom role to the app: On the subscription's Access control (IAM) page toolbar, select + Add and select Add role assignment.
-
Search for and select the role you just created,
mondoo-role. -
Select the Members tab and select User, group, or service principal.
-
Select the + Select Members link, find and select your Mondoo app registration, and select the Select button.
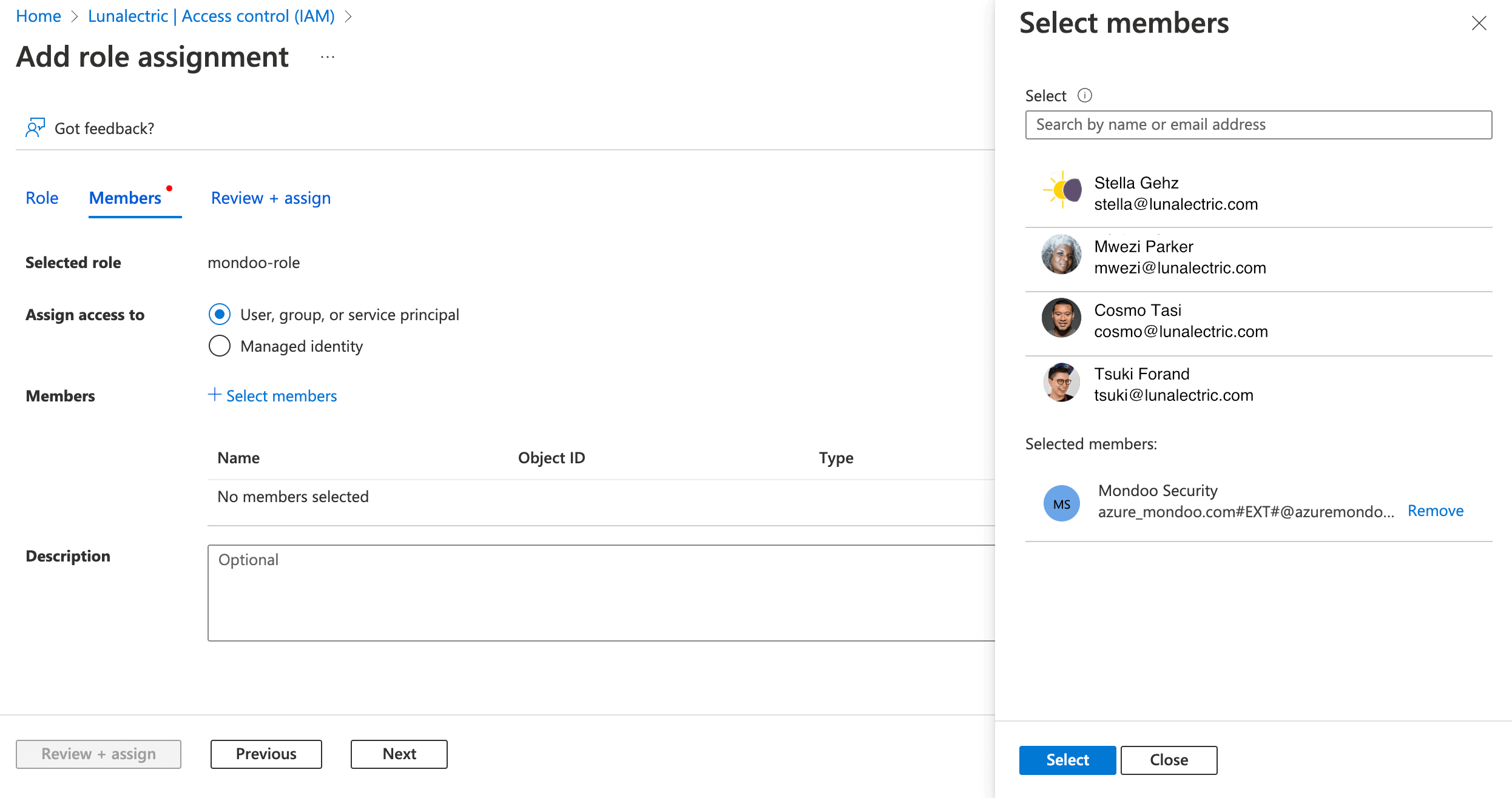
-
Select the Review + assign button to check the assignment. Select the Review + assign button again to assign the
mondoo-rolerole to your Mondoo app registration.
