Automatically Set Up Azure Continuous Scanning
The Mondoo Azure integration lets you continuously scan Azure resources, such as compute instances and databases, in one or more Azure subscriptions.
Choose the manual or automated setup
Mondoo offers two approaches to setting up an integration for continuous Azure scanning: automated and manual.
Follow the manual setup in these rare cases:
-
You want to integrate Mondoo with all subscriptions in a management group
-
You use the legacy access policy permission model for your key vaults (instead of RBAC)
-
Your Azure environment is unusually large
All other users can follow the automatic setup described below.
Prerequisites
Before you integrate Microsoft Azure with Mondoo, be sure you have:
-
A Mondoo account with Editor or Owner permissions for the space in which you want to add the integration.
-
An Azure account with an active subscription and permission to manage applications in Microsoft Entra ID (formerly Active Directory). Any of these Entra built-in roles include the required permissions:
-
If you want to set up the integration to scan Azure virtual machines (VMs), you must have one of these built-in roles:
In the Azure portal you can see what roles your user account has: Go to Microsoft Entra ID > Users > (your user account) > Assigned roles.
Add a new Azure integration in the Mondoo console
Create an integration to set up continuous Mondoo scanning of your Azure subscription.
-
Access the Integrations > Add > Azure page in one of two ways:
-
New space setup: After creating a new Mondoo account or creating a new space, the initial setup guide welcomes you. Select BROWSE INTEGRATIONS and then select Azure.
-
INTEGRATIONS page: In the side navigation bar, under INTEGRATIONS, select Add New Integration. Under Cloud Security, select Azure.
-
-
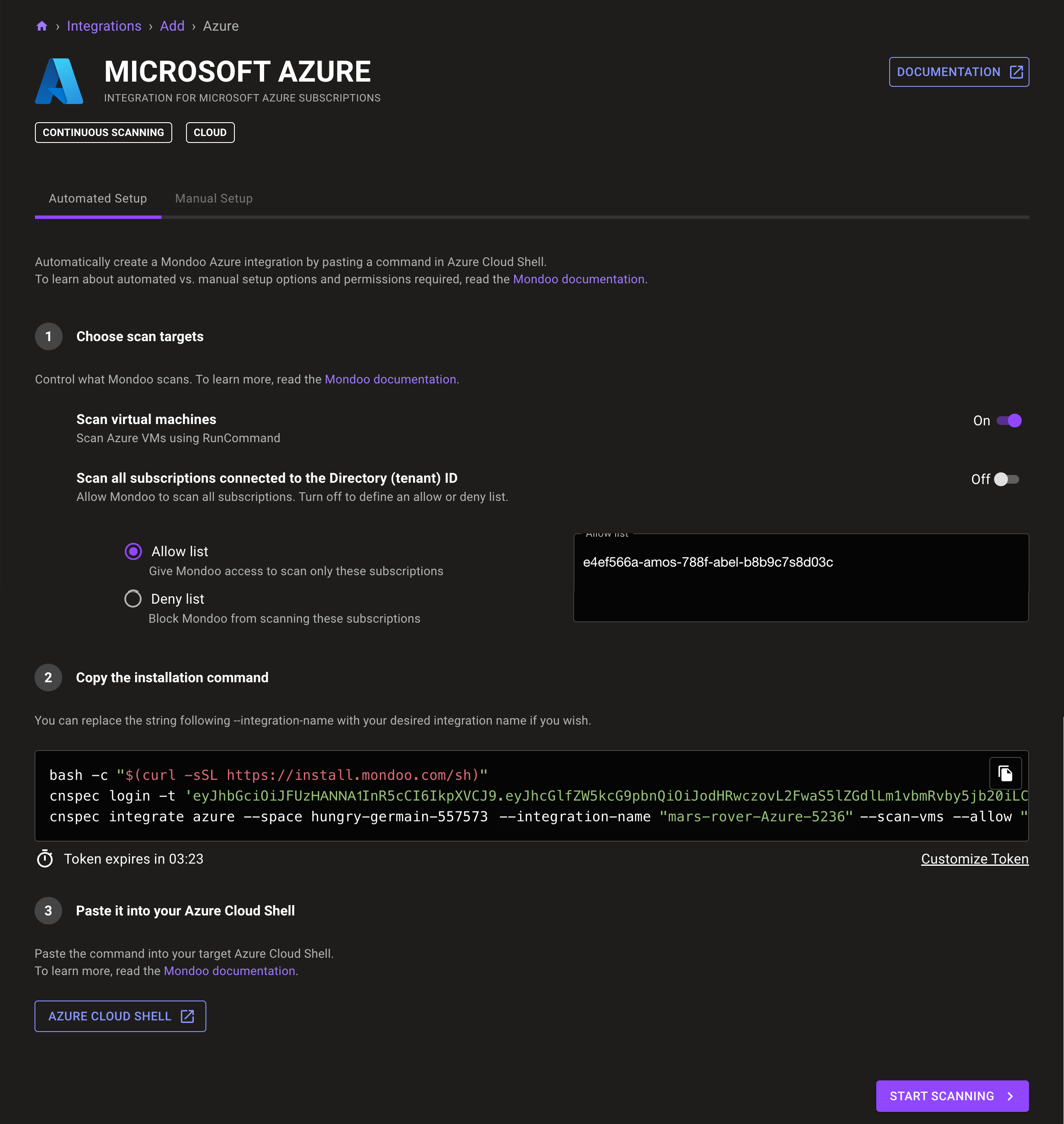
To automatically discover all Linux and Windows virtual machines (VMs) in your subscription and scan them using Azure Run Command, enable Scan virtual machines. If you choose this option, completing the integration setup gives Mondoo permission to read, write, and delete Azure VM run commands through a new role definition named
mondoo_security. -
Choose which subscriptions to scan and which to skip in your Azure tenant. To see a list of your subscriptions and their IDs, go to Subscriptions in the Azure portal.
-
To continuously scan all subscriptions in the tenant, leave the Scan all subscriptions connected to the Directory (tenant) ID toggle enabled.
-
To scan only certain subscriptions, disable the Scan all subscriptions connected to the Directory (tenant) ID toggle. Select Allow list and enter the IDs of the subscriptions to scan. Type each subscription ID on a new line.
-
To scan all subscriptions except those you specify, disable the Scan all subscriptions connected to the Directory (tenant) ID toggle. Select Deny list and enter the IDs of the subscriptions you don't want Mondoo to scan. Type each subscription ID on a new line.
-
-
Under Copy the installation command, you see a custom command that Mondoo generates for you based on your selections above. Running this command in Azure Cloud Shell creates the Mondoo Azure integration for you.
Mondoo names the integration for you. Integration names are visible in the Mondoo console and in reports. You can change the name in the command (in quotes after the --integration-name flag) or change it any time after you create the integration. The ID must be between 7 and 34 characters and can include lowercase letters, numbers, single quotes, hyphens, spaces, and exclamation points. It must start with a lowercase letter and end with a letter or number.
-
Select the copy icon in the installation command box to copy your customized command.
-
Select the AZURE CLOUD SHELL button to open Azure Cloud Shell.