-
Make sure that you have two RBAC roles for the app you created: On the subscription's Access control (IAM) page toolbar, select Check Access.
-
Keep "User, group, or service principal" selected and type name you gave the app, such as
mondoo-security. -
Select the app. Verify that you see two roles: Reader and the custom role that you created.
It can take a few minutes for the roles you assigned to take effect.
Step E: Grant permissions to access Azure key vault
There are two permission models for key vaults: role-based access control (RBAC) and key vault access policy.
See what permission model your key vault uses: In the Azure portal, view the key vault's Access configuration settings. (You can easily change it to RBAC.)
If you are using the RBAC for the key vault, there is no need for further actions; the READ permissions on the key vault will be applied by the "Key Vault Reader" subscription permissions applied in Step C.
If you use legacy access policy permission model for key vaults, this step is required.
A key vault access policy determines whether a given security principal (a user, application or user group) can perform different operations on key vault secrets, keys, and certificates.
-
From the Azure portal home, select Key vaults.
-
Select a key vault from the list.
-
In the sidebar under the key vault name, select Access policies.
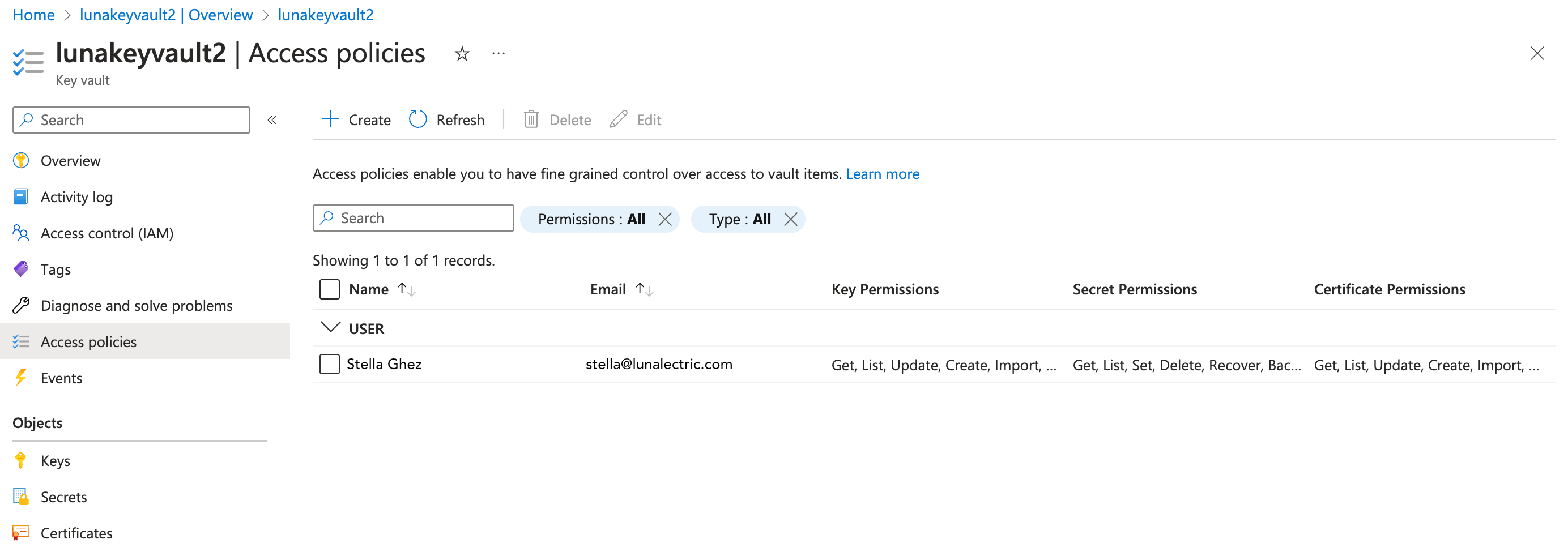
-
In the toolbar, select + Create.
-
Configure the permissions:
-
Under Key permissions, select Get and List.
-
Under Secret permissions, select Get and List.
-
Under Certificate permissions, select Get and List.
-
-
Select the Next button.
-
From the list, select the app registration you created.