-
Paste the copied command in Azure Cloud Shell and press the Enter or Return key. Respond to these prompts:
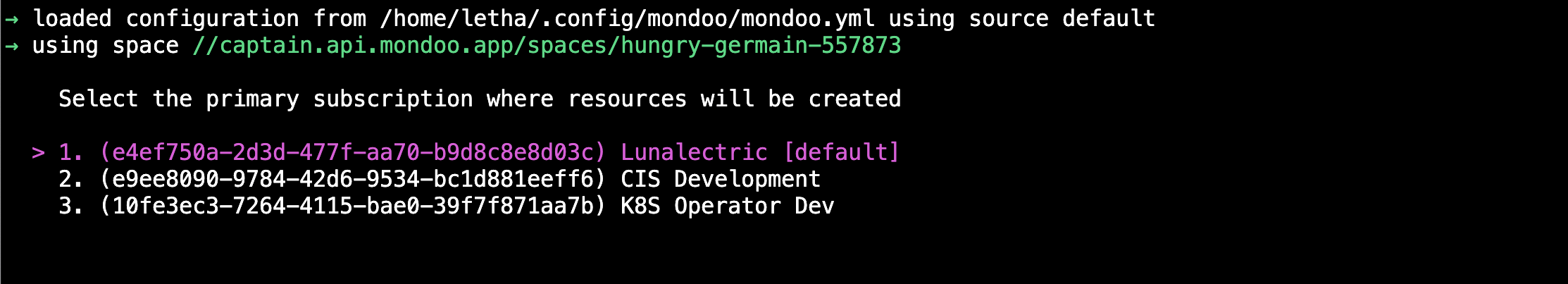
a. When you select this primary subscription, you're not choosing which Azure subscription Mondoo scans; you're specifying where Mondoo creates the resources it needs to perform scans. Use the down arrow key to select the subscription you want and then press Enter.
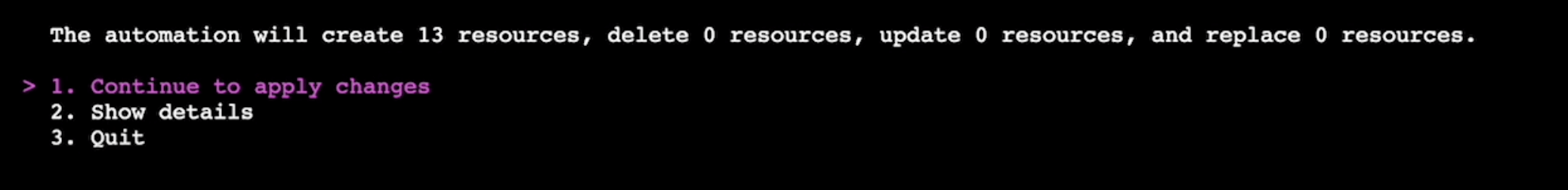
b. The Mondoo automation shows how many resources it must create so it can scan your Azure environment. Press the down arrow key to select 2. Show details and then press Enter.
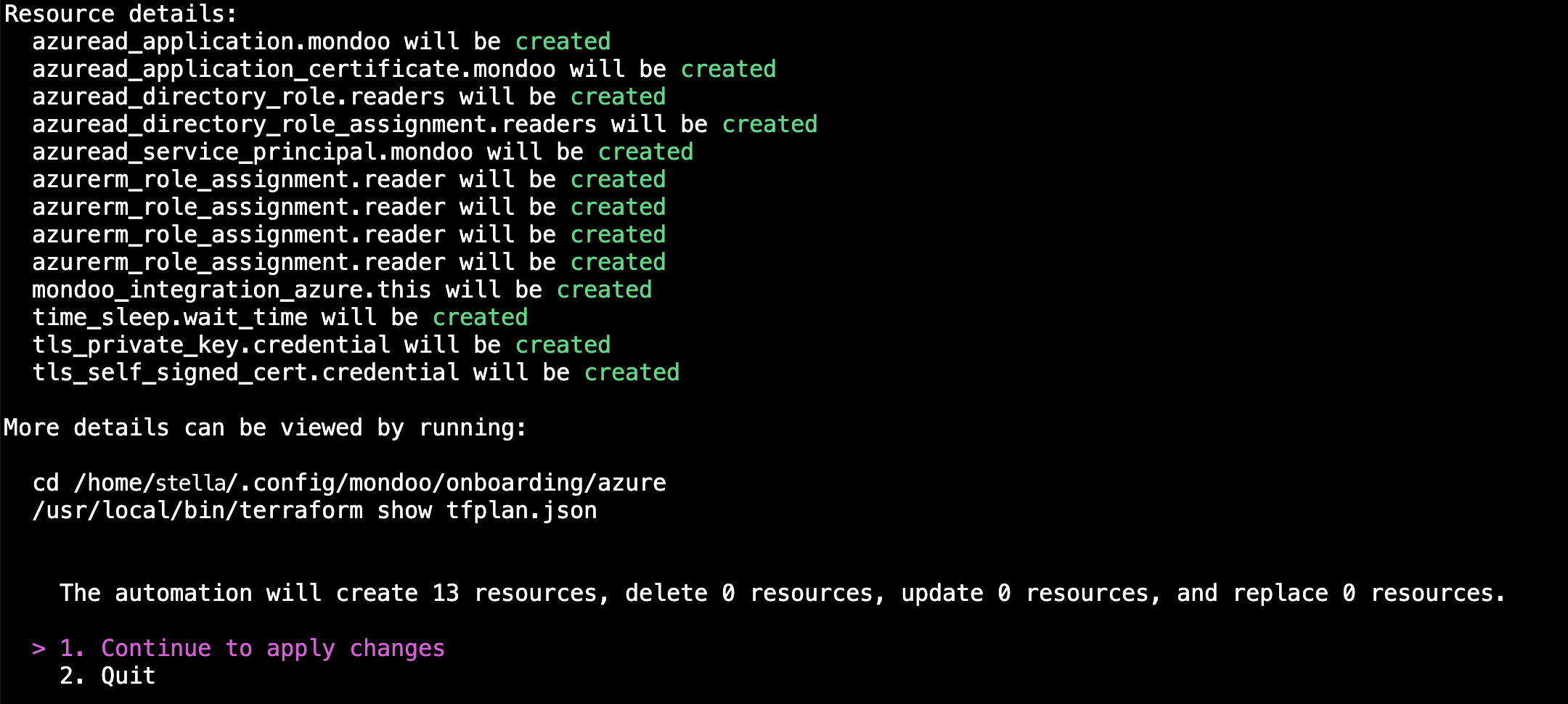
c. Review the list of resources the Mondoo automation must create so it can scan your Azure environment. Press Enter to continue the integration setup.

- When the Mondoo automation reports success, you're finished in Azure Cloud Shell. If you don't see the success message within 5 minutes, read the Troubleshoot section below.
-
Return to the Mondoo console and select the START SCANNING button.
-
On the Recommended Policies page, enable the policies on which you want to base assessments of your Azure environment. To learn more, read Manage Policies.
-
Select FINALIZE SETUP.
Mondoo begins scanning your Azure resources. When it completes, you can see results on the INVENTORY page. To learn more, read Monitor Your Infrastructure Security.
Troubleshoot
-
If the Mondoo automation pauses more than two minutes after you choose the primary subscription, press Control+C to end the process. Paste the copied command and press Enter to run it a second time.
-
If the automation fails, be sure you're logged in with an Azure user account that has the required privileges. To learn more, read the Prerequisites section above.
-
If you don't see your newly created integration in the Mondoo Console after you select policies and finalize setup, try refreshing the page in your browser.
Renew application certificate
The application certificate that was created as part of adding the Azure integration has a limited lifetime (by default 1 year). When this certificate expires the integration will no longer function. Renewing the application certificate can be done from the Azure CLI:
-
Navigate to the app registration you created for Mondoo as part of the integration. Copy the application ID for the next steps.
-
Open the Azure Cloud Shell (top right of the window). We will be renewing the certificate with a newly created one.
-
Enter the following command, inserting the application ID you copied:
az ad app credential reset --id XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXX --create-cert -
The certificate will be stored in your cloud shell. You can download it from there through the "Manage files" button of the Azure Cloud Shell.
-
In the Mondoo console, navigate to Integrations > Azure > your Azure integration.
-
Edit the integration and scroll down to point 5. You should see the following field where you can upload the created certificate:
-
Upload your newly created certificate and save your updated configuration. The Azure integration will start using the new certificate for communication with Azure.