-
Select the Next button and select the Next button again to skip the Application (optional) step.
-
Review the access policy and then select the Create button.
Step F: Upload the application certificate.
The app registration and your Mondoo integration must share a PEM (privacy-enhanced mail) certificate for secure authentication. The certificate must not be password protected.
Create a PEM certificate using the method approved by your organization's security team. You need two files:
-
The file you upload to Azure must have only the certificate, not the private key.
-
The file you upload to Mondoo Console (in the Add a new Azure integration in the Mondoo Console section below) must have both the private key and the certificate. It must have a
.pemextension and must use this format and order of information:-----BEGIN PRIVATE KEY-----
key goes here
-----END PRIVATE KEY-----
-----BEGIN CERTIFICATE-----
certificate goes here
-----END CERTIFICATE-----
Generate a self-signed certificate for testing
For testing purposes only, you can use OpenSSL toolkit together with req to generate a certificate. Run this command in Linux shell, macOS shell, or Azure Cloud shell (bash):
openssl req -newkey rsa:4096 -x509 -sha512 -days 365 -nodes -out certificate.pem -keyout privatekey.key
Add the private key to the beginning of the PEM file:
cat privatekey.key certificate.pem > certificate.combo.pem
Upload the certificate to Azure:
-
From the Azure portal home, select Microsoft Entra ID.
-
In the navigation sidebar, select App registrations.
-
Select the app you created.
-
In the sidebar under the app name, select Certificate & secrets.
-
Select Certificates and then select Upload certificate.
-
Select the PEM certificate and enter a description, such as
Mondoo certificate.
Be sure to choose the file containing only the certificate, not the private key.
- Select the Add button.
Add a new Azure integration in the Mondoo Console
After you've created, granted permissions to, and tested a new app registration, you can create a Mondoo Azure integration. You need some values from the app registration you created in the instructions above.
-
Access the Integrations > Add > Azure page in one of two ways:
-
New space setup: After creating a new Mondoo account or creating a new space, the initial setup guide welcomes you. Select BROWSE INTEGRATIONS and then select Azure.
-
INTEGRATIONS page: In the side navigation bar, under INTEGRATIONS, select Add New Integration. Under Cloud Security, select Azure.
-
-
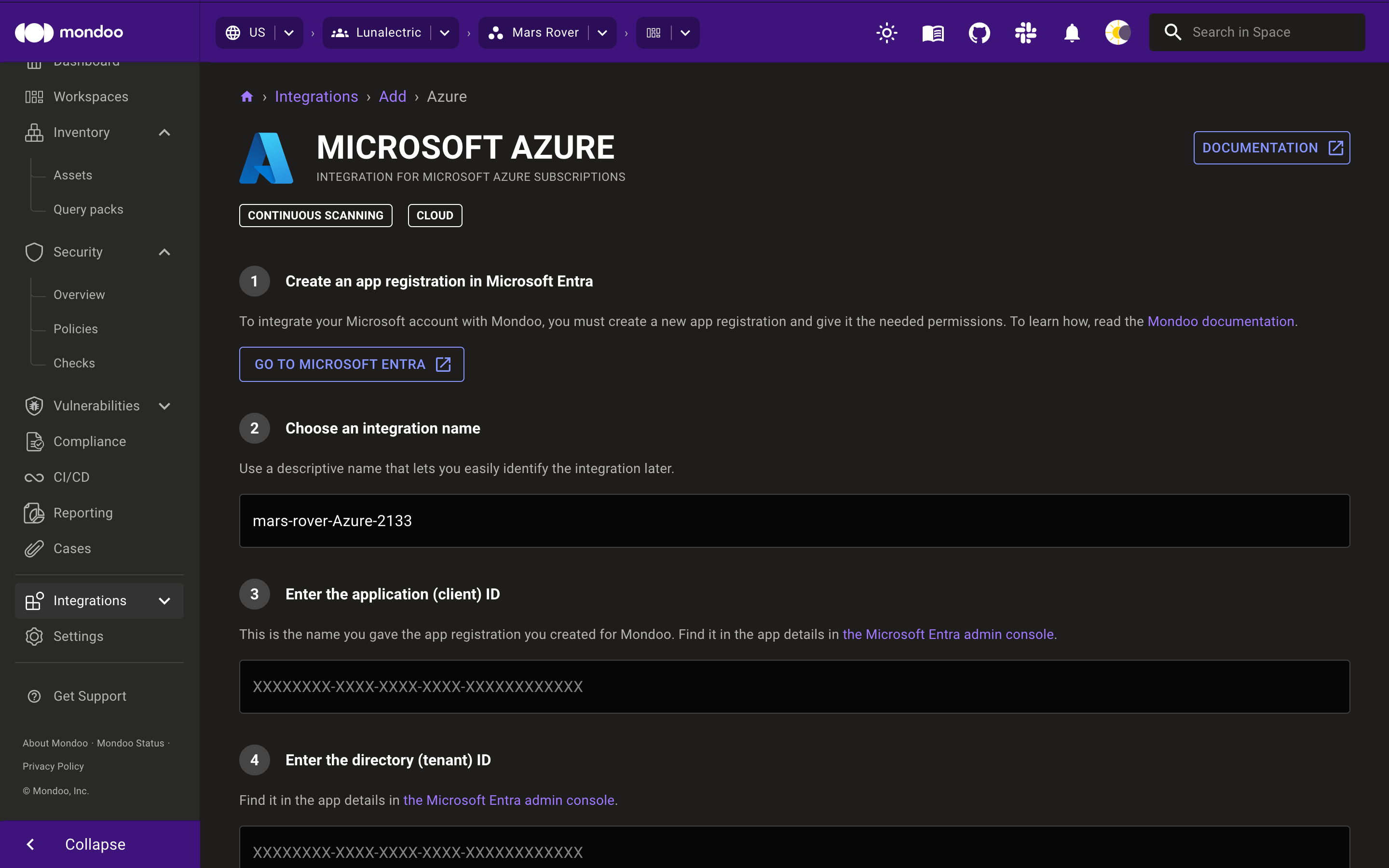
In the Choose an integration name box, enter a name for the integration. Make it a name that lets you easily recognize the Azure tenant.
-
In the Enter the application (client) ID box, enter the value from the app registration's Application (client) ID box.
-
In the Enter the directory (tenant) ID box, enter the value from the app registration's Directory (tenant) ID box.
-
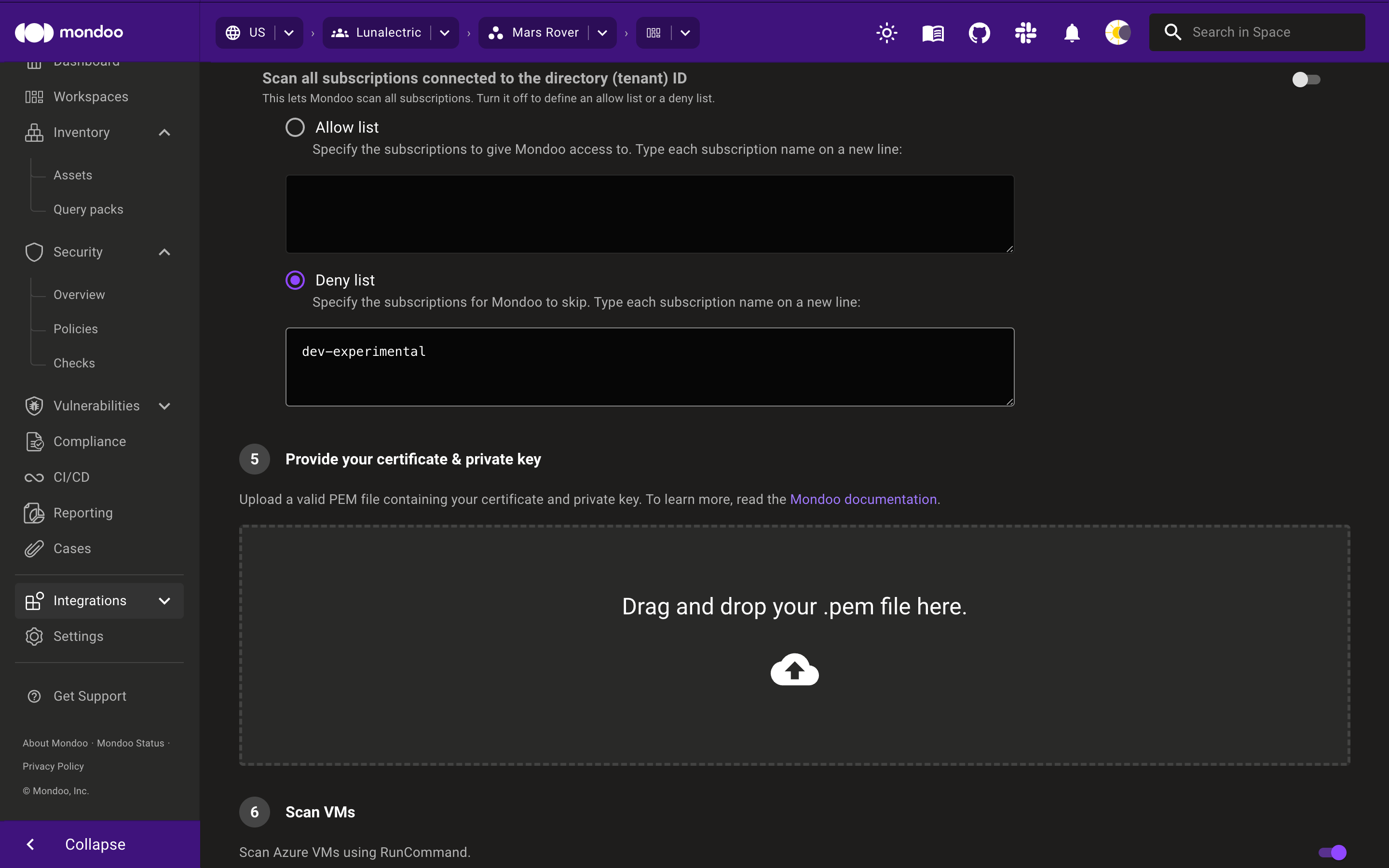
Specify the subscriptions for Mondoo to continuously scan.
-
To continuously scan all subscriptions in the tenant, leave the Scan all subscriptions connected to the directory (tenant) ID toggle enabled.
-
To choose the subscriptions to scan, disable the Scan all subscriptions connected to the directory (tenant) ID toggle, select Allow list and enter the subscription ID to scan.
-
To scan all subscriptions except those you specify, disable the Scan all subscriptions connected to the directory (tenant) ID toggle, select Deny list and enter the names of the subscriptions you don't want Mondoo to scan.
-
-
To automatically discover all Linux and Windows VMs in your subscription and scan them using Azure Run Command, enable Scan VMs.
-
Provide a certificate (a PEM (privacy-enhanced mail) file) for Mondoo to securely authenticate with the app (service principal) you created.
The certificate file must have the
.pemextension and must contain both the private key and the certificate in this order:-----BEGIN PRIVATE KEY-----
key goes here
-----END PRIVATE KEY-----
-----BEGIN CERTIFICATE-----
certificate goes here
-----END CERTIFICATE-----Upload the certificate to Mondoo: In the Drag and drop your .pem file here box, select the cloud icon and choose the file to upload.
-
Select the START SCANNING button.
-
On the Recommended Policies page, enable the policies on which you want to base assessments of your Azure environment. To learn more, read Manage Policies.
-
Select FINALIZE SETUP.
Mondoo begins scanning your Azure resources. When it completes, you can see results on the INVENTORY page. To learn more, read Monitor Your Infrastructure Security.
If your integration is unsuccessful, read Troubleshoot an Azure Configuration.
Renew application certificate
The application certificate created as part of adding the Azure integration has a limited lifetime (by default 1 year). When this certificate expires the integration will no longer function. Renewing the application certificate can be done from the Azure CLI:
-
Navigate to the app registration you created for Mondoo as part of the integration. Copy the application ID for the next steps.
-
Open the Azure Cloud Shell (top right of the window). We will be renewing the certificate with a newly created one.
-
Enter the following command, inserting the application ID you copied:
az ad app credential reset --id XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXX --create-cert -
The certificate will be stored in your cloud shell. You can download it from there through the "Manage files" button of the Azure Cloud Shell.
-
In the Mondoo console, navigate to Integrations > Azure > your Azure integration.
-
Edit the integration and scroll down to point 5. You should see the following field where you can upload the created certificate:
-
Upload your newly created certificate and save your updated configuration. The Azure integration will start using the new certificate for communication with Azure.